The Role of AMSI in Windows Security
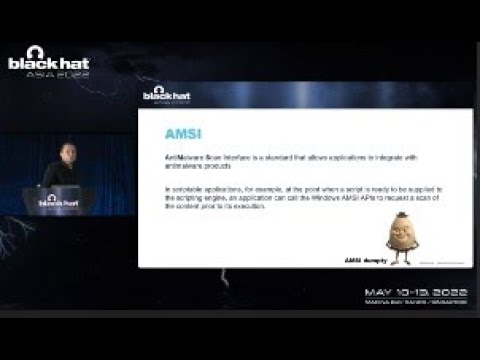
AMSI acts as a bridge, allowing applications and services to integrate with installed antimalware products. When a script, like PowerShell or VBScript, is executed, AMSI intercepts its content *before* it runs. This raw content is then passed to the antimalware provider for scanning. The objective is simple yet critical: identify and block malicious code that might reside within seemingly innocuous scripts, a common tactic for advanced persistent threats (APTs) and malware. Without AMSI, scripts could execute arbitrary code undetected, turning trusted system tools into potent weapons.Anatomy of Known AMSI Bypass Techniques
Attackers, ever resourceful, have devised numerous ways to circumvent AMSI's scrutiny. These techniques often exploit how AMSI is implemented or how scripts are loaded and executed. Understanding these methods is the first step in building robust defenses.1. Patching the `amsi.dll` Memory
One of the most prevalent methods involves directly patching the `amsi.dll` library in memory. This typically involves finding the `AmsiScanBuffer` function within the loaded `amsi.dll` module and modifying its behavior.- **The Mechanism**: Attackers locate the `AmsiScanBuffer` function, the core component responsible for scanning data. They then overwrite a small portion of the function's prologue with instructions that cause it to return a "clean" result immediately, effectively telling AMSI that the script is benign regardless of its actual content.
- **Detection Vectors**:
- **Memory Integrity Checks**: Regularly scanning the memory space of critical processes (like `powershell.exe`, `cmd.exe`, `wscript.exe`, `cscript.exe`) for modifications to known API functions. Tools like Sysmon can log memory modifications, providing valuable forensic data.
- **Hook Detection**: Monitoring for suspicious API hooks or modifications in loaded modules.
- **Behavioral Analysis**: Observing anomalous scripting behavior that bypasses expected security checks.
2. Patching the `AmsiUtils.dll` or `amsi.dll` Export Table
Similar to direct memory patching, this approach targets the export table of `amsi.dll` or related utility DLLs. By nullifying or redirecting the function pointers within the export table, attackers can prevent the AMSI functions from being correctly resolved and called.- **The Mechanism**: Instead of patching the function's code directly, attackers modify the DLL's export directory entries, pointing critical functions like `AmsiScanBuffer` to a dummy routine or nullifying them.
- **Detection Vectors**:
- **DLL Export Table Verification**: Verifying the integrity of the export tables of loaded DLLs against known good signatures.
- **Process Hollowing/Injection Detection**: These techniques are often prerequisites for such tampering.
3. Leveraging Obfuscation and Encryption
While not a direct bypass of AMSI's scanning logic, heavy obfuscation and encryption can hinder its ability to analyze the script content effectively.- **The Mechanism**: Attackers encrypt or encode their malicious payload, and the decryption/deobfuscation routine is embedded within the script. AMSI might scan the initial obfuscated code, finding nothing malicious, and then fail to detect the payload once it's decrypted in memory.
- **Detection Vectors**:
- **Deobfuscation Techniques**: Implementing dynamic analysis environments (sandboxes) that can execute scripts and inspect their behavior after deobfuscation.
- **String Analysis**: Looking for suspicious patterns in strings, even if obfuscated, such as base64 encoding or known obfuscation keywords.
- **Machine Learning/AI**: Training models to identify patterns typical of malicious obfuscation.
4. Disabling AMSI via Registry or Group Policy
In some scenarios, attackers might attempt to disable AMSI entirely on a target system.- **The Mechanism**: This involves changing specific registry keys or Group Policy Object (GPO) settings that control AMSI's activation. This is typically achievable only with elevated privileges.
- **Detection Vectors**:
- **Configuration Monitoring**: Regularly auditing registry keys and GPO settings related to AMSI for unauthorized changes.
- **Endpoint Detection and Response (EDR)**: Modern EDR solutions are designed to detect such critical configuration changes.
The New Frontier: Patching AMSI Providers' Code
The aforementioned techniques primarily target `amsi.dll` itself. However, AMSI's effectiveness relies on the *providers*—the antimalware engines that perform the actual scanning. What if we could bypass the scanner by tampering with the provider's interaction with AMSI, rather than AMSI's core functions? This approach focuses on the code that the antimalware vendor implements to interface with AMSI. Each vendor provides a DLL that AMSI loads to perform scans. By patching this specific provider's code, we can subtly alter its reporting mechanism.A Novel Bypass: The `AmsiScanBuffer` Provider Patch
Instead of patching `amsi.dll` directly, this technique targets the specific provider DLL (e.g., a hypothetical `MyAVProvider.dll`). The goal is to intercept the data being sent for scanning *within* the provider's code, or to manipulate the return values of the scanning process before they are sent back to `amsi.dll`.- **Research Focus**: The core idea is to understand the callback functions that AMSI uses and how providers implement their scanning logic. By injecting code into the provider's process or modifying its loaded module in memory, an attacker could:
- **Nullify Scan Results**: Force the provider to always return a "clean" status code, regardless of actual malicious content.
- **Data Tampering**: Alter the content being scanned just before the provider scans it, rendering malicious patterns unrecognizable.
- **Prevent Scanning**: Cause the provider to crash or exit prematurely when AMSI attempts to scan suspicious content.
- **Implementation Challenge**: This is significantly more complex than patching `amsi.dll`. It requires knowledge of the specific antimalware provider's internals, potentially including reverse engineering its DLLs. The exact implementation would vary greatly between different antimalware solutions.
Defensive Strategies: Beyond Signature-Based Detection
The constant evolution of bypass techniques underscores the need for multi-layered, proactive defense strategies. Relying solely on known signatures for AMSI bypasses is a losing game.1. Enhanced Memory Forensics and Behavioral Monitoring
- **Continuous Memory Scans**: Implement automated, frequent memory scans of critical processes for unauthorized modifications to code sections and API hooks, especially targeting `amsi.dll` and known antimalware provider DLLs.
- **Process Behavior Analysis**: Monitor script execution for anomalous patterns. For instance, scripts that attempt to self-modify, access unusual memory regions, or establish network connections shortly after execution might be suspect. EDR solutions excel here.
2. Runtime Application Self-Protection (RASP) for Scripts
While not a direct AMSI enhancement, RASP principles can be applied to critical administrative scripts. By embedding checks within the script itself, it can detect if its own integrity has been compromised or if it's being executed in a potentially malicious context.3. Vendor Collaboration and Threat Intelligence Sharing
- **Rapid Patching**: Antimalware vendors must be agile. Threat intelligence feeds are crucial for quickly identifying new bypasses and pushing out signature updates or behavioral rules.
- **Proactive Research**: Security researchers and vendors need to continually explore the attack surface of AMSI and its providers, anticipating future bypass methods.
4. Hardening Script Execution Policies
- **Constrained Language Mode**: For PowerShell, using the Constrained Language Mode where applicable can significantly limit the scripting capabilities available to an attacker.
- **Script Block Logging and Module Logging**: Enabling these logging features can provide deeper insights into script execution, even if the content is obfuscated. These logs can be invaluable during incident response.
Veredicto del Ingeniero: AMSI's Evolving Battle
AMSI is a vital component of Windows' security posture, a necessary barrier against script-based attacks. However, its design, as with any security mechanism, presents an attack surface. The techniques to bypass it are constantly evolving, moving from direct patching of `amsi.dll` to more sophisticated methods targeting the antimalware providers themselves. The "new approach" of patching provider code represents a logical progression in the attacker's playbook due to its potential for stealth. It requires a deeper understanding of the antimalware ecosystem. For defenders, this means that vigilance against `amsi.dll` modifications alone is insufficient. A holistic strategy involving robust memory integrity checks, advanced behavioral analysis, and continuous threat intelligence sharing with antimalware vendors is paramount. The arms race continues, and staying ahead requires constant adaptation and a deep understanding of the adversary's evolving tactics.Arsenal del Operador/Analista
- Antivirus/EDR Solutions: Ensuring up-to-date EDRs with strong behavioral monitoring capabilities (e.g., CrowdStrike Falcon, SentinelOne).
- Sysmon: Essential for logging detailed process, network, and registry activity, providing crucial data for detecting memory tampering and suspicious script execution.
- Memory Analysis Tools: Volatility Framework, Rekall for forensic analysis of memory dumps to identify runtime modifications.
- Scripting Languages: PowerShell and Python for developing custom detection scripts and automation tools.
- Reverse Engineering Tools: IDA Pro, Ghidra for deep analysis of DLLs and understanding provider internals.
- Books: "The Official’” PowerShell Practice, Problems, and Solutions" for understanding PowerShell's intricacies, and general reverse engineering texts.
- Certifications: OSCP (Offensive Security Certified Professional) and related certifications provide hands-on experience with offensive techniques, which is invaluable for developing defensive countermeasures.
Taller Práctico: Fortaleciendo la Detección de Parches en Memoria
Este taller se centra en cómo puedes usar Sysmon para detectar modificaciones en memoria, una técnica común en los bypasses de AMSI.
- Instalar Sysmon: Asegúrate de tener Sysmon instalado y configurado en tus endpoints. Una configuración robusta es clave. Puedes usar la configuración de Sysmon recomendada por SwiftOnSecurity u otras fuentes confiables.
-
Configurar Reglas de Integridad de Memoria: Aunque Sysmon no escanea directamente el código en memoria en tiempo real para buscar parches, puedes crear reglas que detecten procesos que intentan modificar la memoria de otros procesos o que cargan módulos de formas sospechosas.
Busca eventos relacionados con:
- Event ID 8: CreateRemoteThread
- Event ID 10: ProcessAccess (filtrando por accesos de escritura a memoria o asignación de memoria)
- Event ID 7: ImageLoad (analizando el orden de carga de DLLs)
Ejemplo de filtro en Sysmon (XML): Para detectar procesos que intentan realizar operaciones de acceso de memoria sospechosas en procesos de scripting como powershell.exe o cmd.exe:
<RuleGroup name="" groupRelation="or"> <ProcessAccess name="detect_remote_thread_powershell"> <SourceImage condition="is">C:\Windows\System32\svchost.exe</SourceImage><!-- Ejemplo de proceso de carga malicioso --> <SourceImage condition="is">C:\Windows\System32\rundll32.exe</SourceImage><!-- Otro ejemplo --> <TargetImage condition="is">C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe</TargetImage> <TargetImage condition="is">C:\Windows\System32\cmd.exe</TargetImage> <GrantedAccess condition="contains">0x10</GrantedAccess><!-- PROCESS_VM_OPERATION --> <GrantedAccess condition="contains">0x20</GrantedAccess><!-- PROCESS_VM_WRITE --> <GrantedAccess condition="contains">0x40</GrantedAccess><!-- PROCESS_VM_READ --> <GrantedAccess condition="contains">0x1000</GrantedAccess><!-- PROCESS_CREATE_THREAD --> </ProcessAccess> </RuleGroup> - Monitorizar Cargas de Módulos: Observa eventos de `ImageLoad` (Event ID 7) para detectar la carga inusual de DLLs en procesos de scripting o antimalware. Un módulo inesperado cargado por `powershell.exe` o un proceso de AV es una gran bandera roja.
- Análisis Forense de Memoria: En caso de sospecha, captura un volcado de memoria del proceso afectado y analízalo con herramientas forenses (como Volatility) para buscar parches en funciones específicas como `AmsiScanBuffer`.
Preguntas Frecuentes
¿Es AMSI una solución completa contra todo tipo de ataques de scripting?
No. AMSI es una capa de defensa crucial, pero no es infalible. Los atacantes desarrollan continuamente técnicas para evadirlo. La seguridad efectiva requiere múltiples capas.¿Qué antimalware es más resistente a los bypasses de AMSI?
La resistencia varía entre proveedores y se actualiza constantemente. Los proveedores que invierten fuertemente en análisis de comportamiento y heurística suelen ser más efectivos contra técnicas de bypass desconocidas.¿Puedo deshabilitar AMSI de forma segura?
No se recomienda. Deshabilitar AMSI elimina una protección crítica contra malware basado en scripts y deja tus sistemas significativamente más vulnerables. Solo debe considerarse en entornos muy controlados y temporales con explicaciones de seguridad documentadas.El Contrato: Fortalece Tu Perímetro de Scripting
Has navegado por las sombras de los bypasses de AMSI, comprendiendo no solo las tácticas de los adversarios, sino también el terreno sobre el que luchan. Ahora, el contrato es tuyo para ejecutar:
- Audita tus Sistemas: Revisa las configuraciones de Sysmon y tus soluciones EDR. ¿Están optimizadas para detectar el acceso a memoria y la carga remota de hilos en procesos de scripting? Identifica al menos una brecha en tu configuración actual de auditoría.
- Investiga tu Antimalware: Consulta la documentación de tu proveedor actual de antimalware. ¿Qué capacidades específicas tienen para detectar bypasses de AMSI o modificaciones en memoria? Si no encuentras información clara, considera esto como una señal para investigar alternativas.
- Desarrolla una Regla de Detección: Basado en tu investigación, escribe una regla de detección conceptual (o real si tienes las herramientas) para un posible bypass de AMSI. Puede ser una regla de YARA para buscar patrones de parches en memoria, o una consulta SIEM para eventos anómalos de procesos de scripting.
El conocimiento sin acción es inútil. El campo de batalla digital no espera a los indecisos. Demuestra tu compromiso con la defensa hoy.