Table of Contents
- The Operative's Edge: Why Kali NetHunter on Android?
- Pre-Deployment Checklist: What You Need
- Phase 1: Securing the Perimeter with Termux
- Phase 2: Deploying Kali NetHunter Framework
- Phase 3: Activating the Graphical Interface (GUI)
- Phase 4: Essential Tooling and Post-Installation
- Troubleshooting Common Anomalies
- Engineer's Verdict: Is This Setup Worth the Deployment?
- Operator's Arsenal: Recommended Gear
- Frequently Asked Questions
- The Contract: Your First Recon Mission
The Operative's Edge: Why Kali NetHunter on Android?
In the shadows of the internet, speed and mobility are paramount. While traditional setups have their place, the ability to conduct reconnaissance, test network defenses, or even perform quick vulnerability assessments from a device that slips into your pocket is an undeniable advantage. Kali NetHunter, when deployed on Android, offers precisely this. It brings the power of a full Kali Linux environment, including its vast array of security tools, directly to your mobile device. The key here is "no root." This circumvents the need for complex device modifications that can void warranties or introduce security risks. By leveraging applications like Termux, we create a chroot environment that houses Kali functionalities without compromising the host Android system.
This strategic deployment is crucial for:
- Mobile Penetration Testing: Conduct tests on networks you have explicit permission to access, directly from the field.
- Bug Bounty Hunting: Quickly set up and test potential vulnerabilities on the go.
- Security Education: A hands-on learning platform that's always accessible.
- Digital Forensics (Limited Scope): Basic data collection and analysis in a mobile capacity.
Pre-Deployment Checklist: What You Need
Before initiating the installation sequence, ensure you have the following operational assets:
- An Android device (version 5.0 or higher recommended).
- A stable internet connection.
- Sufficient storage space (at least 5-10 GB recommended for Kali and tools).
- The Termux application installed from F-Droid (this is critical, as the Play Store version is outdated and lacks necessary features).
- A text editor or a way to easily copy and paste commands.
Phase 1: Securing the Perimeter with Termux
Termux is our initial foothold. It’s a powerful terminal emulator and Linux environment app that runs on Android. It doesn't require root and provides a robust command-line interface.
- Install Termux: Download and install Termux from the F-Droid repository. Search for "Termux" and install the official application.
- Update Packages: Open Termux and run the following commands to ensure all packages are up-to-date. This is a critical step to avoid dependency conflicts later.
pkg update && pkg upgrade -y - Install Required Utilities: We need a few essential tools to facilitate the NetHunter installation.
pkg install git wget proot -ygit: For cloning repositories.wget: For downloading files.proot: A user-space implementation of chroot, used here to simulate a root environment without actual root access.
Phase 2: Deploying Kali NetHunter Framework
Now, we'll deploy the NetHunter installer script. This script automates the process of downloading and setting up the Kali NetHunter environment within Termux.
- Clone the NetHunter-In-Termux Repository: Navigate to a suitable directory and clone the official repository.
cd ~ git clone https://github.com/nmilosevic/termux-nethunter.git - Navigate to the Repository Directory:
cd termux-nethunter - Run the Installation Script: Execute the installer script. This process can take a significant amount of time depending on your internet speed and device performance.
./nethunter-install.shFollow the on-screen prompts. The script will download the Kali rootfs (the core filesystem) and set up the necessary configurations.
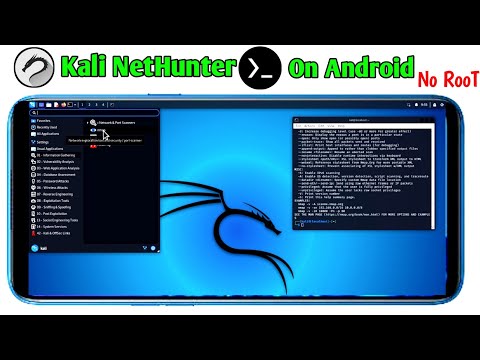
Phase 3: Activating the Graphical Interface (GUI)
The core Kali installation is complete, but to get the GUI mode, we need to set up a VNC (Virtual Network Computing) server. This allows us to remotely access the graphical desktop environment.
- Install VNC Server and Desktop Environment: Once the NetHunter installation script finishes, you’ll need to install a VNC server and a lightweight desktop environment within the Kali chroot. First, start the Kali environment:
./nethunter --install-kali-defaultsThis command will download and install basic Kali packages, including common tools and a desktop environment (often XFCE or LXDE). This can also take a considerable amount of time.
- Start the VNC Server: After the default Kali packages are installed, start the VNC server.
./nethunter --vncThis command will start the VNC server and typically assign it a port (e.g., 5901). Note this port number.
- Install a VNC Viewer App: On your Android device, install a VNC viewer application from the Google Play Store. Popular options include "VNC Viewer - Remote Desktop" by RealVNC or "bVNC Free."
- Connect to the VNC Server:
- Open your VNC viewer app.
- Create a new connection.
- For the address, enter
localhost:PORT(replacePORTwith the port number you noted in step 2, e.g.,localhost:5901). - You may be prompted for a password. The default NetHunter VNC password is usually
nethunter, but it's highly recommended to change this for security.
If everything is configured correctly, you should now see the Kali Linux graphical desktop environment on your phone.
Phase 4: Essential Tooling and Post-Installation
With the GUI up and running, it's time to ensure your toolkit is complete and secure.
- Update Kali Repositories: Once inside the Kali GUI or via the Termux shell (`./nethunter --kali`), update Kali's package lists and upgrade installed packages.
apt update && apt upgrade -y - Install Specific Tools: You can now install any additional tools you need directly within the Kali environment using
apt install. For example:apt install metasploit-framework nmap wireshark hydra john aircrack-ng -y - Change VNC Password: It's imperative to change the default VNC password. You can do this from within the Kali GUI by accessing the terminal and running:
vncpasswdFollow the prompts to set a strong, unique password.
- Explore NetHunter Features: Familiarize yourself with the NetHunter specific tools and features available through the app drawer or terminal commands.
Troubleshooting Common Anomalies
Even in the most sterile environments, glitches occur. Here’s how to handle common issues:
- VNC Connection Fails:
- Ensure the VNC server is running (`./nethunter --vnc`).
- Double-check the IP address and port (usually
localhost:5901). - Verify you're using the correct password.
- Try restarting Termux and running the VNC start command again.
- Slow Performance:
- Kali NetHunter on Android, especially with GUI, is resource-intensive. Close unnecessary Android apps.
- Consider using a lighter desktop environment if available, or stick to command-line tools.
- Ensure your device has sufficient RAM and storage.
- "Command not found" errors:
- Verify that you are in the correct environment (Termux or Kali chroot via `./nethunter --kali`).
- Ensure the tool was installed correctly using
apt installwithin Kali orpkg installwithin Termux.
- Installation script errors:
- Ensure you downloaded the latest version of the script from the official GitHub repository.
- Check your internet connection during the download/installation phase.
- Consult the GitHub repository's issues section for known problems and solutions.
Engineer's Verdict: Is This Setup Worth the Deployment?
Deploying Kali NetHunter GUI on Android via Termux without root is a technically impressive feat that offers significant benefits for mobile security professionals and enthusiasts. The portability and accessibility are unparalleled. However, it's not without its trade-offs. Performance can be a bottleneck on lower-end devices, and the setup requires a degree of technical proficiency. For comprehensive, high-stakes penetration testing, a dedicated laptop or desktop Kali installation will always be superior. But for on-the-go reconnaissance, quick vulnerability checks, and as a powerful learning tool, this setup is absolutely **worth the deployment**. It transforms a ubiquitous device into a potent security asset.
Operator's Arsenal: Recommended Gear
- Core Software: Termux (F-Droid version), VNC Viewer app.
- Kali NetHunter Script: Official `termux-nethunter` repository from GitHub.
- Essential Linux Utilities: `git`, `wget`, `proot` (installed via
pkg). - Kali Tools: `metasploit-framework`, `nmap`, `wireshark`, `aircrack-ng`, `hydra`, `john` (installed via
aptwithin Kali). - Security Books: "The Hacker Playbook" series, "Penetration Testing: A Hands-On Introduction to Hacking"
- Certifications to Aim For: Offensive Security Certified Professional (OSCP) - while not directly related to this mobile setup, it signifies a deep understanding of pentesting principles.
Frequently Asked Questions
Can I use this for Wi-Fi hacking?
Yes, NetHunter supports various Wi-Fi attack vectors, but many advanced Wi-Fi attacks require specific wireless adapters and root access for full functionality. With Termux and NetHunter, you can perform some Wi-Fi reconnaissance and basic attacks, but full compatibility might be limited compared to a rooted device or a dedicated Kali machine.
Is it safe to use NetHunter on my main Android device?
Since this method does not require root, it's generally safer than rooting your device. However, you are installing a powerful suite of security tools. Always be mindful of the networks you connect to and the actions you perform. Never use these tools on networks you do not have explicit permission to test.
How do I update Kali NetHunter when new versions are released?
You will typically need to re-run the installation script or update the `termux-nethunter` repository using `git pull` and then re-execute the installation script. Check the script's GitHub page for the latest update procedures.
The Contract: Your First Recon Mission
Your mission, should you choose to accept it, is to conduct a preliminary network reconnaissance of your *own* home Wi-Fi network. Using your newly deployed Kali NetHunter GUI:
- Connect to your home Wi-Fi.
- Open the Kali terminal.
- Use
nmapto scan your local network. Attempt to discover other devices connected to your network and identify open ports on them. - Document your findings: List the IP addresses of devices found and any open ports.
This exercise is about understanding your network's footprint. Remember, knowledge is power, but misapplied power leads to disaster. Always operate within ethical and legal boundaries.
