Table of Contents
- The Genesis of WannaCry: Exploiting Shadow Broker's Secrets
- The Worm That Ate the World: Propagation and Impact
- Anatomy of the Payload: Encryption and Extortion
- Defensive Failure and Recovery: What Went Wrong?
- Lessons Learned for the Defender
- The WannaCry Aftermath and Evolution
- Engineer's Verdict: Patch Management as the First Line of Defense
- Operator's Arsenal for Ransomware Defense
- Defensive Drill: Detecting and Isolating an Outbreak
- Frequently Asked Questions
- The Contract: Hardening Your Network Against Ransomware
The Genesis of WannaCry: Exploiting Shadow Broker's Secrets
Every major cyber event has a genesis, a point where potential energy transforms into kinetic destruction. For WannaCry, that spark was the EternalBlue exploit. Allegedly developed by the NSA and later leaked by the shadowy entity known as The Shadow Brokers, EternalBlue was a weaponized vulnerability targeting Microsoft's implementation of the Server Message Block (SMB) protocol. SMB is fundamental to Windows networking, handling file sharing, printer access, and inter-process communication. A flaw here, especially one allowing remote code execution without user interaction, is akin to leaving the front door of your digital castle wide open. On April 14, 2017, The Shadow Brokers released the EternalBlue exploit. This was a critical intelligence failure for many organizations: a known exploit, a known target protocol, and yet, a massive attack still succeeded. Microsoft had released security patches (MS17-010) in March 2017, but the sheer number of unpatched systems was staggering. This gap represented the fertile ground where WannaCry would soon germinate.The Worm That Ate the World: Propagation and Impact
What distinguished WannaCry from a simple ransomware dropper was its worm-like propagation mechanism. Once inside a vulnerable system, WannaCry didn't just encrypt local files. It scanned the internal network and the wider internet for other machines susceptible to EternalBlue. This self-propagating nature allowed it to spread with astonishing speed. Within hours, it had infected hundreds of thousands of computers across more than 150 countries. The impact was immediate and devastating:- **Healthcare Systems:** The UK's National Health Service (NHS) was hit hard, forcing the cancellation of appointments and surgeries, and diverting ambulances. This highlighted the critical need for robust cybersecurity in essential services.
- **Global Corporations:** Companies like FedEx, Telefónica, and Renault experienced significant disruptions, leading to operational paralysis and substantial financial losses.
- **Government Agencies:** Various government departments and critical infrastructure faced shutdowns, underscoring the national security implications of such attacks.
"The attack was a wake-up call that security is not just an IT issue; it's a national security issue, a public health issue, and a fundamental business continuity issue."
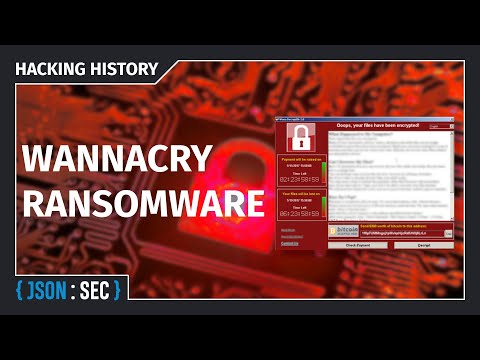
Anatomy of the Payload: Encryption and Extortion
Once WannaCry gained access, its primary objective was to encrypt user files. It targeted a wide range of file types, from documents and photos to databases and backups. The encryption was performed using robust cryptographic algorithms (AES and RSA), making decryption without the private key virtually impossible. The extortion mechanism was classic ransomware: a ransom note demanding payment in Bitcoin. The attackers set a deadline, threatening to double the ransom amount if not paid within three days, and to permanently delete the decryption key after seven days. This created a ticking clock, pressuring victims into making a difficult, often futile, decision. The ransom demand was initially $300, escalating to $600. However, the attackers' financial gains from WannaCry were relatively modest compared to the widespread damage. This raised questions about their primary motive: was it purely financial gain, or was it a demonstration of power and disruption?Defensive Failure and Recovery: What Went Wrong?
The widespread success of WannaCry wasn't solely due to the exploit's potency; it was a cascade of defensive failures:- **Unpatched Systems:** The most significant failure was the sheer number of systems that had not applied the MS17-010 patch. This included not only older, unsupported operating systems like Windows XP and Windows 2003 but also newer versions that were not updated promptly.
- **Inadequate Network Segmentation:** Many organizations lacked proper network segmentation. A breach in one segment could easily jump to others, allowing the worm to spread unimpeded across the entire network.
- **Lack of Robust Backups:** While not directly a failure of prevention, the lack of recent, tested, offline backups meant many organizations had no viable alternative to paying the ransom to recover their data.
- **Slow Incident Response:** In some cases, incident response was slow, allowing the worm to propagate further before containment measures could be effectively implemented.
Lessons Learned for the Defender
WannaCry left an indelible mark on cybersecurity strategy. The lessons are clear and remain critically relevant today:- **Patching is Paramount:** Regularly patching systems, especially those exposed to the internet or internal network services like SMB, is non-negotiable. This includes end-of-life operating systems for which vendor support has ceased but are still in use.
- **Network Segmentation is Crucial:** Divide your network into smaller, isolated zones. This limits the lateral movement of malware and contains outbreaks to a smaller scope.
- **Backup and Disaster Recovery:** Implement a comprehensive backup strategy that includes regular, automated backups stored offline or in an immutable format. Test recovery procedures regularly.
- **Endpoint Detection and Response (EDR):** Modern EDR solutions can detect and block suspicious activities, including the behavior of ransomware and worms, even if the specific signature is unknown.
- **Security Awareness Training:** While WannaCry initially spread via an unpatched vulnerability, subsequent variants and similar attacks often leverage social engineering. Users must be trained to recognize and report suspicious activity.
The WannaCry Aftermath and Evolution
The WannaCry attack wasn't a one-off event. It demonstrated a new paradigm for ransomware: the use of weaponized exploits, particularly those targeting network protocols, to achieve widespread, rapid infection. It catalyzed changes in how organizations approached patching and vulnerability management. Furthermore, it spurred greater collaboration between governments and the private sector to combat cyber threats. While the original WannaCry strain was largely neutralized, its legacy lives on. Variants and similar ransomware attacks continue to emerge, often incorporating new exploits or delivery methods. The fundamental threat remains: unpatched vulnerabilities are gateways for destruction.Engineer's Verdict: Patch Management as the First Line of Defense
Patch management isn't glamorous. It's often a tedious, resource-intensive process. But WannaCry proved it's the bedrock of an effective defense. Ignoring patches is akin to leaving your keys in the ignition and hoping nobody steals your car.- **Pros:** Prevents known exploits, reduces attack surface, maintains compliance.
- **Cons:** Can be resource-intensive, requires careful testing to avoid breaking functionality, can be disruptive if not managed correctly.
- **Verdict:** Essential. The cost of a major breach due to a missed patch far outweighs the cost and effort of a robust patch management program. For any system exposed to a network, especially SMB, patching is not optional.
Operator's Arsenal for Ransomware Defense
To combat threats like WannaCry, a layered defense is crucial. Here's what should be in your toolkit:- **Vulnerability Scanners:** Tools like Nessus, Qualys, or OpenVAS to identify exploitable weaknesses.
- **Patch Management Systems:** Microsoft WSUS/SCCM, Tanium, or similar solutions for systematic patching.
- **Network Intrusion Detection/Prevention Systems (NIDS/NIPS):** Suricata, Snort, or commercial equivalents to detect and block malicious network traffic, including exploit attempts.
- **Endpoint Detection and Response (EDR):** SentinelOne, CrowdStrike, Carbon Black, or Microsoft Defender for Endpoint for real-time threat detection and response on endpoints.
- **Security Information and Event Management (SIEM):** Splunk, ELK Stack, or QRadar to aggregate logs, detect anomalies, and facilitate incident investigation.
- **Backup and Recovery Solutions:** Veeam, Commvault, or cloud-native backup services for data resilience.
- **Offline/Immutable Storage:** Ensuring backups are not accessible from compromised networks.
- **Incident Response Playbooks:** Pre-defined procedures for handling ransomware outbreaks.
Defensive Drill: Detecting and Isolating an Outbreak
Imagine the monitors light up with alerts. How do you react?- Hypothesize: Suspect ransomware outbreak based on user reports of encrypted files, ransom notes, or high network traffic spikes.
-
Identify Scope:
- Initiate immediate network segmentation. Isolate affected subnets or critical servers from the rest of the network.
- Use network monitoring tools (e.g., Wireshark, Suricata logs) to identify the source IP addresses and propagation patterns, looking for SMB traffic to unusual ports or internal IPs.
- Query SIEM for logs indicating SMB connection attempts from internal hosts to known vulnerable ports or systems exhibiting abnormal behavior.
-
Containment:
- Implement firewall rules to block SMB traffic (port 445) from isolated segments to the wider network and internet, if not absolutely essential.
- Disable or isolate compromised endpoints.
- Temporarily halt any unpatched systems from accessing the network if they cannot be patched immediately.
-
Analysis:
- Collect malware samples from affected systems for forensic analysis.
- Analyze endpoint logs (even if encrypted) for initial compromise indicators and lateral movement.
- Review network logs for signs of EternalBlue exploitation (e.g., specific packet patterns, anomalous SMB traffic).
-
Remediation:
- Patch all vulnerable systems identified.
- Restore data from known good backups.
- Remove malware and reimage compromised systems.
- Review and strengthen network segmentation and access controls.
- Post-Incident Review: Conduct a thorough review to update security policies, improve patching processes, and enhance incident response plans.
Frequently Asked Questions
-
What is WannaCry?
WannaCry was a ransomware worm that exploited a vulnerability in Microsoft Windows' SMB protocol to spread rapidly across networks and encrypt files, demanding a ransom payment in Bitcoin.
-
How did WannaCry spread so fast?
It used the EternalBlue exploit, which allowed it to infect systems remotely and then act as a worm, scanning for and infecting other vulnerable machines on the network and the internet without any user interaction.
-
Can WannaCry still infect systems today?
While the primary outbreak was contained, older, unpatched systems remain vulnerable to WannaCry or similar threats that use the EternalBlue exploit. Microsoft released patches for supported and some unsupported versions.
-
What is the best defense against ransomware like WannaCry?
A multi-layered approach including regular patching, robust network segmentation, strong backup and recovery strategies, endpoint detection and response (EDR), and user security awareness training.

