The flickering neon of the city reflects on the rain-slicked streets, a familiar noir backdrop to another night in the digital underworld. Tonight, we aren't dissecting malware or hunting APTs. We're peering into the airwaves, where signals meant for millions were brutally intercepted. Live television, a bastion of controlled information, has been compromised. These aren't just glitches; they're scars left by attackers who bypassed physical and digital defenses, turning a trusted medium into a vector for chaos. Let's pull back the curtain on these digital invasions.
Table of Contents
- The Max Headroom Incident: A Glitch in the Machine
- Bomb Threat Interrupts Sports Broadcast
- Channel 4 News Hijacking
- Swedish TV Hijacked by Activists
- Canadian Politicians Hijacked TV Broadcast
- Indian Broadcast Interrupted by Bomb Threat
- NASA TV Interrupted by Unauthorized Broadcast
- Spanish Broadcaster Hacked Live During Football Match
- Ukrainian TV Hacked to Broadcast Russian Propaganda
- US TV Network Hacked During Interview
In the realm of broadcast media, security is paramount. A compromised signal isn't merely a technical embarrassment; it's a breach of public trust, a potential gateway for disinformation, or even a tool for psychological warfare. These incidents serve as stark reminders that no system is truly impenetrable, and the airwaves, once thought to be a secure conduit, are vulnerable to sophisticated attacks. Understanding how these breaches occurred is the first step for any broadcast engineer or security professional aiming to fortify their infrastructure.
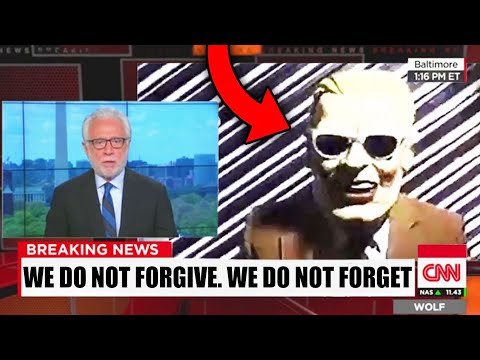
The Max Headroom Incident: A Glitch in the Machine
Perhaps the most infamous incident occurred in Chicago in 1986. A hacker, wearing a Max Headroom mask, disrupted broadcasts of two major networks for several minutes. The intruder replaced the signal with distorted imagery and garbled speech, a surreal and unsettling event that highlighted vulnerabilities in broadcast signal security. This wasn't just a prank; it was a sophisticated intrusion that left engineers scrambling and the public questioning the integrity of their television. The attack exploited weak physical security at the broadcast tower, proving that even in an age of digital threats, analog vulnerabilities persist.
Bomb Threat Interrupts Sports Broadcast
Sports broadcasts, with their massive, live audiences, are prime targets. In one notable case, a live broadcast of a football game was interrupted by a bomb threat delivered via another hijacked signal. The attacker managed to insert a message claiming a device had been planted, causing panic and requiring immediate broadcast shutdown. This highlights how easily a perceived physical threat can be amplified through digital means, disrupting operations and potentially endangering lives. The speed of response from broadcast engineers and authorities is critical in such scenarios.
Channel 4 News Hijacking
In the UK, Channel 4 News experienced a disruption where a hacker managed to insert a message critical of the government. This incident demonstrated that even established news channels are not immune to signal hijacking, raising serious questions about the security of journalistic integrity in the face of determined adversaries. The implications for public trust are immense when a trusted news source can be so easily manipulated.
Swedish TV Hijacked by Activists
Activists have also utilized broadcast hijacking to push their agendas. A prominent instance saw a Swedish television channel's broadcast interrupted by individuals protesting government policies. They replaced the regular programming with their own message, turning a national broadcast into a platform for dissent. This tactic, while disruptive, underscores the power of the airwaves as a soapbox, however illicitly obtained.
Canadian Politicians Hijacked TV Broadcast
During a political event in Canada, a broadcast was interrupted by images of politicians, seemingly in an attempt to discredit them or spread misinformation. Such attacks during critical political periods can have significant ramifications, influencing public opinion and potentially distorting democratic processes. The manipulation of visual media in a live broadcast is a potent tool for political disruption.
Indian Broadcast Interrupted by Bomb Threat
Similar to the sports broadcast incident, an Indian television channel faced a bomb threat delivered through a hijacked signal. This recurring tactic highlights a persistent vulnerability: the ease with which a false sense of physical danger can be manufactured and disseminated to a wide audience through broadcast systems. The psychological impact of such threats cannot be understated.
NASA TV Interrupted by Unauthorized Broadcast
Even government entities are not immune. NASA TV, the broadcast arm of the U.S. space agency, has experienced interruptions, including instances where unauthorized content was inserted. These breaches are particularly concerning given the sensitive nature of NASA's operations and the importance of maintaining secure communication channels for public outreach and critical missions. Securing broadcast infrastructure is vital for national interests.
Spanish Broadcaster Hacked Live During Football Match
A major Spanish broadcaster was compromised during a live football match, with a hacker inserting their own content. These high-profile events, watched by millions, offer a significant stage for attackers. The interruption during a popular sporting event demonstrates a clear understanding of targeting high-visibility moments for maximum impact, both technically and socially.
Ukrainian TV Hacked to Broadcast Russian Propaganda
In a chilling example of information warfare, Ukrainian television channels have been hacked to broadcast Russian propaganda, particularly during times of conflict. This represents a deliberate attempt to manipulate the narrative and sow discord among the population. It highlights the critical role of broadcast security in maintaining national sovereignty and resisting foreign influence. This is where cybersecurity meets geopolitical strategy.
US TV Network Hacked During Interview
A U.S. television network's live interview was disrupted by a hacker, who inserted offensive content. This incident, occurring on a prominent national network during a seemingly routine segment, underscores how unpredictable and pervasive these signal hijackings can be. It leaves viewers questioning the reliability of the media they consume.
These incidents, while varying in motive and execution, share a common thread: the exploitability of broadcast infrastructure. From simple radio frequency interference to sophisticated network intrusions, the methods to hijack a live TV signal are diverse. The common denominator is a failure in security protocols, either physical or digital, that allows unauthorized access to the transmission chain. For broadcast engineers and cybersecurity professionals, these events offer invaluable, albeit costly, lessons.
Arsenal of the Operator/Analyst
- Software: Signal Analyzers (e.g., Rohde & Schwarz, Keysight), Network Scanners (Nmap), Packet Analyzers (Wireshark), SIEM Solutions (Splunk, ELK Stack) for log analysis. Understanding the tools used by attackers requires knowing the defensive counterparts.
- Hardware: Spectrum Analyzers for RF interference detection, Secure Broadcast Transmission Equipment. Investing in robust hardware is the first line of defense.
- Certifications: While direct broadcast security certifications are niche, expertise in Network Security (CCNP Security, CISSP), RF Engineering, and Incident Response (GIAC Certified Incident Handler - GCIH) are crucial.
- Books: "Broadcast Engineering Handbook," "Network Security Essentials," and deep dives into RF communication principles. For the offensive side, studying books on exploit development and network penetration testing can reveal potential attack vectors.
Veredict of the Engineer: Are These Incidents Preventable?
The short answer is yes, but it requires a multi-layered, vigilant approach that often goes beyond traditional IT security. Broadcast systems operate on different principles than standard IT networks, involving specialized hardware, RF spectrum management, and real-time processing demands. Many older systems may still rely on legacy infrastructure with known vulnerabilities. Implementing robust access controls, segmenting networks, continuously monitoring the RF spectrum for anomalies, and keeping firmware/software updated are non-negotiable. Furthermore, comprehensive incident response plans specifically tailored for broadcast disruptions are vital. The continuous threat of signal hijacking means that broadcast security isn't a project; it's an ongoing, complex operation requiring significant investment and expertise. For organizations looking to enhance their broadcast security posture, engaging specialized broadcast pentesting services can identify critical weaknesses before they are exploited.
Frequently Asked Questions
- What is the most common method used to hijack a live TV broadcast?
- While methods vary, common techniques include unauthorized access to broadcast studios or transmission points, exploiting vulnerabilities in satellite uplinks, or direct RF interference. Sophisticated attacks might involve compromising broadcast automation systems.
- Are there legal consequences for hijacking a TV broadcast?
- Absolutely. Hijacking broadcast signals is illegal in most jurisdictions and can result in severe penalties, including hefty fines and imprisonment, depending on the intent and impact of the disruption.
- How can broadcasters protect themselves from signal hijacking?
- Protection involves a combination of physical security, network segmentation, advanced signal monitoring, encryption where possible, and rigorous access control policies. Regular security audits and penetration testing specifically for broadcast environments are also recommended.
- Can a single individual successfully hijack a major TV broadcast?
- While technically challenging, it's not impossible, especially if targeting older or less secure infrastructure. However, large-scale, sophisticated attacks often involve organized groups with significant technical resources.
The Contract: Securing the Airwaves
You've seen the ghosts in the machine, the moments when the airwaves were stolen. Now, the contract is yours: identify one of these broadcast hijacking incidents (or research another if you prefer) and detail the likely technical vector that was exploited. If you were the head of security for that broadcast station, what three immediate actions would you implement post-incident to prevent a recurrence? Share your analysis and proposed solutions in the comments below. Let's dissect the defenses, or the lack thereof.
For those serious about understanding the frontier between offense and defense in broadcast media, consider exploring resources that delve into RF security and broadcast system architecture. The knowledge gained from platforms like Cybersecurity News and advanced courses on penetration testing can provide a foundational understanding, even if focused on IT networks. The principles of identifying vulnerabilities and understanding attack methodologies are transferable.
Video Resources:
