The digital frontier hums. Not with the promise of gold rushes, but with the relentless buzz of transactions, shimmering promises, and the ever-present whisper of the next big thing. Cryptocurrencies, from the venerable Bitcoin to the ephemeral NFT, are carving out their territory. But beneath the gleam of decentralized dreams, a shadow lurks. Is this the dawn of a new financial era, or just the most elaborate, high-tech con ever devised? At Security Temple, we don't deal in faith; we deal in facts, in code, and in the cold, hard reality of exploit vectors and defense strategies. Today, we’re dissecting the crypto phenomenon, not to preach, but to arm you with the analytical tools to discern signal from noise.

The narrative is often spun with utopian fervor: freedom from central banks, democratized finance, digital ownership finally realized. But every revolution has its casualties, and in the crypto space, the price of naivete can be total financial ruin. This isn't about whether crypto *can* be legitimate; it's about understanding the anatomy of its vulnerabilities, the exploitation tactics employed by bad actors, and what it takes for a *defender* in this Wild West to survive, let alone thrive.
Table of Contents
- Cracking the Blockchain: Unpacking the Core Technology and Its Illusions of Security
- The Hacker's Playground: Cybersecurity Weaknesses in the Crypto Ecosystem
- Anatomy of a Crypto Scam: Tactics, Techniques, and Procedures (TTPs) to Watch For
- Web 3.0: The Next Evolution or a Refined Deception?
- Engineer's Verdict: Is Crypto a Net Positive or a Systemic Risk?
- Operator's Arsenal: Tools for Navigating the Crypto Landscape
- Defensive Workshop: Fortifying Your Digital Assets
- Frequently Asked Questions
- The Contract: Your Next Move in the Crypto Arena
Cracking the Blockchain: Unpacking the Core Technology and Its Illusions of Security
The blockchain. A distributed ledger, immutable, transparent, revolutionary. Or so the whitepapers claim. We've all heard the gospel. Let's put on our auditor's hat and look at the code, the consensus mechanisms, the potential exploits. Bitcoin's proof-of-work, Ethereum's shift to proof-of-stake – each has its attack surface. Understanding these underlying mechanics is not an academic exercise; it's the first line of defense against understanding how these systems can be manipulated. We'll dissect the common misconceptions that paint crypto as inherently safe, highlighting where the vulnerabilities lie, and how even "legitimate" use cases can be compromised by operational security failures. The potential for revolution is real, but so is the potential for exploitation in supply chain, healthcare, or any other industry rushed into adoption without due diligence.
The Hacker's Playground: Cybersecurity Weaknesses in the Crypto Ecosystem
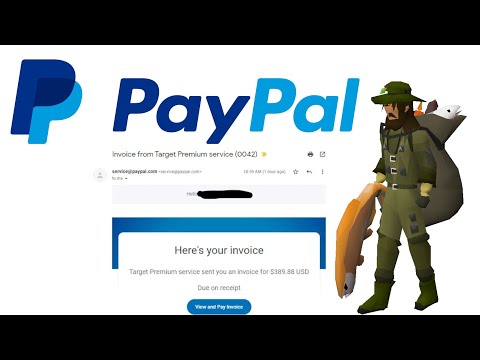
As the digital gold rush accelerates, the attackers are adapting, evolving their methods. This space is a prime target because it often involves untrained users holding significant value. We are going to focus on the practical cybersecurity measures that are not optional, they are survival. This isn't about hoping your password is "Password123!" It's about the non-negotiables: cryptographically secure password management, the crucial implementation of hardware security keys (FIDO2/WebAuthn), the strategic use of air-gapped hardware wallets for significant holdings, and the rigorous application of security best practices. Failure to implement these isn't just negligent; it's an open invitation for phishing attacks, smart contract exploits, and sophisticated rug pulls. These are the real-world risks that can evaporate your carefully cultivated crypto investments overnight.
"The first rule of security is: assume breach. The second rule is: expect the inevitable." - cha0smagick
Anatomy of a Crypto Scam: Tactics, Techniques, and Procedures (TTPs) to Watch For
The crypto landscape is rife with predators. Phishing emails disguised as urgent security alerts, fake ICO promotions promising astronomical returns, Ponzi schemes that drain new investors to pay off early adopters, and the classic pump-and-dump orchestrated on social media. We will break down the TTPs used by these actors. Identifying the patterns is key. Recognizing anonymous founders, unrealistic return promises, high-pressure sales tactics, and unsolicited investment advice are critical skills for any participant. This section is your threat intelligence brief. Knowing the enemy's playbook is the precursor to building effective defenses.
Web 3.0: The Next Evolution or a Refined Deception?
Web 3.0. Decentralized applications (dApps), smart contracts, the metaverse. The narrative promises a user-centric internet, free from corporate gatekeepers. But let's look at the implementation. Smart contracts, once deployed, are often immutable, meaning bugs are permanent vulnerabilities. Decentralized finance (DeFi) offers new avenues for yield farming, but also for flash loan attacks that can destabilize entire protocols. Non-Fungible Tokens (NFTs) are lauded as digital ownership, while often being susceptible to copyright infringement, malicious metadata, and platform vulnerabilities. We will explore the potential, but critically analyze the inherent security challenges and the potential for these new paradigms to simply refine older forms of deception, rather than eliminate them.
Engineer's Verdict: Is Crypto a Net Positive or a Systemic Risk?
From an engineering perspective, the blockchain technology itself is a fascinating innovation with potential applications far beyond speculative finance. However, the current cryptocurrency ecosystem, as it stands, is a high-risk environment. The speculative nature, coupled with widespread security vulnerabilities and the prevalence of sophisticated scams, often overshadows the legitimate technological advancements. For individuals, the risk of loss due to hacks, scams, or market volatility is substantial. For the broader financial system, unchecked growth of unregulated and volatile digital assets presents systemic risks. While Web 3.0 offers a vision of a more decentralized future, its practical implementation is still nascent and fraught with security challenges. Until robust, universally adopted security standards and regulatory frameworks are in place, the crypto space remains a high-stakes gamble. It's not inherently "good" or "bad"; it's a complex technological and financial experiment with a significant attack surface, demanding extreme caution and deep technical understanding from all participants.
Operator's Arsenal: Tools for Navigating the Crypto Landscape
To navigate this complex digital terrain requires more than just instinct; it demands the right tools. For any serious participant in the crypto space, whether for analysis, trading, or security, a well-equipped toolkit is non-negotiable.
- Hardware Wallets: Essential for securing significant crypto holdings. Leading options include Ledger (Nano S Plus, Nano X) and Trezor (Model One, Model T). These are your digital safety deposit boxes.
- Security Keys: For robust two-factor authentication on exchanges and wallets. YubiKey and Google Titan are industry standards.
- Reputable Exchanges: When trading, stick to established platforms with strong security track records and compliant KYC/AML procedures. Research them thoroughly.
- Blockchain Explorers: Tools like Etherscan, Blockchain.com, and Solscan are vital for verifying transactions, analyzing smart contracts, and tracking wallet activity.
- TradingView: For advanced charting and technical analysis, crucial for understanding market dynamics, though remember, technical analysis is not a crystal ball.
- Security Auditing Tools: For developers or those analyzing smart contracts, tools like Mythril, Slither, and Oyente can help identify vulnerabilities.
- Books: "The Bitcoin Standard" by Saifedean Ammous (for understanding the original thesis, albeit with a strong bias), "Mastering Bitcoin" by Andreas M. Antonopoulos (for deep technical dives), and "The Web Application Hacker's Handbook" (for understanding broader web vulnerabilities that can impact crypto platforms).
- Certifications: While not specific to crypto, certifications like the Certified Information Systems Security Professional (CISSP) or Certified Ethical Hacker (CEH) build foundational security knowledge applicable to any digital asset. For advanced blockchain security, specialized vendor certifications are emerging.
Defensive Workshop: Fortifying Your Digital Assets
The best defense is a proactive offense, even when you’re the defender. Here’s how to harden your position in the crypto arena:
- Secure Your Private Keys: This is paramount. Never share your seed phrase or private keys. Store them offline, in multiple secure locations (e.g., a hardware wallet, a fireproof safe, a securely encrypted digital vault with access controls).
- Enable Multi-Factor Authentication (MFA) Everywhere: Use an authenticator app (like Authy or Google Authenticator) or a hardware security key for your exchange accounts, wallets, and email. SMS-based MFA is the weakest form and should be avoided if possible.
- Use Strong, Unique Passwords: Employ a password manager to generate and store complex, unique passwords for every platform.
- Beware of Social Engineering: Be highly skeptical of unsolicited offers, DMs, or emails promising free crypto, guaranteed high returns, or asking for your personal information. Phishing is rampant.
- Verify Smart Contract Deployments: If interacting with new DeFi protocols or dApps, always verify the smart contract address on reputable block explorers and look for audits from trusted security firms. Understand the risks before deploying funds.
- Start Small and Diversify (Cautiously): For beginners, start with small amounts you can afford to lose. Diversify your investments across different assets and platforms, but do so based on rigorous research, not hype.
- Stay Informed on Emerging Threats: Regularly check cybersecurity news sources and crypto-specific security alerts. Knowledge is your shield.
Frequently Asked Questions
Is Bitcoin a scam?
Bitcoin itself is a technological innovation with a decentralised ledger. However, its price is highly speculative, and many schemes built around Bitcoin and other cryptocurrencies are indeed scams. The technology can be used legitimately, but its implementation and trading environment are fraught with risk.
How can I protect myself from crypto scams?
The key is vigilance. Always verify information, be skeptical of unrealistic promises, use strong security measures like hardware wallets and MFA, and never share your private keys or seed phrases. Educate yourself on common scam tactics like phishing, Ponzi schemes, and pump-and-dumps.
Is Web 3.0 safe?
Web 3.0 aims for greater security through decentralization but introduces new complexities and vulnerabilities. Smart contracts can have unpatched bugs, and the overall infrastructure is still evolving. It requires a deep understanding of the underlying technology and associated risks to navigate safely.
What is the biggest risk in cryptocurrency?
The biggest risk is often the loss of funds due to security breaches (hacks, scams, phishing), extreme market volatility leading to significant financial losses, or regulatory uncertainty that can impact asset value and accessibility.
Should I invest in NFTs?
NFTs are highly speculative assets. While they offer potential for digital ownership and utility, they are also susceptible to market manipulation, fraud, intellectual property issues, and platform risks. Invest only what you can afford to lose, and conduct thorough due diligence.
The Contract: Your Next Move in the Crypto Arena
The digital frontier is vast, and the world of cryptocurrency is a labyrinth of innovation, opportunity, and treacherous pitfalls. We've peeled back the layers, examined the code, and exposed the tactics. Now, the contract is yours. Will you dive headfirst into the hype, or will you approach this space with the analytical rigor of a security professional? Your engagement with this domain should be informed, cautious, and built on a foundation of robust security practices. Your digital future depends not on luck, but on diligence.
Now, it's your turn. What specific anomaly have you observed in the crypto market or a related dApp that raised immediate red flags for you? Detail the TTPs you suspect were involved and propose a concrete defense strategy. Let's build that knowledge base, one critical analysis at a time. Drop your findings and strategies in the comments below.