The digital realm is a minefield, and sometimes the most dangerous traps wear the guise of legitimacy. In the shadowy corners of the internet, where illusions are currency and trust is a commodity easily exploited, PayPal phishing scams have evolved. They’re no longer crude attempts at deception; they've become sophisticated operations, weaving themselves into the very fabric of the services we rely on. Today, we're dissecting one such evolving threat, not to teach you how to build it, but to dismantle it, to understand its mechanics so we can erect stronger digital fortresses.
The Deceptive Illusion: How Scammers Exploit Trust
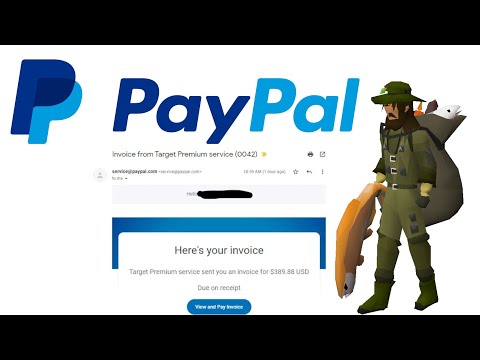
The core of these advanced scams lies in exploiting the inherent trust users place in familiar domains and email addresses. When an invoice arrives from `service@paypal.com`, the immediate internal reaction for most is that it's a legitimate transaction notification. The scammers understand this deeply ingrained trust. They bypass the obvious red flags of a suspicious sender address by using compromised accounts or sophisticated spoofing techniques that can even cause emails to appear as if they were sent directly by PayPal's servers.
The true genius, and the danger, lies in the destination. Instead of directing victims to a fake login page, these scams often use links that, upon initial inspection, appear to lead to the official PayPal website. This is a critical evolution. Users are trained to look for `paypal.com` in the URL. When they see it, their guard drops. The landing page might present a forged login form overlaid on a seemingly legitimate PayPal interface, or it might redirect to a legitimate PayPal page with a subtly altered element or instruction that prompts the user to enter sensitive information under duress or false pretenses.
Anatomy of the Attack: A Blue Team Perspective
Phase 1: Reconnaissance and Infrastructure Setup (The Shadow Play)
Before the first fake invoice is dispatched, the attacker has already done their homework. This phase involves identifying targets, often through breached databases of email addresses or through social engineering tactics. They might also set up infrastructure that aids in spoofing legitimate emails or hosting malicious landing pages that closely resemble PayPal’s authenticated pages. Understanding this initial setup is key; it’s about recognizing the patterns before they manifest as direct threats.
Phase 2: Crafting the Bait (The Illusion of Legitimate Commerce)
This is where the artistry of deception comes into play. Scammers create convincing fake invoices. These aren't just text dumps; they often include:
- Genuine-looking PayPal branding and logos.
- Itemized lists of goods or services, often slightly unusual or with inflated prices.
- A sense of urgency, implying a subscription renewal or an unauthorized purchase that needs immediate attention.
- A sender address that appears legitimate, such as `service@paypal.com` or variations that are hard to distinguish at a glance.
- Links that either redirect through legitimate PayPal domains to a malicious payload, or directly to a carefully crafted phishing page that mimics PayPal’s login portal.
Phase 3: The Delivery Mechanism (The Trojan Horse Email)
The email itself is the delivery system. Sophisticated phishing campaigns leverage techniques to bypass spam filters. This might involve using compromised legitimate email accounts, sending emails within threads that appear to be ongoing conversations, or utilizing HTML formatting that makes the email look identical to a standard PayPal notification.
Phase 4: The Hook and Capture (The Digital Snare)
Once the user clicks the link, the critical moment arrives. If the link leads to a site that looks like PayPal, the user is prompted to log in to "cancel" the transaction or verify their identity. This login attempt is where the credentials are harvested. The attacker captures the username and password, and often, any two-factor authentication codes provided. In more advanced scenarios, the user might be directed to a series of pages designed to extract credit card details, security question answers, or other sensitive PII.
Defensive Strategies: Building Your Digital Sanctuary
Understanding how these scams operate is the first line of defense. However, relying solely on user awareness is a losing battle in the long run. A multi-layered approach is paramount:
1. Vigilance at the Endpoint: Email Security is Paramount
- Advanced Email Filtering: Implement robust email security gateways that utilize AI and machine learning to detect phishing patterns, analyze sender reputation, and scan for malicious links or attachments.
- Domain Verification: Train users to look beyond the display name and hover over links to inspect the actual URL. Be wary of slightly misspelled domains or redirects through unexpected third-party sites.
- SPF, DKIM, DMARC: Ensure your organization's email servers are properly configured with these authentication protocols. A legitimate PayPal domain should always be authenticated.
2. User Education: The Human Firewall
While scammers try to bypass it, the human element remains a critical component of security. Regular, engaging training is essential:
- Phishing Simulations: Conduct regular simulated phishing attacks to gauge user susceptibility and provide immediate, contextual training.
- Awareness Campaigns: Educate users on common phishing tactics, focusing on the evolving nature of these scams, including the use of legitimate-looking invoices and redirects.
- Reporting Mechanisms: Establish clear, easy-to-use channels for users to report suspicious emails. Every reported email is a potential threat identified before it causes damage.
3. Technical Defenses: Fortifying the Perimeter
- Web Filtering and Proxy Servers: Block access to known malicious websites and implement policies that restrict access to categories of sites prone to phishing.
- Endpoint Detection and Response (EDR): Deploy EDR solutions that can detect anomalous behavior on endpoints, which might indicate a compromise resulting from a phishing attack.
- Multi-Factor Authentication (MFA): This is non-negotiable. For any critical service, especially financial ones like PayPal, enforce MFA. Even if credentials are phished, MFA provides a strong barrier against unauthorized access.
4. Incident Response Preparedness: When the Worst Happens
Despite all precautions, breaches can occur. Having a well-defined incident response plan is crucial:
- Clear Protocols: Define steps for identifying, containing, eradicating, and recovering from a phishing-related breach.
- Communication Channels: Establish communication plans for notifying affected users, stakeholders, and regulatory bodies if necessary.
- Post-Incident Analysis: Conduct thorough post-mortem analyses to identify weaknesses and update defensive strategies.
Veredicto del Ingeniero: La Duda Digital es Saludable
The sophistication of these PayPal phishing scams underscores a fundamental truth: in the digital economy, vigilance is not optional, it's a survival skill. The attackers are adapting, leveraging trust and technology against us. This means our defenses must also evolve. Relying on a single layer of security, be it email filters or user awareness alone, is like bringing a knife to a gunfight. True security is built upon multiple layers, interwoven to create a resilient defense-in-depth strategy. The fact that scammers can use PayPal's own services to lend legitimacy to their attacks is a stark reminder that even trusted platforms can be part of an adversary's toolkit. Always question, always verify, and never let your guard down.
Arsenal del Operador/Analista
- Email Security Gateways: Proofpoint, Mimecast, Cisco Secure Email
- Endpoint Security: CrowdStrike Falcon, SentinelOne, Microsoft Defender for Endpoint
- Phishing Simulation Tools: KnowBe4, Cofense, GreatHorn
- Password Managers: LastPass, 1Password, Bitwarden (for users to manage legitimate credentials securely)
- Browser Extensions: Tools that help identify malicious URLs or suspicious website behaviors.
- Books: "The Art of Deception" by Kevin Mitnick, "Applied Network Security Monitoring" by Chris Sanders and Jason Smith.
- Certifications: CompTIA Security+, Certified Ethical Hacker (CEH), Certified Information Systems Security Professional (CISSP) for a foundational understanding of security principles. For a deeper dive into analysis, consider Digital Forensics certifications.
Taller Práctico: Fortaleciendo tus Defensas contra Phishing
Let's put theory into practice. Here’s a basic approach to analyzing an email for signs of phishing, focusing on what an analyst would look for:
-
Examine the Sender Address Thoroughly
Don't just glance at the name. Click to reveal the full email address. Is it `service@paypal.com` or something like `service@pay-pal-secure.com`? Or a free email provider like `paypal-support@gmail.com`? The latter are immediate red flags.
Example of a suspicious sender: "PayPal Support" <paypal.support@mail-updates.net> Legitimate sender: "PayPal" <service@paypal.com> -
Scrutinize the Recipient Address
Is the email addressed to you personally ("Dear John Doe") or generically ("Dear Customer," "Dear User")? Legitimate services often use your name. Although, be aware that some phishing emails can be personalized if they have your name from a previous breach.
-
Hover Over Links (Without Clicking!)
This is crucial. In most email clients, hovering your mouse cursor over a link will display the actual destination URL, usually in the bottom-left corner of your screen or in a tooltip. If the displayed URL doesn't match the expected domain (e.g., it shows `paypal.login-security.net` instead of `paypal.com`), do not click it.
Hovering over "View Invoice" might reveal: http://bit.ly/malicious-link-finder or https://paypal.com.secure-login-portal.com/invoice/12345 -
Analyze the Content for Urgency and Threats
Phishing emails often create a sense of urgency or fear. Phrases like "Your account has been compromised," "Immediate action is required," or "Your payment failed, click here to resolve" are common. Legitimate companies usually provide less alarming ways to address issues.
-
Check for Generic Greetings and Poor Grammar
While scammers are getting better, grammatical errors, awkward phrasing, or overly generic greetings can still be indicators of a non-legitimate message. Compare the tone and style to previous legitimate communications from the company.
-
Verify by Using an Alternate Channel
If you receive a suspicious email about a transaction or account issue, do not use the links provided. Instead, go directly to the company’s official website by typing the URL into your browser or using a trusted bookmark, and log in there to check your account status or recent activity. You can also call their official customer service number.
Frequently Asked Questions (FAQ)
Q1: If an email looks like it's from PayPal and the link goes to paypal.com, is it safe?
Not necessarily. Scammers can use advanced techniques to trick users. The link might redirect through a legitimate PayPal domain to a compromised page, or the page itself might be a convincing replica that appears to be PayPal but is designed to harvest your login details. Always verify critical actions through your browser directly on the official PayPal site.
Q2: What should I do if I accidentally clicked a phishing link?
If you clicked a link but did not enter any information, you are likely safe, but remain vigilant for any unusual account activity. If you entered login credentials, immediately go to the official PayPal website, change your password, and enable multi-factor authentication. If you entered financial information, contact your bank and credit card companies to report potential fraud and monitor your statements closely.
Q3: How do attackers make fake invoices look so real?
They use actual PayPal branding, templates, and sometimes even leverage PayPal's API or features to generate communications that appear to originate from legitimate PayPal services. This makes them incredibly difficult to distinguish from genuine notifications.
Q4: Are there specific browser settings that can help prevent phishing?
Yes, enabling features like Safe Browsing in Chrome or Microsoft Defender SmartScreen in Edge can help by warning you about potentially dangerous websites. However, these are not foolproof and should be used in conjunction with other security practices.
El Contrato: Asegura tu Perímetro Digital
Your mission, should you choose to accept it, is to conduct a personal audit of your own digital accounts. For each critical online service you use (email, banking, social media, or any platform handling sensitive data), ask yourself:
- Is multi-factor authentication enabled? If not, enable it immediately.
- Have I reviewed my account's recent login activity from trusted devices?
- Do I know how to identify a phishing email specific to this service? What are its typical communication styles?
- Have I set up a trusted method (e.g., direct website login, official app) to verify any suspicious communications without using links from the email itself?
The digital shadows are long, and only by actively fortifying your own perimeter can you hope to navigate them safely. Report back with your findings – or better yet, with the new security measures you've implemented.
