The landscape of cyber threats is a battlefield, and complacency is a luxury we cannot afford. Attackers are relentless, their methods evolving with alarming speed. This particular PayPal phishing attack exemplifies a trend towards more sophisticated social engineering tactics, moving beyond crude, easily detectable emails. Understanding the Mechanics is the first step to building impermeable defenses.
The Anatomy of the Phishing Operation
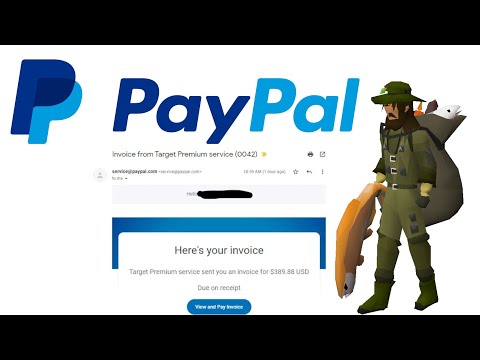
Phase 1: The Deception Vector - Email Craftsmanship
The initial contact isn't a garish, misspelled plea for help. Instead, it’s a meticulously crafted email designed to mimic legitimate PayPal communications. Attackers invest significant effort into:
- Spoofing Sender Addresses: They often use domains that are visually similar to PayPal's official domain, employing subtle misspellings or using subdomains that appear legitimate at first glance.
- Mimicking Official Branding: The email incorporates PayPal's logos, color schemes, and fonts, making it difficult for the untrained eye to distinguish from a genuine message.
- Creating a Sense of Urgency: Phrases like "immediate action required," "security alert," or "unauthorized transaction detected" are used to pressure the recipient into acting without critical thought.
- Personalization (When Possible): While not always present, the most advanced attacks might include your name or other limited personal data, further enhancing credibility.
Phase 2: The Hook - The Malicious Payload
The core of the scam lies in what the email prompts you to do. Common tactics include:
- Links to Fake Login Pages: The email will contain a link that, when clicked, redirects the user to a website that is a near-perfect replica of the PayPal login page. Entering credentials here feeds them directly to the attackers.
- Malicious Attachments: In some cases, the email might contain an attachment disguised as an invoice, a receipt, or a security notification. Opening this attachment could install malware, such as keyloggers or remote access Trojans (RATs), onto the victim's system.
- Requests for Verification: The scammer might ask you to "verify your account" by providing personal information, credit card details, or security codes sent to your phone.
Phase 3: The Exploitation - What Happens When You Fall For It
Should a user succumb to the deception, the consequences can be severe. The attackers aim to leverage the compromised information for financial gain. This typically involves:
- Direct Financial Theft: Accessing the PayPal account to transfer funds to the attacker's own accounts or to make unauthorized purchases.
- Identity Theft: Using the stolen personal information to open fraudulent accounts, apply for credit, or engage in other identity-related crimes.
- Further Compromise: If malware was installed, attackers can gain deeper access to your system, potentially stealing other sensitive data, including banking credentials, or using your machine as a launchpad for further attacks.
Defensive Strategies: Fortifying Your Digital Perimeter
The best defense is a proactive one. Treat every unsolicited communication with suspicion, especially those demanding immediate action or personal information. Here’s how to build your defenses:
Taller Práctico: Fortaleciendo tu Vigilancia contra Phishing
- Verify the Sender: Hover over sender email addresses without clicking. Look for subtle misspellings or unusual domain names. If in doubt, do not engage with the email.
- Never Click Suspicious Links: Instead of clicking links in emails, navigate directly to the official website of the service (e.g., PayPal.com) by typing the URL into your browser.
- Scrutinize Attachments: Be extremely wary of unexpected attachments. If you weren't expecting a file, don't open it. Antivirus software can help, but vigilant human inspection is paramount.
- Enable Two-Factor Authentication (2FA): This is non-negotiable. Even if attackers obtain your password, they will still need your second factor (e.g., a code from your phone) to log in. Ensure 2FA is enabled on your PayPal account and all critical online services.
- Monitor Your Accounts Regularly: Set up transaction alerts for your PayPal account and monitor your bank statements and credit reports for any unauthorized activity.
- Report Phishing Attempts: Most email providers and services like PayPal have mechanisms for reporting phishing emails. Doing so helps them protect others.
Veredicto del Ingeniero: Vigilancia Constante, No Distracción
This PayPal phishing scam isn't a novel attack vector, but its execution highlights the increasing sophistication and psychological manipulation employed by cybercriminals. The ease with which these scams can fool even savvy users underscores the critical need for continuous security awareness training. Relying solely on technical defenses is a losing game; the human element, educated and vigilant, remains the strongest link in the security chain. Investing in robust 2FA and maintaining an active skepticism towards unsolicited digital communications are the bedrock of personal cybersecurity in this evolving threat landscape.
Arsenal del Operador/Analista
- Password Managers: Tools like Bitwarden, 1Password, or LastPass help generate and store strong, unique passwords for every service, mitigating the impact of a single credential compromise.
- Email Security Gateways: For organizations, advanced email security solutions can filter out known phishing attempts and analyze suspicious emails before they reach user inboxes.
- Behavioral Analysis Tools: Advanced threat detection platforms can identify anomalies in user behavior that might indicate a compromised account, even if login credentials were stolen.
- Online Security Courses: Platforms offering courses on cybersecurity awareness and phishing detection can be invaluable. Consider certifications like CompTIA Security+ for a foundational understanding.
Preguntas Frecuentes
- Q: Can PayPal send me an email asking for my password?
A: Never. PayPal will never ask for your password, full credit card number, or bank account details via email. - Q: What should I do if I accidentally clicked a phishing link?
A: Immediately change your password for the affected service and any other service where you use the same password. If you entered financial information, contact your bank or credit card company. - Q: How can I be sure an email is really from PayPal?
A: Always check the sender's email address carefully. Go directly to PayPal's official website by typing the URL into your browser to check for any unread messages or transaction alerts.
El Contrato: Asegura tu CuentaPayPal Hoy Mismo
Your PayPal account is a gateway to your finances. The attackers are patient, they are skilled, and they are waiting for a single mistake. Your contract is to be the vigilant guardian of your own digital assets. Take ten minutes right now. Navigate to your PayPal security settings. Enable two-factor authentication if you haven't already. Review your linked devices and recent activity. This small commitment today is an ironclad defense against the tomorrow’s threats.