The digital storefront: a beacon of commerce, a labyrinth of code. In this shadowy realm, where bits and bytes dance to the tune of profit, lurk those who see not opportunity, but exploit. They are the ghosts in the machine, the ones who can make a thousand-dollar product vanish into thin air, leaving only a phantom order in their wake. Today, we're pulling back the curtain, not just to witness the act, but to understand the anatomy of the deception and, more importantly, to build the fortress that keeps it out.
The illusion of free acquisition is a potent one, often playing on the same vulnerabilities that plague countless e-commerce platforms. It’s not magic; it’s a calculated assault on logic flaws, insecure code, and a trust too readily placed in user input. We're not just talking about a hypothetical scenario. This is real. This is the predatory dance between the attacker and the unprotected cart. The question isn't if your system *could* be exploited, but *how* and *when*.
Table of Contents
- Understanding the Attack Vector: The Price of Blind Trust
- Common Exploitation Techniques in E-commerce
- The Anatomy of a Free Checkout
- Defensive Strategies: Building the Digital Fortress
- Technical Walkthrough: Securing Your Platform
- Arsenal of the Operator/Analyst
- Frequently Asked Questions
- The Contract: Hardening Your E-commerce Perimeter
Understanding the Attack Vector: The Price of Blind Trust
Every transaction, every click, every submitted form is a handshake with your system. For the legitimate customer, it’s a pathway to purchase. For the attacker, it’s a potential handshake with a vulnerability. E-commerce platforms, by their very nature, are complex ecosystems involving user interfaces, payment gateways, inventory management, and shipping logistics. This complexity, while necessary for functionality, also introduces a larger attack surface. The fundamental mistake is often assuming that what happens on the client-side—what the user *sees*—is the authoritative truth. This assumption is the crack in the armor.
Attackers thrive on this discrepancy. If your system trusts the data sent from the browser without rigorous server-side validation, you're essentially inviting them to rewrite the rules of engagement. This is where the "free checkout" exploits often originate: manipulating the data that dictates the price, the quantity, or even the payment method itself before it reaches the secure processing stage.
Common Exploitation Techniques in E-commerce
The digital marketplace is rife with opportunities for those who know where to look. While the specific implementation varies, certain attack patterns emerge repeatedly:
- Price Tampering: Modifying the price parameter in HTTP requests to a lower value (often zero or a negative number) before the order is finalized.
- Quantity Manipulation: Similar to price tampering, but altering the quantity field to excessively high or negative numbers, which can sometimes lead to free items or order cancellation loopholes.
- Coupon/Discount Abuse: Exploiting flaws in coupon code validation logic, enabling the use of expired codes, stacking multiple discounts where they shouldn't apply, or crafting malicious coupon codes.
- Payment Gateway Bypass: Sophisticated attacks that mimic successful payment confirmations without actually processing a payment, often by intercepting and replaying requests or manipulating API responses.
- Logic Flaws in Order Processing: Exploiting business logic errors, such as race conditions during inventory checks or order finalization, to acquire items without proper payment validation.
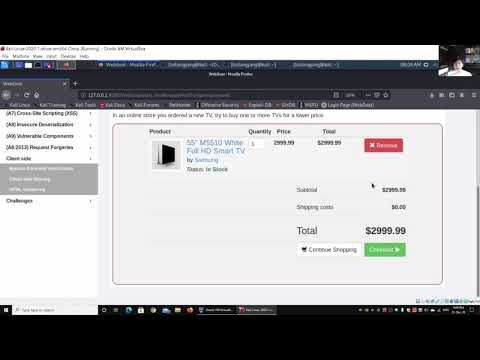
The Anatomy of a Free Checkout
Let's dissect a typical scenario. Imagine a user adds a product to their cart. The website might send a request to the server like this:
POST /cart/update HTTP/1.1
Host: your-ecommerce-site.com
Content-Type: application/json
{
"itemId": "PROD123",
"quantity": 1,
"price": 99.99
}
A naive system would take this `price` value at face value. The malicious actor, however, might intercept this request using a proxy like Burp Suite and alter it:
POST /cart/update HTTP/1.1
Host: your-ecommerce-site.com
Content-Type: application/json
{
"itemId": "PROD123",
"quantity": 1,
"price": 0.00
}
If the server doesn't re-verify the price against its authoritative product database before proceeding to checkout, the item might be listed as free. The subsequent payment gateway interaction might also be similarly manipulated, perhaps by forging a "payment successful" response from a compromised or insecure API.
"The most effective way to defend against attackers is to think like one. Understand their methods, anticipate their targets, and build your defenses accordingly." - cha0smagick
Defensive Strategies: Building the Digital Fortress
Protecting your e-commerce platform requires a multi-layered approach, treating every interaction with suspicion until proven otherwise. The core principle is to shift trust from the client-side to the server-side. Your backend is the ultimate arbiter of truth.
- Server-Side Price and Quantity Validation: Always re-fetch and validate product prices and quantities from your authoritative database on the server before processing an order or payment. Never rely on data submitted by the client.
- Secure Payment Gateway Integration: Implement payment gateway integrations using their recommended server-to-server APIs. Use tokenization and ensure that payment confirmation is received directly from the payment provider, not from the client.
- Input Sanitization and Parameterized Queries: Sanitize all user inputs meticulously to prevent injection attacks (SQLi, XSS) that could be used to manipulate data or application logic. Use parameterized queries for all database interactions.
- Rate Limiting and Anomaly Detection: Implement rate limiting on critical endpoints (like checkout and payment processing) to thwart brute-force and rapid manipulation attempts. Utilize anomaly detection to flag unusual transaction patterns.
- Web Application Firewalls (WAFs): Deploy a robust WAF configured to detect and block common e-commerce attack patterns. Keep its rules updated.
- Regular Security Audits and Penetration Testing: Proactively identify vulnerabilities through frequent security audits and professional penetration testing. Investing in these services is critical for identifying blind spots.
- Secure Session Management: Ensure that session tokens are securely generated, transmitted, and managed to prevent session hijacking.
Technical Walkthrough: Securing Your Platform
Let's illustrate server-side validation. Consider a typical checkout process using a hypothetical Python/Flask backend:
Step 1: Client-Side Request (Insecure Example)
The client sends order details to the `/checkout` endpoint:
# Insecure client-side JavaScript (for illustration only)
formData = {
"items": [
{"productId": "PROD456", "quantity": 2}
],
"shippingAddress": "123 Main St",
"paymentToken": "tok_xxxxxxxxxxxx"
}
fetch('/checkout', {
method: 'POST',
headers: {'Content-Type': 'application/json'},
body: JSON.stringify(formData)
})
Step 2: Vulnerable Server-Side Handler (Illustrative - DONT USE THIS)
This handler naively trusts client-provided pricing.
from flask import Flask, request, jsonify
app = Flask(__name__)
# Dummy product database (should be a real DB)
products_db = {
"PROD456": {"name": "Gadget X", "price": 50.00}
}
@app.route('/checkout_insecure', methods=['POST'])
def insecure_checkout():
data = request.get_json()
total_price = 0
for item in data['items']:
# !!! VULNERABILITY !!! Directly using client-provided price
# This is where an attacker could send price: 0.00 or negative
item_price = item.get('price', products_db[item['productId']]['price']) # Example of using client price if provided
total_price += item_price * item['quantity']
# ... proceed to payment processing with potentially manipulated total_price ...
return jsonify({"message": "Checkout initiated (insecurely)", "total": total_price})
Step 3: Secure Server-Side Handler (Recommended)
This handler fetches prices from the authoritative `products_db`.
from flask import Flask, request, jsonify
app = Flask(__name__)
# Dummy product database (should be a real DB, ideally with inventory checks)
products_db = {
"PROD456": {"name": "Gadget X", "price": 50.00, "stock": 100}
}
@app.route('/checkout_secure', methods=['POST'])
def secure_checkout():
data = request.get_json()
total_price = 0
order_items = []
# 1. Validate and calculate server-side
for item_data in data.get('items', []):
product_id = item_data.get('productId')
quantity = item_data.get('quantity')
if not product_id or not isinstance(quantity, int) or quantity <= 0:
return jsonify({"error": "Invalid item data"}), 400
product_info = products_db.get(product_id)
if not product_info:
return jsonify({"error": f"Product not found: {product_id}"}), 404
# Server-side validation of price and stock
current_price = product_info['price']
current_stock = product_info['stock']
if quantity > current_stock:
return jsonify({"error": f"Insufficient stock for {product_id}"}), 400
item_total = current_price * quantity
total_price += item_total
order_items.append({
"productId": product_id,
"quantity": quantity,
"price_per_unit": current_price,
"subtotal": item_total
})
# 2. Process payment using paymentToken and validated total_price
payment_token = data.get('paymentToken')
shipping_address = data.get('shippingAddress')
if not payment_token or not shipping_address:
return jsonify({"error": "Missing payment token or shipping address"}), 400
# --- Integrate with your Payment Gateway API here ---
# Example: payment_result = payment_gateway.charge(payment_token, total_price)
# Ensure server-to-server communication for this step.
payment_successful = True # Simulate successful payment
if not payment_successful:
return jsonify({"error": "Payment failed"}), 400
# --- End Payment Gateway Integration ---
# 3. Update inventory and finalize order
for item in order_items:
products_db[item['productId']]['stock'] -= item['quantity']
order_id = f"ORD-{hash(str(order_items) + payment_token)[:8]}" # Simple order ID generation
return jsonify({
"message": "Checkout successful!",
"orderId": order_id,
"totalPaid": total_price,
"items": order_items
}), 200
# A simple endpoint to simulate fetching product details
@app.route('/product/', methods=['GET'])
def get_product(id):
return jsonify(products_db.get(id, {"error": "Not found"}))
if __name__ == '__main__':
app.run(debug=True) # In production, use a proper WSGI server and disable debug
This walkthrough highlights the critical shift: data validation and critical logic must reside on the server. Any sensitive calculation like price, quantity, or final total should never be trusted from the client.
Arsenal of the Operator/Analyst
To effectively defend your digital assets, you need the right tools and knowledge. This isn't optional; it's the cost of doing business in the modern world.
- Web Application Proxies: Burp Suite Pro is the industry standard for intercepting, inspecting, and manipulating web traffic. Essential for understanding how attackers interact with your site.
- Code Analysis Tools: Static Application Security Testing (SAST) tools and Dynamic Application Security Testing (DAST) tools can help identify vulnerabilities in your codebase and running application respectively.
- WAF Solutions: Cloudflare, AWS WAF, or ModSecurity offer robust protection against common web attacks. Proper configuration is key.
- Security Monitoring and Logging: Centralized logging (e.g., ELK Stack, Splunk) and Security Information and Event Management (SIEM) systems are vital for detecting suspicious activity in real-time. Consider tools like Wazuh for open-source SIEM capabilities.
- Penetration Testing Services: For an objective assessment, engaging a reputable penetration testing firm is invaluable.
- Books: "The Web Application Hacker's Handbook" (a foundational text) and "Real-World Bug Hunting" offer deep insights into web vulnerabilities.
- Certifications: While not a substitute for experience, certifications like Offensive Security Certified Professional (OSCP), Certified Ethical Hacker (CEH), and CompTIA Security+ demonstrate a commitment to the field and validated knowledge.
Frequently Asked Questions
How can I prevent price manipulation?
Always re-validate product prices on the server-side against your authoritative product database before finalizing any transaction. Never trust prices sent from the client.
Is client-side validation completely useless?
No. Client-side validation provides a better user experience by offering immediate feedback. However, it should never be the *sole* defense. It's purely for usability; server-side validation is for security.
What's the difference between an SQL injection and price tampering?
SQL Injection is about manipulating database queries to extract or modify data. Price tampering is about altering legitimate data fields (like price or quantity) within valid requests to achieve a fraudulent outcome.
Can a Web Application Firewall (WAF) stop all these attacks?
A WAF is a crucial layer of defense, but it's not a silver bullet. It effectively blocks known attack patterns. However, novel exploits or complex business logic flaws might bypass a WAF, necessitating robust server-side validation and regular penetration testing.
The Contract: Hardening Your E-commerce Perimeter
The digital marketplace is a battlefield, and every e-commerce site is a potential target. The tactics used to procure products for free are not acts of genius, but rather the exploitation of known, and often ignored, security principles. The contract between you and your customer is built on trust, but that trust must be fortified by rigorous, server-side security. The question is no longer about *if* you will be tested, but *how prepared* you are when that test arrives.
Your task, should you choose to accept it: Conduct a full security audit of your checkout process. Identify every point where client-side data influences critical calculations. Implement server-side validation for prices, quantities, and applied discounts. Then, go further. Test your payment gateway integration for vulnerabilities and ensure it communicates securely with your backend. This isn't just a technical exercise; it's a commitment to the integrity of your business.
Now, it's your turn. What other vulnerabilities have you seen in e-commerce checkout flows? Share your insights and your defensive code snippets in the comments below. Let's build a stronger, more secure digital frontier, together.
