The digital shadows are growing longer, and the whispers of compromise are becoming a deafening roar. In this high-stakes game of cat and mouse, simply reacting to alerts is a losing strategy. True mastery lies in the proactive hunt, in sniffing out the unseen adversary before they can embed themselves deeper into the network. Welcome to the hunt. Today, we're dissecting Symantec Endpoint Security Complete (SESC) not as a mere AV solution, but as a potent arsenal for the modern threat hunter.
Symantec Endpoint Security Complete, often viewed through the lens of endpoint protection, harbors capabilities that, when wielded correctly, can transform a security operations center (SOC) from a reactive defense line into an offensive shield. This isn't about deploying policies and hoping for the best; it's about leveraging the console's deep telemetry and analytical tools to trace the footprints of sophisticated threats. For those who understand the adversary's mindset, SESC becomes a powerful ally in the relentless pursuit of digital integrity.
Understanding the Threat Hunter's Mandate
Before we dive into the technical intricacies of SESC, let's calibrate our perspective. Threat hunting is an assumption-driven process. It's the art and science of proactively searching through networks and endpoints for signs of malicious activity that have evaded existing security controls. It's not about waiting for an alert; it's about asking questions like: "Are there any unusual PowerShell scripts executing?", "Are there any lateral movement attempts occurring via SMB?", or "Are there any known malicious domains being contacted from unexpected internal hosts?".
This requires a deep understanding of attacker methodologies, common attack chains (like the MITRE ATT&CK framework), and the ability to correlate seemingly disparate pieces of telemetry. The goal is to identify Indicators of Compromise (IoCs) and Indicators of Attack (IoAs) that would otherwise go unnoticed.
Leveraging Symantec EDR for Proactive Detection
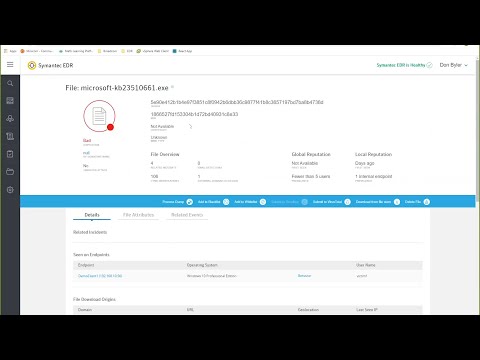
Symantec EDR, the core engine powering many of SESC's threat hunting functionalities, provides a crucial window into endpoint activity. Its strength lies in its ability to collect and analyze vast amounts of data, offering hunters the raw materials they need to piece together complex narratives of compromise.
Telemetry Collection: The Hunter's Binoculars
SESC, through its EDR component, collects a rich dataset from endpoints. This includes:
- Process execution details (parent-child relationships, command line arguments).
- Network connections (source/destination IPs, ports, protocols).
- File system activity (creation, modification, deletion).
- Registry modifications.
- System event logs.
Understanding what data is collected and how it's stored is foundational. For a threat hunter, this data is equivalent to forensic evidence at a crime scene.
Search and Investigate: Following the Digital Trail
The Symantec EDR console offers powerful search capabilities that are the bedrock of any threat hunt. Hunters can query this collected telemetry using a variety of criteria:
- Process Search: Identify specific processes, their command lines, and their parent processes to detect unusual or malicious execution patterns. For instance, searching for `powershell.exe` with specific obfuscated arguments can be a critical step in uncovering script-based attacks.
- Network Connection Search: Pinpoint suspicious connections, especially those to known bad IPs, unusual ports, or internal hosts exhibiting anomalous behavior. Correlating network activity with process execution is key here.
- File Search: Locate files based on name, hash, or creation/modification timestamps, helping to identify dropped malware or configuration files.
- Endpoint Search: Query specific endpoints for detailed activity logs when an initial hypothesis points to a particular machine.
The true power emerges when these searches are combined. A hunter might first search for any instance of `rundll32.exe` executing from a user's Downloads folder, then refine that search to see if those processes made any outbound network connections. This iterative approach is what allows hunters to narrow down vast datasets to actionable intelligence.
Crafting Effective Threat Hunting Queries
Writing effective queries is an art form that blends technical skill with an understanding of attacker tactics. While SESC's interface simplifies much of this, underlying principles remain crucial.
Hypothesis-Driven Hunting
Every hunt should start with a hypothesis. This hypothesis is often derived from threat intelligence, observed attack trends, or anomalies detected in system behavior. For example:
- Hypothesis: An attacker is using PowerShell for initial foothold and lateral movement.
- Hunt Strategy: Search for unusual PowerShell execution patterns, such as encoded commands, download cradles, or execution from non-standard directories. Look for PowerShell processes that initiate network connections to external IPs.
Leveraging MITRE ATT&CK
The MITRE ATT&CK framework is an invaluable companion for threat hunters. By mapping potential attacker techniques to specific data sources and detection methods within SESC, hunters can build more robust and comprehensive searches. For example:
- ATT&CK Technique: T1059.001 - PowerShell
- SESC Telemetry: Process execution, command line arguments.
- Hunt Query Idea: Search for PowerShell executions with base64 encoded commands or suspicious download/execution cmdlets.
Example Hunt Scenario: Detecting Persistence via Scheduled Tasks
Let's walk through a hypothetical hunt for persistence mechanisms using scheduled tasks.
- Hypothesis: An adversary has created a malicious scheduled task to maintain persistence.
- Action: Navigate to the Symantec EDR console. Initiate a search within the "Events" or "Process" data sets.
- Query: Look for instances of
schtasks.exebeing executed, particularly with parameters that create, modify, or query tasks. A refined query might look for `schtasks.exe` command lines containing `/create` or `/change`. - Analysis: Examine the command lines used. Are there any unusual executables being scheduled to run? Are the tasks set to run at unusual intervals or under privileged accounts without clear justification?
- Corroboration: If a suspicious task is found, investigate the executable it's scheduled to run. Use SESC to analyze its properties, hash, and any network connections it makes.
Beyond the Console: Integrating Threat Intelligence
While SESC provides a powerful platform, its effectiveness is amplified when integrated with external threat intelligence feeds. Indicators of Compromise (IoCs) such as malicious IP addresses, domain names, file hashes, and URLs, can be ingested into SESC to automate the detection of known threats. This allows hunters to focus on novel or previously unseen adversary techniques.
Veredicto del Ingeniero: SESC as a Threat Hunter's Toolkit
Symantec Endpoint Security Complete, powered by its robust EDR capabilities, is far more than just an endpoint protection solution. For the dedicated threat hunter, it’s a highly capable platform for proactive detection and investigation. Its strength lies in its deep telemetry, flexible search queries, and the ability to integrate threat intelligence.
Pros:
- Extensive telemetry collection.
- Powerful search and investigation interface.
- Integration with threat intelligence feeds.
- Can be a significant force multiplier for SOC teams.
Cons:
- Requires skilled personnel to leverage fully.
- Can be resource-intensive depending on configuration.
- Understanding the underlying data and attack chains is paramount.
Verdict: Essential for organizations serious about moving beyond reactive security. Investing in the training and expertise to effectively utilize SESC EDR for threat hunting will yield significant returns in early threat detection and incident containment.
Arsenal del Operador/Analista
- Endpoint Detection and Response (EDR): Symantec Endpoint Security Complete (SESC)
- Threat Intelligence Platforms (TIPs): MISP, ThreatConnect
- Behavioral Analysis Tools: SIEM solutions, custom scripting (Python with libraries like `pandas`, `yara`).
- Frameworks: MITRE ATT&CK, Cyber Kill Chain.
- Books: "The Practice of Network Security Monitoring" by Richard Bejtlich, "Threat Hunting with FOCA" (Focus on finding specific threat actor tactics).
- Certifications: GIAC Certified Incident Handler (GCIH), Certified Threat Hunting Professional (CTHP).
Taller Práctico: Fortaleciendo la Detección de Ejecución Maliciosa
- Objective: Configure SESC to better detect anomalous process execution.
- Step 1: Policy Review. Navigate to your SESC policy settings. Ensure that advanced process monitoring and command-line logging are enabled. Verify that telemetry collection for process events is set to the highest available level.
- Step 2: Custom Intrusion Detection Rules. Explore the possibility of creating custom detection rules within SESC or your connected SIEM. For example, create a rule that alerts on any `powershell.exe` execution originating from a web server's IIS logs or any `cmd.exe` spawning `powershell.exe` without administrative privileges.
- Step 3: Baseline Normal. Take time to understand what "normal" process execution looks like on your endpoints. This baseline is crucial for identifying deviations that might indicate malicious activity. Document common processes, their typical parent-child relationships, and command-line arguments.
- Step 4: Integrate with SIEM. If SESC is integrated with a SIEM, ensure that process execution and network connection logs are being ingested. Develop SIEM correlation rules that leverage this data for more advanced hunting scenarios, such as tracking lateral movement attempts.
Preguntas Frecuentes
Q: How often should threat hunting be performed?
A: Threat hunting should ideally be continuous. However, for organizations with limited resources, scheduled hunts (daily, weekly) based on specific hypotheses or threat intelligence are a practical approach.
Q: Can SESC automate threat hunting?
A: While SESC automates detection of known threats and provides the tools for investigation, true threat hunting requires human intuition and hypothesis generation. Automation assists the hunter, but doesn't replace them.
Q: What are the most critical data points for hunting within SESC?
A: Process execution details (command lines, parent-child relationships), network connections, and file system activity are often the most critical data points for effective hunting.
Q: How can I improve my threat hunting skills?
A: Practice consistently, study adversary tactics and techniques (MITRE ATT&CK), leverage threat intelligence, and participate in capture-the-flag (CTF) events focused on detection and hunting.
El Contrato: Tu Primer Anomaly Hunt Protocol
Your mission, should you choose to accept it, is to design a hunt protocol using Symantec EDR to identify potentially unauthorized remote access tools. Assume an attacker has dropped and executed a portable version of a tool like TeamViewer, AnyDesk, or ScreenConnect without proper IT authorization. Outline the steps, the queries you would run within SESC, and the IoCs you'd be looking for to confirm compromise.
