STRATEGY INDEX
- Introduction: The Mobile Fortress Unleashed
- The Arsenal: 20 Elite Hacking Apps Deconstructed
- 20. Haven: Your Personal Digital Guardian
- 19. NetHunter Store: The Kali Linux Mobile Hub
- 18. DriveDroid: Bootable Drives from Your Pocket
- 17. WiFi Analyzer: Mastering Your Wireless Spectrum
- 16. Orbot: Anonymous Browsing with Tor
- 15. Kali NetHunter: Full Kali Power on Android
- 14. Shodan Mobile: The IoT Search Engine
- 13. USB Cleaver: Windows Credential Extractor
- 12. NetCut: Wi-Fi Network Control
- 11. Hackode: The Ethical Hacker's Toolkit
- 10. AndroDumpper: WPS Vulnerability Tester
- 9. dSploit: Comprehensive Mobile Pentesting Suite
- 8. Nessus: Advanced Vulnerability Scanner
- 7. WiFi WPS WPA Tester: Router Security Assessment
- 6. cSploit: All-in-One IT Security Toolkit
- 5. Nmap: The Ultimate Network Mapper
- 4. Fing: Network Device Discovery and Security
- 3. Hacker's Keyboard: PC-Grade Input on Mobile
- 2. DroidSheep: Session Hijacking Analysis
- 1. zANTI: Mobile Network Penetration Testing
- Comparative Analysis: Mobile Pentesting Suites vs. Individual Tools
- The Engineer's Verdict: Mobile Pentesting in the Modern Landscape
- Frequently Asked Questions
- About The Cha0smagick
- Mission Debrief: Your Next Steps
Introduction: The Mobile Fortress Unleashed
The digital frontier is no longer confined to desktop workstations. Today's sophisticated threats, and conversely, today's most effective defenses, often reside in our pockets. Ever wondered how elite operators leverage their smartphones for advanced reconnaissance, network analysis, and vulnerability assessment? This dossier breaks down the 20 indispensable applications transforming your mobile device into a formidable ethical hacking platform. We'll dissect each tool, understand its core functionality, and illustrate its strategic value in the modern cybersecurity landscape. Prepare to upgrade your mobile arsenal.
The Arsenal: 20 Elite Hacking Apps Deconstructed
This section meticulously details each application, transforming a simple list into a comprehensive technical briefing. We move beyond mere descriptions to explore the 'how' and 'why' behind each tool's efficacy for ethical hackers and security professionals.
20. Haven: Your Personal Digital Guardian
Developed with insights from Edward Snowden and the Guardian Project, Haven is more than an app; it's a sophisticated mobile security system. By leveraging your phone's onboard sensors—camera, microphone, accelerometer—Haven transforms your device into a motion and sound detector. Upon detecting an anomaly, it can trigger alerts, record audio or video, and send secure notifications. Its strategic value lies in providing an affordable, portable, and discreet surveillance solution for physical security, safeguarding sensitive locations or assets.
- Core Functionality: Sensor-based anomaly detection and alerting.
- Strategic Use Case: Physical security monitoring, secure room surveillance, asset protection.
- Developer: Guardian Project & Snowden Associates.
19. NetHunter Store: The Kali Linux Mobile Hub
The NetHunter Store is the official repository for tools designed to augment Kali NetHunter, the premier mobile penetration testing platform for Android. It provides a curated selection of applications specifically designed for network analysis, vulnerability scanning, and exploit development, all optimized for mobile execution. Think of it as a specialized app store for offensive and defensive security operations on the go, ensuring you have the right tools readily available in the field.
- Core Functionality: Distribution of Kali NetHunter-compatible security tools.
- Strategic Use Case: Accessing and deploying specialized mobile pentesting utilities.
- Platform: Associated with Kali Linux.
18. DriveDroid: Bootable Drives from Your Pocket
DriveDroid revolutionizes system recovery and OS installation by allowing your Android device to function as a bootable USB drive. It supports numerous Linux distributions and can even boot from disk images stored on your phone. This capability is invaluable for IT professionals and security analysts who need rapid system deployment, forensic imaging, or the ability to run specialized live OS environments without carrying physical media.
- Core Functionality: Emulating USB bootable drives from ISO/IMG files.
- Strategic Use Case: OS installation, system recovery, forensic live boot environments.
- Compatibility: Supports various Linux distros and Windows installers.
17. WiFi Analyzer: Mastering Your Wireless Spectrum
Understanding and optimizing Wi-Fi networks is fundamental. WiFi Analyzer provides a clear visualization of your surrounding wireless environment. It maps Wi-Fi channels, measures signal strength, and identifies potential interference sources. For penetration testers, this tool is crucial for identifying weak access points, understanding network congestion, and planning Wi-Fi-based attacks or defenses. It helps in selecting the optimal channel for a more robust and secure wireless connection.
- Core Functionality: Wi-Fi channel analysis, signal strength mapping, interference detection.
- Strategic Use Case: Wi-Fi network assessment, signal optimization, identifying rogue APs.
- Value Add: Enhances Wi-Fi performance and security diagnostics.
16. Orbot: Anonymous Browsing with Tor
Orbot acts as a proxy that encrypts your internet traffic using the Tor network, effectively anonymizing your online activity and masking your IP address. It routes your traffic through multiple volunteer-operated servers, making it extremely difficult to trace. Essential for maintaining privacy, bypassing censorship, and conducting reconnaissance without revealing your origin, Orbot is a cornerstone for any privacy-conscious operative.
- Core Functionality: Encrypts and routes traffic through the Tor network.
- Strategic Use Case: Anonymous browsing, bypassing geo-restrictions and censorship, privacy protection.
- Technology: Powered by The Onion Router (Tor).
15. Kali NetHunter: Full Kali Power on Android
Kali NetHunter is the definitive mobile penetration testing platform, bringing the entire Kali Linux ecosystem to your Android device. It supports advanced attacks, including USB HID keyboard emulation (acting as a keyboard), and features a custom kernel for enhanced Wi-Fi capabilities. For field security professionals, NetHunter offers unparalleled power, allowing for comprehensive network analysis, vulnerability exploitation, and digital forensics directly from a smartphone or tablet.
- Core Functionality: Full Kali Linux integration on Android devices.
- Strategic Use Case: Mobile penetration testing, advanced Wi-Fi attacks, digital forensics.
- Key Feature: Support for USB HID keyboard attacks.
14. Shodan Mobile: The IoT Search Engine
Shodan is renowned as the "search engine for the Internet of Things." Its mobile counterpart allows you to query Shodan's vast database of internet-connected devices directly from your phone. Discovering exposed devices, understanding the scope of potential attack surfaces, and identifying vulnerabilities in IoT ecosystems is critical. Shodan Mobile provides this intelligence, highlighting the urgent need for robust IoT security measures.
- Core Functionality: Search and discover internet-connected devices and services.
- Strategic Use Case: IoT device reconnaissance, attack surface analysis, vulnerability identification.
- Impact: Underscores the importance of securing connected devices.
13. USB Cleaver: Windows Credential Extractor
USB Cleaver is a potent tool designed for post-exploitation scenarios on Windows systems. When plugged into a compromised machine, it silently gathers sensitive information, including stored passwords, Wi-Fi keys, browser credentials, and other critical data. Its primary value is in rapid data exfiltration and privilege escalation within a target network, making it a key asset for red team operations.
Advertencia Ética: La siguiente técnica debe ser utilizada únicamente en entornos controlados y con autorización explícita. Su uso malintencionado es ilegal y puede tener consecuencias legales graves.
- Core Functionality: Extracts credentials and sensitive data from Windows systems.
- Strategic Use Case: Post-exploitation data gathering, credential harvesting.
- Target Systems: Windows OS.
12. NetCut: Wi-Fi Network Control
NetCut offers granular control over devices connected to your local Wi-Fi network. It allows you to view all connected clients and disconnect unauthorized or suspicious devices with a single tap. This is invaluable for network administrators and security personnel seeking to prevent unauthorized access, manage bandwidth, or isolate potentially compromised devices on a network.
- Core Functionality: Network discovery and device disconnection (ARP spoofing).
- Strategic Use Case: Unauthorized device blocking, network access control, bandwidth management.
- Requirement: Requires root access on Android.
11. Hackode: The Ethical Hacker's Toolkit
Hackode consolidates a suite of essential hacking tools into a single, convenient mobile application. It encompasses functionalities for reconnaissance, network scanning, vulnerability analysis, and even includes Google Dorking capabilities for uncovering hidden information. Its integrated approach streamlines the workflow for ethical hackers, providing quick access to fundamental tools for initial phases of a security assessment.
- Core Functionality: Collection of reconnaissance, scanning, and security feed tools.
- Strategic Use Case: Initial information gathering, security assessment planning.
- Key Feature: Integrated Google Dorking functionality.
10. AndroDumpper: WPS Vulnerability Tester
AndroDumpper is designed to test the security of Wi-Fi networks, specifically targeting routers with WPS (Wi-Fi Protected Setup) enabled. By attempting to exploit vulnerabilities in the WPS protocol, it can potentially reveal the network's password. This tool is critical for ethical hackers assessing the security posture of wireless networks against common Wi-Fi attack vectors.
Advertencia Ética: La siguiente técnica debe ser utilizada únicamente en entornos controlados y con autorización explícita. Su uso malintencionado es ilegal y puede tener consecuencias legales graves.
- Core Functionality: Tests Wi-Fi network security via WPS vulnerability exploitation.
- Strategic Use Case: Wireless network security assessment, WPS PIN brute-forcing.
- Target: Routers with WPS enabled.
9. dSploit: Comprehensive Mobile Pentesting Suite
dSploit is a powerful, all-in-one network analysis and penetration testing suite for Android. It offers a wide array of features, including network mapping, vulnerability scanning, man-in-the-middle (MITM) attacks, password sniffing, and exploit execution. Its comprehensive nature makes it a highly effective tool for deep network assessments and understanding complex attack scenarios from a mobile platform.
- Core Functionality: Network analysis, MITM attacks, vulnerability scanning, exploit execution.
- Strategic Use Case: In-depth network penetration testing, exploitation simulation.
- Requires: Root access for full functionality.
8. Nessus: Advanced Vulnerability Scanner
Nessus, developed by Tenable, is a widely respected vulnerability scanner used for comprehensive network security assessments. While typically run on desktops, mobile access through this app allows for on-the-go monitoring and initial scans. It identifies thousands of known vulnerabilities, misconfigurations, and compliance issues across operating systems, devices, and applications, forming a critical part of any robust vulnerability management program.
- Core Functionality: Comprehensive vulnerability and misconfiguration scanning.
- Strategic Use Case: Network-wide vulnerability assessment, compliance auditing.
- Reputation: Industry-standard security scanner.
7. WiFi WPS WPA Tester: Router Security Assessment
Similar to AndroDumpper, this application specializes in testing the security of Wi-Fi networks by targeting WPS vulnerabilities. It attempts to connect to WPS-enabled routers, effectively assessing the strength of the wireless security protocol. The app generates detailed reports, aiding in the identification and remediation of weak points in Wi-Fi networks.
Advertencia Ética: La siguiente técnica debe ser utilizada únicamente en entornos controlados y con autorización explícita. Su uso malintencionado es ilegal y puede tener consecuencias legales graves.
- Core Functionality: Tests Wi-Fi WPS security and attempts WPA/WPA2 connection.
- Strategic Use Case: Wireless security auditing, identifying weak router configurations.
- Output: Detailed security reports.
6. cSploit: All-in-One IT Security Toolkit
cSploit is an advanced IT security toolkit that provides a comprehensive suite of features for network mapping, vulnerability scanning, and exploit execution. It includes modules for cracking Wi-Fi passwords, performing man-in-the-middle attacks, and analyzing network traffic. Its modular design allows security professionals to tailor their assessment based on the specific needs of the target environment.
- Core Functionality: Network mapping, vulnerability scanning, MITM attacks, Wi-Fi password cracking.
- Strategic Use Case: Comprehensive network security assessment, exploit development.
- Modularity: Allows for customized security testing workflows.
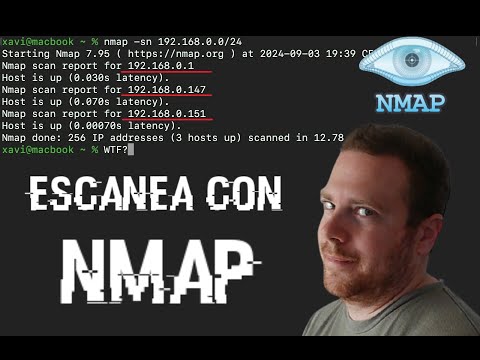
5. Nmap: The Ultimate Network Mapper
Nmap (Network Mapper) is a foundational tool in cybersecurity. This mobile version allows you to discover hosts and services on a network, identify open ports, detect operating systems, and probe for vulnerabilities. Its versatility and power make it indispensable for network administrators, security analysts, and penetration testers for mapping network topologies and understanding the attack surface.
- Core Functionality: Network discovery, port scanning, OS detection, service version detection.
- Strategic Use Case: Network inventory, security auditing, vulnerability assessment.
- Status: De facto standard for network mapping.
4. Fing: Network Device Discovery and Security
Fing provides a user-friendly interface for discovering all devices connected to a network. It offers detailed information about each device, including its IP address, MAC address, and manufacturer. Crucially, Fing can detect unauthorized devices and alert you, making it an excellent tool for maintaining network integrity and identifying potential intrusions or rogue devices.
- Core Functionality: Network scanning, device identification, unauthorized device detection.
- Strategic Use Case: Network monitoring, asset management, intrusion detection.
- Alerting: Proactive alerts for suspicious devices.
3. Hacker's Keyboard: PC-Grade Input on Mobile
For many command-line tools and remote administration tasks, a full PC keyboard layout is essential. Hacker's Keyboard emulates this on your mobile device, providing crucial keys like Ctrl, Alt, Esc, arrow keys, and function keys (F1-F12). This significantly enhances usability when interacting with terminal-based applications, SSH clients, or remote desktop environments directly from your smartphone.
- Core Functionality: Provides a full PC-style keyboard layout on mobile.
- Strategic Use Case: Enhanced usability for command-line tools, SSH, remote desktop.
- Key Feature: Includes special keys like Ctrl, Alt, Tab, and arrow keys.
2. DroidSheep: Session Hijacking Analysis
DroidSheep is a security tool focused on testing web application security against session hijacking. It operates by intercepting web session cookies transmitted over a network, allowing an attacker to potentially hijack a user's active session. This highlights the critical importance of using secure connections (HTTPS) and implementing robust session management techniques to prevent unauthorized access to user accounts.
Advertencia Ética: La siguiente técnica debe ser utilizada únicamente en entornos controlados y con autorización explícita. Su uso malintencionado es ilegal y puede tener consecuencias legales graves.
- Core Functionality: Intercepts and captures web session cookies.
- Strategic Use Case: Testing web application security, demonstrating session hijacking risks.
- Vulnerability Focus: Session cookie security and HTTPS enforcement.
1. zANTI: Mobile Network Penetration Testing
Developed by Zimperium, zANTI is a comprehensive mobile penetration testing toolkit. It allows security professionals to simulate advanced network attacks, conduct vulnerability assessments, and generate detailed reports on network security posture. From Wi-Fi analysis and man-in-the-middle attacks to vulnerability scanning, zANTI consolidates essential offensive security capabilities into a powerful mobile application, making it the top-tier choice for on-the-go pentesting.
- Core Functionality: Network assessment, Wi-Fi analysis, MITM attacks, vulnerability scanning.
- Strategic Use Case: Comprehensive mobile penetration testing, security posture evaluation.
- Reporting: Generates detailed security assessment reports.
Comparative Analysis: Mobile Pentesting Suites vs. Individual Tools
The landscape of mobile hacking tools presents a dichotomy: comprehensive suites like zANTI and Kali NetHunter versus specialized, single-purpose applications like Nmap or WiFi Analyzer. Suites offer the advantage of consolidation, streamlining workflows and providing a broad range of capabilities in one package. They are ideal for rapid, on-site assessments where diverse functionalities are needed simultaneously.
However, individual tools often provide deeper functionality, finer control, and more specialized features within their niche. For instance, while a suite might offer basic Wi-Fi analysis, a dedicated app like WiFi Analyzer might provide more granular control over channel selection and interference mapping. Furthermore, the legality and ethical implications of certain tools (like those involved in direct credential extraction or session hijacking) demand careful consideration regardless of whether they are part of a suite or standalone. The optimal strategy often involves leveraging both: using a robust suite for broad assessments and deploying specialized tools for in-depth analysis of critical areas.
The Engineer's Verdict: Mobile Pentesting in the Modern Landscape
The proliferation of powerful, pocket-sized tools has democratized advanced security testing, but it has also amplified the need for stringent ethical guidelines and legal compliance. These applications are not mere toys; they are sophisticated instruments capable of revealing critical vulnerabilities. As an engineer, my verdict is clear: mastery of these mobile tools is no longer optional for serious cybersecurity professionals. They enable rapid response, field-based assessments, and a deeper understanding of the attack surface in environments where traditional tools are impractical. However, their power mandates responsibility. Always operate within legal boundaries, obtain explicit authorization, and prioritize defensive security knowledge above all else.
Frequently Asked Questions
- Can I use these apps on any smartphone?
- Are these tools legal to use?
- How do I get started with mobile penetration testing?
- What's the difference between ethical hacking and malicious hacking?
Most of these applications are designed for Android. Some, especially those requiring deep system access or specific kernel modifications (like Kali NetHunter), may require root access or specific device compatibility. Always check the app's requirements.
The tools themselves are legal to possess and use. However, using them to access, scan, or attack systems without explicit, written authorization is illegal and unethical. Their purpose is educational and for authorized penetration testing.
Start by thoroughly understanding the ethical and legal framework. Then, begin with tools like WiFi Analyzer and Nmap in your own home network. Progress to more complex tools like Kali NetHunter or zANTI within a controlled lab environment. Continuous learning and practice are key.
Ethical hacking is performed with permission to identify vulnerabilities and improve security. Malicious hacking (black hat hacking) is illegal, unauthorized, and aims to exploit vulnerabilities for personal gain or to cause harm. The intent and authorization are the defining factors.
About The Cha0smagick
The Cha0smagick is a seasoned digital operative and polymathematics engineer, steeped in the trenches of cybersecurity and software development. With a pragmatic, analytical approach forged through countless audits and engagements, he transforms complex technical challenges into actionable intelligence and robust solutions. This dossier is a product of his relentless pursuit of knowledge and his commitment to empowering fellow digital explorers.
Mission Debrief: Your Next Steps
You've now been equipped with the intelligence on 20 powerful mobile hacking applications. The knowledge has been imparted; the tools are at your disposal. But intelligence without action is inert.
Your Mission: Execute, Analyze, and Secure
Your next operational phase is critical:
- Deploy & Practice: Select 2-3 tools from this list that align with your current learning objectives. Set up a secure, isolated lab environment (e.g., using virtual machines or a dedicated test network). Practice their functionalities rigorously.
- Document Findings: Treat every test as a mini-engagement. Document your steps, observations, potential vulnerabilities discovered, and mitigation strategies. This builds critical analytical and reporting skills.
- Share Intelligence (Responsibly): If this blueprint has significantly enhanced your understanding or provided actionable insights, disseminate it. Share this knowledge within your professional networks, forums, or teams. An informed community is a more resilient community.
Your feedback is vital intelligence. What other mobile security tools or techniques warrant deep dives? Which of these apps surprised you the most? Engage in the debriefing process by leaving your insights, questions, and mission reports in the comments below. Let's refine our collective operational effectiveness.
For a quick reference, download the Pro Hacker's Cheat Sheet summarizing these tools.
To further enhance your operational security and explore digital asset management, consider establishing a secure foundation. For a robust and versatile platform to manage your digital assets, explore opening an account on Binance and leverage their ecosystem.
Trade on Binance: Sign up for Binance today!