The digital frontier is a treacherous place, a labyrinth of encrypted data and forgotten keys. In this realm, forgotten passwords are the ghosts in the machine, guarding fortunes or locking away access to vital resources. Today, we’re not just talking about finding lost keys; we’re dissecting the anatomy of a potential recovery, a controlled demolition of a cryptographic lock. The target: a Bitcoin wallet. The weapon: Hashcat.
Many view Bitcoin wallets as impregnable vaults. And for the average user, they are. Most rely on strong, unique passwords, a solid defense against casual snooping. But for those who understand the underlying mechanics, for those who operate on the bleeding edge of digital forensics and security analysis, every lock has a key, or at least a methodology to find it. This isn't about illegal access; it's about understanding the attack vectors to build stronger defenses. It's about ethical hacking, penetration testing, and the relentless pursuit of knowledge. If you're serious about cybersecurity, understanding how systems can be compromised is paramount. This deep dive into brute-forcing Bitcoin wallets with Hashcat is not for the faint of heart, nor for the malicious. It's for the analyst, the defender, the security enthusiast who needs to know the enemy’s playbook.
Table of Contents
- Understanding Bitcoin Wallet Security
- The Role of Hashcat in Cryptographic Attacks
- Essential Tools for Wallet Recovery
- Step-by-Step Guide to Brute-Forcing
- Mitigation Strategies and Best Practices
- FAQ: Bitcoin Wallet Brute-Forcing
- The Contract: Securing Your Digital Fortune
Understanding Bitcoin Wallet Security
At its core, a Bitcoin wallet is essentially a digital key pair: a public key and a private key. The public key is used to generate your Bitcoin address, which you can share freely. The private key, however, is the golden ticket. It’s what allows you to spend your Bitcoins. If someone gains access to your private key, they control your funds. For most desktop wallets, like Bitcoin Core, this private key is protected by a password, which is then used to encrypt the wallet file (often a `wallet.dat` file).
The encryption employed is typically robust, utilizing industry-standard algorithms like AES. The strength of your wallet's security, therefore, hinges directly on the strength of your chosen password. A weak password, one that is short, common, or easily guessable, becomes the Achilles' heel of an otherwise secure system. This is where the concept of brute-forcing comes into play. It's a trial-and-error method aimed at systematically guessing the correct password.
"The password is the key. Without the right key, the most sophisticated vault is just a metal box." - cha0smagick paraphrase of countless security doctrines.
The Role of Hashcat in Cryptographic Attacks
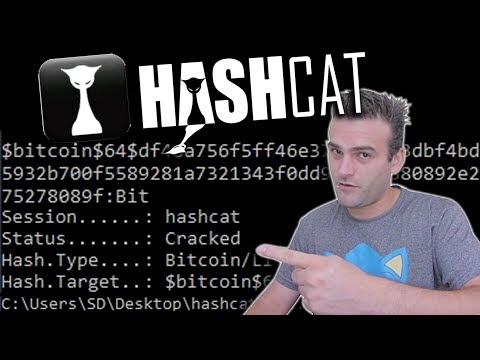
Hashcat is not your average password-cracking tool. It's a highly advanced and versatile password recovery utility, renowned for its speed and ability to leverage both CPU and GPU power. It operates by taking a hash (a one-way cryptographic function result) and attempting to find the original plaintext password that generated that hash. In the context of Bitcoin wallets, the process involves extracting the hash of the wallet's encryption password and then feeding it to Hashcat.
Hashcat supports a staggering array of hash types, and for Bitcoin wallet files, specific conversion tools and Hashcat modes are required. Its true power lies in its optimization for parallel processing, allowing it to test millions, even billions, of password combinations per second, especially when using powerful GPUs. This makes it a formidable tool for security professionals when authorized for penetration testing or auditing, and a significant threat if left unaddressed for unprotected wallets.
Essential Tools for Wallet Recovery
To embark on this journey of understanding, you'll need a specific set of tools. Think of this as assembling your forensic kit:
- Hashcat: The primary engine for password recovery. Ensure you have the latest version installed, optimized for your system's hardware (CPU, and especially GPU). Mastering Hashcat's various attack modes (mask, dictionary, brute-force) is crucial. For advanced users looking to refine their techniques and understand the underlying optimizations, consider exploring resources that delve into CUDA or OpenCL programming, as Hashcat heavily relies on these for GPU acceleration.
- Bitcoin2John.py Script: This Python script is vital. It takes your encrypted Bitcoin wallet file (`wallet.dat`) and converts the relevant password hash into a format that Hashcat can understand. You can find this script publicly available, often on code repositories like GitHub. It's a testament to the open-source community that such tools, while potentially dangerous in the wrong hands, are accessible for legitimate security research.
- A Powerful Computing Rig: Brute-forcing is computationally intensive. While it's possible to attempt with a standard CPU, the success rate and time required are drastically improved with one or more high-end GPUs. For serious security analysis or professional pentesting engagements, investing in dedicated hardware or utilizing cloud-based GPU instances is often a necessity.
- Target Wallet File: You'll need an actual encrypted `wallet.dat` file. For ethical testing, this should be a wallet you own and have permission to perform recovery attempts on, or a specifically prepared test file. Never attempt to brute-force a wallet you do not have explicit authorization for.
For those serious about mastering these techniques, investing in professional-grade hardware or cloud GPU access can mean the difference between a successful audit and an impossible task. Tools like **NVIDIA's Tesla or AMD's Radeon Pro series** are often the hardware of choice for dedicated security labs.
Step-by-Step Guide to Brute-Forcing
Let’s walk through the process. Remember, this is for educational purposes on wallets you own and have permission to test.
- Obtain the Bitcoin Wallet File: Locate your `wallet.dat` file. For Bitcoin Core, this is typically found in the Bitcoin data directory on your operating system.
-
Convert the Wallet Hash:
Use the Bitcoin2John.py script to extract the password hash. The command typically looks like this:
python bitcoin2john.py /path/to/your/wallet.datThis script will output a string representing the hash. Save this string to a text file, for example, `wallet.hash`.
-
Prepare Hashcat:
Hashcat requires specific parameters to run effectively. For Bitcoin (and many other wallet types), you'll need to identify the correct "mode" for Hashcat. The mode for Bitcoin `wallet.dat` is typically mode `11300`. The command structure will be:
hashcat -m 11300 wallet.hash /path/to/your/wordlist.txtWhere:
- `-m 11300` specifies the hash type (Bitcoin RPC/wallet.dat).
- `wallet.hash` is the file containing the extracted hash.
- `/path/to/your/wordlist.txt` is a dictionary file containing potential passwords.
For a pure brute-force attack without a dictionary, you would use Hashcat's mask attack capabilities. This is where you define character sets and lengths. For example, to brute-force a 6-digit numeric password:
hashcat -m 11300 -a 3 wallet.hash ?d?d?d?d?d?dHere, `-a 3` signifies a brute-force attack using a mask.
-
Execute the Attack:
Run the Hashcat command. The time it takes will vary dramatically based on password complexity, your wordlist quality (if using dictionary attack), and the power of your GPUs. A simple, short password might be cracked in minutes or hours. A complex, long password could take years, even with powerful hardware. This starkly highlights why strong, unique passwords are non-negotiable.
-
Recover the Password:
If Hashcat finds the password, it will display it. You can then use this password with your `wallet.dat` file to access your Bitcoins. If the attack times out or exhausts all possibilities without success, it means the password is too complex for the chosen attack strategy and time constraints.
For those serious about automating and optimizing such processes, exploring **advanced Hashcat attack vectors** and **custom wordlist generation techniques** is key. Platforms like YouTube host numerous tutorials demonstrating these complex scenarios, offering visual insights that complement the technical documentation available for tools like Hashcat. If you're looking for structured learning, consider **online courses on ethical hacking or digital forensics**; many reputable providers offer modules on password cracking and recovery.
Witness the process in action.
Mitigation Strategies and Best Practices
Understanding how to break into a Bitcoin wallet is a double-edged sword. The primary takeaway should always be about strengthening your own defenses. Here’s how to make your Bitcoin wallet a fortress:
- Use Strong, Unique Passwords: This is the bedrock of your security. Employ a mix of uppercase and lowercase letters, numbers, and symbols. Aim for length, as each additional character exponentially increases the difficulty of brute-forcing. Consider using a password manager to generate and store these complex passwords securely.
- Enable Wallet Encryption: Ensure your wallet is encrypted. Most modern wallet software prompts you to set a password upon creation. Never skip this step.
- Regularly Back Up Your Wallet: While not a direct defense against brute-forcing, a secure backup is your lifeline if your primary wallet is compromised or lost. Store backups offline and in multiple secure locations.
- Consider Hardware Wallets: For significant amounts of Bitcoin, hardware wallets (like Ledger or Trezor) offer a superior level of security. They store your private keys offline, isolated from internet-connected devices, making them extremely difficult to target with software-based attacks like brute-forcing. They often involve PINs and recovery phrases, adding further layers of defense. Investing in a reputable hardware wallet is one of the most effective steps you can take.
- Beware of Malware: Keep your operating system and antivirus software updated. Malware designed to steal wallet files or capture keystrokes can bypass even strong passwords.
The cybersecurity landscape is constantly evolving. Staying informed about the latest threats and best practices is not optional; it's a requirement for anyone holding digital assets. Regularly reviewing your security posture and seeking advice from **certified cybersecurity professionals** can provide invaluable peace of mind.
FAQ: Bitcoin Wallet Brute-Forcing
-
Is it legal to brute-force a Bitcoin wallet?
It is legal to brute-force a Bitcoin wallet if you are the owner of the wallet and have forgotten your password, or if you have explicit, written permission from the owner to perform such an attempt for security auditing purposes. Attempting to brute-force a wallet you do not own or have authorization for is illegal and unethical. -
How long does it take to brute-force a Bitcoin wallet?
The time required varies dramatically. A simple, short password might take minutes to hours on a powerful GPU setup. A complex, long password (e.g., 12+ characters with mixed case, numbers, and symbols) could take centuries with current technology. This is why password strength is paramount. -
Can Bitcoin wallets be cracked without brute-forcing?
While brute-forcing targets the password, other attack vectors exist. These include exploiting vulnerabilities in the wallet software itself, phishing attacks to steal the `wallet.dat` file or private keys, or keylogging malware. This underscores the importance of a layered security approach. -
What is the best tool to brute-force a Bitcoin wallet?
Hashcat is widely considered the most powerful and versatile tool for password recovery, including Bitcoin wallets, due to its speed and optimization for GPUs. However, effective use often requires specialized scripts like `bitcoin2john.py` for hash extraction and a deep understanding of Hashcat's attack modes.
The Contract: Securing Your Digital Fortune
The digital ether is a realm of both immense opportunity and profound risk. We’ve peeled back the layers, not to exploit them, but to understand their resilience. You’ve seen how a Bitcoin wallet, secured by a password, can be targeted through systematic brute-forcing using tools like Hashcat. The power of these tools is undeniable, but their effectiveness is directly proportional to the weakness of the defenses.
Your contract, the unspoken agreement you make with your digital assets, is to protect them with everything you’ve got. This means crafting passwords that are not mere suggestions, but formidable barriers. It means leveraging the strongest available encryption and, when dealing with significant value, arming yourself with hardware wallets. The knowledge exposed here is a weapon. Wield it wisely; use it to build better defenses, not to tear down the walls of others. The true mastery lies not in cracking the code, but in ensuring it never needs cracking in the first place.
Now, analysts, it’s your turn. What are your go-to strategies for strengthening wallet security beyond simple password management? Are there specific Hashcat mask patterns or wordlist generation techniques that you find particularly effective for modern wallet encryption? Share your insights, code snippets, or battle-tested methodologies in the comments below. Let’s build a stronger digital frontier, together.

