The digital shadows are long, and within them, privilege escalation remains the siren song for any operator truly looking to understand a system's underbelly. We're not just patching vulnerabilities; we're dissecting the anatomy of control. Today, we pull back the curtain on sudoedit, a seemingly benign utility, and reveal how it can be twisted into a vector for unbridled root access. This isn't about finding a pre-written script; it's about understanding the mechanics, the memory, and the logic that allows for such a dramatic shift in power.
The Anatomy of a Trusted Command
sudoedit, often wielded by administrators to safely edit files using their preferred editor without needing to run the entire session as root, appears innocuous. It’s designed to provide a controlled environment. However, beneath this veneer of security lies a complex interaction between processes, temporary files, and environment variables. Understanding this interaction is the first step in identifying the cracks.
The core idea, as often seen in sophisticated exploits, revolves around manipulating how the system loads external components or executes code. In this case, the manipulation targets the loading of shared libraries. If we can influence which library gets loaded, and crucially, what code that library executes, we can hijack the intended flow of execution.
Recap: The Library Loading Exploit Concept
The fundamental principle we're exploring is the ability to control the loading of a malicious library. When a program needs functionality it doesn't have internally, it dynamically links to shared libraries. The `dlopen()` function is a cornerstone of this process in many Unix-like systems, allowing programs to load libraries at runtime. By finding a way to trick a privileged process, like one launched via sudoedit, into loading a library we control, we can achieve arbitrary code execution with the privileges of that process – in this case, root.
Debugging the Unseen: Finding the Entry Point
The journey to exploitation is paved with meticulous debugging. We often encounter crashes or unexpected behaviors that, to the uninitiated, seem like mere bugs. But to the trained eye, they are signposts. The process involves delving into the memory space of the target application, scrutinizing its behavior, and identifying points where external input or state can be influenced.
Debug a Different Crash
Sometimes, the most direct path is blocked. Instead of chasing the obvious crash, we pivot. Debugging a seemingly unrelated crash can reveal underlying mechanisms or shared vulnerabilities that are more exploitable. This is where patience and a willingness to explore tangential issues become paramount.
Can We Reach dlopen?
The critical question is whether our attack vector can influence the program's execution path to a point where it invokes `dlopen()` with parameters we can control. This often involves understanding the sequence of operations within the targeted utility and finding a way to inject or modify arguments passed to key functions.
Leveraging Memory Corruption: Offsets and Wrappers
Once we've identified a potential path, memory corruption techniques come into play. Finding accurate memory offsets is a dark art, often requiring advanced debugging tools and a deep understanding of memory layout. Tools like GDB (GNU Debugger) are indispensable.
Using Patterns to Find Offsets
To pinpoint specific memory locations, we might inject unique, patterned data into the program's input. By observing how these patterns are handled or where they end up in memory, we can calculate the precise offsets needed to overwrite critical data structures or return addresses.
Writing NULL Bytes
Null bytes (`\x00`) are often terminators in C-style strings. Overwriting areas with null bytes can truncate strings, bypass security checks, or manipulate data structures in unexpected ways. Understanding where and how to inject these can be crucial for controlling program flow.
Crafting the Attack: Execution Wrappers and Shared Libraries
With offsets and control points identified, the next phase is constructing the payload. This involves two key components: the wrapper script or function that prepares the environment, and the malicious shared library itself.
Create Execution Wrapper sudoenv
A wrapper script, such as sudoenv, can be designed to set up the necessary environment variables or arguments before executing the target command. This wrapper acts as an intermediary, ensuring that when the main program starts, it’s in a state susceptible to our exploit.
Controlling the ni Struct
In the context of library loading, specific data structures often govern how libraries are searched for and loaded. Manipulating these structures, perhaps identified as `ni` in the original research, allows direct control over the loading process. This is where deep knowledge of the operating system's internals becomes a weapon.
Single Step Exploit Code
Developing the exploit code often involves a staged approach. Initial steps might focus on proving basic functionality, like simply executing a benign command from our library. This "single-step" approach allows for iterative debugging and confirmation before attempting more complex operations.
Create Attack Shared Library
The heart of the exploit is the malicious shared library. This `.so` file (Shared Object) contains the code that will be executed. It's typically written in C or C++ and compiled to be loaded dynamically. The `_init` or `constructor` function within a shared library is often the ideal place to hook into execution, as it runs automatically when the library is loaded.
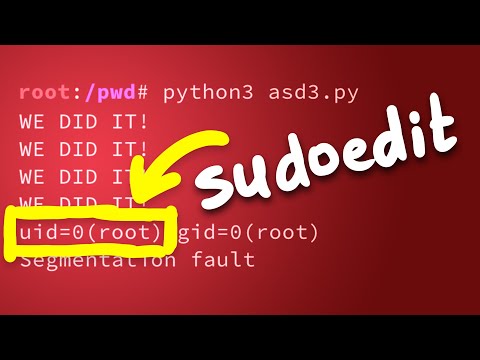
The Moment of Truth: First Successful Exploit?
The culmination of this process is testing the exploit. If all the pieces align – the controlled environment, the correct memory offsets, the crafted shared library – you should witness your injected code execute with root privileges. This often involves observing system calls, file modifications, or process information that confirms the elevated access.
The User vs. Root: Understanding Privilege Boundaries
A critical observation in this type of research is often the distinction between executing as a regular user and executing as root. Many privilege escalation exploits specifically target the elevated permissions granted to root. If the `sudoedit` command itself isn't executed with `sudo`, the exploit might fail because the target process doesn't have the necessary privileges to be compromised in the same way.
This highlights a fundamental security principle: the attack surface and exploitability of a system component can drastically change based on the user's privileges. What is a vulnerability at one privilege level might be harmless at another.
Veredicto del Ingeniero: ¿Vale la pena adoptarlo?
sudoedit, while a utility for safer editing, presents a fascinating case study in how even trusted commands can harbor avenues for escalation. Exploiting it isn't about a flaw in the editor itself, but in the complex interplay of system calls, temporary file handling, and privilege management that underpins its operation. For defenders, this underscores the need for continuous vigilance and a deep understanding of how core utilities interact. For aspiring red teamers, it’s a testament to the fact that no system is inherently secure; robust security is built on understanding and mitigating these intricate interaction points. The key takeaway is that privilege escalation is an art of observing behavior, manipulating context, and exploiting the trust inherent in system design.
Arsenal del Operador/Analista
- Debugging Tools: GNU Debugger (GDB), Valgrind, strace.
- Exploit Development Frameworks: Metasploit Framework (for understanding modules and concepts).
- System Monitoring: `htop`, `ps`, `lsof`.
- Code Editors/IDEs: VS Code, Vim, Emacs.
- Books: "The Shellcoder's Handbook: Discovering and Exploiting Security Holes", "Practical Binary Analysis".
- Certifications: Offensive Security Certified Professional (OSCP) - invaluable for practical exploit development and privilege escalation. Consider also eLearnSecurity's Certified Penetration Tester (eCPPT) for hands-on skills.
Taller Práctico: Simulación de Ataque a Sudoedit (Entorno Controlado)
Este taller simula los pasos conceptuales para un ataque a sudoedit. **ADVERTENCIA**: Ejecuta esto solo en un entorno de laboratorio controlado y aislado. Nunca en sistemas de producción.
-
Preparar el Entorno de Laboratorio: Crea una máquina virtual (VM) con una distribución Linux vulnerable (ej. una versión antigua de Ubuntu o Kali Linux). Asegúrate de tener GDB y las herramientas de compilación (build-essential) instaladas.
-
Identificar el Objetivo: En la VM, intenta ejecutar
sudoedit /etc/passwd. Observa el comportamiento y los procesos iniciados. -
Crear una Biblioteca Maliciosa de Prueba: Escribe un simple programa en C que, al ser cargado, ejecute un comando como root (ej. crear un archivo en
/root). Compílalo como una biblioteca compartida.// malicious_lib.c #include <stdio.h> #include <stdlib.h> #include <unistd.h> #include <sys/types.h> void __attribute__ ((constructor)) exploit_init() { printf("Executing with elevated privileges!\n"); // Example: Create a file in /root FILE *f = fopen("/tmp/pwned_by_root", "w"); if (f) { fprintf(f, "Exploit successful!\n"); fclose(f); printf("Created /tmp/pwned_by_root\n"); } else { perror("Failed to create file"); } // Consider adding a system() call for more complex actions, // but be mindful of security implications and dynamic linking. // system("echo 'Exploited!' > /tmp/exploit_output.txt"); }Compila:
gcc -shared -fPIC -o malicious_lib.so malicious_lib.c -
Identificar la Vulnerabilidad (Simplificado): En un escenario real, necesitarías encontrar un punto donde puedas influir en las variables de entorno (como
LD_PRELOAD) o manipular argumentos que lleven a la carga de tu biblioteca. Para este ejemplo simplificado, asumimos que podemos forzar la carga deLD_PRELOAD. -
Ejecutar el Ataque: Intenta ejecutar
sudoeditconLD_PRELOADapuntando a tu biblioteca maliciosa. Esto puede requerir un wrapper que ajuste el entorno.# Asumiendo que malicious_lib.so está en el directorio actual sudo LD_PRELOAD="./malicious_lib.so" sudoedit /etc/hostsNota: La efectividad de
LD_PRELOADconsudoeditdepende de la configuración desudoersy las variables de entorno permitidas. En setups modernos,sudorestringe fuertementeLD_PRELOADpor defecto. -
Verificar el Resultado: Después de ejecutar el comando, revisa si se creó el archivo
/tmp/pwned_by_root. Si es así, has logrado una ejecución de código con privilegios elevados.
Preguntas Frecuentes
¿Es sudoedit seguro por diseño?
sudoedit está diseñado para ser más seguro que ejecutar un editor directamente con sudo al limitar el alcance de la operación a un archivo específico y usar un mecanismo de copia temporal. Sin embargo, como cualquier software, puede tener configuraciones incorrectas o vulnerabilidades subyacentes que permitan la escalada de privilegios bajo ciertas condiciones.
¿Cómo puedo defenderme contra este tipo de ataque?
La defensa principal implica una configuración estricta de sudoers, limitando las variables de entorno que se pueden pasar (como LD_PRELOAD) y aplicando el principio de mínimo privilegio. Mantener el sistema y las utilidades de sudo actualizadas es crucial.
¿Cuál es la diferencia entre sudoedit y sudo vim file.txt?
sudo vim file.txt ejecuta el editor vim directamente como root, dando acceso completo al sistema de archivos y la capacidad de ejecutar comandos root dentro del editor. sudoedit, por otro lado, crea una copia temporal del archivo, permite editar esa copia con tu editor (incluso si no es sudo), y luego sobrescribe el archivo original con la copia editada, limitando la exposición de privilegios.
¿Qué es LD_PRELOAD?
LD_PRELOAD es una variable de entorno en sistemas Linux y Unix que permite especificar bibliotecas compartidas que deben ser cargadas antes que otras bibliotecas estándar. Se utiliza comúnmente para depuración, análisis de rendimiento o, como en este caso, para la inyección de código malicioso.
El Contrato: Asegura el Perímetro de tus Comandos
Has visto el poder de manipular la ejecución de código a través de comandos de apariencia inocua como sudoedit. Ahora, el contrato está contigo. Tu desafío es tomar este conocimiento y aplicarlo de forma defensiva. Analiza los comandos que usas a diario con `sudo`. ¿Qué variables de entorno son permitidas? ¿Qué procesos se inician y cómo interactúan? Realiza tu propia auditoría de sudoers. ¿Puedes identificar otros puntos ciegos similares en tu entorno de producción o laboratorio? Documenta tus hallazgos y, lo más importante, implementa las contramedidas. El perímetro digital no se protege solo; requiere la astucia y la diligencia de un operador que piensa como un atacante, pero actúa como un guardián.
