The digital ether hums with unseen battles. Every packet traversing the wires, every request hitting a server, is a potential entry point. Understanding common network attacks isn't just about passing a certification; it's about survival in a landscape where a single oversight can cascade into catastrophe. This is less a tutorial and more an autopsy of digital incursions, a dissection of how the lines of code designed to connect us are twisted into weapons, and critically, how to build the walls high enough to withstand the siege. We're not just listing vulnerabilities; we're deconstructing the mindset of an attacker to fortify the defender.
This analysis dissects prevalent network attack vectors that form the bedrock of any comprehensive cybersecurity curriculum, particularly those aligned with the CISSP certification domain. We will explore how these attacks are executed and, more importantly, the robust countermeasures that form the first, last, and every line of defense. For those aiming to cement their expertise, platforms like Skillset.com offer a structured path, but true mastery lies in understanding the underlying mechanics. Over 40,000 candidates across 58 countries have found a more efficient route to certification through such platforms, leveraging unlimited practice questions, readiness scores, and personalized plans to eliminate wasted study time. This article complements that structured approach by providing an attacker's perspective on common threats.
Table of Contents
- Understanding Network Threats
- Denial-of-Service (DoS) and Distributed Denial-of-Service (DDoS) Attacks
- Man-in-the-Middle (MitM) Attacks
- SQL Injection and Cross-Site Scripting (XSS)
- Malware and Ransomware
- Spoofing and Phishing
- Session Hijacking
- Understanding the Attack Chain
- Strategic Countermeasures for Robust Defense
- Implementing Network Segmentation and Firewalls
- Leveraging Intrusion Detection and Prevention Systems (IDPS)
- Data Encryption and Secure Protocols
- Access Control and Authentication Mechanisms
- Security Awareness Training: The Human Firewall
- Engineer's Verdict: Is CISSP Training Worth It?
- Operator/Analyst Arsenal
- Frequently Asked Questions
- The Contract: Securing Your Network Perimeter
Understanding Network Threats
The network is the lifeblood of any modern organization. It's the nervous system connecting endpoints, servers, and the cloud. But this interconnectedness is also its Achilles' heel. Attackers don't need to breach your physical perimeter if they can exploit vulnerabilities within your network protocols, applications, or even your users. The landscape is littered with threats, ranging from subtle manipulations of data to brute-force assaults aimed at incapacitation.
Common network attacks are not just theoretical exercises for whitepapers; they are the daily bread of malicious actors. From the casual script kiddie to sophisticated APTs (Advanced Persistent Threats), the methodologies often rely on exploiting fundamental weaknesses in design, implementation, or human behavior. Understanding these vectors is the first step in building effective defenses. It's about thinking like the adversary, anticipating their moves, and deploying countermeasures that are not only reactive but also proactive.
Denial-of-Service (DoS) and Distributed Denial-of-Service (DDoS) Attacks
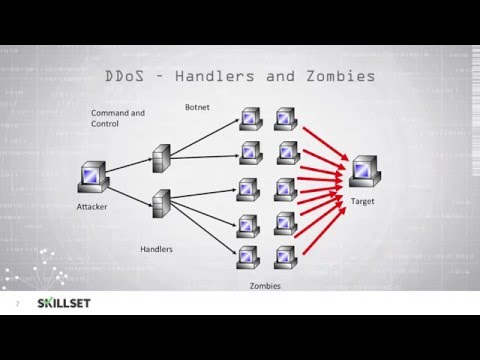
The goal here is simple: overwhelm a target system, service, or network with a flood of internet traffic, rendering it unusable for legitimate users. A DoS attack typically originates from a single source, while a DDoS attack leverages multiple compromised systems (a botnet) to launch a coordinated assault. This isn't about stealing data; it's about disruption, extortion, or creating a smokescreen for other malicious activities.
- Amplification Attacks: Exploiting services like DNS or NTP to send a small request that results in a much larger response directed at the victim.
- SYN Flood: Exploiting the TCP handshake by sending numerous SYN requests without completing the handshake, exhausting server resources.
- Botnet Attacks: Using a network of compromised devices to flood the target with traffic from geographically diverse locations, making it harder to block.
Man-in-the-Middle (MitM) Attacks
In a MitM attack, the adversary secretly intercepts and potentially alters communications between two parties who believe they are directly communicating with each other. This is achieved by inserting themselves into the communication path, often through Wi-Fi spoofing, ARP poisoning, or DNS cache poisoning.
- Eavesdropping: Simply listening to the traffic to capture sensitive information like credentials or financial data.
- Data Tampering: Modifying the data being exchanged, perhaps to inject malicious code or alter transaction details.
- Credential Theft: Intercepting login attempts to capture usernames and passwords.
"The network is a powerful conduit, but it is also a highway for unseen threats. Silence its traffic, and you cripple the enterprise. Compromise its integrity, and you shatter trust." - cha0smagick
SQL Injection and Cross-Site Scripting (XSS)
These are fundamentally application-layer attacks that exploit vulnerabilities in web applications. SQL Injection targets databases by injecting malicious SQL code into input fields, while XSS targets users by injecting malicious scripts into websites viewed by others.
- SQL Injection: Allows an attacker to execute arbitrary SQL queries, potentially reading sensitive data, modifying or deleting data, or even gaining administrative control over the database.
- XSS: Can be used to steal session cookies, deface websites, redirect users to malicious sites, or execute actions on behalf of the user.
Malware and Ransomware
Malware is a broad category encompassing viruses, worms, Trojans, spyware, and ransomware. While some malware aims to steal data or disrupt systems, ransomware specifically encrypts a victim's files, demanding a ransom for the decryption key. These infections often spread through email attachments, malicious downloads, or exploiting software vulnerabilities.
- Viruses/Worms: Self-replicating code that spreads across networks and systems, causing damage or stealing information.
- Trojans: Malicious software disguised as legitimate software, designed to create backdoors or steal data.
- Ransomware: Encrypts files and demands payment for their release—a direct financial attack.
Spoofing and Phishing
Spoofing involves disguising a communication from an unknown source as being from a known, trusted source. Phishing is a type of social engineering attack, often executed via email, that tricks victims into revealing sensitive information or downloading malware. It preys on human trust and urgency.
- Email Spoofing: Falsifying the sender address in an email to make it appear legitimate.
- IP Spoofing: Masquerading as a trusted IP address to gain unauthorized access or bypass security controls.
- Phishing/Spear Phishing: Targeted attacks designed to extract credentials, financial information, or install malware.
Session Hijacking
This attack involves an attacker taking over a valid user session over a network. Once a user is authenticated, a session ID or token is established. An attacker can steal this session ID (often through XSS or by sniffing unencrypted traffic) and use it to impersonate the legitimate user, bypassing the need for authentication.
- Cookie Theft: Stealing session cookies from a user's browser.
- Session Fixation: Forcing a user's browser to use a specific session ID known to the attacker.
Understanding the Attack Chain
Few attacks are monolithic. They often involve a chain of events: reconnaissance, initial compromise, privilege escalation, lateral movement, and finally, achieving the objective (data exfiltration, disruption, etc.). Recognizing this chain allows defenders to identify and intercept threats at various stages.
- Reconnaissance: Gathering information about the target network and systems.
- Weaponization: Creating a malicious payload or exploit.
- Delivery: Transmitting the weapon to the target (e.g., via email, web).
- Exploitation: Triggering the vulnerability to execute the payload.
- Installation: Establishing persistence on the compromised system.
- Command and Control (C2): Establishing communication with the compromised system for remote management.
- Actions on Objectives: Executing the attacker's ultimate goal.
Strategic Countermeasures for Robust Defense
Defending a network is not a single product or technique, but a layered strategy. It requires a deep understanding of potential threats and the implementation of multiple, overlapping security controls. The goal is to create a security posture so robust that the cost and effort for an attacker to breach it outweigh any potential gain.
Implementing Network Segmentation and Firewalls
Firewalls are the gatekeepers, controlling traffic flow between network segments based on predefined rules. Network segmentation divides a network into smaller, isolated zones, limiting the blast radius of a breach. If one segment is compromised, the attacker is contained and cannot easily move to other critical areas.
- Next-Generation Firewalls (NGFW): Offer advanced capabilities like deep packet inspection, intrusion prevention, and application awareness.
- Demilitarized Zones (DMZ): A buffer zone between the internal network and the external internet, housing public-facing servers.
- VLANs: Virtual Local Area Networks to logically segment traffic within a physical network.
Leveraging Intrusion Detection and Prevention Systems (IDPS)
IDPS solutions monitor network traffic for malicious activity or policy violations. Intrusion Detection Systems (IDS) detect and alert, while Intrusion Prevention Systems (IPS) can automatically block detected threats. Signature-based detection looks for known attack patterns, while anomaly-based detection identifies deviations from normal network behavior.
- Network-based IDPS (NIDS/NIPS): Monitor network traffic for threats.
- Host-based IDPS (HIDS/HIPS): Monitor individual host systems for malicious activity.
"Don't just build a wall. Build a fortress with layers of defense. Because the lowest common denominator—the human—will always be the weakest link." - Reflecting on early cybersecurity principles.
Data Encryption and Secure Protocols
Encryption scrambles data, rendering it unreadable to anyone without the decryption key. Using secure protocols like TLS/SSL for web traffic (HTTPS), SSH for remote access, and VPNs for secure remote connections are fundamental to protecting data in transit. End-to-end encryption ensures that only the sender and intended recipient can access the data.
- TLS/SSL: Secures communications over computer networks (e.g., HTTPS for websites).
- IPsec: A suite of protocols used to authenticate and encrypt IP packets.
- VPNs: Create secure, encrypted tunnels over public networks.
Access Control and Authentication Mechanisms
Strong authentication ensures that only legitimate users can access network resources. Multi-Factor Authentication (MFA) is a critical defense against credential theft, requiring users to provide two or more verification factors. Role-Based Access Control (RBAC) ensures users only have access to the resources necessary for their job functions, adhering to the principle of least privilege.
- Multi-Factor Authentication (MFA): Combines something you know (password), something you have (token, phone), and something you are (biometrics).
- Principle of Least Privilege: Granting users only the minimum permissions required to perform their tasks.
- Centralized Authentication: Using systems like RADIUS or TACACS+ for managing user authentication across network devices.
Security Awareness Training: The Human Firewall
Technical controls are vital, but often the most vulnerable point is the human element. Regular, comprehensive security awareness training educates users about common threats like phishing, social engineering, and safe browsing habits. A well-informed user is the most effective first line of defense. It's not just about clicking buttons; it's about fostering a security-conscious culture.
Engineer's Verdict: Is CISSP Training Worth It?
For professionals serious about advancing in cybersecurity, especially in enterprise environments, CISSP certification is a significant milestone. Platforms like Skillset.com, offering unlimited practice questions, exam readiness scores, and personalized learning, can indeed accelerate the process. However, the certification itself is only a stepping stone. The true value lies in the comprehensive knowledge base it demands. It forces a deep dive into domains like network security, cryptography, identity and access management, and risk management – all critical for understanding and mitigating the attacks detailed here. While you can learn these concepts independently, a structured approach with reliable practice resources can optimize study time and guarantee exam readiness more effectively. For those aiming for senior roles or consulting positions, the CISSP is often a non-negotiable credential.
Operator/Analyst Arsenal
- Essential Tools:
- Wireshark: For deep-packet analysis.
- Nmap: For network discovery and security auditing.
- Metasploit Framework: For penetration testing and exploit development (use ethically!).
- Burp Suite: For web application security testing.
- ClamAV/Malwarebytes: For malware detection.
- OpenVAS/Nessus: For vulnerability scanning.
- Key Protocols & Technologies:
- TCP/IP Suite: The foundation of all network communication.
- TLS/SSL: For secure data transmission.
- IPsec: For secure IP communications.
- RADIUS/TACACS+: For authentication, authorization, and accounting.
- Firewalls (NGFW), IDS/IPS: For perimeter and internal defense.
- Must-Read Books:
- "The CISSP All-in-One Exam Guide" by Shon Harris.
- "Network Security Essentials" by William Stallings.
- "The Web Application Hacker's Handbook" by Dafydd Stuttard and Marcus Pinto.
- Crucial Certifications:
- CISSP (Certified Information Systems Security Professional).
- CompTIA Security+: A foundational certification.
- CEH (Certified Ethical Hacker): For understanding offensive techniques.
Frequently Asked Questions
What is the primary goal of a DoS attack?
The primary goal is to disrupt the availability of a service, system, or network by overwhelming it with traffic or malicious requests, making it inaccessible to legitimate users.
How can I protect myself from Man-in-the-Middle attacks?
Use secure, encrypted connections (HTTPS, VPNs), avoid public Wi-Fi for sensitive transactions, and ensure your devices have up-to-date security software.
Is ransomware a type of malware?
Yes, ransomware is a specific type of malicious software (malware) designed to encrypt a victim's data and demand a ransom payment for its decryption.
What is the 'human firewall'?
The 'human firewall' refers to educated and vigilant users who are trained to recognize and report security threats, acting as a crucial layer of defense against social engineering and phishing attacks.
How does network segmentation improve security?
Network segmentation divides a network into smaller, isolated zones. This containment limits the lateral movement of attackers and reduces the impact of a security breach to a specific segment.
The Contract: Securing Your Network Perimeter
The defenses we've discussed—firewalls, IDPS, encryption, strong authentication, and user training—form the core of a robust network security strategy. They are not merely options; they are prerequisites for operating in the modern digital space. Your contract is with reality: failing to implement these measures is an open invitation to compromise.
Your challenge: Map out a hypothetical network for a small e-commerce business. Identify the critical assets, the most likely attack vectors based on this post, and design a layered defense strategy using the countermeasures discussed. Detail how you would segment the network, which types of firewalls and IDPS you'd deploy, and the authentication mechanisms you'd mandate. Treat this as your initial security architecture proposal.
Now, take this knowledge and apply it. The digital shadows are long, and vigilance is the only currency that truly matters. Did we miss a critical attack vector? Are your defenses as robust as you think? The conversation continues below.
