STRATEGY INDEX
- Introduction: The Evolving Threat Landscape
- Understanding Phishing: The Anatomy of a Cyber Heist
- Setting Up Your Ethical Phishing Test Lab
- Mastering Website Clones: The Credential Harvester
- Crafting Convincing Phishing Links: The Art of Deception
- Your Defense Arsenal: Fortifying Against Phishing
- The Persistent Effectiveness of Phishing: The Human Factor
- Comparative Analysis: Phishing Tools vs. Manual Techniques
- The Engineer's Verdict on Phishing Defense
- Frequently Asked Questions
- About The Cha0smagick
Introduction: The Evolving Threat Landscape
Greetings, operative. In the digital realm, information is currency, and the most valuable currency is often the credentials that unlock access to systems and data. Attackers, ever the opportunists, have honed their craft of credential harvesting into a sophisticated art form. Phishing, once a rudimentary scam, has evolved into a multi-faceted threat capable of breaching even ostensibly secure networks. This dossier dissects the mechanics of modern phishing attacks, moving beyond theoretical discussions to provide actionable intelligence and defensive blueprints.
"The alarming reality of modern phishing attacks is their sheer volume and increasing sophistication. Attackers are no longer limited to crude email attempts; they leverage social engineering, crafted websites, and deceptive links to exploit human trust."
In this comprehensive guide, we will equip you with the knowledge to understand how attackers operate, build your own secure testing environment, analyze their methods, and more importantly, implement robust defense strategies. This is not merely about identifying phishing; it's about understanding the entire lifecycle of an attack to build impenetrable defenses.
Understanding Phishing: The Anatomy of a Cyber Heist
Phishing is a deceptive practice used to obtain sensitive information such as usernames, passwords, and credit card details by masquerading as a trustworthy entity in an electronic communication. The effectiveness of phishing lies in its exploitation of human psychology, often referred to as social engineering. Attackers understand that while systems can be technically secured, humans remain the most vulnerable link.
The Mechanics of Credential Theft
Credential theft typically involves luring a victim to a fake login page or tricking them into revealing information directly. The process can be broken down:
- Reconnaissance: Attackers gather information about their target (individual or organization) to craft personalized and believable attacks.
- Delivery: This is usually an email, SMS (smishing), or social media message containing a malicious link or attachment.
- Engagement: The victim clicks the link, leading them to a fake website or prompting them to open a malicious file.
- Harvesting: The victim enters their credentials or sensitive data, which is then transmitted to the attacker.
- Exploitation: The attacker uses the stolen credentials to gain unauthorized access, commit fraud, or sell the information on the dark web.
Real-World Implications
The consequences of compromised accounts can be devastating, ranging from financial loss and identity theft to reputational damage and the exposure of sensitive corporate data. For businesses, a single successful phishing attack can lead to significant financial penalties, regulatory fines, and a loss of customer trust.
Setting Up Your Ethical Phishing Test Lab
To truly understand phishing, one must be able to dissect it in a controlled environment. Setting up a secure lab is paramount for ethical security research. This lab will allow you to experiment with tools and techniques without risking any real-world systems.
System Preparation and Updates
Before diving into specialized tools, ensure your testing platform is up-to-date. For this exercise, Kali Linux is an excellent choice due to its pre-installed security tools. Always run system updates to patch known vulnerabilities and ensure all software is current.
sudo apt update && sudo apt upgrade -yUnderstanding the Social Engineering Toolkit (SET)
The Social Engineering Toolkit (SET) is a powerful open-source Python-driven tool that provides a suite of social engineering attacks. It simplifies the process of launching various types of attacks, including phishing.
To install SET if it's not already present (common in Kali):
sudo apt install social-engineer-toolkit -yTo launch SET:
sudo setoolkitConfiguring Security Testing Tools
Within SET, you'll find various modules. For phishing, the 'Website Attack Vectors' and 'Social-Engineering Attacks' are most relevant. You'll also need a method to host your cloned website, which SET can often facilitate using its built-in web server or by integrating with other tools.
Mastering Website Clones: The Credential Harvester
A core component of sophisticated phishing is the credential harvester. This is a fake website, meticulously cloned from a legitimate one, designed to trick users into entering their credentials. When the user submits their information on the fake page, it's captured by the attacker.
Credential Harvester Attack Method
SET provides templates for creating credential harvesters. After launching `setoolkit`, navigate through the menus:
- Select 'Website Attack Vectors'.
- Choose 'Credential Harvester Attack Method'.
- Select 'Website Cloner'.
- Enter the URL of the website you wish to clone (e.g., a legitimate login page).
- SET will download the site and set up a listener on your local machine.
Site Cloning Techniques
The effectiveness of a cloned site depends on its fidelity to the original. Tools like SET or specialized scripts automate this process, downloading HTML, CSS, JavaScript, and images. However, complex JavaScript functionalities or server-side interactions might not be perfectly replicated, making thorough testing crucial.
Testing the Phishing Environment
Before deploying any phishing campaign, even in a lab, test your cloned site. Access it via your Kali machine's IP address or a local domain. Attempt to log in with test credentials. Verify that the submitted data is being captured by your listener (SET will typically display this in the console).
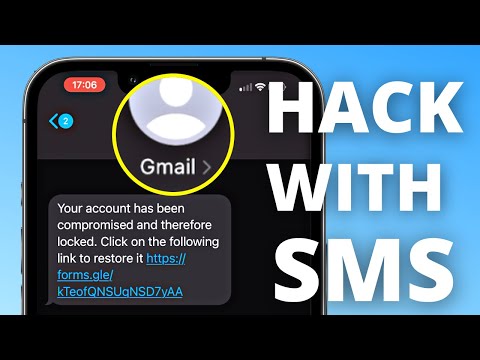
Crafting Convincing Phishing Links: The Art of Deception
A phishing link needs to look legitimate to be effective. Attackers employ various techniques to mask the true destination of a URL.
URL Masking Techniques
Common masking techniques include:
- Subdomain Spoofing: Using seemingly legitimate subdomains (e.g., `login.yourbank.com.malicious-site.com`).
- Typosquatting: Registering domains with slight misspellings of legitimate ones (e.g., `amaz0n.com` instead of `amazon.com`).
- URL Shorteners: Using services like bit.ly to hide the true destination.
- HTML Entities: Creating URLs that appear different in display text versus the actual link.
Using Specialized Tools like Facad1ng
Tools like `facad1ng` (a hypothetical example representing advanced URL obfuscation tools) are designed to create highly convincing phishing pages that mimic legitimate sites. They often involve techniques to bypass basic security filters and make the URL appear benign.
While `facad1ng` itself might be a specific tool, the principle involves dynamically generating pages or using JavaScript to alter the URL displayed in the browser's address bar, often by leveraging techniques like HTML entity encoding or manipulating the browser's history API. For instance, a link might appear as `https://www.example.com` but actually redirect to `http://malicious-domain.com/fake-login?target=https://www.example.com`.
Creating Convincing Distribution Links
The final step is distributing the link. This often happens via email or social media. The message content is crucial, creating a sense of urgency or importance (e.g., "Your account has been compromised, please verify your details immediately," or "You have a pending delivery, click here to confirm").
Your Defense Arsenal: Fortifying Against Phishing
Understanding attack vectors is the first step; implementing defenses is the critical second. Here’s how to build your resilience:
URL Verification Best Practices
- Hover Before You Click: Always hover your mouse cursor over a link (without clicking) to see the actual destination URL in your browser's status bar.
- Inspect URLs Closely: Be wary of unusual domain names, misspellings, or excessive subdomains. Look for `https://` and a valid certificate (padlock icon), though this can also be faked.
- Avoid Clicking Links in Suspicious Emails: If an email seems suspicious, go directly to the organization's website by typing the URL into your browser or using a trusted bookmark, rather than clicking the link in the email.
Two-Factor Authentication (2FA) Importance
Two-factor authentication (2FA) is one of the most effective defenses against credential theft. Even if an attacker obtains your password, they will still need your second factor (e.g., a code from your phone app, an SMS code, or a hardware token) to log in. Enable 2FA on all your critical accounts.
Browser Security Measures
- Keep Browsers Updated: Modern browsers have built-in phishing and malware protection.
- Install Security Plugins: Consider reputable browser extensions that can help identify malicious websites.
- Be Cautious with Forms: Never enter sensitive information on a website you accessed through an unsolicited email or suspicious link.
- Utilize Password Managers: Password managers can help autofill credentials only on legitimate sites and often flag suspicious URLs.
The Persistent Effectiveness of Phishing: The Human Factor
Despite technological advancements, phishing remains highly effective because it targets the human element. Attackers exploit our inherent trust, curiosity, fear, and desire for convenience.
Psychological Manipulation Techniques
Common psychological triggers include:
- Urgency: "Your account will be suspended within 24 hours!"
- Fear: "We've detected suspicious activity on your account."
- Curiosity: "You have a package waiting to be claimed."
- Authority: Impersonating trusted entities like banks, government agencies, or IT support.
- Greed: "You've won a prize!"
The Importance of Continuous Vigilance
Cybersecurity is not a set-it-and-forget-it discipline. Continuous vigilance, ongoing education, and a healthy dose of skepticism are your best defenses. Regularly review your security practices and stay informed about emerging threats.
Comparative Analysis: Phishing Tools vs. Manual Techniques
While automated tools like SET and specialized frameworks simplify phishing, manual techniques offer a deeper understanding and can sometimes evade detection more effectively.
- Automated Tools (e.g., SET, Gophish):
- Pros: Speed, ease of use, ability to clone complex sites quickly, pre-built templates, reporting features.
- Cons: Can be detected by security software, generated code might have flaws, less flexibility for highly customized attacks.
- Manual Techniques (e.g., custom HTML/JS, server-side scripts):
- Pros: Maximum flexibility, ability to tailor attacks precisely, can evade signature-based detection, deeper understanding of web technologies.
- Cons: Time-consuming, requires significant technical expertise (HTML, JavaScript, backend languages, server configuration), higher learning curve.
For ethical testers, employing both approaches provides a comprehensive understanding. Automated tools are excellent for quickly testing basic defenses and common attack vectors, while manual crafting allows for more targeted and sophisticated penetration tests.
The Engineer's Verdict on Phishing Defense
Phishing is a persistent and evolving threat, fundamentally exploiting the human element. While technical defenses like firewalls and intrusion detection systems play a role, they are often bypassed by well-crafted social engineering. The most robust defense strategy is multi-layered, combining technological safeguards with continuous user education and a culture of security awareness. Never underestimate the power of skepticism and verification.
Frequently Asked Questions
1. Can Kali Linux be used to hack any account?
No. Kali Linux is a penetration testing distribution containing tools that *can* be used for malicious purposes, but its ethical use is for security auditing and research in authorized environments. Hacking accounts without permission is illegal.
2. How can I make sure a website is legitimate?
Verify the URL carefully for misspellings or unusual domains, check for the HTTPS padlock, and if in doubt, navigate to the site directly through your browser or a known bookmark, rather than clicking links from emails or messages.
3. Is Two-Factor Authentication (2FA) foolproof?
While 2FA significantly enhances security and is highly recommended, it's not entirely foolproof. Sophisticated attacks like SIM-swapping or advanced phishing techniques targeting 2FA codes can sometimes bypass it. However, for the vast majority of users and common threats, it provides a critical layer of protection.
4. What is the best way to learn about cybersecurity threats?
Continuous learning is key. Follow reputable cybersecurity news outlets, subscribe to security blogs, participate in ethical hacking communities, and consider certifications. Hands-on practice in lab environments is also invaluable.
About The Cha0smagick
The Cha0smagick is a seasoned digital operative and polymath engineer, deeply entrenched in the trenches of cybersecurity and advanced technology. With a pragmatic and analytical approach forged through countless system audits and digital investigations, they specialize in transforming complex technical challenges into actionable blueprints. Their expertise spans the spectrum from deep-level coding and reverse engineering to data analysis and the exploitation of emergent vulnerabilities, always with a focus on ethical application and robust defense.
Your Mission: Execute, Share, and Debate
This dossier has provided you with the intelligence required to understand and analyze phishing attacks. Now, it's your turn to operationalize this knowledge.
Debriefing of the Mission
If this blueprint has illuminated the dark corners of credential harvesting for you, share it with your network. An informed operative is a safer operative. If you encounter a phishing technique that stumps you, or if you have insights from your own observations, detail them in the comments below. Your input refines our collective intelligence.
Your mission, operative, is to internalize this knowledge and apply it diligently. Stay vigilant.
For further exploration and to support our research, consider exploring the broader ecosystem of digital finance. A sound strategy involves not just defense but also smart asset management. To this end, consider opening an account on Binance and exploring the cryptocurrency landscape.
Stay tuned for more technical dossiers from Sectemple.