STRATEGY INDEX
- Introduction: The Hacker's Imperative
- The Real Hacker Mindset: Pragmatism Over Theory
- The Essential Toolkit: Your Hacking Arsenal
- Field Training Grounds: Legal Hacking Platforms
- Monetizing Skills: Bug Bounty Hunting from Scratch
- Diversification Strategy: Exploring Digital Assets
- Ethical Hacking vs. Traditional Cybersecurity Education
- Frequently Asked Questions
- About The Cha0smagick
Introduction: The Hacker's Imperative
Stop wasting precious cycles on theoretical abstractions. The digital trenches are not built for academics; they are forged by action. Real-world hackers, the operatives who truly understand the intricate dance of systems, don't spend years buried in textbooks. They dive in, they probe, they learn by dissecting live systems, and crucially, they monetize their skills. This dossier is your direct operational manual to bypass the conventional learning curve and transition into practical, profitable ethical hacking. We cut through the noise – no fluff, just actionable intelligence designed to get you earning.
The Real Hacker Mindset: Pragmatism Over Theory
Forget the Hollywood portrayals. The core of ethical hacking isn't about elaborate social engineering or theoretical exploits you'll never see in the wild. It's about a relentless, pragmatic mindset focused on problem-solving and continuous learning through practical application. Real hackers embody:
- Curiosity & Exploration: An insatiable drive to understand how things work, and more importantly, how they can be made to work differently.
- Persistence: The ability to stare down a complex system or a stubborn vulnerability and refuse to yield until a solution is found.
- Adaptability: The digital landscape shifts daily. A real hacker is constantly updating their knowledge base and toolset.
- Ethical Boundaries: Understanding that the most powerful skills are those wielded responsibly. The goal is to find and fix, not to destroy.
- Results-Oriented Focus: Theory is a foundation, but the true value lies in demonstrable results – identifying vulnerabilities, securing systems, and delivering tangible outcomes.
This dossier emphasizes this pragmatic approach. We move beyond abstract concepts to deliver tangible skills you can use immediately.
The Essential Toolkit: Your Hacking Arsenal
Every operative needs their gear. While the digital world is vast, a core set of tools will equip you for the majority of initial engagements. Mastering these is your first mission objective.
Network Scanning and Reconnaissance:
-
Nmap (Network Mapper): The undisputed king of network discovery.
Core Functionality: Host discovery, port scanning, OS detection, service version detection, scriptable interaction (NSE).
Essential Commands:nmap -sn 192.168.1.0/24(Ping scan to discover live hosts)nmap -sV -p- 192.168.1.1(Scan all ports with version detection)nmap -A -T4 target.com(Aggressive scan with OS/version detection and traceroute)
Nmap is your initial reconnaissance phase, mapping the attack surface before any deeper penetration attempts. Its versatility allows for quick scans or deep dives depending on your objective.
Web Application Penetration Testing:
-
Burp Suite (Community Edition): The industry standard for web vulnerability analysis.
Core Functionality: Intercepting proxy, web application scanner, intruder (fuzzing), repeater (manual request manipulation).
Workflow: Configure your browser to use Burp Suite as a proxy. Browse the target application, and Burp will capture all HTTP/S requests and responses. Use the Intruder and Repeater tools to systematically test for common web vulnerabilities like SQL injection, XSS, and parameter tampering. The scanner can automate detection of many common issues. -
OWASP ZAP (Zed Attack Proxy): A strong, open-source alternative to Burp Suite.
Core Functionality: Similar to Burp Suite, offering proxying, scanning, and fuzzing capabilities. Excellent for those starting with web app testing.
Password Cracking and Brute-Forcing:
-
Hydra: A rapid network logon cracker.
Core Functionality: Supports numerous protocols (SSH, FTP, HTTP, SMB, RDP, etc.) and performs brute-force attacks using wordlists.
Essential Commands:hydra -l admin -P passwords.txt ssh://192.168.1.10(Attempt to log in as 'admin' with passwords from the file)hydra -L users.txt -p password123 http-get /login.php target.com(Brute-force passwords for multiple users)
Use Hydra with extreme caution and only on authorized systems. It's a powerful tool for testing password strength and detecting weak credentials.
-
John the Ripper: A password cracker that supports numerous hash and cipher types.
Core Functionality: Primarily used for cracking password hashes obtained during penetration tests. Can perform dictionary attacks, brute-force attacks, and hybrid attacks. -
Hashcat: The world's fastest and most advanced password recovery utility.
Core Functionality: Leverages GPU acceleration for significantly faster cracking of a wide array of hash types. Requires a deeper understanding of hash algorithms and hardware.
Exploitation Frameworks (Advanced):
-
Metasploit Framework: The premier framework for developing, testing, and executing exploits.
Core Functionality: Provides a vast library of exploits, payloads, auxiliary modules, and encoders. Essential for understanding how vulnerabilities are leveraged.
Operational Use: Used after successful reconnaissance and vulnerability identification to gain unauthorized access or test system resilience.
Mastering these tools is not about memorizing commands; it's about understanding their underlying principles and applying them strategically to identify and exploit weaknesses within a defined scope.
Field Training Grounds: Legal Hacking Platforms
You cannot hone your skills by only reading. Practical, hands-on experience is non-negotiable. Fortunately, there are dedicated platforms designed for you to practice your craft legally and ethically, sharpening your abilities against realistic challenges.
-
TryHackMe: Your guided entry into practical cybersecurity.
Focus: Beginner-friendly learning paths, guided rooms, and virtual labs covering a wide range of cybersecurity topics from basic networking to advanced exploitation.
Why it's Crucial: Offers structured learning modules that build foundational knowledge alongside practical exercises. Perfect for transitioning from theory to action. -
Hack The Box: The ultimate playground for offensive security professionals.
Focus: Highly challenging retired and active machines, labs, and challenges designed for intermediate to advanced users. Features a competitive leaderboard and community.
Why it's Crucial: Pushes your problem-solving skills to their limits. You'll encounter real-world scenarios and diverse attack vectors that demand creative solutions. -
VulnHub: A repository of vulnerable virtual machines.
Focus: Downloadable VMs that you can run locally in virtual environments (VirtualBox, VMware). Each VM is designed to be exploited.
Why it's Crucial: Offers complete control over your practice environment and allows for offline learning. Great for experimenting with different attacks without time constraints.
Engage with these platforms daily. Treat each challenge as a mission. Document your findings, analyze your successes and failures, and iterate. This is how true skill is cultivated.
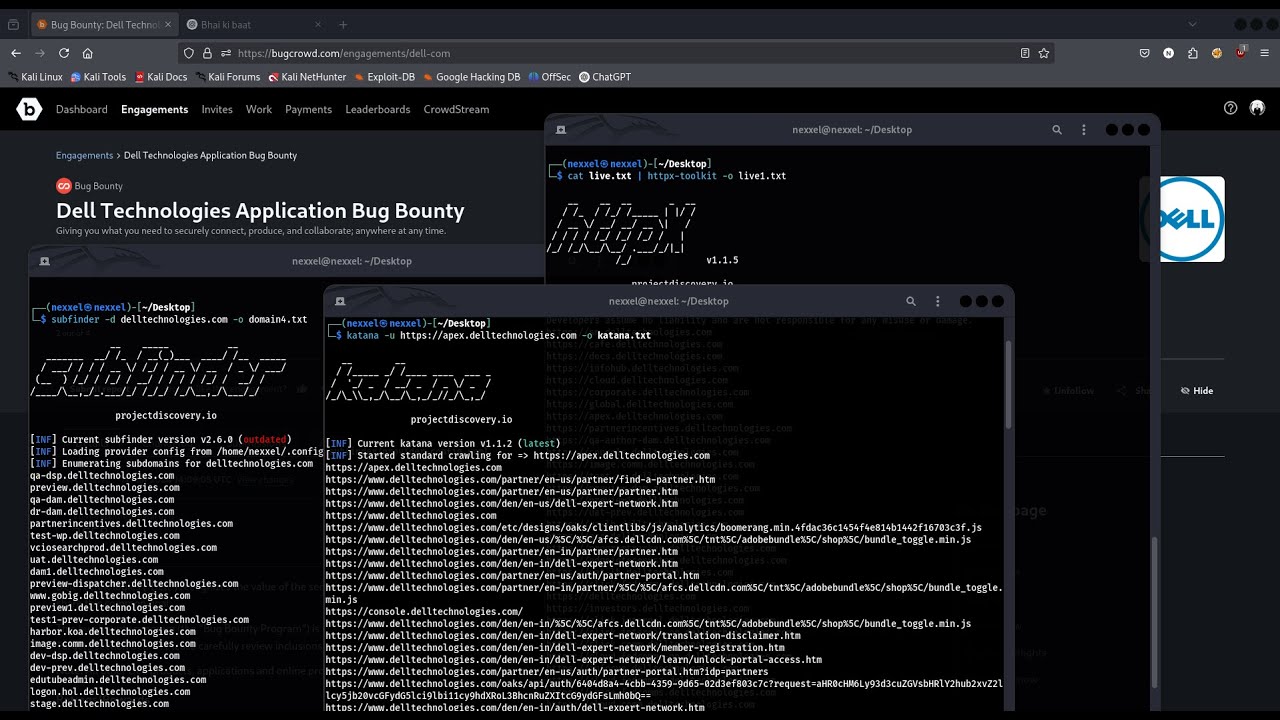
Monetizing Skills: Bug Bounty Hunting from Scratch
Once you have a foundational understanding of tools and methodologies, the most direct path to earning is through bug bounty programs. These programs incentivize ethical hackers to find and report vulnerabilities in real-world applications.
-
Choose a Platform: Start with major bug bounty platforms that aggregate programs from various companies.
- HackerOne
- Bugcrowd
- Intigriti
- Select Your Target: Begin with programs that have a wide scope and a good reputation for paying out. Look for programs that explicitly welcome new researchers. Start small – perhaps a program with a lower maximum payout but a broader acceptable vulnerability list.
- Understand the Rules of Engagement (RoE): This is paramount. Every program has specific rules regarding what is in-scope, out-of-scope, testing methodologies allowed, and disclosure policies. Violating these rules can lead to disqualification or even legal repercussions.
- Reconnaissance is Key: Dedicate significant time to understanding the target's digital footprint. Use tools like Nmap, Sublist3r, Amass, and Google Dorking to find subdomains, hidden directories, APIs, and other attack vectors.
-
Vulnerability Identification: Systematically test for common vulnerabilities. Focus on areas like:
- Cross-Site Scripting (XSS)
- SQL Injection (SQLi)
- Authentication and Authorization flaws
- Insecure Direct Object References (IDOR)
- Server-Side Request Forgery (SSRF)
- Misconfigurations
Leverage tools like Burp Suite extensively for manual testing and analysis.
-
Craft a High-Quality Report: A clear, concise, and actionable report is crucial for getting paid. Include:
- A descriptive title
- The vulnerability type
- The affected URL and specific parameters
- Step-by-step instructions to reproduce the vulnerability
- Proof of Concept (screenshots, videos, code snippets)
- The potential impact of the vulnerability
- Suggested remediation (optional but appreciated)
- Submit and Wait: Submit your report through the platform. Be patient. Triaging can take time. Respond professionally to any follow-up questions from the security team.
Your first payout might be small, but each successful report builds your reputation, hones your skills, and provides valuable intel for your next engagement. The journey from zero to earning is paved with consistent, ethical effort.
Diversification Strategy: Exploring Digital Assets
In the modern digital economy, understanding and leveraging diverse asset classes is a strategic imperative. Beyond bug bounties and penetration testing, exploring decentralized finance and digital assets can offer significant opportunities for growth and wealth accumulation. For those looking to diversify their income streams and investment portfolio, robust and secure platforms are essential. Consider exploring the vast ecosystem of digital assets and trading opportunities. A well-regarded entry point for many is Binance, offering a comprehensive suite of tools for trading, investing, and managing cryptocurrencies.
Ethical Hacking vs. Traditional Cybersecurity Education
The debate between practical, hands-on hacking and traditional academic cybersecurity education is ongoing. While both have their place, the operational effectiveness and earning potential often lean towards the former:
| Aspect | Ethical Hacking (Practical) | Traditional Cybersecurity Education |
|---|---|---|
| Learning Focus | Hands-on, tool-driven, exploit-focused, problem-solving. | Theoretical frameworks, policies, compliance, risk management, broad concepts. |
| Outcome | Directly applicable skills for penetration testing, bug bounty hunting, immediate earning potential. | Foundational knowledge, preparation for certifications (CISSP, Security+), broad career readiness. |
| Pace of Learning | Rapid, iterative, learn-by-doing. | Structured, often slower-paced, theoretical absorption. |
| Earning Potential (Entry) | High, with demonstrable skills in bug bounties or pentesting roles. | Moderate, often requiring further specialization or certifications for high-paying roles. |
| Tools Emphasized | Nmap, Burp Suite, Metasploit, Kali Linux, scripting languages. | SIEM tools, firewalls, IDS/IPS, GRC platforms (often theoretical). |
While a degree can provide a strong theoretical foundation and open doors to certain corporate roles, the hacker's path focuses on developing the specific, high-demand skills that companies directly pay to have addressed. The raw ability to break and then fix systems is often more immediately valuable in the offensive security market.
Frequently Asked Questions
Q1: How quickly can I start earning money with ethical hacking?
A1: With focused effort on learning practical tools and methodologies, and dedicating time to bug bounty hunting, it's possible to earn your first payout within weeks to a few months. Consistent success requires ongoing learning and practice.
Q2: Do I need a computer science degree to be a hacker?
A2: Absolutely not. While a CS background can be helpful, it's not a prerequisite. The most critical elements are a strong aptitude for problem-solving, continuous learning, and hands-on skill development. Many successful hackers are self-taught.
Q3: Is it legal to practice hacking?
A3: Practicing on systems you do not have explicit, written permission to test is illegal. Platforms like TryHackMe and Hack The Box provide legal, safe environments. Bug bounty programs give you permission to test specific company assets within defined rules.
Q4: What's the difference between a hacker and a black hat hacker?
A4: A "hacker" is someone with deep technical knowledge and the ability to bypass security. An "ethical hacker" (or white hat) uses these skills for defensive purposes, with permission. A "black hat" hacker uses their skills maliciously and illegally.
About The Cha0smagick
I am The Cha0smagick, an operative forged in the digital shadows. My expertise spans deep system analysis, reverse engineering, network exploitation, and data forensics. I translate complex technical landscapes into actionable intelligence and functional blueprints. My mission is to equip fellow operatives with the knowledge and tools needed to navigate and dominate the digital frontier, ethically.
Your Mission: Execute, Share, and Debate
This dossier is not meant to be a passive read. It is a directive. The true value of this intelligence lies in your execution.
Debriefing of the Mission
Implement these strategies. Master the tools. Engage with the platforms. Hunt for bugs. If this blueprint has significantly accelerated your path or provided critical insights, disseminate this intelligence. Share it with your network; knowledge weaponized ethically benefits us all. Identify operatives wading through theory; tag them. Let them know where the real mission begins. Most importantly, engage in the comments below. What vulnerabilities are you hunting? What challenges are you facing? Your debriefings fuel the next wave of intelligence.
Stay sharp. Stay ethical. Keep breaking.
Join the inner circle for exclusive drops, early access to guides, and live hacking sessions:
Trade on Binance: Sign up for Binance today!