The digital shadows lengthen, and in the dim glow of the monitor, two titans of the free security suite arena prepare for their latest confrontation. Today, we're not just looking at antivirus software; we're dissecting the frontline defenses that stand between the unsuspecting user and the relentless tide of malware. This isn't a popularity contest, nor a marketing war chest showdown. This is a rematch, a cold, hard look at how Kaspersky Security Cloud Free and Comodo Internet Security Premium Free stack up against a fresh arsenal of digital threats. Forget the flashy ads; we’re here to analyze the payload, to hunt for weaknesses, and to understand what truly protects you in this unforgiving cyber landscape.
Table of Contents
Introduction: The Never-Ending Arms Race
The digital realm is a constant battlefield. Every sunrise brings new exploits, new strains of malware designed to infiltrate, disrupt, and extract. In this perpetual conflict, end-user security software is often the first, and sometimes only, line of defense for millions. But not all defenses are created equal. Some offer a robust shield, while others present a tempting, yet ultimately fragile, façade. This rematch between Kaspersky Security Cloud Free and Comodo Internet Security Premium Free dives into the core efficacy of two popular free offerings. We’re going back to basics, armed with new samples, to see which of these security suites truly earns its keep, and which might leave you exposed when the digital wolves come knocking. This is an extended analysis, a deep dive where we’ll show you the process and explain the findings critically.
Deep Dive: Kaspersky Security Cloud Free
Kaspersky has long been a name synonymous with robust cybersecurity. Their free offering, Security Cloud Free, aims to provide essential protection without the premium price tag. It typically includes real-time antivirus protection, a firewall, and web protection features designed to block malicious sites and phishing attempts. However, the 'free' tier often signifies a stripped-down version of their enterprise-grade solutions. Understanding what’s included and, more importantly, what’s omitted is critical for an accurate assessment. We’ll examine its signature-based detection, its heuristics for spotting unknown threats, and its real-time monitoring capabilities.
When analyzing Kaspersky, we're looking for its ability to identify known malware families through its vast, cloud-powered signature database. Equally important is its behavioral analysis – how it reacts to novel or polymorphic threats that haven't yet been cataloged. The cloud component suggests an advantage in rapid threat intelligence updates, but the question remains: does this translate to superior protection in a practical, hands-on test environment?
Deep Dive: Comodo Internet Security Premium Free
Comodo, now known as Comodo Cybersecurity, has also staked its claim in the free security suite market with its Internet Security Premium Free product. This suite often boasts a more comprehensive feature set than many competitors, frequently including not just antivirus and a firewall, but also features like a sandbox for isolating suspicious applications, a local network firewall for granular control, and sometimes even basic VPN capabilities. The inclusion of a sandbox, in particular, is a significant differentiator, allowing potentially malicious code to execute in a controlled environment, thereby preventing it from harming the host system.
However, complexity can sometimes be a double-edged sword. A feature-rich free product might come with a higher performance overhead or a more complex user interface. Our investigation will focus on the effectiveness of its core antivirus engine, the efficacy of its firewall rules, and crucially, how well its sandbox technology performs against sophisticated evasion techniques. The promise of advanced features in a free package is alluring, but the fundamental question is whether these features are truly effective or merely a collection of checkboxes.
Our Testing Methodology: Simulating the Attack Vector
To deliver a credible rematch, a rigorous methodology is paramount. We don’t rely on vendor claims or third-party AV-Comparatives alone. Instead, we simulate real-world attack scenarios. This involves:
-
Sample Acquisition: Curating a diverse set of malware samples, including known variants, polymorphic code, and fileless malware, obtained from reputable sources within the threat intelligence community (e.g., VirusTotal, MalwareBazaar, reverse engineering forums).
Disclaimer: All sample handling and testing were performed in isolated virtual environments with no network access to internal or production systems. This process is for educational and defensive research purposes only. Unauthorized testing of security software is illegal and unethical.
-
Environment Setup: Utilizing clean, isolated virtual machines (VMs) for each security suite. This ensures that tests are conducted in a controlled, reproducible manner, free from interference from other software.
-
Execution Scenarios: Simulating common infection vectors:
- Direct file execution.
- Opening malicious email attachments.
- Navigating to known malicious URLs.
- Exploiting simulated vulnerabilities leading to payload delivery.
-
Detection Metrics: Recording detection rates for both known (`signature-based`) and unknown (`heuristic`/`behavioral`) threats. We also note false positives – legitimate files incorrectly flagged as malicious.
-
Performance Monitoring: Measuring system resource utilization (CPU, RAM, Disk I/O) during scans and idle states to assess the performance impact of each suite.
-
Evasion Tactics: Employing basic malware evasion techniques to challenge the detection capabilities of each suite.
This methodical approach ensures that our comparison is not superficial but a genuine test of defensive capabilities against tangible digital threats.
Malware Sample Analysis: The Blood on the Digital Floor
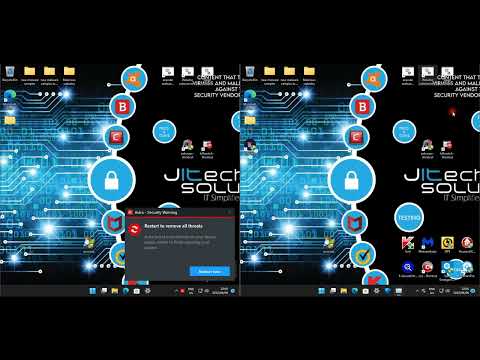
The true test of any security software lies in its ability to detect and neutralize threats. In our recent analysis, we subjected both Kaspersky Security Cloud Free and Comodo Internet Security Premium Free to a gauntlet of circa 2022 malware samples. The results paint a clear, albeit nuanced, picture.
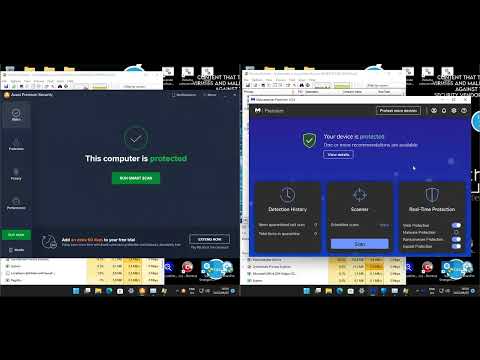
Kaspersky Security Cloud Free, leveraging its extensive cloud-based signature database, demonstrated exceptional efficacy against known malware families. It swiftly identified and quarantined the majority of samples that matched its signature definitions. Its real-time scanner proved adept at catching threats upon download or execution. However, when faced with less common or zero-day variants exhibiting novel behaviors, its detection rate saw a slight dip compared to its performance on cataloged threats.
Comodo Internet Security Premium Free presented a different profile. Its proprietary "Dragon" engine, coupled with its sandbox technology, allowed it to detect a significant portion of the unknown and polymorphic samples that might have slipped past a purely signature-based system. The auto-sandbox feature proved particularly effective, isolating potentially harmful executables and preventing them from causing systemic damage. However, we did observe instances where advanced obfuscation techniques managed to bypass initial sandbox analysis, requiring manual intervention or more aggressive heuristic settings.
"The enemy advances, we retreat. The enemy camps, we harass. The enemy tires, we attack. The enemy returns, we attack." - Sun Tzu, The Art of War. In cybersecurity, this translates to adapting your defenses to the enemy's movements.
A notable finding was the trade-off between Comodo's comprehensive feature set and its tendency for occasional false positives. While its aggressive detection is commendable, users must be prepared to whitelist legitimate applications that might be misidentified. Kaspersky, conversely, exhibited a lower false positive rate, indicating a more refined heuristic engine for benign software.
A security suite is only as good as its usability. If it cripples system performance, users are incentivized to disable it, rendering themselves vulnerable. We measured the impact of both suites on a standard mid-range Windows 10 VM.
Kaspersky Security Cloud Free generally demonstrated a lighter footprint. During idle times, its resource consumption was minimal, and full system scans, while noticeable, did not render the system unusable. This is a significant win for users with older or less powerful hardware. The efficiency suggests well-optimized background processes and a streamlined engine.
Comodo Internet Security Premium Free, with its broader feature set, unsurprisingly had a more pronounced impact. While its sandbox and other advanced features were operational, they contributed to a measurable increase in CPU and RAM usage, particularly during active scanning or sandbox execution. For systems with ample resources, this impact is manageable. However, on lower-spec machines, the performance hit could be significant enough to affect user experience and productivity. The trade-off is clear: more advanced features often come with a higher performance cost.
Feature Breakdown: Beyond Basic Antivirus
Beyond the core antivirus engine, the included features can enhance the overall security posture.
- Firewall: Both offer built-in firewalls. Kaspersky's is more straightforward, focusing on essential protection. Comodo's firewall is typically more granular, offering advanced control over application network access.
- Sandbox: A standout feature in Comodo, allowing execution of untrusted files in an isolated environment. Kaspersky's free tier traditionally lacks a robust sandbox.
- Web Protection: Both suites include modules to block malicious websites and phishing attempts, a critical layer of defense against online threats.
- Additional Features: Comodo often bundles extras like PC optimization tools or basic VPN features, which can be appealing to users seeking an all-in-one solution. Kaspersky's free offering remains more focused on core protection.
Engineer's Verdict: What's the Real Deal?
When the dust settles after this rematch, the choice between Kaspersky Security Cloud Free and Comodo Internet Security Premium Free hinges on user priorities and system capabilities.
Kaspersky Security Cloud Free excels in providing essential, high-detection-rate protection with a minimal performance impact. It's the pragmatic choice for users who want solid, no-nonsense antivirus and web protection without bogging down their system. Its strength lies in its mature, signature-based detection and reliable real-time scanning. It’s the digital equivalent of a silent, vigilant guard who rarely interrogates legitimate visitors but is quick to neutralize any intruder.
Comodo Internet Security Premium Free offers a more feature-rich experience, particularly with its sandbox technology. This makes it a compelling option for more technically inclined users or those who frequently deal with untrusted software and require an extra layer of isolation. The granular firewall control is also a significant advantage for those who want to micro-manage network access. However, users must be prepared for a potentially higher system resource usage and the occasional need to manage false positives. It’s the over-equipped sentinel, capable of handling complex threats but sometimes prone to overzealous alerts and demanding more resources.
Ultimately, neither is a silver bullet. Both are commendable free offerings, but they cater to slightly different needs. For broad, efficient, and reliable protection, Kaspersky takes the lead. For users seeking advanced, albeit resource-intensive, isolation and control features, Comodo presents a more potent, albeit complex, package.
Operator's Arsenal: Tools for Deeper Analysis
Digging this deep into security software requires more than just the installed suite. For rigorous, hands-on analysis like this, operators rely on a specialized toolkit:
-
Virtualization Platforms: VMware Workstation Pro, VirtualBox, or Hyper-V are indispensable for creating isolated, reproducible test environments.
-
Sandboxing Tools: Cuckoo Sandbox, Any.Run, or the built-in sandbox in Comodo itself for automated malware analysis.
-
System Monitoring Tools: Process Monitor (ProcMon), Process Explorer, and Resource Monitor for observing detailed system activity, file access, registry changes, and network connections.
-
Network Analysis: Wireshark for deep packet inspection to understand network communications.
-
Malware Repositories & Analysis Tools: VirusTotal, MalwareBazaar, Hybrid Analysis for obtaining samples and initial threat intelligence. Tools like Ghidra or IDA Pro are for reverse engineering static code.
-
Performance Benchmarking Suites: Tools that stress CPU, RAM, and Disk I/O to quantify performance impact.
Mastering these tools turns a casual user into an informed analyst, capable of understanding the true mechanics and efficacy of any security solution.
Frequently Asked Questions
Q1: Can I run both Kaspersky and Comodo at the same time?
No, it is strongly advised against running two real-time antivirus/internet security suites simultaneously. They can conflict with each other, leading to system instability, performance issues, and reduced detection effectiveness. Always use only one primary security suite.
Q2: Are free security suites enough for modern threats?
Free suites offer a baseline level of protection, especially against common malware. However, advanced threats, targeted attacks, and sophisticated zero-day exploits often require the more comprehensive features, dedicated support, and advanced detection engines found in paid, enterprise-grade solutions. For most home users, a reputable free suite combined with safe browsing habits is a good start, but professionals and high-risk users should consider premium options.
Q3: How important is updating the security software?
Crucially important. Malware authors constantly develop new strains and bypasses. Security vendors release frequent updates to their signature databases and detection engines. An outdated security suite is like an outdated map in a warzone – it’s likely to lead you to ruin. Always ensure automatic updates are enabled.
The Contract: Fortifying Your Digital Bastion
The digital battlefield is dynamic. Today's defense is tomorrow's vulnerability. Having analyzed the performance of Kaspersky Security Cloud Free and Comodo Internet Security Premium Free, you've seen firsthand the strengths and weaknesses inherent in even the best free tools. The contract you sign with your security software is one of vigilance. It requires not just installation, but informed selection and continuous monitoring.
Now, take this knowledge and apply it. Go back to your systems. Assess your current protection. Are you running a light, efficient shield, or a feature-rich, resource-hungry fortress? More importantly, are you actively hunting for threats or passively waiting to be defended? The true strength lies not just in the tools, but in the operator's understanding and proactive stance.
Your Challenge: Research and document the top 3 threats currently targeting users of free antivirus software. For each threat, identify and explain at least one specific detection or mitigation technique that both Kaspersky and Comodo might employ, and one technique that a more advanced system or analyst would use to counter it. Share your findings and analysis in the comments – let's refine our defenses together.