The hum of servers, the whisper of data packets, the silent ballet of network traffic – this is where the real war is fought. Firewalls and EDRs are the first lines of defense, the visible bulwark. But when the walls are breached, when the ghosts in the machine surface, true visibility lies in the captured streams, the unvarnished transit of information. This is the realm of Network Detection and Incident Response (NDIR), and its most potent weapons are forged in the crucible of open source. Forget the proprietary black boxes that drain your budget; the real power lies in community-driven intelligence and tools that cut to the bone.

In the shadowed alleys of cybersecurity, incident responders are detectives, not just system administrators. We sift through digital detritus, reconstructing events piece by painstaking piece. The traditional tooling, while necessary, often paints an incomplete picture. EDRs react, firewalls block, but the network itself? It remembers everything. It’s the ultimate black box recorder, a tapestry of evidence woven from every connection, every transaction. To truly understand a breach, you must dive into this tapestry. And for that dive, nothing beats the raw, unadulterated power of open-source solutions. These aren't just tools; they're extensions of a global consciousness, a distributed intelligence network that can be your greatest ally.
The Open Source Advantage: More Than Just Free
The allure of open-source security tools isn't merely their lack of licensing fees. It's about transparency, customization, and the sheer velocity of innovation driven by a global community. When a zero-day exploit hits, proprietary solutions often lag, waiting for vendor patches. Open-source communities? They swarm. Intel is shared in real-time, detections are refined collectively, and the tools themselves evolve at a pace that outstrips corporate roadmaps. This isn't charity; it's survival. A shared fight against a common enemy, powered by shared tools.
Core Pillars of Open-Source NDIR
When we talk about building a robust NDIR capability with open-source, a few names consistently surface, each offering a unique lens on network activity:
- Zeek (formerly Bro): This isn't just a network sniffer; it's a powerful network analysis framework. Zeek interprets network traffic, providing rich, high-level logs of network activity – from HTTP requests and DNS queries to SSL certificates and file transfers. It transforms raw packet data into structured, actionable logs that are invaluable for threat hunting and forensic analysis. Think of it as the intelligence analyst dissecting communication patterns.
- Suricata: A high-performance Network Intrusion Detection System (NIDS), Intrusion Prevention System (NIPS), and Network Security Monitoring (NSM) engine. Suricata excels at real-time threat detection using sophisticated rule sets. It can identify malicious traffic signatures, protocol anomalies, and even exploit attempts, acting as the frontline sentinel against known and emerging threats.
- Elastic Stack (Elasticsearch, Logstash, Kibana): While not strictly a network tool, the Elastic Stack is the indispensable command center. Elasticsearch provides powerful search and analytics capabilities for the vast amounts of data generated by Zeek and Suricata. Logstash ingests and transforms this data, and Kibana offers a visually intuitive dashboard for exploration, visualization, and alerting. It's where raw evidence becomes a coherent narrative.
Real-Life Exploitation: Use Cases from the Trenches
These tools aren't academic exercises; they are battle-tested. Consider these scenarios:
- Detecting Lateral Movement: An attacker gains a foothold on a single machine. EDR might flag the initial compromise, but how do you track their movements across the network? Zeek logs can reveal unusual internal DNS lookups, SMB connections to suspicious hosts, or unexpected RDP sessions. Suricata can alert on crafted packets attempting to exploit vulnerabilities on other internal systems. Kibana visualizes these connections, highlighting the attacker's path.
- Identifying C2 Communications: Malicious actors often use Command and Control (C2) channels to manage compromised systems. Zeek's HTTP logs can expose connections to known malicious domains or unusual user agents. Its DNS logs can reveal communication with newly registered or suspicious domains. Suricata rulesets can directly detect patterns indicative of specific C2 frameworks.
- Forensic Analysis of Malware: When malware is detonated, it rarely operates in silence. Zeek can log DNS queries made by the malware, the files it attempts to download or exfiltrate, and the connections it establishes. By analyzing these logs in Kibana, investigators can reconstruct the malware's behavior, identify its command infrastructure, and understand its objectives.
- Responding to Zero-Days: While signature-based systems like Suricata might miss novel exploits, Zeek's ability to log *all* network activity, including anomalous protocol behaviors or unexpected data payloads, can provide the crucial early indicators. Community-shared Zeek scripts can be rapidly deployed to hunt for patterns associated with newly discovered threats before official signatures are available.
Leveraging the Community as a Force Multiplier
The true power of open-source isn't just the code; it's the community. Global security teams, researchers, and enthusiasts constantly share threat intelligence, develop new detection rules, and refine existing tools. Platforms like GitHub, mailing lists, and specialized forums become hubs for real-time intel sharing. When a new threat emerges, these communities often develop and distribute detection logic for tools like Zeek and Suricata days, even hours, before commercial vendors can. For a security team operating with limited resources, tapping into this collective intelligence is a strategic imperative. It's the difference between reacting to a known threat and proactively hunting for shadows.
The Engineer's Verdict: Open Source for the Win?
Verdict of the Engineer: When to Deploy Open Source NDIR
For organizations serious about network defense and incident response, embracing open-source tools is not an alternative; it's a necessity. These solutions offer unparalleled depth of visibility, flexibility, and a direct line to cutting-edge threat intelligence. While they require expertise to deploy and manage effectively, the return on investment in terms of defensive capability is immense.
- Pros: Deep Visibility, High Customization, Rapid Innovation, Cost-Effectiveness, Strong Community Support, Transparency.
- Cons: Requires Significant Expertise, Steeper Learning Curve, Potentially Higher Initial Deployment Effort, Less "Out-of-the-Box" Polish than Commercial Counterparts.
Can you afford to be blind to what's happening on your network? The answer should be a resounding 'no'. Open-source provides the eyes you need without bankrupting your operation.
Arsenal of the Operator/Analyst
- Network Analysis Framework: Zeek
- IDS/IPS & NSM: Suricata
- Log Aggregation & Visualization: Elastic Stack (Elasticsearch, Logstash, Kibana)
- Packet Analysis: Wireshark (essential for deep dives into raw captures)
- Configuration Management: Ansible, SaltStack (for deploying and managing distributed sensor networks)
- Essential Reading: "The Network Security Monitoring Handbook" by Richard Bejtlich, "Practical Packet Analysis" by Chris Sanders.
- Relevant Certifications: Security+, OSCP (for broader offensive/defensive understanding), specialized vendor training for Elastic/Zeek/Suricata.
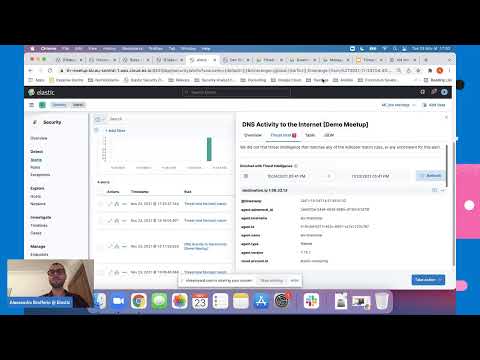
Defensive Workshop: Hunting Suspicious DNS Queries
Workshop: Detecting Malicious DNS Activity
- Objective: Identify DNS queries indicative of malicious activity, such as C2 communication or domain generation algorithms (DGAs).
- Tool: Zeek (specifically the `dns.log`) and Kibana.
- Step 1: Deploy Zeek Sensors. Ensure Zeek is deployed at strategic network points (e.g., egress points, internal server segments) to capture relevant DNS traffic. Configure Zeek to generate `dns.log`.
- Step 2: Ingest Logs into Elasticsearch. Use Logstash or Filebeat to forward Zeek's `dns.log` files to your Elasticsearch cluster.
- Step 3: Create a Kibana Dashboard. Navigate to Kibana and create a new dashboard.
- Step 4: Visualize Top DNS Queries. Add a "Data Table" visualization to show the top queried domains. Look for:
- Very long random-looking domain names (indicative of DGAs).
- Newly registered or suspicious-sounding domains.
- High query volume to a single, unusual domain.
- Step 5: Filter by Query Type. Add filters to examine specific query types (e.g., A, AAAA, TXT) which might contain encoded data.
- Step 6: Correlate with Source IPs. Add a "Data Table" showing the source IPs making the suspicious queries. Investigate these IPs for signs of compromise.
- Step 7: Set up Alerts. Configure Kibana alerts for specific patterns, such as unusual domain length or high query rates to non-standard domains.
This granular analysis of DNS traffic, powered by Zeek and visualized in Kibana, can uncover hidden malicious command and control channels that other security tools might miss.
Frequently Asked Questions
[ { "@context": "https://schema.org", "@type": "Question", "name": "Can open-source NDIR tools replace commercial solutions entirely?", "acceptedAnswer": { "@type": "Answer", "text": "For many organizations, yes. Open-source tools like Zeek, Suricata, and the Elastic Stack provide comprehensive visibility and detection capabilities. However, commercial solutions may offer added value in terms of integrated support, managed services, or advanced AI features. The choice often depends on the organization's expertise, budget, and specific requirements." } }, { "@context": "https://schema.org", "@type": "Question", "name": "What is the typical learning curve for these tools?", "acceptedAnswer": { "@type": "Answer", "text": "The learning curve can vary. Zeek requires understanding its scripting language and log formats. Suricata involves mastering rule syntax and tuning. The Elastic Stack has its own learning curve for setup and query language (KQL/Lucene). However, abundant documentation and active community support significantly ease the process." } }, { "@context": "https://schema.org", "@type": "Question", "name": "How do I integrate Zeek and Suricata effectively?", "acceptedAnswer": { "@type": "Answer", "text": "A common approach is to run Zeek to generate detailed logs of network activity (like connection details, HTTP requests, DNS queries) and then feed these logs, along with Suricata's alerts and logs, into the Elastic Stack for centralized storage, analysis, and visualization. This provides both granular event logging and real-time threat detection." } } ]
The Contract: Securing Your Digital Perimeter
The digital battlefield is vast, and the shadows hold countless threats. Open-source tools like Zeek, Suricata, and the Elastic Stack are not mere alternatives; they are essential components of any modern, effective defense. They offer the visibility needed to detect the undetectable, the insight to understand complex attacks, and the power to respond decisively. Your contract is clear: understand your network, arm yourself with the best available intelligence, and maintain constant vigilance. The question is no longer *if* you will face an incident, but *when* and how well you will be prepared to respond. The power is in your hands, in the code, in the community. Use it wisely.
Now, I've laid out the blueprint. The real test begins when you implement it. Can you configure Zeek to log every suspicious file transfer? Can you craft a Suricata rule to detect a novel phishing attempt? Can you build a Kibana dashboard that flags anomalies before they escalate? Share your findings, your challenges, and your triumphs in the comments below. Let's build a stronger defense, together.
```