The digital realm, a shadowy expanse where secrets whisper and vulnerabilities fester, demands constant vigilance. We, the guardians of Sectemple, understand that the best defense is forged from the ashes of offensive knowledge. Today, we dissect the art of threat hunting, not as a chaotic assault, but as a meticulous, analytical pursuit. Our quarry: Indicators of Compromise (IOCs), the digital footprints left by adversaries as they slither through your networks. Our weapon of choice: The Elastic Stack, a formidable arsenal for the blue team.
Elasticsearch, a titan in data collection and enrichment, offers a direct conduit to infuse your defenses with the sharpest threat intelligence. Integrated seamlessly with the Elastic Security detection engine, it empowers security analysts to identify malicious activity, transforming raw alerts into actionable intelligence through precise threat indicator matching. This meetup isn't about breaking down doors; it's about understanding the architectural weaknesses an attacker exploits, and building a fortress against them. We'll demystify Cyber Threat Intelligence (CTI) and showcase how Elastic elegantly ingests these vital feeds, forging robust CTI capabilities. For those seeking a deeper dive into the offensive arts and their defensive countermeasures, the path leads to comprehensive tutorials and cutting-edge security news.
Elastic Stack: Your Digital Fortress Architect
The Elastic Stack, a cornerstone for modern security operations, comprises Elasticsearch, Logstash, and Kibana, augmented by Beats for data shipping. This integrated system is more than just a log management solution; it's a dynamic platform for threat hunting, incident response, and continuous security monitoring. In the context of hunting for IOCs, its power lies in its ability to ingest, process, and analyze vast quantities of security-relevant data at scale.
- Elasticsearch: The heart of the stack, a distributed search and analytics engine. It stores and indexes your security data, making it searchable in near real-time. Its powerful query DSL (Domain Specific Language) allows for complex data retrieval, crucial for identifying patterns indicative of compromise.
- Logstash/Ingest Nodes: These components are responsible for collecting data from various sources, transforming it, and sending it to Elasticsearch. For threat hunting, this means ingesting logs from endpoints, firewalls, IDS/IPS, and crucially, threat intelligence feeds.
- Kibana: The visualization layer. Kibana allows analysts to explore, visualize, and dashboard their data. This is where raw data transforms into insights, enabling the visual identification of IOCs and anomalous behavior.
- Elastic Security: Built on the Elastic Stack, this integrated security solution provides SIEM, endpoint security (EDR), and threat intelligence capabilities. It offers pre-built detection rules that leverage CTI to identify known malicious activities.
Understanding Cyber Threat Intelligence (CTI)
Cyber Threat Intelligence (CTI) is not mere data; it's refined knowledge about existing or emerging threats that can be used to make informed decisions regarding the subject's response to that threat. It encompasses information about threat actors, their motives, capabilities, and the Tactics, Techniques, and Procedures (TTPs) they employ. For threat hunting, CTI serves as a crucial guide, providing known malicious IP addresses, domains, file hashes, and malware signatures – our IOCs.
"In the dark, the patterns are harder to see. CTI provides the flashlight and the map, turning chaos into an investigation." - cha0smagick
Integrating CTI into your security operations allows your detection mechanisms to proactively flag known malicious entities before they can cause significant damage. Without it, you're essentially hunting in the dark, relying solely on anomaly detection which can be prone to false positives and misses.
Ingesting Threat Intelligence Feeds with Elastic Stack
Translating raw CTI into actionable intelligence within the Elastic Stack involves several key steps. The goal is to make these IOCs readily available for matching against your ingested security logs.
Method 1: Threat Intelligence Platform (TIP) Integration
For mature security operations, a dedicated Threat Intelligence Platform (TIP) often serves as the central hub for managing and curating CTI. Many TIPs can export data in various formats (STIX/TAXII, CSV, JSON). Logstash or Elastic Agent can be configured to consume these feeds.
Example: Ingesting a CSV feed via Logstash
input {
file {
path => "/mnt/threat_intel/malicious_ips.csv"
start_position => "beginning"
sincedb_path => "/dev/null"
}
}
filter {
csv {
separator => ","
columns => ["ip_address", "threat_type", "source"]
}
mutate {
convert => {
"ip_address" => "string"
}
}
date {
match => ["timestamp", "ISO8601"]
}
}
output {
elasticsearch {
hosts => ["http://elasticsearch:9200"]
index => "threat_intel-ips-%{+YYYY.MM.dd}"
pipeline => "cti_enrichment_pipeline"
}
}
This Logstash configuration reads a CSV file, parses IP addresses and associated threat types, and indexes them into Elasticsearch under a specific index pattern. The `cti_enrichment_pipeline` can then be used.
Method 2: Direct Ingestion of Open-Source Feeds
Numerous open-source threat intelligence feeds are available. You can configure Logstash or, more efficiently, use Elastic Agent with built-in integrations to pull data from these sources.
Using Elastic Agent with the CTI Integration:
Elastic Agent's CTI integration simplifies the process. You can define the source URL of the threat intelligence feed (e.g., a raw URL from GitHub) and the type of IOCs it contains.
Example configuration snippet for Elastic Agent:
# agent_policy.yml
type: integration
name: threat_intelligence
# ... other configurations ...
streams:
- dataset: threat_intelligence.stix_taxii
# For STIX/TAXII feeds
data_sources:
- type: stix_taxii
url: "https://your.tip.server/stix/taxii"
collection_name: "malicious_indicators"
- dataset: threat_intelligence.ip_list
# For simple IP lists (e.g., raw URLs from GitHub)
data_sources:
- type: ip_list
url: "https://raw.githubusercontent.com/someuser/ioc-list/main/ips.txt"
threat_type: "malicious_ip"
source: "github_ioc_list"
- dataset: threat_intelligence.domain_list
# For domain lists
data_sources:
- type: domain_list
url: "https://raw.githubusercontent.com/someuser/ioc-list/main/domains.txt"
threat_type: "c2_domain"
source: "github_ioc_list"
This configuration allows Elastic Agent to pull IOCs directly and process them. The ingested data will be available in Elasticsearch, ready for use by the Elastic Security detection engine.
Building Robust CTI Capabilities with Elastic Security
Once your CTI is ingested into Elasticsearch, the next critical step is to leverage it within the Elastic Security SIEM and EDR solutions.
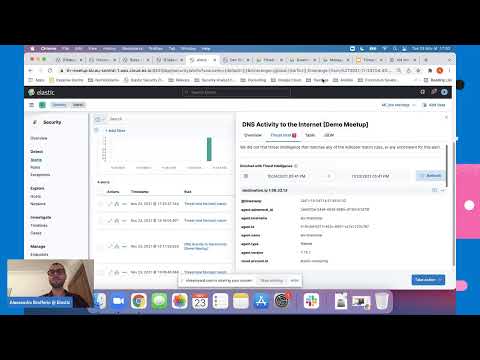
1. Creating Indicator Match Detections
Elastic Security allows you to create detection rules that match incoming event data against your CTI indices. This is the core of threat hunting with IOCs.
Within Kibana's Security App, you can navigate to Rules and create a new rule. Choose the "Indicator match" rule type.
- Query: Define a query that looks for matches between your event data and your CTI indices. For example, to detect connections to malicious IPs:
network.destination.ip : _exists_ and source.ip : _exists_ and "threat_intel-ips-*" : (ip_address)logs-*-network).threat_intel-ips-*).network.destination.ip) to fields in your CTI index (e.g., ip_address).threat_type) to a field in your event data for enrichment.This rule will trigger an alert whenever an event contains an IP address present in your threat intelligence feed.
2. Leveraging the CTI Feed in Endpoint Security (EDR)
Elastic Endpoint Security can ingest CTI directly. This allows the agent to perform real-time analysis on the endpoint itself, detecting malicious processes, file modifications, or network connections based on known IOCs before they even reach the SIEM.
By configuring Elastic Agent with the CTI integration and mapping these IOCs to the agent's detection rules, you create a powerful, distributed defense mechanism.
Threat Hunting Scenarios with Elastic Stack
Armed with CTI and the Elastic Stack, you can launch targeted threat hunts.
Scenario 1: Hunting for C2 Communications
Hypothesis: An adversary is communicating with a known Command and Control (C2) server.
Hunt:
- Ingest known C2 domains and IP addresses into Elasticsearch using the CTI integration.
- Create an Elastic Security rule to alert on any network connection (e.g., DNS requests, HTTP/S traffic) originating from your internal network to these CTI-listed IPs/domains.
- Run a search in Kibana over your network logs (e.g., proxy logs, firewall logs) for any logs containing the CTI IPs or domains in destination fields.
- If alerts are triggered or suspicious connections are found, investigate the source endpoint using Elastic Endpoint Security for further host-based IOCs (malware files, suspicious processes).
Scenario 2: File Integrity Monitoring for Malware Droppers
Hypothesis: Malware is being dropped onto endpoints, identifiable by its hash.
Hunt:
- Ingest known malicious file hashes (MD5, SHA1, SHA256) into Elasticsearch.
- Configure Elastic Endpoint Security to monitor file creation and modification events.
- Create a SIEM rule that triggers when a file hash observed on an endpoint matches a hash in your CTI index.
- Investigate any triggered alerts. Examine the file's origin, the process that created it, and its behavior using the endpoint security agent.
Veredicto del Ingeniero: ¿Vale la pena adoptar Elastic Stack para CTI?
The Elastic Stack, when leveraged for Cyber Threat Intelligence, is not merely a "nice-to-have"; it's a critical component of a proactive, defense-in-depth security posture. Its scalability, flexibility, and deep integration capabilities make it exceptionally well-suited for consuming, correlating, and acting upon threat intelligence. For organizations serious about moving beyond reactive security, investing in understanding and implementing CTI within Elastic is not just recommended – it's imperative. The ability to pivot from raw logs to actionable threat data by matching against known bad is a fundamental requirement for any modern SOC.
Arsenal del Operador/Analista
- Elastic Stack: Elasticsearch, Logstash, Kibana, Beats, Elastic Agent. (Essential)
- Threat Intelligence Feeds: Open-source lists (e.g., from GitHub repositories like MalwarePatrol, Abuse.ch) or commercial feeds.
- Elastic Security: SIEM and EDR capabilities for detection and endpoint analysis.
- Kibana: For visualization, dashboarding, and ad-hoc querying.
- Books: "The Elastic Stack Solution" by Jonathan McBride, "Threat Intelligence" by Scott J. Roberts.
- Certifications: Elastic Certified Engineer, Elastic Certified Analyst.
Taller Práctico: Fortaleciendo el Perímetro con CTI
Paso a Paso: Configurando una Alerta de CTI para IPs Maliciosas
- Pre-requisitos: Asegúrate de tener Elastic Stack desplegado y el Elastic Agent configurado para enviar logs de red (ej. Packetbeat, Filebeat con módulo de red) a Elasticsearch.
- Ingesta de CTI: Configura Elastic Agent con la integración de
threat_intelligence.ip_listpara consumir una lista de IPs maliciosas de un URL público (ej. una lista de IPs de malware conocidas). - Verificación de Ingesta: En Kibana, navega a Security > Threat Intelligence. Verifica que las IPs se están mostrando y que son indexadas en un índice como
logs-threat_intelligence-default. - Crear Regla de Detección: Ve a Security > Rules > Create new rule.
- Tipo de Regla: Selecciona Indicator match.
- Nombre de la Regla: "Malicious IP Connection Detected"
- Indices a Escanear: Especifica tu índice de logs de red (ej.
packetbeat-*ologs-network-*). - Indicator Index: Escribe el patrón de tu índice de CTI (ej.
logs-threat_intelligence-*). - Indicator Fields: Mapea
network.destination.ip(o el campo IP de destino en tus logs de red) al campo de la IP en tu índice CTI (ej.threat.ipsi tu CTI fue normalizado a esa forma, o el campo original de la CTI). - Threat Type Mapping (Opcional pero recomendado): Si tu CTI tiene campos de tipo de amenaza, mapea el campo de tu índice de red (ej.
threat.indicator.type) al campo de tipo de amenaza en tu CTI. - Acciones: Configura la acción para generar una alerta y enviarla a un webhook o crear un caso.
- Guardar y Habilitar: Guarda la regla y asegúrate de que esté habilitada.
- Prueba: Si es posible y ético, intenta realizar una conexión a una de las IPs maliciosas ingresadas desde una máquina de prueba dentro de tu red monitorizada para verificar que la alerta se dispara.
Preguntas Frecuentes
Q1: ¿Qué es un Indicador de Compromiso (IOC)?
Un IOC es una pieza de evidencia digital forense de que un incidente de seguridad ha ocurrido o está ocurriendo. Ejemplos incluyen direcciones IP maliciosas, nombres de dominio, hashes de archivos y certificados digitales.
Q2: ¿Puedo usar fuentes de CTI pagas con Elastic Stack?
Sí, Elastic Stack es muy flexible y puede ingerir datos de casi cualquier fuente de CTI, incluyendo feeds comerciales que a menudo ofrecen datos más curados y de mayor fidelidad.
Q3: ¿Cuál es la diferencia entre CTI y TTPs?
CTI se enfoca en "qué" es malicioso (IPs, hashes, dominios), mientras que TTPs (Tácticas, Técnicas y Procedimientos) describen "cómo" los adversarios operan (sus métodos y comportamientos). Ambos son vitales para una defensa completa.
Q4: ¿Elastic Security reemplaza a un firewall?
No. Elastic Security es una herramienta de detección y respuesta. Trabaja en conjunto con controles de seguridad perimetrales como firewalls, no los reemplaza. El firewall bloquea el acceso conocido, mientras que Elastic Security detecta actividades sospechosas que podrían haber eludido el perímetro.
El Contrato: Fortalece Tu Defensa
Tu red es un campo de batalla digital. Ignorar las intelignecias sobre los atacantes es como entrar en combate sin conocer al enemigo. Has visto cómo el Elastic Stack, un arma formidable en manos del defensor, puede ser el arquitecto de tu fortaleza digital. Ahora, el contrato es tuyo:
Desafío: Identifica una fuente de threat intelligence de código abierto que contenga hashes de malware. Configura un pipeline (ya sea con Logstash o Elastic Agent) para ingerir estos hashes en tu instancia de Elasticsearch. Una vez ingeridos, crea una regla de detección básica en Elastic Security para alertar si algún proceso iniciado en tu red tiene un hash que coincida con tu feed de CTI. Documenta tu proceso y comparte tus hallazgos o dificultades en los comentarios.
El conocimiento es poder, pero la aplicación es soberanía. Demuestra tu dominio.
