Table of Contents
- Understanding the Mechanism: Nmap's Role
- Threat Actors' Tactics and Techniques
- Reconnaissance and Initial Access
- Defensive Countermeasures and Detection
- Securing the Perimeter: Hardening Network Services
- Arsenal of the Analyst
- FAQ
- The Contract: Fortifying Your Network Foundation
Understanding the Mechanism: Nmap's Role
Nmap (Network Mapper) is a utility, a digital Swiss Army knife for network exploration and security auditing. Its core function is to discover hosts and services on a computer network by sending packets and analyzing the responses. However, its true power, and the vector for potential misuse, lies in the Nmap Scripting Engine (NSE). NSE allows users to write and share scripts to automate network tasks of all kinds, including network discovery, vulnerability detection, and vulnerability exploitation. When we talk about "getting a shell with Nmap," it's rarely about Nmap *itself* exploiting a zero-day. Instead, it typically involves:- Service Enumeration: Identifying running services and their versions.
- Vulnerability Script Invocation: Using NSE scripts designed to interact with specific services in ways that might reveal vulnerabilities or misconfigurations.
- Triggering Exploits or Misconfigs: These scripts can, in turn, trigger conditions on the target service that result in the attacker receiving a network shell (e.g., a bind shell or a reverse shell).
Threat Actors' Tactics and Techniques
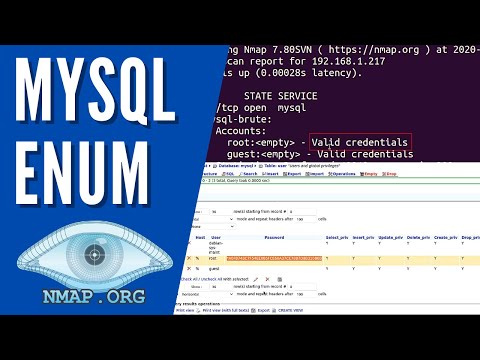
A sophisticated threat actor understands that direct exploitation of Nmap is unlikely. Their method is to use Nmap as an advanced reconnaissance and interaction tool. They might employ NSE scripts for:- Brute-Force Attacks: Using scripts like
brute.nseor specific service brute-force scripts (e.g.,ftp-brute.nse,ssh-brute.nse) to guess credentials on exposed services. A successful brute-force on SSH, for instance, grants direct shell access. - Exploiting Known Vulnerabilities: Certain NSE scripts are designed to check for and, in some cases, leverage known vulnerabilities in specific service versions. If a vulnerability allows for remote command execution, and Nmap can trigger it, a shell can be established.
- Configuration Exploitation: Discovering and exploiting insecure configurations. For example, a misconfigured TFTP server might allow file uploads that could later be used to gain code execution. An NSE script could discover and interact with such a service.
- Information Gathering for Further Exploitation: Even if an NSE script doesn't directly yield a shell, it can provide critical information (e.g., exact software versions, user enumeration) that is then fed into more potent, targeted exploit frameworks.
"The attacker doesn't need to break into the castle if the gate guard left the door wide open and is ready to hand over the keys after a polite request."
Reconnaissance and Initial Access
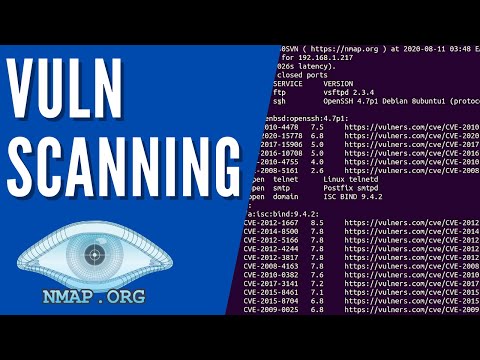
The journey typically begins with reconnaissance. An attacker scans a target network, searching for open ports and the services running on them."Port scanning is the digital equivalent of casing a joint. You're looking for the unlocked windows, the back doors, the weak spots in the facade."Nmap excels at this. Once a promising service is identified (e.g., an old version of Apache, an exposed FTP server, an administrative interface), the attacker then deploys specific NSE scripts. **Example Scenario: Exploiting an FTP Server** 1. **Discovery:** Attacker scans the target IP `192.168.1.100` for open ports.
nmap -sV 192.168.1.100
```
Output reveals TCP port 21 (FTP) is open, running `vsftpd 2.3.4`. This version is known to have a vulnerability allowing arbitrary command execution.
2. **Exploitation Trigger:** The attacker uses an NSE script designed to exploit this specific vulnerability.
```bash
nmap --script ftp-vsftpd-backdoor,ftp-anon -p 21 192.168.1.100
```
The `ftp-vsftpd-backdoor` script attempts to trigger a hidden backdoor in the `vsftpd 2.3.4` version. If successful, it can establish a shell.
The attacker sets up a listener on their machine, waiting for the connection.
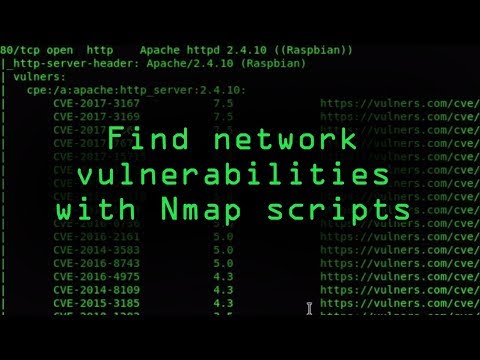
Defensive Countermeasures and Detection
From a defender's standpoint, the critical aspect is detecting *and* preventing such actions.Detection Strategies:
- Network Traffic Analysis: Monitor network traffic for unusual Nmap scan patterns, especially those involving NSE scripts. Tools like Suricata, Zeek (Bro), or commercial SIEMs can be configured to alert on suspicious Nmap activity. Look for connections to non-standard ports using common service banners or patterns indicative of script execution.
- Log Analysis: Scrutinize logs from firewalls, IDS/IPS, and individual services. Anomalies could include unexpected login attempts, command execution on services that shouldn't allow it, or unusual data transfers.
- Endpoint Detection and Response (EDR): EDR solutions can detect the execution of Nmap on internal systems, which might indicate a compromise from within or an attacker moving laterally. They can also detect shell processes initiated by unusual parent processes.
- IDS/IPS Signatures: Maintain updated signatures for anomaly detection related to Nmap and common NSE scripts. While attackers may try to obfuscate their tools, many signature sets can identify common patterns.
Prevention Strategies:
- Regular Patching and Updates: The most effective defense is to eliminate known vulnerabilities. Ensure all services are updated to their latest stable versions, including Nmap itself if it's being used for legitimate purposes.
- Principle of Least Privilege: Ensure services run with the minimum necessary privileges. This limits the impact if a shell is acquired.
- Firewall Rules: Implement strict firewall rules, allowing only necessary ports and protocols. Block all inbound traffic by default and explicitly permit required outbound connections.
- Network Segmentation: Segment the network to limit lateral movement. If one segment is compromised, the attacker's access to other critical segments is restricted.
- Disable Unnecessary Services: If a service isn't required, disable it. Every open port is a potential attack vector.
Securing the Perimeter: Hardening Network Services
The foundation of network security rests on hardening the services exposed to the network. Nmap scripts are merely tools to probe and exploit weaknesses; the weaknesses themselves must be addressed.Key Hardening Practices:
- Service Configuration: Review the configuration of every network service. Disable anonymous access for FTP, enforce strong authentication for SSH, and secure administrative interfaces.
- Application-Level Security: For web servers, applications, and databases, implement robust input validation, output encoding, and parameterized queries to prevent injection attacks.
- Access Control Lists (ACLs): Use ACLs at the host and network levels to restrict which IP addresses can connect to specific ports and services.
- Intrusion Prevention Systems (IPS): Deploy IPS solutions that can actively block malicious traffic patterns, including those associated with common Nmap scripts, in real-time.
Arsenal of the Analyst
To effectively defend against threats leveraging tools like Nmap for malicious purposes, an analyst needs a robust set of tools and knowledge.- Nmap: Ironically, the best tool to understand how Nmap can be misused is Nmap itself. Use it ethically for legitimate scanning and auditing.
- Wireshark/tcpdump: For deep packet inspection and analysis of network traffic. Essential for understanding the exact nature of the communication.
- Zeek (Bro): A powerful network security monitor that can generate detailed logs of network activity, detect anomalies, and even execute custom analysis scripts.
- Suricata/Snort: Intrusion detection and prevention systems that can be configured with rules to detect malicious Nmap activity.
- Metasploit Framework: While an exploitation framework, it's invaluable for understanding how exploits work and for testing defenses against them.
- SIEM Solutions (Splunk, ELK Stack, QRadar): Centralized logging and analysis platforms to correlate events across the network and identify suspicious activities.
- Security Certifications: Certifications like OSCP (Offensive Security Certified Professional) provide hands-on experience with offensive techniques, which is crucial for developing effective defensive strategies. Even certifications like CISSP (Certified Information Systems Security Professional) offer a broad understanding of security principles.
- Books: "The Nmap Network Scanner: The Official Network Exploration Toolkit" for deep knowledge of Nmap, and "The Web Application Hacker's Handbook" for understanding networked application vulnerabilities.
FAQ
Q1: Can Nmap itself be "hacked" to get a shell?
Nmap itself is a tool. While software can have vulnerabilities, the common scenario of "getting a shell with Nmap" refers to using Nmap's scripts (NSE) to interact with *vulnerable services* on a target system, thereby eliciting a shell from that service, not from Nmap.
Q2: Are all Nmap scripts malicious?
Absolutely not. Nmap Scripting Engine (NSE) is an incredibly powerful and versatile tool for legitimate network administration, security auditing, and vulnerability assessment. Only a subset of scripts can be used for potentially malicious purposes when combined with vulnerable services.
Q3: How can I detect if someone is using Nmap aggressively on my network?
Monitor network traffic for port scanning patterns. IDS/IPS systems are designed to detect this. Analyze firewall logs for a high volume of connection attempts across many ports or hosts. Look for the execution of Nmap on internal machines if considered unauthorized.
Q4: What's the difference between using Nmap for vulnerability scanning and for exploitation?
Vulnerability scanning, even with NSE, typically involves probing services to identify potential weaknesses or information that could be exploited. Exploitation, in this context, means using an Nmap script (or another tool) to actively trigger a vulnerability that grants unauthorized access, such as a shell.
The Contract: Fortifying Your Network Foundation
The ability to "get a shell" via Nmap is not a reflection of Nmap's inherent maliciousness, but a testament to the exposed vulnerabilities on systems that Nmap can probe. Your network is your domain. The contract is this: **you are responsible for its integrity.** Your challenge is to perform a proactive audit of your own network's perimeter. Identify all exposed services. For each service, determine:- Is it strictly necessary? If not, shut it down.
- Is it running the latest patched version? If not, patch it immediately.
- Is it configured securely? Review configurations, enforce strong authentication, and limit access.
- Are your IDS/IPS and firewall rules adequate? Test them. Can they detect aggressive scanning or known NSE script patterns?