The digital realm is a labyrinth of data, and within its intricate pathways, services like MySQL often guard critical information. They whisper secrets, but only to those who know how to listen. Tonight, we're not just listening; we're interrogating. We're peeling back the layers of a MySQL instance using a tool as old as the network itself, but as sharp as ever: Nmap. Forget the fancy dashboards; we're going manual, offensive, and analytical. This is about understanding the attack surface before the adversary does.
Table of Contents
- Understanding Nmap's Offensive Stance
- The MySQL Attack Vector: Port 3306 Screaming to Be Probed
- Phase 1: Recon - Host Discovery and Port Scanning
- Phase 2: Service and OS Detection - Building the Profile
- Phase 3: Deep Dive with Nmap Scripting Engine (NSE)
mysql-enum.nse: The Analyst's Best Friend- Practical Walkthrough: Command Execution
- Arsenal of the Operator
- Verdict of the Engineer
- Frequently Asked Questions
- The Contract: Securing Your MySQL Perimeter
Understanding Nmap's Offensive Stance
Nmap is more than just a scanner; it’s a reconnaissance tool for the modern age. For us, it's the initial probe in a complex engagement. It allows us to map the terrain, identify potential entry points, and understand the services running on target hosts. When it comes to MySQL enumeration, Nmap, armed with the right scripts, transforms from a passive surveyor into an active interrogator. We're not just looking for open ports; we're looking for vulnerabilities, misconfigurations, and the digital breadcrumbs left by lazy administrators.
This isn't about network mapping for IT support. This is about building an offensive profile. Every open port, every banner, every version number is a data point that can be weaponized. Our objective: understand the attack surface of MySQL instances to either exploit them or, more importantly, to build better defenses. The Nmap Scripting Engine (NSE) is our secret weapon here, allowing us to deploy Lua scripts that can perform complex tasks, from vulnerability detection to brute-force attacks.
The MySQL Attack Vector: Port 3306 Screaming to Be Probed
MySQL typically runs on TCP port 3306. This is the digital doorstep for your database. If this port is exposed to the internet, or even just accessible within a less-than-secure internal network segment, it becomes a prime target. Understanding how to enumerate this service is critical for both penetration testers and system administrators who want to ensure their databases aren't broadcasting information to the wrong ears. Attackers often leverage default credentials or known vulnerabilities in older MySQL versions to gain initial access. Our goal is to find these exposed doors before they are exploited.
The information gained from MySQL enumeration can range from user privileges and database names to sensitive data leaks if proper authentication and authorization are not enforced. Think of it as a reconnaissance mission where you're trying to determine who lives in the house, what rooms they have, and if any doors are unlocked. This information is crucial for escalating privileges or identifying data that could be exfiltrated.
Phase 1: Recon - Host Discovery and Port Scanning
Before we can enumerate MySQL, we need to know where it is. This begins with solid reconnaissance. We identify live hosts on the network and then scan them for open ports, specifically looking for that tell-tale 3306.
A typical offensive approach would involve:
- Host Discovery: Using Nmap's ping scans (e.g.,
-PEfor ICMP echo requests,-PAfor TCP ACK probes,-PSfor TCP SYN probes) to identify active hosts. Consider faster, stealthier methods if needed, but for enumeration, a thorough scan is key. - Port Scanning: Once live hosts are identified, we perform port scans. A basic TCP SYN scan (
-sS) is common for its speed and stealth. We'll focus on port 3306, but scanning for common ports (-p-for all 65535 ports, or-Ffor fast scan of top 100 ports) can reveal other opportunities.
The command might look something like this for a targeted scan:
nmap -sS -p 3306 <target_IP_or_range> -oN nmap_mysql_scan.txtThis command initiates a SYN scan (`-sS`) targeting only port 3306 (`-p 3306`) against your specified target(s) and saves the output to a file named `nmap_mysql_scan.txt`. Analyzing this output is the first critical step to identify potential MySQL servers.
Phase 2: Service and OS Detection - Building the Profile
With potential MySQL ports identified, the next logical step is to confirm the service running and gather more context about the system. Nmap's service version detection (`-sV`) is invaluable here. It probes open ports with a series of probes to determine the application and version number.
Additionally, operating system detection (`-O`) can provide insights into the underlying OS, which might hint at default configurations or known vulnerabilities specific to that platform (e.g., Linux vs. Windows). While not directly related to MySQL enumeration, this information builds a more complete profile of the target, aiding in subsequent attack planning.
A command incorporating these options might be:
nmap -sV -O -p 3306 <target_IP> -oN nmap_mysql_profile.txtThis command not only checks for port 3306 but also attempts to identify the service version and the operating system of the target host. The output is saved for detailed analysis. It's in this phase that you might see banners revealing older, potentially vulnerable MySQL versions (e.g., "MySQL 5.0.12").
Phase 3: Deep Dive with Nmap Scripting Engine (NSE)
This is where Nmap truly shines for offensive security. The Nmap Scripting Engine (NSE) allows users to write and share scripts (in Lua) to automate a wide variety of networking tasks. For MySQL enumeration, NSE provides powerful specialized scripts that go far beyond simple port and version detection.
NSE scripts can perform tasks like:
- Discovering MySQL users and their associated privileges.
- Extracting database schemas and table names.
- Checking for weak or default credentials.
- Identifying specific MySQL vulnerabilities.
To leverage NSE scripts, you typically use the -sC flag (which runs default, safe scripts) or specify individual scripts using the --script option.
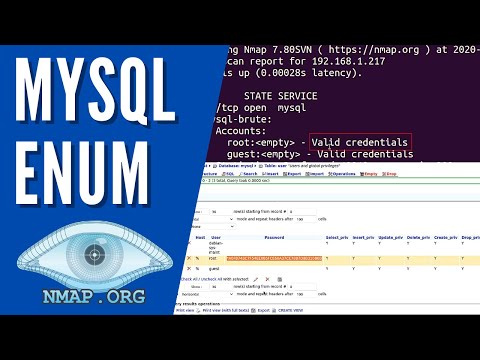
mysql-enum.nse: The Analyst's Best Friend
Among the many NSE scripts, mysql-enum.nse is particularly potent for MySQL enumeration. This script can connect to a MySQL server and attempt to gather detailed information about the databases, users, roles, and privileges configured on that server.
To run this script specifically:
nmap -p 3306 --script mysql-enum <target_IP> -oN nmap_mysql_enum.txtIf the MySQL server is configured to allow passwordless login for certain users, or if you have a set of common credentials to test, this script can yield valuable insights. It's crucial to understand that running such enumeration scripts against systems you do not have explicit permission to test is illegal and unethical. This guide is for educational purposes and authorized penetration testing scenarios.
The output from mysql-enum.nse might look like this (simplified):
Interesting ports on <target_IP> (<target_hostname>):
PORT STATE SERVICE VERSION
3306/tcp open mysql MySQL 5.7.33-0ubuntu0.18.04.1
Host script results:
| mysql-enum:
| Databases:
| information_schema
| mysql
| performance_schema
| sys
| mydatabase
| Users:
| root@localhost (Superuser: YES, SSL required: NO)
| admin@'%' (Superuser: NO, SSL required: NO)
| ... (further details on privileges and tables)
|_ Comments: MySQL server: 5.7.33-0ubuntu0.18.04.1
Practical Walkthrough: Command Execution
Let's walk through a simulated scenario. Assume we've identified a target IP, 192.168.1.105, with MySQL running on port 3306.
- Initial Scan: Start with identifying the open port and service.
This confirms port 3306 is open and identifies it as MySQL, possibly with a version.nmap -sV -p 3306 192.168.1.105 - NSE Enumeration: Now, deploy the specialized script.
Analyze `mysql_enumeration_results.txt`. Look for interesting databases like `information_schema` and `mysql`, and critically, any user accounts with broad privileges or accounts accessible from remote hosts (`'%'`).nmap -p 3306 --script mysql-enum 192.168.1.105 -oN mysql_enumeration_results.txt - Credential Testing (Ethical Context): If the script reveals a user like `admin@'%'` with weak or default credentials, you might consider using Nmap's brute-force capabilities with a wordlist. This is a high-risk step and requires explicit authorization.
Note: `users.txt` and `pass.txt` would contain lists of usernames and passwords to test. Never use this without proper authorization.nmap -p 3306 --script mysql-brute --script-args userdb=./users.txt,passdb=./pass.txt 192.168.1.105
Arsenal of the Operator
To effectively perform this kind of enumeration, a well-equipped operator needs the right tools. Your toolkit should include:
- Nmap: The cornerstone of network reconnaissance. Invest time in mastering its advanced features, especially NSE. Consider the Nmap for Penetration Testing course for a deep dive.
- Wireshark: For analyzing network traffic and understanding the packets Nmap sends and receives. It's invaluable for debugging scans and understanding protocol behavior.
- Metasploit Framework: While Nmap is for enumeration, Metasploit often contains modules for exploiting identified MySQL vulnerabilities or for credential stuffing.
- SQLMap: A powerful, automated SQL injection tool that can also be used for database enumeration and exploitation beyond Nmap's capabilities.
- Wordlists: Essential for brute-force attacks. Tools like SecLists on GitHub provide comprehensive collections.
- Books: "The Nmap Network Scanner: The Official Nmap User's Guide" and "The Web Application Hacker's Handbook" are foundational.
Mastering these tools, especially Nmap and its scripting engine, is non-negotiable for anyone serious about offensive security or robust database defense. Certifications like the OSCP heavily emphasize these reconnaissance skills.
Verdict of the Engineer
Nmap's capabilities for MySQL enumeration are robust and indispensable for offensive security professionals. The combination of its core scanning features with the power of the Nmap Scripting Engine, especially `mysql-enum.nse`, offers unparalleled insight into MySQL server configurations and user privileges.
- Pros: Highly versatile, scriptable, widely adopted, excellent for initial reconnaissance and identifying potential attack vectors. The
-sVand NSE scripts provide deep enumeration capabilities. - Cons: Can be noisy if not configured carefully. Brute-force scripts require careful handling and explicit authorization to avoid detection or legal issues. May require additional tools for deeper exploitation or data exfiltration.
Conclusion: Nmap is foundational. For MySQL enumeration, it's your first line of inquiry. Don't underestimate its power, but always wield it responsibly.
Frequently Asked Questions
What is the default port for MySQL?
The default TCP port for MySQL is 3306.
Can Nmap alone exploit MySQL vulnerabilities?
Nmap's primary role is enumeration and vulnerability detection. While some NSE scripts might perform basic exploitation, for complex exploits, you'd typically use frameworks like Metasploit.
Is using mysql-enum.nse on a server I don't own legal?
No, accessing or enumerating systems without explicit, written authorization is illegal and unethical. Always ensure you have proper permission.
How can I make my Nmap scans stealthier when enumerating MySQL?
Techniques include fragmentation, decoys, and using less common scan types, but these can also reduce scan speed and accuracy. For enterprise environments, consider using Nmap in conjunction with IDS/IPS evasion techniques, often detailed in advanced penetration testing courses.
What are the risks of exposing MySQL port 3306 to the internet?
Exposing port 3306 to the internet without proper firewall rules, strong authentication, and security hardening is extremely risky. It makes your database vulnerable to unauthorized access, data breaches, credential brute-forcing, and potential exploitation of known vulnerabilities.
The Contract: Securing Your MySQL Perimeter
You've seen how Nmap can lift the veil on exposed MySQL services. The knowledge is power, but power demands responsibility. Your contract is simple: use this insight to defend. If you've identified an open 3306 port on a system you manage, the next step isn't to look for more users, but to lock the door.
Your Challenge: For every MySQL instance you manage, review its network exposure. Is port 3306 accessible externally? If so, implement strict firewall rules to limit access only to necessary internal IP addresses or trusted jump hosts. Implement strong, unique passwords for all MySQL users, and consider disabling remote root access. Regularly audit user privileges and remove unnecessary accounts. Document your findings and remediation steps. The true win isn't finding a vulnerability; it's patching it before it’s used against someone.
Now, go secure your perimeter. The shadows never sleep, and neither should your vigilance.

No comments:
Post a Comment