The digital ether is a minefield. Every ping, every call, leaves a trace, a whisper in the vast network. A phone number, seemingly innocuous, is often the key that unlocks a vault of hidden truths. Today, we don't just look for data; we hunt it. We track the ghosts in the machine, using the echoes of digits to reconstruct a digital identity. This isn't about idle curiosity; it's about professional reconnaissance.
Table of Contents
The Digital Fingerprint
In the clandestine world of Open Source Intelligence (OSINT), the seemingly mundane can become your most powerful weapon. A phone number, a string of digits that connects people across distances, is a prime example. It's a direct line, a potential identifier that can lead to a cascade of linked information. When conducting reconnaissance, whether for a bug bounty hunt, threat hunting, or due diligence, that number is your first thread to pull.
Historically, a single number could reveal a wealth of data: the carrier, the region, even associated accounts. However, the landscape is constantly shifting. As privacy concerns and regulations evolve, so do the methods attackers and defenders alike must employ. Tools that once offered a treasure trove of information may now be restricted, requiring more sophisticated techniques and a deeper understanding of data aggregation.
This guide delves into how a phone number can serve as a critical starting point for your OSINT operations. We'll explore the evolution of tools, the current challenges, and the methodologies that remain effective in extracting actionable intelligence. Remember, in this game, knowledge is power, and understanding the tools is the first step to mastering them.
Phoneinfoga: The Command-Line Interrogator
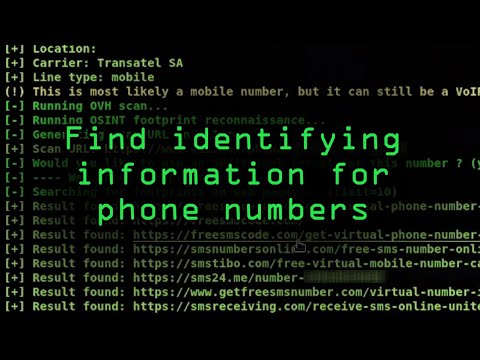
When precise, rapid data extraction from a phone number is required, the command line is often the most efficient battlefield. Phoneinfoga stands out as a robust tool for this purpose. It's designed to gather information about a phone number, including carrier details, SIM information, and VoIP capabilities. This isn't just about passively collecting data; it's about actively interrogating the digital infrastructure.
The power of Phoneinfoga lies in its ability to parse and present complex data structures in an easily digestible format. For security professionals, this means quickly identifying potential points of contact, understanding the technical infrastructure behind a number, and flagging any anomalies that warrant further investigation. Its efficacy is a testament to the principle that direct, programmatic access to information often yields the most valuable insights.
While the landscape of OSINT tools has seen disruptions, as noted in 2019 regarding the IntelTechniques suite, tools like Phoneinfoga often persevere due to adaptable development cycles. Mastery of such command-line utilities is crucial; it’s the bedrock upon which more complex investigations are built. For those aiming for advanced certifications or seeking to automate reconnaissance, understanding and implementing tools like Phoneinfoga is non-negotiable. Consider it your fundamental handshake with the target's digital identity.
Navigating the Shifting Sands: Web-Based Tools
The digital intelligence landscape is fluid, a constant cat-and-mouse game between those who seek to expose information and those who try to obscure it. Web-based OSINT tools, once a convenient one-stop shop, have faced significant challenges. Increased DDoS attacks, Digital Millennium Copyright Act (DMCA) takedowns, and cease-and-desist orders have led to the removal or restriction of many previously popular platforms. IntelTechniques, for example, saw some of its aggregated tools taken offline.
This doesn't render phone number analysis obsolete; it merely elevates the significance of adaptable strategies. Instead of relying on a single, comprehensive web application, the modern OSINT operator must be prepared to:
- Utilize Individual Company Tools: Many mobile carriers and telecommunication providers offer their own online lookups or APIs. While these might be restricted or require specific credentials, they can offer direct and authoritative information.
- Leverage Social Media Platforms: Thoroughly investigate any social media presence linked to the phone number. Platforms like LinkedIn, Twitter, and even more niche forums can reveal professional connections, personal interests, and geographical data.
- Explore Aggregation and Scraping Techniques: For advanced users, custom scripts or specialized APIs might be employed to scrape data from various publicly accessible sources, then aggregate and cross-reference it. This requires a deeper technical skillset and an understanding of web scraping ethics and legalities.
- Consider Paid OSINT Services: For critical investigations or professional engagements, investing in specialized, legitimate OSINT services can provide access to curated databases and advanced analytical tools. These services often have the resources to navigate the complex legal and technical hurdles.
The key takeaway is resilience. When one door closes, a skilled investigator finds another, or builds a new one. The era of easily accessible, comprehensive web OSINT tools might be waning, but the demand for the intelligence they provided continues to grow. This shift necessitates a deeper dive into foundational techniques and a commitment to continuous learning in the ever-evolving OSINT domain. Investing in a comprehensive course on ethical hacking and OSINT principles, such as those leading to the OSCP certification, will provide the foundational knowledge to navigate these complexities.
Synthesizing the Echoes: From Data to Intelligence
Gathering raw data is merely the first act. The true value of OSINT lies in the synthesis and analysis—transforming disconnected pieces of information into a coherent, actionable intelligence picture. A phone number is just a string of digits until it’s cross-referenced with other digital breadcrumbs.
Once you have extracted initial details using tools like Phoneinfoga or by exploring web-based resources, the real work begins. This involves:
- Correlation: Link the phone number to other identifiers. Does it appear in public directories, social media profiles (even indirectly), or data breach dumps? Search engines and specialized databases are your allies here.
- Contextualization: What does the carrier, region, or type of service (mobile, landline, VoIP) tell you about the target's potential location and operational environment? A VoIP number, for instance, might suggest a more transient or pseudonymous digital presence.
- Pattern Recognition: Look for recurring patterns in how the number is used or listed. Are there specific online communities or forums where it appears? Does it correlate with specific online activities?
- Timeliness Analysis: When was the number first associated with this individual or entity? Is the information current, or is it stale data from years past? The age of the data significantly impacts its reliability.
This stage is where the skills honed through dedicated study and practice truly shine. It requires critical thinking, a deep understanding of how data propagates online, and the technical acumen to efficiently query and cross-reference vast datasets. Professionals engaged in bug bounty programs often leverage this analytical depth to identify user accounts or associated infrastructure that might harbor vulnerabilities.
Arsenal of the Operator
To navigate the complexities of OSINT investigations, particularly concerning phone numbers, a well-equipped arsenal is indispensable:
- Phoneinfoga: As discussed, this command-line tool is fundamental for initial phone number data extraction.
pip install phoneinfogais your first step. - Search Engines: Google, Bing, DuckDuckGo. Master advanced search operators (`site:`, `inurl:`, `filetype:`, `+`, `-`) to refine your queries.
- Social Media Platforms: LinkedIn for professional context, Twitter for real-time information and connections, Facebook for broader personal data (if accessible and ethically permissible).
- Data Breach Archives: Tools and databases that aggregate leaked credentials and personal information (use with extreme caution and ethical consideration).
- Specialized OSINT Frameworks: While some have been curtailed, research alternatives and understand how they function. Platforms like Maltego can be powerful for visualizing relationships.
- VPN and Secure Browsing Tools: Essential for maintaining anonymity and avoiding attribution during your investigations. Consider using Tor Browser for sensitive reconnaissance.
- Reference Materials: Books like "The Web Application Hacker's Handbook" (while focused on web apps, it instills critical thinking applicable to all security domains) and "Open Source Intelligence Techniques" by Michael Bazzell are invaluable for foundational knowledge, even if specific tools mentioned are outdated.
Investing in your skillset is paramount. Consider pursuing certifications like the Certified Ethical Hacker (CEH) or, for deeper offensive capabilities, the Offensive Security Certified Professional (OSCP). These programs equip you with the methodologies to perform thorough investigations and understand exploitation vectors.
Taller Práctico: Uncovering Secrets with Phoneinfoga
Let's get our hands dirty. We'll use Phoneinfoga to extract information from a hypothetical phone number. For this demonstration, we'll use a placeholder number. Remember to replace it with the actual number you are legally authorized to investigate.
-
Install Phoneinfoga: If you haven't already, clone or install Phoneinfoga. On most Linux systems, this involves:
git clone https://github.com/typicode/phoneinfoga.git cd phoneinfoga pip install -r requirements.txt -
Run the Basic Query: Execute Phoneinfoga with a phone number. Ensure you use the correct international format (e.g., +1 for the US).
phoneinfoga -n +15551234567Note: Replace
+15551234567with the target number. -
Analyze the Output: Phoneinfoga will now query various sources and present the findings. Look for:
- Carrier: The mobile network operator.
- SIM Details: Information about the SIM card, potentially including issuer.
- VoIP: Whether the number is associated with a Voice over IP service.
- Country/Region: Geographical location data.
-
Explore Aliases (if available): Phoneinfoga can also search for associated online aliases. Run:
phoneinfoga -n +15551234567 --find-social-mediaThis command attempts to link the number to social media profiles, providing additional avenues for investigation. Always verify these findings through manual cross-referencing.
-
Advanced Options: Explore other flags like
--scan-portsor--osint-onlyto tailor your search. Consult the tool's documentation for a complete list of capabilities.
This practical exercise demonstrates how a command-line tool can rapidly surface initial intelligence. The subsequent steps involve integrating this data into a broader investigation, searching for associated online presences, and verifying the information through multiple trusted sources. Remember, the goal is not just information, but reliable, verifiable intelligence.
Preguntas Frecuentes
¿Es legal realizar OSINT sobre un número de teléfono?
La legalidad depende completamente de tu jurisdicción, la fuente de la información y el propósito de tu investigación. Acceder a bases de datos privadas sin autorización o utilizar información de forma malintencionada es ilegal. Siempre opera dentro de los marcos legales y éticos, y asegúrate de tener la autorización necesaria.
¿Qué debo hacer si las herramientas de OSINT basadas en web ya no funcionan?
Adapta tu enfoque. Utiliza herramientas de línea de comandos más granulares como Phoneinfoga, investiga las herramientas individuales de cada compañía, explora bases de datos de filtraciones de datos (con precaución), y considera la posibilidad de invertir en servicios de OSINT profesionales. La resiliencia y la adaptabilidad son claves.
¿Cómo puedo verificar la autenticidad de la información obtenida?
La verificación es crucial. Busca la misma información a través de múltiples fuentes independientes. Cruza los datos con perfiles de redes sociales, registros públicos, o comunicados oficiales. Un solo punto de datos rara vez es suficiente para confirmar algo de manera concluyente.
¿Qué tipo de información se puede encontrar a partir de un número de teléfono?
Dependiendo de las herramientas y las fuentes disponibles, puedes obtener: información del operador móvil, detalles de la SIM, ubicación geográfica aproximada, posibles nombres asociados, cuentas de redes sociales vinculadas, y registros de su uso en brechas de datos.
¿Existen certificaciones recomendadas para especializarse en OSINT?
Sí. Si bien OSINT es a menudo una habilidad transversal, hay certificaciones que pueden validar tu experiencia. Considera la Certified Ethical Hacker (CEH) para una base amplia, o investiga programas más especializados en inteligencia o forense digital. La perseverancia y la práctica constante son tus mejores credenciales.
The Contract: Your Next Move
The digital phantom you're tracking leaves faint signals. A phone number is just one of them, but a vital one. You've seen the tools, the methods, the challenges. Now, the contract is yours to fulfill.
Your contract: Choose a phone number (legally accessible to you, perhaps your own or a freely provided test number from a reputable OSINT practice platform) and run it through Phoneinfoga. Document at least three distinct pieces of information you extract. Then, attempt to find a publicly available social media profile (like LinkedIn or Twitter) that *might* be associated with that number's owner. Report your findings, and importantly, highlight any discrepancies or points of uncertainty. Did the tools provide reliable data? Were there false positives? What challenges did you encounter?
This isn't just an exercise; it's your entry into the field. The digital realm is a labyrinth. Navigate it with precision, integrity, and an insatiable curiosity. The secrets are there for those who know how to look.
