The digital realm is a battlefield. Every system, every connection, a potential point of compromise. We build defenses, layer them thick, and then we get complacent. That's when the shadows move. Multi-Factor Authentication (MFA) has been hailed as the last bastion, the impenetrable wall. But walls, in the right hands, can be scaled, bypassed, or sometimes, simply walked around. Today, we're not dissecting how to exploit it; we're dissecting how it's broken, so you, the defender, can anticipate the move and reinforce your perimeter. This is about understanding the enemy's playbook to sharpen yours.
The allure of MFA is its promise of layered security. It adds a second, third, or even fourth checkpoint to verify identity, moving beyond the static weakness of a password. Yet, the implementation, the human element, and the sheer ingenuity of attackers mean that "easily bypassed" is a phrase that keeps security professionals up at night. We'll break down the anatomy of these bypasses, focusing on the reconnaissance, the tools, and the critical junctures where MFA's strength falters, and how you can spot the signs before the breach is irreversible.
Table of Contents
- Understanding MFA Weaknesses: The Core Vulnerabilities
- Evilginx2: The Adversarial Proxy in Action
- Phishing Beyond the Credentials: Session Hijacking
- Detecting and Mitigating MFA Bypass
- The Future of Authentication: Beyond Today's Weaknesses
- Engineer's Verdict: MFA's Role in a Modern Defense
- Operator/Analyst Arsenal
- Frequently Asked Questions
- The Contract: Fortifying Your MFA
Understanding MFA Weaknesses: The Core Vulnerabilities
MFA isn't a monolithic entity. It's a combination of factors, and it's often the integration, not the core technology, that becomes the weak link. Attackers are less interested in breaking cryptographic algorithms and more interested in tricking systems and users. Common attack vectors include:
- Phishing: The classic. Luring users into entering credentials and then, crucially, the second factor.
- Session Hijacking: Once authenticated, an attacker can steal valid session cookies, effectively bypassing the need for future authentication checks.
- Man-in-the-Middle (MITM) Attacks: Intercepting communication between the user and the legitimate service.
- Social Engineering: Tricking users into approving MFA prompts ("MFA fatigue") or revealing one-time codes.
- Configuration Errors: Misconfigured MFA policies that allow bypasses in specific scenarios (e.g., trusted IPs, outdated browsers).
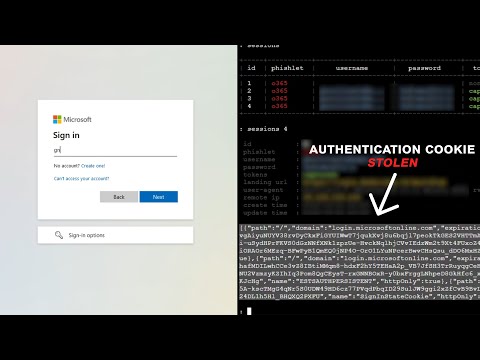
The critical observation is that many MFA bypass methods don't break the MFA itself but rather circumvent the authentication process by stealing or manipulating the session *after* a successful MFA prompt, or by tricking the user into granting access. This highlights that MFA, while essential, is not a silver bullet and must be part of a comprehensive security strategy.
Evilginx2: The Adversarial Proxy in Action
Tools like Evilginx2 exemplify the sophisticated approaches attackers take. Evilginx2 operates as a man-in-the-middle proxy designed to intercept credentials and session cookies, especially effective against OAuth and other federated identity protocols often used in conjunction with MFA. It doesn't steal your password directly from the source; it steals the *session* that is established *after* you've successfully authenticated, MFA and all.
Here's the procedural flow from an attacker's perspective, which is crucial for a defender to understand:
- Setup: The attacker configures Evilginx2, setting up phishing domains that mimic legitimate services (e.g., Microsoft 365, Google Workspace).
- Redirection: A victim is lured to a phishing link. The attacker's domain handles the initial request.
- Legitimate Authentication Flow: The victim is presented with a login page on the attacker's domain, which then forwards the request to the legitimate service for authentication. The victim enters their username and password, and then proceeds through the MFA prompt (e.g., entering an OTP, approving a push notification).
- Session Token Interception: Crucially, upon successful authentication and MFA verification on the legitimate site, the server sends back a session cookie. Evilginx2 captures this cookie.
- Session Impersonation: The attacker uses the stolen session cookie to impersonate the victim, gaining authenticated access to the target application without ever needing to know the password or the MFA code directly.
This technique leverages the trust inherent in how browsers handle session cookies and federated identities. It's a powerful demonstration of how session management, not just credential entry, is a critical security frontier.
Phishing Beyond the Credentials: Session Hijacking
The core of many advanced MFA bypasses lies in session hijacking. Traditional phishing focuses on capturing usernames and passwords. Advanced phishing, often facilitated by tools like Evilginx2, goes further: it captures the session token. Once an attacker possesses a valid, active session token, they can bypass the need to re-authenticate through MFA because the system already trusts the established session.
Consider a typical MFA workflow:
- User enters username and password.
- User is prompted for MFA (e.g., authenticator app code, SMS code, push notification).
- User provides MFA input.
- If all checks pass, the server issues a session token/cookie.
- User is logged in and can access resources.
A bypass scenario looks like this:
- Attacker sets up a phishing page that mirrors the legitimate login but acts as a proxy.
- User enters credentials and MFA code/approves prompt on the phishing page.
- The phishing proxy forwards these to the legitimate server, authenticates, and captures the resulting session token.
- Attacker uses the captured session token to access the legitimate service directly, effectively skipping steps 2 and 3 for future access within the token's validity period.
This means even if your users are diligent about MFA, a well-crafted phishing attack targeting session tokens can render it ineffective. The key takeaway for defenders is to monitor for anomalous session activity and unauthorized access from unexpected locations, even if MFA was supposedly used.
Detecting and Mitigating MFA Bypass
Effective defense requires a multi-pronged approach. Simply enabling MFA isn't enough; you need to bolster it and monitor for its subversion.
Detection Strategies:
- Log Analysis: Scrutinize authentication logs for unusual patterns. Look for:
- Multiple failed MFA attempts followed by a single success.
- Logins from geographically disparate locations within a short timeframe originating from the same user account.
- Access from unusual or unexpected IP addresses/user agents on authenticated sessions.
- Sudden changes in user behavior or access patterns immediately following authentication.
- Threat Hunting for Session Anomalies: Proactively search for signs of session hijacking. This can involve querying endpoint logs for suspicious processes or network traffic indicative of proxy activity.
- Monitoring for MFA Fatigue Attacks: While harder to detect technically, observe users for reports of frequent, unsolicited MFA prompts. Implement policies that limit repeated MFA requests.
- Behavioral Analytics: User and Entity Behavior Analytics (UEBA) tools can detect deviations from normal user activity that might indicate a compromised session.
Mitigation Tactics:
- Strong Phishing Awareness Training: Educate users rigorously on identifying phishing attempts, especially those that mimic login pages or request MFA approvals. Emphasize never approving prompts they didn't initiate.
- Use of FIDO2/WebAuthn Security Keys: Hardware security keys are significantly more resistant to phishing and session hijacking than OTPs or push notifications, as they require physical presence and are cryptographically bound to the legitimate site.
- Conditional Access Policies: Implement policies that restrict access based on location, device health, and user behavior. For example, require stronger authentication or block access from untrusted networks.
- Session Timeout and Revocation: Enforce strict session timeouts and ensure mechanisms are in place to quickly revoke compromised sessions.
- Browser and Network Security: Use browser extensions that can help detect malicious sites and ensure your network infrastructure is secure against man-in-the-middle attacks.
- Reviewing MFA Implementation: Regularly audit your MFA configuration. Ensure you're not relying on outdated or easily manipulated factors and that your federated identity providers are securely configured.
The battle against MFA bypass is ongoing. Staying ahead means continuously updating your detection and mitigation strategies based on emerging threats and advanced attacker techniques.
The Future of Authentication: Beyond Today's Weaknesses
Passwords and even current MFA implementations have inherent weaknesses that attackers continue to exploit. The drive towards more secure and user-friendly authentication is relentless. Technologies like FIDO2 (Fast Identity Online) and WebAuthn are paving the way for passwordless authentication, relying on hardware-based cryptographic keys. These keys are inherently resistant to phishing because they are tied to specific origins and require physical user interaction, making them incredibly difficult to steal remotely.
Beyond hardware keys, advancements in biometrics, behavioral biometrics (analyzing typing cadence, mouse movements, etc.), and context-aware authentication are emerging. The goal is to move away from something you *know* (password) or something you *have* (phone for OTP) towards something you *are* (biometrics) in a way that is both secure and seamless. However, it's crucial to remember that no system is entirely invulnerable. As authentication methods evolve, so too will the techniques used to bypass them. The security community must remain vigilant, adapting defenses as new attack vectors are discovered.
Engineer's Verdict: MFA's Role in a Modern Defense
MFA is not a panacea, but it is an indispensable layer of defense. To call it "easily bypassed" is a dangerous oversimplification that ignores the significant hurdle it presents to many opportunistic attackers. Its resilience varies dramatically based on the implementation and the specific factors used.
Pros:
- Significantly raises the bar for attackers compared to password-only authentication.
- Effective against credential stuffing and brute-force attacks targeting weak passwords.
- Mandatory for compliance in many industries.
Cons:
- Vulnerable to sophisticated phishing, MITM, and session hijacking attacks, especially when using SMS or push notifications.
- Can lead to "MFA fatigue" if not properly monitored, with users approving fraudulent requests.
- User experience friction can lead to workarounds or a false sense of security.
Verdict: MFA should be considered a critical component, not the entirety, of a defense-in-depth strategy. Prioritize phishing-resistant factors like FIDO2/WebAuthn keys. Continuously monitor, audit, and educate. Assume it *can* be bypassed and build your detection and response mechanisms accordingly.
Operator/Analyst Arsenal
To effectively defend against MFA bypasses and other advanced threats, the modern security professional needs a robust set of tools and knowledge:
- SIEM/Log Management Solutions: Essential for aggregating and analyzing authentication logs. Tools like Splunk, ELK Stack (Elasticsearch, Logstash, Kibana), or Microsoft Sentinel are invaluable.
- Endpoint Detection and Response (EDR): Solutions like CrowdStrike, Carbon Black, or Microsoft Defender for Endpoint provide visibility into endpoint activity, crucial for detecting suspicious processes or network connections.
- Threat Intelligence Platforms: Stay informed about the latest IOCs and attack techniques.
- Network Traffic Analysis (NTA): Tools like Zeek (Bro) or Suricata can help identify malicious network activity.
- Security Orchestration, Automation, and Response (SOAR): For automating detection and response workflows.
- Phishing Simulation Tools: To regularly test and train your user base.
- Books: The Web Application Hacker's Handbook (for understanding web vulnerabilities), Red Team Field Manual (RTFM) (for tactical commands), Applied Network Security Monitoring.
- Certifications: OSCP (Offensive Security Certified Professional), CISSP (Certified Information Systems Security Professional), GIAC certifications (e.g., GCTI, GCFA).
Frequently Asked Questions
How can I protect myself from MFA bypass attacks?
The best personal protection is extreme vigilance against phishing. Use hardware security keys (FIDO2/WebAuthn) whenever possible, and never approve an MFA prompt you did not initiate. Keep your software updated.
Is SMS-based MFA secure?
SMS-based MFA is generally considered the weakest form of MFA due to vulnerabilities like SIM swapping and interception. Push notifications can also be susceptible to MFA fatigue. Hardware tokens and authenticator apps are generally more secure.
What is MFA fatigue?
MFA fatigue occurs when an attacker repeatedly sends MFA authentication requests to a user, hoping the user will eventually approve one out of annoyance or mistake, thereby granting the attacker access.
The Contract: Fortifying Your MFA
Your current MFA implementation is a critical defense, but the digital shadows are always probing. The question isn't *if* your MFA will be tested, but *how* and *when*. Your contract is to move beyond simply enabling MFA and to actively harden it.
Your Challenge: Select one of your organization's critical applications currently protected by MFA. Review its specific configuration. Identify the MFA factors in use. Then, research known bypasses for those specific factors and configurations. Develop a short (3-5 point) mitigation plan to address the most plausible bypasses. Document your findings and share them with your security team.
This isn't about fear-mongering; it's about strategic preparedness. Understand the vulnerabilities, and you'll build defenses that truly stand. The network never sleeps, and neither should your vigilance.
