The digital battlefield is a chaotic symphony of packets and protocols, a constant flux where threats emerge from the ether like phantoms. In this realm, understanding the anatomy of network attacks isn't just knowledge; it's the tactical advantage. We're not here to play offense, but to build defenses so robust they laugh in the face of disruption. This is your deep dive into the heart of network assaults, framed not for the attacker, but for the guardian.
Network vulnerabilities are the cracks in our digital fortresses, exploited by those who thrive in chaos. From the subtle whispers of a Man-in-the-Middle attack to the deafening roar of a Distributed Denial of Service (DDoS), the attack surface is vast and ever-changing. To defend, you must first dissect.
The Network Attack Landscape: A Threat Hunter's Perspective
The OSI model, a theoretical construct, often becomes a battleground in reality. Attacks can manifest at any layer:
- Layer 1 (Physical) & Layer 2 (Data Link): While less common for sophisticated remote attacks, physical access or compromised network hardware can lead to issues like MAC flooding or unauthorized network access. Think rogue access points or tapped cables – the low-tech backdoors that often go unnoticed.
- Layer 3 (Network) & Layer 4 (Transport): This is where IP-based assaults thrive. IP spoofing, ICMP floods, and SYN floods aim to overwhelm routing tables or connection states. Distributed Denial of Service (DDoS) attacks, often amplified by botnets, are a prime example, aiming to render services inaccessible by sheer volume. Understanding traffic patterns and anomalous connection requests is key here.
- Layer 5 (Session), Layer 6 (Presentation), Layer 7 (Application): The higher layers are fertile ground for more nuanced attacks. This is where session hijacking, DNS poisoning, and application-specific exploits like SQL injection or Cross-Site Scripting (XSS) reside. A Man-in-the-Middle (MITM) attack often operates here, intercepting and potentially altering communications between two parties.
Common Network Attack Vectors and Their Countermeasures
Let's strip down some of the most prevalent threats and, more importantly, how to build your shield against them.
Distributed Denial of Service (DDoS)
Anatomy of the Assault: Imagine an army of compromised machines (a botnet) bombarding a server with millions of connection requests simultaneously. The target server, overwhelmed, can't respond to legitimate users, effectively shutting down its service. It's a brute-force method, sheer volume over sophistication.
Defensive Strategy:
- Rate Limiting: Configure firewalls and intrusion prevention systems (IPS) to limit the number of requests from a single IP address or subnet over a given period.
- Content Delivery Networks (CDNs) & Specialized DDoS Mitigation Services: Services like Cloudflare or Akamai act as a buffer. They absorb and filter malicious traffic before it even reaches your origin servers. They leverage massive global infrastructure to distribute and scrub traffic.
- Traffic Scrubbing Centers: These specialized facilities analyze incoming traffic, identify malicious patterns, and filter out attack traffic while allowing legitimate requests to pass through.
- Network Architecture: Distribute your services geographically. A single point of failure is an invitation.
Man-in-the-Middle (MITM)
Anatomy of the Assault: The attacker subtly inserts themselves into the communication channel between two parties. They can eavesdrop, steal credentials, or even inject malicious content into the data stream, all while the two communicating entities believe they are talking directly to each other. ARP spoofing on local networks or compromised Wi-Fi hotspots are common enablers.
Defensive Strategy:
- End-to-End Encryption (TLS/SSL): Ensure all sensitive communications use robust encryption protocols. This makes intercepted data unreadable without the decryption keys.
- Secure Network Protocols: Advocate for and implement protocols that inherently offer better security, like SFTP over FTP, or HTTPS over HTTP.
- Network Segmentation: Isolate critical systems. A breach in one segment shouldn't automatically grant access to others.
- Public Key Infrastructure (PKI) & Certificate Pinning: For applications, certificate pinning can prevent connections to imposter servers by ensuring only trusted certificates are accepted.
- User Education: Train users to be wary of suspicious network prompts, especially regarding SSL/TLS certificate warnings.
DNS Poisoning (DNS Cache Poisoning)
Anatomy of the Assault: The Domain Name System (DNS) translates human-readable domain names (like example.com) into IP addresses. DNS poisoning involves corrupting the DNS resolver's cache with false information. When a user tries to visit a legitimate website, they are instead redirected to a malicious site controlled by the attacker, often for phishing or malware distribution.
Defensive Strategy:
- DNSSEC (DNS Security Extensions): This suite of protocols adds a layer of authentication to DNS data, allowing clients to verify the origin and integrity of DNS responses.
- Secure DNS Servers: Use reputable and secured DNS servers. Ensure your own internal DNS servers are hardened and regularly updated.
- Monitor DNS Traffic: Look for unusual DNS query patterns, unexpected responses, or sudden spikes in traffic to suspicious domains.
- Regular Cache Flushing: While not a primary defense, periodically flushing DNS caches can mitigate the impact of a stale, poisoned entry.
The Operator's Toolkit: Essential for Defense
Building a robust defense requires the right tools and knowledge. While the offensive side may boast shiny exploits, the defensive side relies on meticulous analysis and proactive hardening.
- Wireshark: The gold standard for packet analysis. Understanding traffic flow, identifying anomalies, and dissecting attack payloads is impossible without it. For serious analysis, the 101 Labs - Wireshark WCNA training can illuminate its full potential.
- Intrusion Detection/Prevention Systems (IDS/IPS): Tools like Snort or Suricata are your digital sentinels, monitoring network traffic for malicious patterns and actively blocking them.
- Firewalls (Next-Generation): Beyond simple port blocking, modern firewalls offer deep packet inspection, application control, and threat intelligence integration.
- Security Information and Event Management (SIEM): Tools like Splunk or ELK Stack aggregate logs from across your network, enabling centralized analysis and threat hunting.
- Content Delivery Networks (CDNs) & DDoS Mitigation Services: As mentioned, services like Cloudflare are indispensable for absorbing and filtering volumetric attacks.
The SSCP Certification Pathway: Building Core Competencies
For those serious about establishing foundational knowledge and proving their expertise in systems security, the Systems Security Certified Practitioner (SSCP) certification is a critical step. It covers a broad spectrum of security concepts, including access controls, cryptography, risk management, and operational security, all vital for understanding and countering network attacks.
To accelerate your journey towards this certification, consider a comprehensive training program. A 13-hour video training course with included practice exams can provide the concentrated knowledge needed to pass. Investing in your skills is the ultimate offensive move against the threats that seek to exploit your systems.
Veredicto del Ingeniero: The Unseen Architecture of Defense
Network attacks are not abstract threats; they are the tangible consequences of architectural flaws and negligence. The tools and techniques discussed are merely enablers for a deeper mindset: the proactive, analytical posture of a defender. DDoS, MITM, DNS poisoning – these are not just attack names; they are syndromes of exploited weaknesses. Your defense must be layered, adaptive, and constantly evolving. Relying solely on perimeter defenses is like building a castle wall and leaving the gates wide open. True security lies in understanding the attack vectors intimately, fortifying every layer, and maintaining constant vigilance. The digital realm rewards preparedness; it punishes complacency.
Arsenal del Operador/Analista
- Packet Analysis: Wireshark (Essential), tcpdump (Command-line).
- Network Monitoring: Nagios, Zabbix, Prometheus.
- Threat Intelligence Platforms: MISP, ThreatConnect.
- Log Aggregation & Analysis: Elasticsearch/Logstash/Kibana (ELK Stack), Splunk.
- Firewall/IPS: pfSense, OPNsense, Snort, Suricata.
- DDoS Mitigation: Cloudflare, Akamai; internal rate-limiting configurations.
- Certifications to Pursue: SSCP, Security+, Network+, CISSP, OSCP.
- Books: "The Web Application Hacker's Handbook", "Network Security Essentials".
Taller Práctico: Fortaleciendo tu Infraestructura contra Ataques de Nivel de Red
This hands-on section guides you through simulated defensive measures. Remember: these exercises are for authorized testing environments only. Never attempt these on systems you do not own or have explicit permission to test.
-
Configurar Firewall Rules for DDoS Mitigation
Objective: Implement basic rate limiting on an edge firewall (simulated).
Scenario: Protect a web server from excessive connection attempts.
# Example using iptables on a Linux server (requires root privileges) # Allow established connections iptables -A INPUT -m conntrack --ctstate ESTABLISHED,RELATED -j ACCEPT # Allow traffic on common web ports (HTTP, HTTPS) iptables -A INPUT -p tcp --dport 80 -j ACCEPT iptables -A INPUT -p tcp --dport 443 -j ACCEPT # Rate limit new incoming connections per IP for port 80 (e.g., 10 new connections per minute) iptables -A INPUT -p tcp --dport 80 -m state --state NEW -m recent --set --name WEB_LIMIT --rsent-qlen 10 --rsent-max 10 --timeout 60 iptables -A INPUT -p tcp --dport 80 -m state --state NEW -m recent --update --name WEB_LIMIT --seconds 60 -j DROP # Repeat for port 443 if necessary echo "Basic rate limiting configured for web ports."Analysis: This configuration attempts to limit the rate of new TCP connections to ports 80 and 443. Legitimate users, once connected, will fall into the ESTABLISHED state and bypass these rules. Attackers trying to initiate many new connections will be dropped after exceeding the configured limit.
-
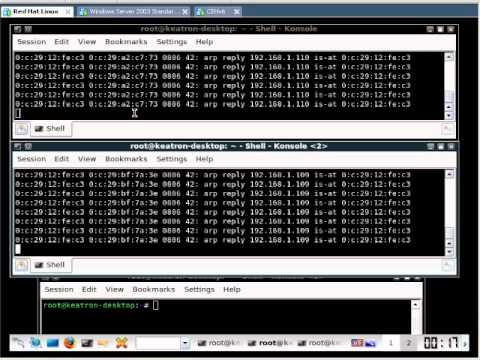
Detecting ARP Spoofing with Ettercap (Ethical Use ONLY)
Objective: Understand how ARP spoofing works and how to detect it.
Scenario: In a controlled lab environment, use Ettercap to simulate an ARP spoofing attack and then use Wireshark to identify the malicious traffic.
Disclaimer: This procedure is for educational purposes in a lab environment ONLY. Unauthorized ARP spoofing is illegal and harmful.
- Set up a simple lab network (e.g., two client VMs and an attacker VM running Kali Linux).
- On the attacker VM, start Ettercap:
sudo ettercap -T -q -i eth0(replaceeth0with your network interface). - Perform a scan for hosts and select the target IP address (e.g., a victim VM) and the gateway IP.
- Initiate the ARP poisoning attack via Ettercap's MITM menu.
- On the victim VM, open Wireshark. Filter for ARP traffic (
arp). - Observe the ARP replies: You will see the attacker's MAC address being advertised for the gateway's IP address, and vice-versa, indicating the MITM position.
Detection: Network monitoring tools that detect duplicate MAC addresses for different IPs or unusual ARP traffic patterns can alert you to such threats.
Frequently Asked Questions
-
What is the most common network attack vector today?
While DDoS remains prevalent, phishing attacks (often leading to credential theft and subsequent network compromise) and exploit kits targeting unpatched vulnerabilities at the application layer are extremely common.
-
How can I protect my home network from basic attacks?
Keep your router's firmware updated, use strong, unique passwords for your Wi-Fi and router admin interface, enable WPA2/WPA3 encryption, and be cautious of unknown Wi-Fi networks.
-
Is network security a continuous process?
Absolutely. The threat landscape evolves daily. Continuous monitoring, regular vulnerability assessments, and ongoing security awareness training are crucial.
-
What's the difference between an IDS and an IPS?
An Intrusion Detection System (IDS) monitors for suspicious activity and alerts administrators. An Intrusion Prevention System (IPS) does the same but can also actively block or prevent the detected malicious activity.
The Contract: Secure Your Digital Perimeter
You've seen the blueprints of network warfare. Now, the contract is yours to fulfill: implement at least one of the defensive strategies discussed today in your lab environment. Whether it's setting up basic rate limiting, analyzing traffic with Wireshark for specific patterns, or researching DNSSEC implementation for a hypothetical network, the act of building and testing defenses solidifies knowledge. Share your findings, your challenges, or your improved configurations in the comments below. Let's turn theory into hardened reality.
Recommended Resources
- Cisco CCNA Simplified - For foundational network understanding.
- 101 Labs - CompTIA Security+ - Broaden your security knowledge.
- 101labs.net - 30-Day Access for $1 - Hands-on labs invaluable for practice.
For comprehensive, hands-on IT certification training, including Cisco CCNA, CompTIA Security+, and more, visit our website. Use coupon code 'youtube' for substantial discounts. Special offer: get 30 days of access for just $1 via this link: https://ift.tt/emaTcBx.
Need a push? Grab your FREE motivation goodies here: https://ift.tt/FbLvB5Y.