The digital realm is a battlefield, and every skirmish leaves its mark. In this war, penetration testing isn't just a service; it's an essential reconnaissance mission. But how do you put a price on peering into the abyss of a client's defenses? Charge too little, and you devalue your expertise, risking burnout. Charge too much, and the deal dies before it even begins. This isn't about slapping a number on a service; it's about understanding the true value of your offensive capabilities and translating that into a contract that satisfies both parties. Forget the guesswork; we're here to dissect the anatomy of a profitable pentest pricing strategy.
The objective is clear: deliver genuine, manual penetration testing services that uncover critical vulnerabilities, not just run a scanner and call it a day. This guide will illuminate the dark alleys of pricing, distinguishing between superficial "count-based" metrics and the more robust "diagnostic-based" approach. For those looking to establish realistic penetration testing budgets or scrutinize a vendor's true offering, this is your intel brief. The difference between a vendor providing genuine manual services and one merely pushing automated scans can be the difference between security and disaster.
Table of Contents
What is Penetration Testing Pricing?
Pricing a penetration test is an art form, deeply entwined with the science of offensive security. It's not a commodity; it's a bespoke service tailored to the unique threat landscape of each client. A comprehensive penetration test aims to simulate real-world attacks, exposing vulnerabilities before malicious actors can exploit them. The price reflects the depth of the simulated assault, the expertise of the testers, the time invested, and the potential impact of the findings.
In essence, you're not just selling hours; you're selling risk reduction, business continuity, and peace of mind. A lower price might attract more clients initially, but it can lead to rushed assessments, missed critical flaws, and ultimately, a damaged reputation. Conversely, a price that accurately reflects the value delivered builds trust and long-term relationships.
Count-Based vs. Diagnostic-Based Pricing
The market is flooded with different pricing models, but two stand out: count-based and diagnostic-based. Understanding the distinction is crucial for both the service provider and the client.
"The cheapest penetration test is rarely the best. Quality in security comes from expertise, thoroughness, and relentless curiosity – all of which have a cost."
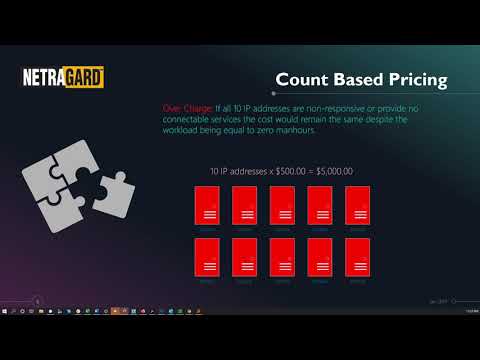
Count-Based Pricing: This model, often seen with automated scanning tools, bases the price on the number of IP addresses, URLs, or application components tested. It's straightforward, predictable, and often appeals to clients with limited budgets or a superficial understanding of security needs. However, it inherently incentivizes quantity over quality. A vendor might run automated scans across thousands of IPs, generating a report filled with low-fidelity alerts but missing deep, exploitable vulnerabilities that require manual analysis. This approach often equates to little more than a glorified vulnerability scan.
Diagnostic-Based Pricing: This is the hallmark of genuine, manual penetration testing. The price is determined by the complexity of the target environment, the scope of the engagement, the types of attacks to be simulated, and the required depth of analysis. It accounts for the human element – the researcher's skill in crafting custom exploits, chaining vulnerabilities, and understanding business logic flaws. This model is more nuanced and requires a detailed scoping session with the client. It aligns the price with the potential business impact discovered, ensuring that the client pays for the value of uncovering critical risks.
The key takeaway? Automated scans can identify known weaknesses. Manual penetration tests, priced diagnostically, uncover the unknown threats, the business logic flaws, and the sophisticated attack vectors that automated tools can't even comprehend. For organizations serious about security, diagnostic-based pricing is the only path to genuine assurance.
Factors Influencing Pentest Costs
Several variables contribute to the final price tag of a penetration test. A thorough assessment requires understanding these components:
- Scope of Engagement: What exactly are you testing? A single web application? An entire corporate network? Cloud infrastructure? Mobile applications? The broader and more complex the scope, the higher the cost.
- External Network Pentest: Simulating attacks from the internet.
- Internal Network Pentest: Simulating attacks from within the network perimeter (e.g., a compromised employee machine).
- Web Application Pentest: Focusing on vulnerabilities within web applications (SQLi, XSS, authentication bypasses).
- Mobile Application Pentest: Testing iOS or Android applications for vulnerabilities.
- Cloud Security Assessment: Evaluating the security of cloud environments (AWS, Azure, GCP).
- Social Engineering: Phishing campaigns, vishing calls, or physical pretexting to gain access.
- Depth of Testing: Are we looking for surface-level vulnerabilities, or are we aiming for full system compromise and demonstrating business impact? Deeper, more sophisticated testing requires more time and advanced skill sets.
- Methodology and Tools: While manual testing is paramount, efficient testers leverage a suite of tools to speed up reconnaissance and identify potential weaknesses. The types of commercial tools used (e.g., Burp Suite Professional, Nmap scripts, specialized exploit frameworks) can influence costs, though the true value lies in the tester's ability to wield them effectively.
- Team Expertise and Experience: Highly skilled and certified penetration testers command higher rates. Their experience in identifying complex, business-logic vulnerabilities and their ability to articulate findings clearly are invaluable. Certifications like OSCP, OSCE, or CISSP often indicate a higher level of proficiency.
- Reporting Requirements: The quality and detail of the final report significantly impact the price. A comprehensive report includes a detailed executive summary, technical findings with risk ratings, proof-of-concept exploits, and actionable remediation recommendations. A basic report might just list vulnerabilities found by an automated scanner.
- Compliance Requirements: If the client needs to meet specific regulatory compliance standards (e.g., PCI DSS, HIPAA, SOC 2), the pentest methodology might need to be tailored to address those specific controls, potentially increasing complexity and cost.
- Time Constraints: Urgent requests or tight deadlines may incur rush fees. Penetration testing requires careful planning and execution, and attempting to compress this process can compromise quality.
When creating a proposal, detailing each of these factors transparently helps the client understand the value proposition and justify the investment. Avoid vague statements; be specific.
Building Your Pentest Proposal
A robust penetration testing proposal is your sales document. It needs to be clear, concise, and compelling, demonstrating a deep understanding of the client's needs while advocating for the value of your service. Here’s how to structure it:
- Executive Summary: A high-level overview of the engagement, its objectives, and the expected outcomes. This section should appeal to non-technical stakeholders.
- Understanding of Client Needs: Show that you've listened. Reiterate the client's security concerns and business objectives.
- Scope of Work: Clearly define what will be tested (assets, systems, applications) and what will be explicitly excluded. This prevents scope creep and misunderstandings. Be granular.
- Target Assets: List specific IPs, domains, URLs, or application names.
- Testing Types: Specify internal, external, web app, etc.
- Attack Vectors: Outline potential attack types (e.g., authentication bypass, injection flaws, logic flaws, configuration errors).
- Exclusions: Clearly state any systems or activities that are out of scope.
- Methodology: Briefly describe the approach you will take. Mention adherence to industry standards like OWASP, NIST, or PTES. Emphasize the manual testing aspect over reliance on automated tools.
- Deliverables: Detail what the client will receive, primarily the penetration test report. Specify the format, typical sections (executive summary, technical findings, risk assessment, remediation recommendations), and delivery timeline.
- Timeline: Provide a realistic schedule for each phase of the engagement – reconnaissance, active testing, analysis, reporting, and debriefing.
- Team Qualifications: Introduce your team, highlighting relevant experience, certifications, and expertise. This builds confidence and trust.
- Pricing: Clearly present the cost. If using diagnostic-based pricing, break it down into logical components or phases. If offering tiered packages, explain the differentiators. Transparency here is key. For example, instead of a flat fee, consider itemizing costs for scoping, testing phases, reporting, and debriefing.
- Assumptions and Dependencies: List any assumptions made about the client's environment or any dependencies on client cooperation (e.g., providing necessary credentials, ensuring testing windows).
- Terms and Conditions: Include standard contractual clauses regarding confidentiality, liability, and payment terms.
A well-crafted proposal isn't just a price quote; it's a testament to your professionalism and understanding of the security risks at play.
Common Pricing Pitfalls to Avoid
Navigating the pricing landscape can be treacherous. Beware of these common mistakes:
- Underpricing: The temptation to win bids by offering a low price is strong, but it's a race to the bottom. Low prices often correlate with shallow testing, insufficient resources, and burnout. It signals a lack of confidence in your own value.
- Ignoring Scope Creep: Clients may request additional testing outside the agreed-upon scope. Without a clear change control process, this eats into your profit margins and can compromise the quality of the original engagement. Always have a mechanism to formally scope and price out-of-scope requests.
- Vagueness in Scope: Ambiguous definitions of what will be tested lead to disputes. If it's not clearly defined, it's open to interpretation, often to your detriment.
- Not Accounting for Non-Testing Time: Penetration testing isn't just about the hours spent actively exploiting systems. It includes meticulous planning, reconnaissance, in-depth analysis of findings, report writing, and client debriefings. These "behind-the-scenes" hours are critical and must be factored into the pricing.
- Lack of Value Articulation: Simply stating a price without explaining the value it represents is a missed opportunity. Help the client understand the ROI of a thorough pentest – the cost of a breach versus the cost of prevention.
- Not Differentiating Services: Presenting all pentests as equal fails to acknowledge the varying levels of complexity and risk. Clearly distinguish between different types of tests and their associated pricing structures.
Your pricing strategy should be built on a foundation of realistic effort estimation and a clear understanding of the value you deliver. Never be afraid to charge what your expertise is worth.
Engineer's Verdict: Is It Worth It?
Absolutely. Pricing a penetration test correctly is not just about covering costs; it's about aligning your service with the perceived and actual value to the client. When done right, diagnostic-based pricing for comprehensive manual testing proves its worth manifold. It fosters trust by demonstrating that you're invested in uncovering genuine risks, not just ticking boxes. Clients who understand this value see the pentest as an investment in their security posture, not just an expense. Those who focus solely on the cheapest option are playing a dangerous game. In the digital trenches, a sharp tool, wielded by a skilled hand, is priceless. A bargain-basement pentest is precisely that – a bargain, with all the inherent risks.
Operator/Analyst Arsenal
To deliver high-quality penetration testing, an operator needs a robust set of tools and knowledge. Here’s a glimpse into the essential arsenal:
- Core Tools:
- Burp Suite Professional: Indispensable for web application testing. Its intercepting proxy, scanner, and repeater functionalities are critical. Investing in the Pro version unlocks advanced scanning capabilities and automation.
- Nmap: The de facto standard for network discovery and security auditing. Essential for mapping out the attack surface.
- Metasploit Framework: A powerful tool for developing and executing exploit code against remote target machines. Crucial for post-exploitation and privilege escalation scenarios.
- Wireshark: For deep packet inspection and network traffic analysis. Vital for understanding network communication and identifying subtle anomalies.
- Impacket Suite: A collection of Python classes for working with network protocols, particularly useful for Windows environments and lateral movement.
- Specialized Tools: Depending on the target, this might include tools for mobile app analysis (e.g., Frida, MobSF), cloud security assessment (e.g., Pacu, Scout Suite), or IoT device testing.
- Programming Languages: Proficiency in Python is almost a prerequisite for scripting custom tools, automating tasks, and analyzing data. Other languages like Bash, PowerShell, or even Go can be highly beneficial.
- Knowledge Resources:
- "The Web Application Hacker's Handbook" by Dafydd Stuttard and Marcus Pinto: A foundational text for understanding web vulnerabilities.
- OWASP Top 10: The definitive list of current web application security risks. Essential reading for any web pentester.
- NIST SP 800-115: Technical Guide to Information Security Testing and Assessment. Provides a solid framework for penetration testing.
- Certifications: While not strictly an "arsenal" item, holding certifications like Certified Ethical Hacker (CEH), Offensive Security Certified Professional (OSCP), or GIAC Penetration Tester (GPEN) validates expertise and can justify higher service rates. For serious engagements, consider OSCP and beyond.
Remember, tools are only as good as the operator wielding them. Continuous learning and practical experience are paramount.
Practical Workshop: Crafting Your Rate Card
Let's move from theory to practice. Building a rate card involves more than just setting an hourly wage; it's about creating a scalable pricing structure.
- Calculate Your Baseline Cost:
- Overhead: Factor in rent, utilities, software licenses (e.g., Burp Suite Pro, vulnerability scanners), hardware, insurance, administrative costs, and marketing.
- Personnel Costs: Include salaries, benefits, payroll taxes, and training for your team members.
- Desired Profit Margin: What profit do you aim to achieve? A common target is 20-30%, but this can vary.
Example: If your total monthly overhead + personnel costs are $30,000, and you work 160 hours a month per person, your breakeven hourly rate is $30,000 / 160 = $187.50. Add a 25% profit margin: $187.50 * 1.25 = $234.375. Round up to $235/hour for your baseline.
- Define Service Tiers: Create distinct packages based on depth and scope.
- Basic Scan (Automated): Low hourly rate, limited scope. Aimed at clients with minimal budgets. (e.g., $75-$125/hour). Clearly state it's primarily automated.
- Standard Pentest (Manual Core): A balanced offering with significant manual testing. (e.g., $175-$250/hour). This should be your most common offering.
- Advanced Pentest (Deep Dive/Red Team): Higher rate, extensive scope, complex attack simulations, focus on business logic and impact. (e.g., $250-$400+/hour).
- Factor in Project Complexity: For fixed-price projects, estimate the total hours required for each phase (scoping, testing, reporting, debriefing) and multiply by your hourly rate for that service tier. Use ranges or add contingencies for unforeseen complexities.
- Small Web App: Estimate 40-80 hours.
- Medium Network: Estimate 80-160 hours.
- Large Enterprise/Red Team: Estimate 200-500+ hours.
- Consider Value-Based Pricing: For high-impact engagements, where the potential loss from a breach is astronomical, price based on the value of the risk mitigated rather than just the hours spent. This requires strong client communication and justification.
- Add-ons and Specializations: Offer specific modules like social engineering campaigns, phishing simulations, or cloud configuration reviews as separate line items or packages.
Your rate card should be a living document, reviewed and adjusted annually based on market rates, your growing expertise, and changes in your operational costs. Invest in tools and certifications to justify higher rates over time.
Frequently Asked Questions
- What is the difference between penetration testing and vulnerability scanning?
- Vulnerability scanning is an automated process that identifies known weaknesses based on signatures. Penetration testing is a manual process that simulates real-world attacks to exploit vulnerabilities, assess their impact, and determine the extent of potential compromise.
- How long does a penetration test typically take?
- The duration varies greatly depending on the scope and complexity. A small web application test might take a few days, while a comprehensive network assessment or red team exercise could take several weeks.
- Can I use the findings from a penetration test for compliance audits?
- Yes, a well-documented penetration test report, especially one adhering to specific compliance frameworks (like PCI DSS or HIPAA), is often a requirement for audits.
- What if a vulnerability is found that could cause significant disruption?
- Ethical penetration testers have a responsibility to communicate critical findings immediately to the client, often outside the formal reporting process, to allow for prompt remediation and prevent business disruption.
- How do you ensure client data confidentiality?
- Confidentiality is paramount. We typically sign Non-Disclosure Agreements (NDAs) and employ secure data handling practices throughout the engagement. All findings and reports are treated with the highest level of confidentiality.
The Contract: Securing Your Next Engagement
The proposal is signed, the scope is agreed upon. Now, the real work begins. Your task is to not just execute the test, but to deliver a report that is actionable, insightful, and undeniably valuable. Can you articulate the business risk associated with a missed SQL injection in a way that makes a CEO understand the potential financial fallout? Can you demonstrate that the 3 hours spent discovering a privilege escalation path were worth more than the 3 days a scanner might have spent searching for surface-level flaws?
Your challenge: Take a hypothetical scenario – a small e-commerce platform with a customer database containing PII. Outline the potential attack vectors an external attacker might use, focusing on 2 distinct vulnerabilities. For each, describe the manual exploit process and the potential business impact (data breach, financial loss, reputational damage). Then, assign a "diagnostic-based" price range for testing these specific vectors, justifying your pricing based on complexity and potential impact.
```
The Art of the Deal: Pricing Your Penetration Tests for Maximum Impact and Profit
The digital realm is a battlefield, and every skirmish leaves its mark. In this war, penetration testing isn't just a service; it's an essential reconnaissance mission. But how do you put a price on peering into the abyss of a client's defenses? Charge too little, and you devalue your expertise, risking burnout. Charge too much, and the deal dies before it even begins. This isn't about slapping a number on a service; it's about understanding the true value of your offensive capabilities and translating that into a contract that satisfies both parties. Forget the guesswork; we're here to dissect the anatomy of a profitable pentest pricing strategy.
The objective is clear: deliver genuine, manual penetration testing services that uncover critical vulnerabilities, not just run a scanner and call it a day. This guide will illuminate the dark alleys of pricing, distinguishing between superficial "count-based" metrics and the more robust "diagnostic-based" approach. For those looking to establish realistic penetration testing budgets or scrutinize a vendor's true offering, this is your intel brief. The difference between a vendor providing genuine manual services and one merely pushing automated scans can be the difference between security and disaster.
Table of Contents
What is Penetration Testing Pricing?
Pricing a penetration test is an art form, deeply entwined with the science of offensive security. It's not a commodity; it's a bespoke service tailored to the unique threat landscape of each client. A comprehensive penetration test aims to simulate real-world attacks, exposing vulnerabilities before malicious actors can exploit them. The price reflects the depth of the simulated assault, the expertise of the testers, the time invested, and the potential impact of the findings.
In essence, you're not just selling hours; you're selling risk reduction, business continuity, and peace of mind. A lower price might attract more clients initially, but it can lead to rushed assessments, missed critical flaws, and ultimately, a damaged reputation. Conversely, a price that accurately reflects the value delivered builds trust and long-term relationships.
Count-Based vs. Diagnostic-Based Pricing
The market is flooded with different pricing models, but two stand out: count-based and diagnostic-based. Understanding the distinction is crucial for both the service provider and the client.
"The cheapest penetration test is rarely the best. Quality in security comes from expertise, thoroughness, and relentless curiosity – all of which have a cost."
Count-Based Pricing: This model, often seen with automated scanning tools, bases the price on the number of IP addresses, URLs, or application components tested. It's straightforward, predictable, and often appeals to clients with limited budgets or a superficial understanding of security needs. However, it inherently incentivizes quantity over quality. A vendor might run automated scans across thousands of IPs, generating a report filled with low-fidelity alerts but missing deep, exploitable vulnerabilities that require manual analysis. This approach often equates to little more than a glorified vulnerability scan.
Diagnostic-Based Pricing: This is the hallmark of genuine, manual penetration testing. The price is determined by the complexity of the target environment, the scope of the engagement, the types of attacks to be simulated, and the required depth of analysis. It accounts for the human element – the researcher's skill in crafting custom exploits, chaining vulnerabilities, and understanding business logic flaws. This model is more nuanced and requires a detailed scoping session with the client. It aligns the price with the potential business impact discovered, ensuring that the client pays for the value of uncovering critical risks.
The key takeaway? Automated scans can identify known weaknesses. Manual penetration tests, priced diagnostically, uncover the unknown threats, the business logic flaws, and the sophisticated attack vectors that automated tools can't even comprehend. For organizations serious about security, diagnostic-based pricing is the only path to genuine assurance.
Factors Influencing Pentest Costs
Several variables contribute to the final price tag of a penetration test. A thorough assessment requires understanding these components:
- Scope of Engagement: What exactly are you testing? A single web application? An entire corporate network? Cloud infrastructure? Mobile applications? The broader and more complex the scope, the higher the cost.
- External Network Pentest: Simulating attacks from the internet.
- Internal Network Pentest: Simulating attacks from within the network perimeter (e.g., a compromised employee machine).
- Web Application Pentest: Focusing on vulnerabilities within web applications (SQLi, XSS, authentication bypasses).
- Mobile Application Pentest: Testing iOS or Android applications for vulnerabilities.
- Cloud Security Assessment: Evaluating the security of cloud environments (AWS, Azure, GCP).
- Social Engineering: Phishing campaigns, vishing calls, or physical pretexting to gain access.
- Depth of Testing: Are we looking for surface-level vulnerabilities, or are we aiming for full system compromise and demonstrating business impact? Deeper, more sophisticated testing requires more time and advanced skill sets.
- Methodology and Tools: While manual testing is paramount, efficient testers leverage a suite of tools to speed up reconnaissance and identify potential weaknesses. The types of commercial tools used (e.g., Burp Suite Professional, Nmap scripts, specialized exploit frameworks) can influence costs, though the true value lies in the tester's ability to wield them effectively.
- Team Expertise and Experience: Highly skilled and certified penetration testers command higher rates. Their experience in identifying complex, business-logic vulnerabilities and their ability to articulate findings clearly are invaluable. Certifications like OSCP, OSCE, or CISSP often indicate a higher level of proficiency.
- Reporting Requirements: The quality and detail of the final report significantly impact the price. A comprehensive report includes a detailed executive summary, technical findings with risk ratings, proof-of-concept exploits, and actionable remediation recommendations. A basic report might just list vulnerabilities found by an automated scanner.
- Compliance Requirements: If the client needs to meet specific regulatory compliance standards (e.g., PCI DSS, HIPAA, SOC 2), the pentest methodology might need to be tailored to address those specific controls, potentially increasing complexity and cost.
- Time Constraints: Urgent requests or tight deadlines may incur rush fees. Penetration testing requires careful planning and execution, and attempting to compress this process can compromise quality.
When creating a proposal, detailing each of these factors transparently helps the client understand the value proposition and justify the investment. Avoid vague statements; be specific.
Building Your Pentest Proposal
A robust penetration testing proposal is your sales document. It needs to be clear, concise, and compelling, demonstrating a deep understanding of the client's needs while advocating for the value of your service. Here’s how to structure it:
- Executive Summary: A high-level overview of the engagement, its objectives, and the expected outcomes. This section should appeal to non-technical stakeholders.
- Understanding of Client Needs: Show that you've listened. Reiterate the client's security concerns and business objectives.
- Scope of Work: Clearly define what will be tested (assets, systems, applications) and what will be explicitly excluded. This prevents scope creep and misunderstandings. Be granular.
- Target Assets: List specific IPs, domains, URLs, or application names.
- Testing Types: Specify internal, external, web app, etc.
- Attack Vectors: Outline potential attack types (e.g., authentication bypass, injection flaws, logic flaws, configuration errors).
- Exclusions: Clearly state any systems or activities that are out of scope.
- Methodology: Briefly describe the approach you will take. Mention adherence to industry standards like OWASP, NIST, or PTES. Emphasize the manual testing aspect over reliance on automated tools.
- Deliverables: Detail what the client will receive, primarily the penetration test report. Specify the format, typical sections (executive summary, technical findings, risk assessment, remediation recommendations), and delivery timeline.
- Timeline: Provide a realistic schedule for each phase of the engagement – reconnaissance, active testing, analysis, reporting, and debriefing.
- Team Qualifications: Introduce your team, highlighting relevant experience, certifications, and expertise. This builds confidence and trust.
- Pricing: Clearly present the cost. If using diagnostic-based pricing, break it down into logical components or phases. If offering tiered packages, explain the differentiators. Transparency here is key. For example, instead of a flat fee, consider itemizing costs for scoping, testing phases, reporting, and debriefing.
- Assumptions and Dependencies: List any assumptions made about the client's environment or any dependencies on client cooperation (e.g., providing necessary credentials, ensuring testing windows).
- Terms and Conditions: Include standard contractual clauses regarding confidentiality, liability, and payment terms.
A well-crafted proposal isn't just a price quote; it's a testament to your professionalism and understanding of the security risks at play.
Common Pricing Pitfalls to Avoid
Navigating the pricing landscape can be treacherous. Beware of these common mistakes:
- Underpricing: The temptation to win bids by offering a low price is strong, but it's a race to the bottom. Low prices often correlate with shallow testing, insufficient resources, and burnout. It signals a lack of confidence in your own value.
- Ignoring Scope Creep: Clients may request additional testing outside the agreed-upon scope. Without a clear change control process, this eats into your profit margins and can compromise the quality of the original engagement. Always have a mechanism to formally scope and price out-of-scope requests.
- Vagueness in Scope: Ambiguous definitions of what will be tested lead to disputes. If it's not clearly defined, it's open to interpretation, often to your detriment.
- Not Accounting for Non-Testing Time: Penetration testing isn't just about the hours spent actively exploiting systems. It includes meticulous planning, reconnaissance, in-depth analysis of findings, report writing, and client debriefings. These "behind-the-scenes" hours are critical and must be factored into the pricing.
- Lack of Value Articulation: Simply stating a price without explaining the value it represents is a missed opportunity. Help the client understand the ROI of a thorough pentest – the cost of a breach versus the cost of prevention.
- Not Differentiating Services: Presenting all pentests as equal fails to acknowledge the varying levels of complexity and risk. Clearly distinguish between different types of tests and their associated pricing structures.
Your pricing strategy should be built on a foundation of realistic effort estimation and a clear understanding of the value you deliver. Never be afraid to charge what your expertise is worth.
Engineer's Verdict: Is It Worth It?
Absolutely. Pricing a penetration test correctly is not just about covering costs; it's about aligning your service with the perceived and actual value to the client. When done right, diagnostic-based pricing for comprehensive manual testing proves its worth manifold. It fosters trust by demonstrating that you're invested in uncovering genuine risks, not just ticking boxes. Clients who understand this value see the pentest as an investment in their security posture, not just an expense. Those who focus solely on the cheapest option are playing a dangerous game. In the digital trenches, a sharp tool, wielded by a skilled hand, is priceless. A bargain-basement pentest is precisely that – a bargain, with all the inherent risks.
Operator/Analyst Arsenal
To deliver high-quality penetration testing, an operator needs a robust set of tools and knowledge. Here’s a glimpse into the essential arsenal:
- Core Tools:
- Burp Suite Professional: Indispensable for web application testing. Its intercepting proxy, scanner, and repeater functionalities are critical. Investing in the Pro version unlocks advanced scanning capabilities and automation.
- Nmap: The de facto standard for network discovery and security auditing. Essential for mapping out the attack surface.
- Metasploit Framework: A powerful tool for developing and executing exploit code against remote target machines. Crucial for post-exploitation and privilege escalation scenarios.
- Wireshark: For deep packet inspection and network traffic analysis. Vital for understanding network communication and identifying subtle anomalies.
- Impacket Suite: A collection of Python classes for working with network protocols, particularly useful for Windows environments and lateral movement.
- Specialized Tools: Depending on the target, this might include tools for mobile app analysis (e.g., Frida, MobSF), cloud security assessment (e.g., Pacu, Scout Suite), or IoT device testing.
- Programming Languages: Proficiency in Python is almost a prerequisite for scripting custom tools, automating tasks, and analyzing data. Other languages like Bash, PowerShell, or even Go can be highly beneficial.
- Knowledge Resources:
- "The Web Application Hacker's Handbook" by Dafydd Stuttard and Marcus Pinto: A foundational text for understanding web vulnerabilities.
- OWASP Top 10: The definitive list of current web application security risks. Essential reading for any web pentester.
- NIST SP 800-115: Technical Guide to Information Security Testing and Assessment. Provides a solid framework for penetration testing.
- Certifications: While not strictly an "arsenal" item, holding certifications like Certified Ethical Hacker (CEH), Offensive Security Certified Professional (OSCP), or GIAC Penetration Tester (GPEN) validates expertise and can justify higher service rates. For serious engagements, consider OSCP and beyond.
Remember, tools are only as good as the operator wielding them. Continuous learning and practical experience are paramount.
Practical Workshop: Crafting Your Rate Card
Let's move from theory to practice. Building a rate card involves more than just setting an hourly wage; it's about creating a scalable pricing structure.
- Calculate Your Baseline Cost:
- Overhead: Factor in rent, utilities, software licenses (e.g., Burp Suite Pro, vulnerability scanners), hardware, insurance, administrative costs, and marketing.
- Personnel Costs: Include salaries, benefits, payroll taxes, and training for your team members.
- Desired Profit Margin: What profit do you aim to achieve? A common target is 20-30%, but this can vary.
Example: If your total monthly overhead + personnel costs are $30,000, and you work 160 hours a month per person, your breakeven hourly rate is $30,000 / 160 = $187.50. Add a 25% profit margin: $187.50 * 1.25 = $234.375. Round up to $235/hour for your baseline.
- Define Service Tiers: Create distinct packages based on depth and scope.
- Basic Scan (Automated): Low hourly rate, limited scope. Aimed at clients with minimal budgets. (e.g., $75-$125/hour). Clearly state it's primarily automated.
- Standard Pentest (Manual Core): A balanced offering with significant manual testing. (e.g., $175-$250/hour). This should be your most common offering.
- Advanced Pentest (Deep Dive/Red Team): Higher rate, extensive scope, complex attack simulations, focus on business logic and impact. (e.g., $250-$400+/hour).
- Factor in Project Complexity: For fixed-price projects, estimate the total hours required for each phase (scoping, testing, reporting, debriefing) and multiply by your hourly rate for that service tier. Use ranges or add contingencies for unforeseen complexities.
- Small Web App: Estimate 40-80 hours.
- Medium Network: Estimate 80-160 hours.
- Large Enterprise/Red Team: Estimate 200-500+ hours.
- Consider Value-Based Pricing: For high-impact engagements, where the potential loss from a breach is astronomical, price based on the value of the risk mitigated rather than just the hours spent. This requires strong client communication and justification.
- Add-ons and Specializations: Offer specific modules like social engineering campaigns, phishing simulations, or cloud configuration reviews as separate line items or packages.
Your rate card should be a living document, reviewed and adjusted annually based on market rates, your growing expertise, and changes in your operational costs. Invest in tools and certifications to justify higher rates over time.
Frequently Asked Questions
- What is the difference between penetration testing and vulnerability scanning?
- Vulnerability scanning is an automated process that identifies known weaknesses based on signatures. Penetration testing is a manual process that simulates real-world attacks to exploit vulnerabilities, assess their impact, and determine the extent of potential compromise.
- How long does a penetration test typically take?
- The duration varies greatly depending on the scope and complexity. A small web application test might take a few days, while a comprehensive network assessment or red team exercise could take several weeks.
- Can I use the findings from a penetration test for compliance audits?
- Yes, a well-documented penetration test report, especially one adhering to specific compliance frameworks (like PCI DSS or HIPAA), is often a requirement for audits.
- What if a vulnerability is found that could cause significant disruption?
- Ethical penetration testers have a responsibility to communicate critical findings immediately to the client, often outside the formal reporting process, to allow for prompt remediation and prevent business disruption.
- How do you ensure client data confidentiality?
- Confidentiality is paramount. We typically sign Non-Disclosure Agreements (NDAs) and employ secure data handling practices throughout the engagement. All findings and reports are treated with the highest level of confidentiality.
The Contract: Securing Your Next Engagement
The proposal is signed, the scope is agreed upon. Now, the real work begins. Your task is to not just execute the test, but to deliver a report that is actionable, insightful, and undeniably valuable. Can you articulate the business risk associated with a missed SQL injection in a way that makes a CEO understand the potential financial fallout? Can you demonstrate that the 3 hours spent discovering a privilege escalation path were worth more than the 3 days a scanner might have spent searching for surface-level flaws?
Your challenge: Take a hypothetical scenario – a small e-commerce platform with a customer database containing PII. Outline the potential attack vectors an external attacker might use, focusing on 2 distinct vulnerabilities. For each, describe the manual exploit process and the potential business impact (data breach, financial loss, reputational damage). Then, assign a "diagnostic-based" price range for testing these specific vectors, justifying your pricing based on complexity and potential impact.
For more in-depth insights and continuous updates, visit Sectemple.
Explore related content on my other blogs: El Antroposofista, Gaming Speedrun, Skate Mutante, Budoy Artes Marciales, El Rincón Paranormal, Freak TV Series.
Discover unique NFTs at Mintable.app/u/cha0smagick.