The glint of chrome, the silent hum of electric power – Tesla cars have captured imaginations, and unfortunately, the attention of those with less noble intentions. The allure of effortless entry and a smooth ride can be overshadowed by a chilling reality: the digital locks that secure these vehicles are not impenetrable. In the shadowy corners of the digital realm, vulnerabilities are constantly probed, and the methods to bypass them evolve. Today, we dissect an operation that turns a prized possession into a target, exploring how a sophisticated attack can compromise a Tesla's security with alarming speed. This isn't about glorifying compromise; it's about understanding the anatomy of a threat to build fortifications.
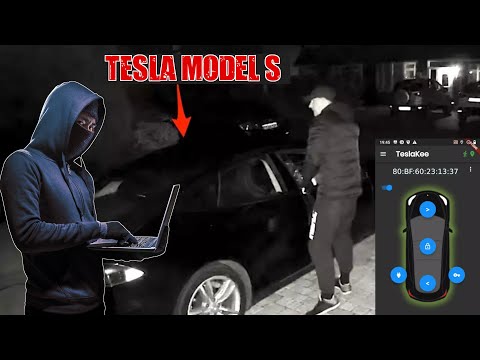
The digital fortress surrounding a Tesla, while advanced, has shown cracks. Multiple vectors have been identified, each exploiting a specific weakness in the vehicle's interconnected systems. One critical pathway involves vulnerabilities within the Near Field Communication (NFC) key cards, the very convenience that allows for quick access. An attacker, armed with the right tools and knowledge, can leverage these flaws to effectively 'register' a counterfeit key to the vehicle, granting them unauthorized ownership.
But authentication is only one layer. Even with multi-factor driving security features like Pin2Drive enabled, a separate, critical vulnerability can allow the attacker to bypass this final barrier. This dual exploitation means that unlocking the car is merely the prelude; driving it away becomes the grim finale, all achievable within an astonishingly short timeframe. The demonstration, though alarming, serves as a stark reminder that no system is entirely immune and that constant vigilance is the price of security.
Understanding the Attack Vectors
The compromise of a Tesla vehicle typically hinges on exploiting weaknesses in its digital access and control systems. The primary tools of this trade exploit the very technology designed for user convenience.
NFC Key Card Vulnerability
Tesla vehicles utilize NFC key cards for entry and ignition. These cards store cryptographic data that the vehicle uses to authenticate the user. The vulnerability lies in how the car handles the registration of new key cards. In certain scenarios, an attacker can intercept or manipulate the communication during the key registration process.
- **Attack Mechanism**: An attacker, physically near the vehicle or through a compromised onboard system, can initiate a process that tricks the car into accepting a newly cloned key card. This often involves relay attacks or exploiting flaws in the authentication handshake between the key card and the vehicle's ECU (Electronic Control Unit).
- **Impact**: Successful exploitation of this vulnerability means the attacker can add their own key to the vehicle's authorized list, effectively gaining physical access and the ability to start the car.
Pin2Drive Bypass
To further enhance security, Tesla implemented features like Pin2Drive, which requires a user-defined PIN code before the vehicle can be driven, even with an authorized key. However, like many security layers, this is not infallible.
- **Attack Mechanism**: Research has demonstrated that even with Pin2Drive enabled, certain exploits can bypass this requirement. This might involve manipulating the vehicle's internal state, exploiting firmware bugs, or using specialized diagnostic tools to override security protocols. The exact method often depends on the vehicle's software version and specific hardware configuration.
- **Impact**: This bypass effectively nullifies the secondary authentication layer, allowing the attacker to drive the vehicle away once the key has been compromised.
The Temporal Aspect: Gone in 130 Seconds
The speed at which these attacks can be executed is perhaps the most alarming aspect. Demonstrations have shown the entire process, from initial access to driving away, can be completed in under two minutes. This brief window highlights the importance of quick detection and robust preventative measures.
Defensive Strategies: Building the Digital Ramparts
While the sophistication of these attacks is a concern, owners and security professionals can implement layered defenses to significantly mitigate the risk. The principle of "defense in depth" is paramount here, ensuring that the compromise of one layer does not lead to complete system failure.
NFC Security Augmentation
The convenience of NFC comes with inherent risks. Strengthening its security requires a multi-pronged approach.
- **Key Card Storage**: Consider storing NFC key cards in specialized RFID-blocking pouches or wallets when not in use. This prevents unauthorized reading or relay attacks from a distance.
- **Firmware Updates**: Regularly update your Tesla's software. Manufacturers often patch vulnerabilities as they are discovered. Staying current is a fundamental step in maintaining security.
- **Access Control Review**: Periodically review the list of authorized keys associated with your vehicle through the Tesla app. Remove any keys that are no longer recognized or necessary.
Enhancing Pin2Drive and Driving Security
Even with the Pin2Drive feature, additional measures can bolster security.
- **Strong PIN Codes**: Use complex, unpredictable PIN codes for Pin2Drive. Avoid easily guessable sequences like birthdates or common patterns.
- **Physical Security**: While not directly related to the digital attack, traditional physical security measures remain relevant. Parking in well-lit areas and utilizing any available physical deterrents can add extra friction for an attacker.
- **Monitoring and Alerts**: Enable any available security alerts through the Tesla app. Notifying you of unusual activity, such as unauthorized key registration attempts or unexpected vehicle movement, can be crucial in early detection.
Anatomy of a Counter-Attack: Threat Hunting and Analysis
For those tasked with protecting fleets or investigating such incidents, the technical details of the attack provide valuable intelligence for threat hunting.
Indicators of Compromise (IoCs)
Detecting an attempted or successful compromise often involves looking for specific anomalies.
- **Unusual Key Registration Events**: Logs detailing unexpected key card registration attempts outside of normal usage patterns.
- **Pin2Drive Bypass Logs**: System logs that indicate the Pin2Drive prompt was bypassed or deactivated without user authorization.
- **Unexpected Vehicle Movement**: Alerts from GPS tracking or vehicle telemetry suggesting unauthorized operation.
- **Communication Anomalies**: Network traffic analysis revealing suspicious communication patterns from the vehicle's diagnostic ports or wireless interfaces.
Investigative Tools and Techniques
Analyzing such incidents requires a methodical approach, akin to digital forensics.
- **Log Analysis**: Deep dives into vehicle event logs, system logs, and diagnostic data are essential. Tools that can parse and analyze large volumes of structured and unstructured data are invaluable.
- **Firmware Analysis**: For researchers or incident responders with appropriate access and authorization, analyzing the vehicle's firmware can reveal the precise mechanisms of the exploit.
- **Network Traffic Interception**: In a controlled, authorized environment, analyzing wireless traffic around the vehicle during a suspected attack can reveal relay or cloning attempts.
Veredicto del Ingeniero: ¿Vale la pena la conveniencia sobre la seguridad?
The core of this issue is the perennial tension between user convenience and robust security. Tesla's innovations in vehicle access are undeniable. However, the reported vulnerabilities highlight that the digital keys, while elegant, are susceptible to sophisticated attacks. For the average owner, understanding these risks and implementing basic defensive measures like secure key storage and regular software updates is crucial. For security professionals and fleet managers, the exploit serves as a case study in the evolving threat landscape of connected vehicles, necessitating continuous monitoring and incident response preparedness. The trade-off between a seamless user experience and absolute security is one that manufacturers and consumers alike must navigate critically.
Arsenal del Operador/Analista
To stay ahead in the arms race against sophisticated threats like Tesla key cloning, a well-equipped toolkit is indispensable:
- **Software:**
- **Wireshark:** For deep packet inspection and network traffic analysis.
- **Jupyter Notebooks (with Python libraries like Pandas, Scikit-learn):** For analyzing large datasets of vehicle logs and identifying anomalies.
- **Hex Editors (e.g., HxD):** For low-level binary analysis of firmware or data dumps.
- **Nmap/Masscan:** For network reconnaissance (in authorized environments) to understand the attack surface.
- **Hardware:**
- **RFID/NFC Analyzers/Cloners (e.g., Proxmark3):** Essential for understanding and replicating NFC-based attacks (for research and testing purposes only).
- **Diagnostic Tools (OEM specific):** For accessing vehicle-specific logs and diagnostic information.
- **Certifications:**
- **Certified Ethical Hacker (CEH):** Provides a broad understanding of hacking techniques and tools.
- **GIAC Global Incident Handler (GCIH):** Focuses on incident detection and response.
- **Offensive Security Certified Professional (OSCP):** Develops hands-on penetration testing skills.
- **Books:**
- *"The Car Hacker's Handbook: A Guide to Wireless Vehicle Exploitation"* by Craig Smith: Fundamental reading for understanding vehicle security.
- *"Applied Cryptography"* by Bruce Schneier: For a deep dive into cryptographic principles often exploited in these attacks.
Taller Defensivo: Fortaleciendo la Credencial del Vehículo
This practical guide focuses on hardening the digital credentials of your vehicle, using principles applicable beyond just Teslas.
-
Segregar Credenciales: Use different physical key cards for different access scenarios if possible. Dedicate one card solely for driving and keep it secure.
-
Implementar Protocolos de Verificación Adicionales: If your vehicle's infotainment system allows for custom security settings, explore options for additional authentication prompts for critical functions like ignition or driving. While Tesla's Pin2Drive is built-in, consider if your vehicle offers similar or supplementary options.
-
Establecer Geolocalización y Notificaciones de Movimiento: Configure your vehicle's companion app (if available) to send instant alerts for any movement or ignition outside of designated geofenced areas or times. This provides immediate awareness of unauthorized use.
-
Auditar Accesos Registrados Regularmente: Treat your vehicle's key registry like a user access list for a critical system. Periodically log in to your vehicle's management portal and review all registered key fobs or cards. Remove any credentials that are no longer active or accounted for.
-
Utilizar Bloqueos Físicos como Barrera Secundaria: Consider using steering wheel locks or pedal locks as a physical deterrent. While they don't stop digital cloning, they add a crucial layer of friction that can deter opportunistic thieves who may not be prepared for a multi-stage attack.
Preguntas Frecuentes
¿Son todas las vulnerabilidades de Tesla explotables en tiempo real?
La explotabilidad en tiempo real depende de la versión específica del software y hardware del vehículo, así como de las herramientas y técnicas que posea el atacante. Las demostraciones públicas suelen utilizar métodos probados contra versiones específicas.
¿Cómo puedo saber si mi vehículo ha sido comprometido?
Busque señales como accesos no autorizados registrados en su cuenta, el vehículo activándose o moviéndose inesperadamente, o la imposibilidad de usar su llave legítima.
¿Qué debo hacer si creo que mi Tesla ha sido comprometido?
Contacte inmediatamente a Tesla Support y a las autoridades locales. Revise los registros de acceso en su aplicación Tesla e intente localizar el vehículo a través de su sistema de seguimiento GPS.
El Contrato: Asegura tu Perímetro Digital
Now, the knowledge is laid bare. The digital silk that wraps your vehicle's security has been unraveled. Your contract is simple: do not become another statistic in the quiet war fought on asphalt and silicon.
Your challenge: **Documento the digital handshake protocol** between a standard NFC key card and a vehicle's receiver. If you were tasked with *defending* against a relay attack, what specific signals or timing anomalies would you train your hypothetical intrusion detection system to look for? Provide a conceptual outline of such a system's detection logic in the comments below. Let's build the next layer of defense, together.

