Table of Contents
- The Digital Shadow: Phone Numbers as Intelligence Vectors
- Prerequisites: Arming Your Termux Operative Environment
- Walkthrough: Deploying PhoneInfoga in Termux
- Operationalizing PhoneInfoga: Beyond Installation
- Engineer's Verdict: The Mobile OSINT Advantage
- Analyst's Arsenal: Essential Tools for the Field
- Frequently Asked Questions
- The Contract: Your First Mobile OSINT Reconnaissance
The Digital Shadow: Phone Numbers as Intelligence Vectors
In the relentless pursuit of tactical advantage, every data point is a potential vulnerability or a strategic asset. A phone number, seemingly innocuous, is far more than a means of communication. It's a nexus, a unique identifier that can be correlated with social media profiles, leaked databases, geographical locations, and even operational history. PhoneInfoga is designed to exploit this nexus, transforming raw numerical data into actionable intelligence. Running it within Termux, a powerful terminal emulator for Android, democratizes this capability, putting advanced OSINT techniques directly into the hands of the field operative. This guide is your blueprint to mastering this potent combination.Prerequisites: Arming Your Termux Operative Environment
Before we begin the deployment, ensure your Termux environment is battle-ready. A clean, updated system is paramount to avoid the dreaded dependency hell that plagues less disciplined operations. Think of this as prepping the operational theater.- Termux Installed: The foundation of our mobile command center. Ensure you have the latest version from F-Droid or the official GitHub releases, as the Google Play Store version is outdated.
- Internet Connectivity: OSINT tools are useless without access to the vast, chaotic network. A stable connection is non-negotiable.
- Basic Terminal Familiarity: You need to be comfortable navigating directories, executing commands, and understanding basic syntax.
Walkthrough: Deploying PhoneInfoga in Termux
This is where the rubber meets the road. Follow these steps meticulously. Deviation is not an option when precision is key.- Update and Upgrade Packages:
Launch Termux and immediately sync your package lists and upgrade installed packages. This is your first line of defense against compatibility issues.
pkg update && pkg upgrade -y - Install Essential Tools:
PhoneInfoga requires
gitfor cloning andpythonfor execution. Ensure they are present.
If Python is already installed, this command will simply confirm its presence. Do not skip this step; it's the bedrock.pkg install git python -y - Clone the PhoneInfoga Repository:
Navigate to a directory where you wish to house your operational tools. The official GitHub repository is the only source you should trust.
This command pulls the latest stable version directly from the developer's repository.git clone https://github.com/sundowndev/phoneinfoga.git - Enter the Tool's Directory:
Change your current working directory to the newly cloned PhoneInfoga folder.
cd phoneinfoga - Install Python Dependencies:
PhoneInfoga is a Python application and relies on several external libraries. The
requirements.txtfile lists them all. Install them using pip.
This step is critical. Any missing dependency will render the tool non-functional.pip install -r requirements.txt
Operationalizing PhoneInfoga: Beyond Installation
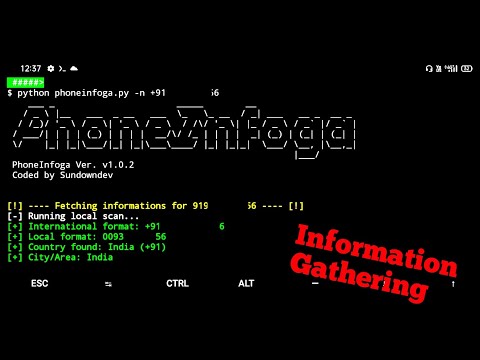
With the tool deployed, the real work begins. PhoneInfoga doesn't just fetch data; it analyzes and correlates it. The primary command is straightforward, but understanding its output is the operative skill. The basic syntax for running PhoneInfoga is:python3 phoneinfoga.py -n [PHONE_NUMBER][PHONE_NUMBER] with the target number, preferably in international format (e.g., +1XXXXXXXXXX for the US, +44XXXXXXXXXX for the UK).
PhoneInfoga will then query various sources, attempting to identify:
- Carrier Information: The mobile network provider.
- Line Type: Mobile, Landline, VoIP.
- Country and Region: Geographical origin associated with the number.
- Potential Social Media Links: Correlating the number with known profiles.
- Risk Assessment: Flagging numbers associated with spam or fraudulent activities.
"The network is not a place you go; it's a place you are. And every node has a story, if you know how to listen." - Attributed to a legendary dark web analyst.
Engineer's Verdict: The Mobile OSINT Advantage
Deploying PhoneInfoga within Termux is a masterstroke for mobile-first reconnaissance. For the security professional or bug bounty hunter who operates on the move, this integration offers unparalleled convenience. While desktop tools might offer more raw processing power or a broader array of features, the accessibility and immediacy of a mobile setup cannot be understated. It transforms downtime into operational uptime. The primary drawback is, naturally, the limited processing power and potential for network instability compared to a dedicated workstation. However, for targeted, on-the-go information gathering, it's an indispensable asset.Analyst's Arsenal: Essential Tools for the Field
To complement PhoneInfoga and elevate your mobile OSINT game, consider these additional tools and resources:- Termux:API: Allows Termux apps to access device hardware and features (e.g., camera, location).
- Nmap: For network scanning, available via
pkg install nmapin Termux. Essential for understanding target network perimeters. - Hydra: A powerful brute-force login cracker. Install with
pkg install hydra. Use responsibly and ethically. - Recon-ng: A modular framework for web reconnaissance. Requires more involved setup but is incredibly powerful.
- The Web Application Hacker's Handbook: The bible for web security professionals. Its principles are timeless, even when applied from a mobile device.
- OSCP (Offensive Security Certified Professional) Certification: While not a tool, the knowledge gained from preparing for this certification is invaluable for understanding attack vectors and defensive strategies. Consider investing in training courses for advanced pentesting techniques.
Frequently Asked Questions
Q1: Can PhoneInfoga be used on iOS devices?
Direct installation of PhoneInfoga on iOS is not natively supported due to Apple's restrictive operating system. However, you might explore cloud-based Termux instances or remote SSH access to a Linux server running PhoneInfoga from an iOS device.
Q2: Is PhoneInfoga illegal to use?
The tool itself is not illegal; it's a data collection utility. However, using it to gather information on individuals without their explicit consent or for malicious purposes is illegal and unethical. Always operate within legal boundaries and ethical guidelines.
Q3: What's the best way to handle rate limits from APIs PhoneInfoga uses?
Sophisticated OSINT operators often use rotating proxies or VPNs to mitigate API rate limits. For advanced users, exploring tools that manage proxy rotation within Termux can be beneficial.
Q4: How can I contribute to PhoneInfoga development?
Visit the official PhoneInfoga GitHub repository. Developers are usually welcoming of bug reports, feature requests, and pull requests from the community.





