STRATEGY INDEX
- Mission Briefing: The Digital Ransom
- Attack Vector 1: The Art of Guessing
- Attack Vector 2: Information Harvesting
- Attack Vector 3: The Cracking Engine
- Attack Vector 4: Credential Spraying
- Attack Vector 5: The Credential Stuffing Machine
- Fortification: Your Defensive Blueprint
- Comparative Analysis: Tactics vs. Defenses
- Frequently Asked Questions
- The Engineer's Verdict
- The Operator's Arsenal
- About The Cha0smagick
- Mission Debrief: Your Next Objective
Mission Briefing: The Digital Ransom
In the shadowy corners of the digital realm, information is the ultimate currency, and passwords are its keys. Hackers, like meticulous locksmiths or ruthless burglars, constantly probe for weaknesses to gain unauthorized access. Understanding their methods isn't just about knowledge; it's about survival. This dossier, codenamed "Operation: Password Integrity," will dissect the five principal attack vectors employed by malicious actors to pilfer your credentials. Equip yourself with this intelligence, and you can begin to construct an impenetrable defense.
The landscape of cyber threats is ever-evolving. For a broader perspective on emerging risks, delve into the 2024 Threat Intelligence Index. It provides critical insights into ransomware, dark web threats, and the escalating dangers posed by AI.
Attack Vector 1: The Art of Guessing (Simple & Brutal)
This is the most rudimentary, yet surprisingly effective, method. Attackers exploit human psychology and predictable patterns. It involves trying common, easily guessable passwords like "123456", "password", "qwerty", or personal information such as birthdays, pet names, or family members' initials.
Methodology:
- Dictionary Attacks: Using lists of common words and phrases.
- Pattern-Based Guessing: Exploiting common password structures (e.g., Year + Name, Name + Number).
- Social Engineering Reconnaissance: Gathering personal information from social media profiles, public records, or previous data breaches to craft educated guesses.
Why it works: Many users opt for convenience over security, creating weak passwords or reusing them across multiple platforms. It's low-effort for the attacker and can yield immediate results if successful.
Attack Vector 2: Information Harvesting (The Subtle Approach)
Instead of directly attacking a password, this method focuses on intercepting or acquiring it through indirect means. It's about being sneaky and leveraging information asymmetry.
Methodology:
- Phishing: Deceptive emails, messages, or websites designed to trick users into voluntarily entering their credentials. These can be sophisticated, mimicking legitimate communications perfectly.
- Malware (Keyloggers/Trojans): Installing software on a user's device that records keystrokes or captures screen data when credentials are typed.
- Shoulder Surfing: Physically observing someone entering their password, often in public places or through unsecured surveillance.
- Confidentiality Breaches: Obtaining credentials through insider threats or compromised internal systems.
Why it works: It bypasses direct technical defenses by exploiting human trust and vulnerability. A well-crafted phishing campaign can be incredibly difficult to detect.
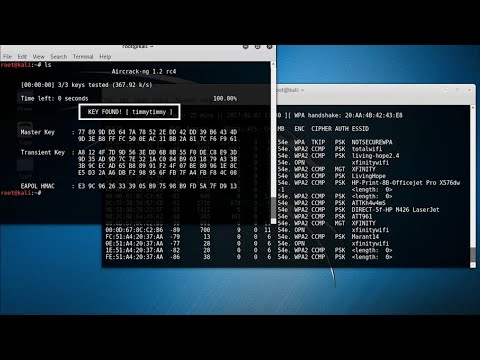
Attack Vector 3: The Cracking Engine (Computational Power)
This is a more technical approach that involves systematically trying combinations of characters to discover a password, often by analyzing breached password hashes. Attackers typically use specialized software and powerful hardware.
Methodology:
- Brute Force Attacks: Systematically trying every possible combination of letters, numbers, and symbols. This is computationally intensive and time-consuming but guaranteed to succeed eventually if not protected against. To prevent this, implementing measures like rate limiting is crucial. For a deeper dive into the mechanics, understand how a Brute Force Attack functions.
- Dictionary Attacks (Advanced): Similar to simple guessing, but uses highly sophisticated, customized wordlists and linguistic rules.
- Hybrid Attacks: Combining dictionary words with numerical or symbolic substitutions (e.g., "P@sswOrd1").
- Rainbow Tables: Pre-computed tables that map hash values back to potential passwords, significantly speeding up the cracking process for common hashes.
Why it works: With sufficient computational power and time, almost any password can eventually be cracked. The effectiveness increases if the attacker obtains password hashes from a data breach.
Attack Vector 4: Credential Spraying (Targeted Broad Assault)
Credential spraying is a sophisticated variant of brute-force attacks. Instead of trying many passwords against one account, attackers use a small list of common passwords against a large number of accounts.
Methodology:
- The attacker obtains a list of usernames (often from previous breaches or reconnaissance).
- A small set of common passwords (e.g., "Password123", "Spring2024", "123456789") is used against these usernames.
- Objective: To avoid account lockout policies that trigger after too many failed attempts on a single account. By distributing attempts across many accounts, the attacker can remain under the radar for longer.
Why it works: Many organizations use similar password policies and common default passwords. This method exploits the widespread use of weak password choices across an organization's user base.
Attack Vector 5: The Credential Stuffing Machine (Leveraging Breaches)
This is arguably one of the most prevalent and dangerous attacks today. It relies on the unfortunate reality that users frequently reuse the same username and password combinations across multiple websites and services.
Methodology:
- Attackers acquire large databases of stolen credentials (username:password pairs) from previous data breaches.
- They then use automated tools to "stuff" these credentials into login forms on other websites and services.
- If a user has reused their credentials, the attacker gains immediate access to their secondary accounts.
Why it works: User password reuse is rampant. A single breach can provide attackers with access to a user's email, banking, social media, and other sensitive accounts.
Fortification: Your Defensive Blueprint
Securing your digital assets against these sophisticated threats requires a multi-layered approach. It's time to move beyond basic password hygiene and implement robust security measures.
- Multi-Factor Authentication (MFA): This is your primary line of defense. MFA adds an extra layer of security by requiring users to provide two or more verification factors to gain access to a resource. This can include something you know (password), something you have (a phone, a security key), or something you are (biometrics).
- Password Managers: Utilize reputable password managers to generate and store unique, complex passwords for every online service. This eliminates the need for users to remember multiple passwords and prevents credential stuffing.
- Passkeys: The future of authentication. Passkeys are a more secure and user-friendly alternative to passwords, using cryptographic pairs tied to a device or biometric. They are resistant to phishing and credential stuffing.
- Rate Limiting: Implement strict limits on the number of login attempts allowed within a specific time frame. This directly thwarts brute-force and credential spraying attacks.
- Account Lockouts: After a set number of failed login attempts, temporarily or permanently lock the affected account.
- Monitoring and Alerting: Continuously monitor login activity for suspicious patterns (e.g., multiple failed attempts, logins from unusual locations) and set up real-time alerts.
- User Education: Regularly train users on the importance of strong, unique passwords, the dangers of phishing, and the benefits of MFA and password managers.
Comparative Analysis: Tactics vs. Defenses
The effectiveness of hacker tactics is directly countered by the strength of defensive strategies. Let's break down the synergy:
- Guessing/Harvesting vs. Password Managers & MFA: Guessing relies on human error and predictability. Password managers enforce complexity and uniqueness, while MFA provides a second, independent layer that even a compromised password cannot bypass.
- Cracking/Spraying vs. Rate Limiting: Cracking and spraying are brute-force methods. Rate limiting and account lockouts are the direct technical countermeasures, making these attacks prohibitively slow or impossible.
- Credential Stuffing vs. Unique Passwords & MFA: Stuffing exploits password reuse. By using unique passwords for every service (via a password manager) and enforcing MFA, the impact of a single breached credential is contained, rendering stuffing ineffective.
The battle is won not by eliminating one attack, but by building a resilient defense that neutralizes multiple vectors simultaneously. For organizations looking to understand the broader impact of these threats, the Cost of a Data Breach report offers invaluable statistics and insights.
Frequently Asked Questions
Q1: How often should I change my passwords?
A1: While frequent changes were once recommended, the current best practice, especially with password managers and MFA, is to use strong, unique passwords and only change them if a breach is suspected or the password is known to be weak.
Q2: Are password managers truly safe?
A2: Reputable password managers use strong encryption (like AES-256) and require a master password that should be exceptionally strong and unique. They significantly enhance security compared to reusing passwords or using weak ones.
Q3: What's the difference between a brute force attack and credential stuffing?
A3: A brute force attack tries many passwords against a single account. Credential stuffing uses lists of *already known* username/password pairs from data breaches to try against multiple accounts, exploiting password reuse.
Q4: Can passkeys completely replace passwords?
A4: While passkeys offer superior security and user experience, widespread adoption is still ongoing. For now, they often work alongside passwords, but the trend is towards passwordless authentication.
The Engineer's Verdict
The methods employed by hackers to steal passwords are a testament to their ingenuity, but they are not insurmountable. Each tactic, from the low-tech art of guessing to the automated scale of credential stuffing, preys on predictable human behavior and systemic weaknesses. The critical takeaway is that robust cybersecurity is not a single solution, but a layered strategy. Implementing strong password policies, universally adopting Multi-Factor Authentication, leveraging password managers, and embracing emerging technologies like passkeys are no longer optional – they are the baseline requirements for digital survival in 2024 and beyond. Treat your credentials with the value they hold; they are the gatekeepers to your digital life.
The Operator's Arsenal
To effectively defend against these threats, consider integrating the following tools and knowledge into your operational toolkit:
- Password Managers: 1Password, Bitwarden, LastPass
- MFA Solutions: Google Authenticator, Authy, YubiKey (Hardware Security Key)
- Passkey Support: Google, Apple, Microsoft ecosystems, and growing browser/website support.
- Security Awareness Training Platforms: KnowBe4, Proofpoint Security Awareness Training
- Threat Intelligence Resources: IBM Security (for reports like the Threat Intelligence Index), CISA Alerts, OWASP Foundation.
- Learning Resources: CompTIA Security+, Certified Information Systems Security Professional (CISSP), Offensive Security Certified Professional (OSCP) certifications, and continuous reading of cybersecurity news.
About The Cha0smagick
I am The Cha0smagick, an engineer and ethical hacker operating at the intersection of technology and security. My experience spans deep system analysis, reverse engineering, and the pragmatic application of cybersecurity principles. I construct these dossiers to demystify complex digital threats, providing actionable intelligence and blueprints for defense. My goal is to empower you with the knowledge to navigate the evolving cyber landscape with confidence and resilience.
Mission Debrief: Your Next Objective
This dossier has equipped you with intelligence on the primary methods hackers use to steal passwords. Understanding these threats is the first step towards comprehensive defense. Now, it's time for you to act.
"The only cybersecurity strategy that works is one that is comprehensive, layered, and constantly evolving."
Your Mission: Execute, Share, and Debate
If this blueprint has saved you valuable time and enhanced your understanding, consider it your duty to share this knowledge. A well-informed operative strengthens the entire network.
- Share the Dossier: Forward this analysis to your colleagues, CISO, or anyone who manages digital assets. Knowledge is a weapon, and this is a tactical guide.
- Implement Defenses: Review your current authentication practices. Are you using MFA everywhere possible? Do you have a password manager? Are you exploring passkeys? Execute the fortification strategies outlined above.
- Demand Better: Encourage your service providers and employers to implement robust security measures. Your active participation shapes the security of the digital ecosystem.
Debriefing of the Mission
Did this analysis uncover any blind spots in your security posture? What other hacker tactics do you want dissected in future dossiers? Your feedback is critical intelligence. Share your thoughts, your experiences, and your questions in the comments below. Let's engage in a constructive debate and refine our collective defenses.
For continuous learning and to explore more critical security topics, consider integrating a platform like Binance for managing your digital assets and exploring financial tools in the evolving digital economy. Diversification and securing your financial identity are paramount.
Trade on Binance: Sign up for Binance today!