Table of Contents
The Shadowy Network
The digital landscape is a battlefield, and your traffic is the intel. In this concrete jungle, unencrypted packets are like neon signs screaming your location. We’re not here to chat about firewalls; we’re here to disappear. Today, we dive deep into the art of masking your digital presence, turning your network traffic into a phantom. We'll be dissecting two potent tools: Proxychains and the notorious Tor network. This isn't about casual browsing; it's about tactical anonymity, the kind you need when you're peeling back layers of a system or simply want to exist outside the surveillance grid. Forget privacy policies; we're building our own.
The core of this operation is making any TCP connection made by any given application act like a ghost. We want to force traffic through proxies, and when combined with Tor, we achieve a level of obscurity that makes attribution a high-stakes gamble. This guide is your blueprint for building that cloak of invisibility.
Deconstructing Proxychains
Proxychains is a versatile tool that acts as an intermediary, forcing any TCP connection from an application through a proxy server. Think of it as a bouncer for your network requests, redirecting them to a specific backstage entrance before they hit the main stage. It's not magic; it's engineering. You configure it, and then you tell your applications to talk through it.
The configuration file, `proxychains.conf`, is your command center. Here, you define the type of proxy chain (dynamic, strict, random) and list your proxy servers. For our purposes, we'll focus on a dynamic chain, allowing Proxychains to intelligently route traffic through multiple proxies.
"Networking is not about the lines on the diagram. It's about the packets that flow, and how they are controlled." - Ancient Network Operator Proverb
The power of Proxychains lies in its simplicity and its ability to integrate with virtually any TCP-based application. From a simple `curl` command to a full-blown web browser, if it makes network calls, Proxychains can reroute them. This makes it an indispensable tool for penetration testers and security researchers who need to ensure their activities originate from an unexpected location.
Beneath the Onion: Tor's Layers
The Tor (The Onion Router) network is the backbone of many anonymity efforts. It's a decentralized network of relays designed to anonymize your internet traffic. Instead of a direct connection from you to a server, your traffic is encrypted in multiple layers, like an onion, and bounced through a series of volunteer-operated servers (relays). Each relay decrypts one layer of encryption to know which is the next hop, passing the remaining encrypted data to the next relay. The final relay, the exit node, decrypts the final layer and sends the traffic to its destination. Crucially, the exit node does not know the original source IP address, and the entry node does not know the final destination.
This multi-hop approach makes tracing the origin of the traffic incredibly difficult, though not impossible. Understanding the architecture of Tor—entry nodes, middle nodes, and exit nodes—is critical. While Tor offers robust anonymity, it's essential to acknowledge its limitations. Exit nodes can potentially monitor unencrypted traffic, which is why using HTTPS is always recommended, even over Tor.
Weaving the Cloak: Proxychains + Tor
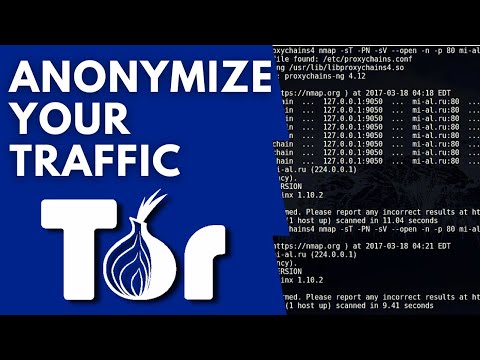
The real magic happens when we combine the routing capabilities of Proxychains with the anonymity provided by Tor. By configuring Proxychains to use the Tor network's SOCKS proxy (typically running on `127.0.0.1:9050`), we can force ANY application's TCP connections through Tor. This bypasses the native Tor Browser bundle and allows you to anonymize specific applications or even your entire system's traffic.
This integration is paramount for operations where you need granular control over your anonymization. Imagine needing to scan a target using Nmap from an IP address that is not your own and is protected by Tor's exit nodes. Using Proxychains with Tor empowers you to do precisely that.
The critical step is ensuring your `proxychains.conf` file is correctly set up. You'll want to specify a dynamic chain and point it to the Tor SOCKS proxy. This setup ensures that your traffic not only goes through a proxy but is also layered with Tor's encryption and anonymization protocols.
Taller Práctico: Encrypting Your Footprints
Let's get our hands dirty. This is where theory meets the gritty reality of command lines.
-
Installation: The Foundation
First, you need the building blocks. On Debian/Ubuntu systems, this is usually as simple as:
For other distributions, consult your package manager or compile from source. Ensure the Tor service is running:sudo apt update sudo apt install tor proxychains -y
Verify Tor is listening, typically on port 9050:sudo systemctl start tor sudo systemctl enable tor # To ensure it starts on bootsudo ss -tulnp | grep 9050 -
Proxychains Configuration: The Blueprint
Edit the configuration file. The default location is usually `/etc/proxychains.conf`. You'll want to ensure it looks something like this, paying close attention to the `chain_type` and the specific proxy.
Crucially, the `socks5 127.0.0.1 9050` line must be present and correctly configured to point to your running Tor instance.# proxychains.conf strict_chain # Use the following proxies for strict chain, it terminates on the first host that fails. # For example, if you want to chain 192.168.1.1, 192.168.1.2 and 192.168.1.3, you can # write the following config: # server 192.168.1.1 # server 192.168.1.2 # server 192.168.1.3 # # quiet_chain # Use the following proxies, while the chain stops only when all the previous proxies # in the list are already dead. This is the default behaviour. # # dynamic_chain # Use the following proxies, while the chain stops only when all the previous proxies # in the list are already dead. When you run out of proxies, it will try to find # new proxies on the fly. (This is the default chain type) # # Note that you can not mix chain types. # # The following are the default values that will be used if you do not specify the # country, state and city. This is useful for random chain. country 00 state 00 city 00 # Always run Tor as a SOCKS proxy on 127.0.0.1:9050 # Ensure this is the FIRST entry in your proxylist. # The Tor service MUST be running for this to work. socks5 127.0.0.1 9050 # Other proxies can be added here if needed. # For example, a different SOCKS proxy: # socks4 192.168.1.2 1080 # Or an HTTP proxy: # http 192.168.1.3 8080 -
Running Applications: The Infiltration
Now, launch your target application prefixed with `proxychains`. For a web browser (e.g., Firefox):
For a command-line tool like `curl` to check your IP:proxychains firefox
You should see an IP address that is part of the Tor network, not your actual public IP.proxychains curl ifconfig.me
The Fissures in the Armor
While Proxychains and Tor offer significant anonymity, they are not foolproof. The exit node is a critical point of failure. If the traffic between the exit node and the destination server is not encrypted (i.e., not HTTPS), the operator of the exit node can see and potentially modify your data. This is why employing end-to-end encryption, preferably TLS/SSL, is non-negotiable. Tools like HTTPS Everywhere can help enforce this.
Furthermore, sophisticated adversaries might employ timing attacks or traffic correlation to de-anonymize users, especially if they control both entry and exit nodes. Browser fingerprinting and client-side vulnerabilities can also betray your identity. Therefore, always practice good operational security (OPSEC) alongside your technical anonymization tools.
"Anonymity is a shield, but even the best shields can be pierced by the right weapon." - cha0smagick
Consider your threat model. Are you hiding from your ISP, a malicious actor, or state-level surveillance? Each scenario demands a different level of precaution. For critical operations, using a virtual machine to isolate your anonymized activities is standard practice. This prevents potential leaks from your host operating system.
Arsenal del Operador/Analista
- Proxychains: The traffic rerouter. Essential for forcing applications through proxies.
- Tor Browser Bundle: For general browsing and understanding Tor's ecosystem. While we use Tor as a service here, the bundle is a great starting point.
- Nmap: Network scanner that can be anonymized with Proxychains for reconnaissance.
- Wireshark/tcpdump: Network analysis tools to understand traffic patterns (use with caution and ethically).
- Virtual Machine Software (e.g., VirtualBox, VMware): For isolating anonymized activities and creating secure, reproducible environments.
- Books: "The Web Application Hacker's Handbook" for understanding targets, and any advanced guides on network security and anonymity protocols.
- Certifications: While not directly tied, certifications like OSCP or CISSP demonstrate a foundational understanding of security that complements these tools.
Preguntas Frecuentes
What is the primary function of Proxychains?
Proxychains forces any TCP connection from a given application to go through specified proxy servers, effectively masking the origin IP address of those connections.
How does Tor provide anonymity?
Tor anonymizes traffic by encrypting it in multiple layers and routing it through a volunteer network of relays, making it difficult to trace the connection back to its origin.
Can I use Proxychains with any application?
As long as the application makes TCP connections, Proxychains can generally be used to reroute its traffic. However, some applications with specific network handling might require custom configurations.
Is using Tor and Proxychains completely risk-free?
No. While it significantly enhances anonymity, vulnerabilities can exist, particularly at the Tor exit node if traffic is unencrypted (no HTTPS) or through advanced correlation attacks. OPSEC is crucial.
How can I verify my anonymization is working?
You can use websites like "ifconfig.me" or "checkip.amazonaws.com" to check your public IP address. Before running traffic through `proxychains`, check your IP; after, run the check again using `proxychains curl ifconfig.me`. The IPs should differ.
El Contrato: Advanced Anonymity Scenarios
You've mastered the basics of weaving Proxychains and Tor into a single cloak of digital invisibility. Now, the contract: Imagine you need to conduct reconnaissance on a sensitive target. Your objective is to map open ports and identify running services without revealing your presence. How would you leverage Proxychains and Tor not just for basic IP masking, but to actively confuse potential network defenders? Consider using random proxy chains within Proxychains, or periodically switching Tor entry nodes. Discuss the potential detection vectors and how you might further obfuscate your methodology to evade sophisticated Intrusion Detection Systems (IDS) or honeypots. What are the trade-offs in terms of speed and reliability when implementing these advanced obfuscation techniques?

