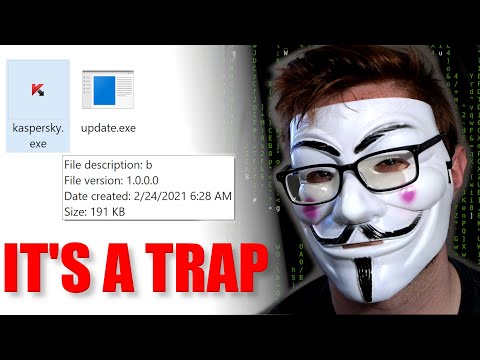
The digital underworld is a realm of shadows and deception. Among the most insidious threats are those that masquerade as trusted guardians. Today, we're not patching systems; we're performing an autopsy on a digital phantom. A file, lurking in the dark corners of the web, claims to be a Kaspersky antivirus executable, but under the harsh light of analysis, it reveals its true, malicious intent. This is not about fixing a system; it's about understanding the enemy's playbook.
In the constant cat-and-mouse game between defenders and attackers, decoy executables are a recurring tactic. They prey on user trust, exploiting the familiarity of legitimate software names to bypass initial scrutiny. Our target: a sample masquerading as kaspersky.exe. This isn't just a file; it's a carefully crafted illusion designed to infiltrate, propagate, and ultimately compromise systems. To truly defend, we must think like the adversary. We must dissect their tools, understand their methods, and anticipate their next move. This deep dive into malware analysis aims to pull back the curtain on such deceptions.
The Anatomy of Deception: Initial Observations
The first rule in malware analysis is to establish a safe, isolated environment. A virtual machine, air-gapped from your primary network, is non-negotiable. We're not playing games here; we're dealing with code that has one primary objective: to cause harm. The moment you execute a suspicious file on your host, you've already lost.
Upon initial inspection of our kaspersky.exe sample, several red flags immediately emerge. The file size is suspiciously small for a modern antivirus installer, which typically bundles numerous components and signature databases. Furthermore, a quick check against VirusTotal™ might show a low detection rate, a common indicator that the malware authors have implemented basic evasion techniques or that the sample is novel.
"Trust, but verify." - Ronald Reagan. In cybersecurity, it's more accurately: "Never trust, always verify."
Static analysis, the process of examining a file without executing it, is our starting point. Tools like PE Explorer, IDA Pro, or Ghidra (a free, powerful alternative from the NSA) allow us to peek under the hood. We're looking for:
- Unusual strings: Hardcoded IP addresses, suspicious URLs, filenames that don't align with legitimate antivirus operations.
- Imported functions: What system APIs does the executable intend to use? Antivirus software usually imports functions for file system access, network communication, and process manipulation. Malware will often import similar functions but for nefarious purposes.
- Packers or obfuscation: Malware authors frequently "pack" their executables to make static analysis more difficult. Identifying the packer is the first step in unpacking and revealing the original code.
Unmasking the Payload: Dynamic Analysis Walkthrough
Static analysis only tells part of the story. To understand what kaspersky.exe *does*, we must observe it in action. This is where dynamic analysis, executed within our sandboxed environment, becomes critical.
Our virtual machine is set up with:
- A clean operating system installation.
- Monitoring tools: Process Monitor (Procmon) for file system and registry activity, Process Explorer for process trees and handles, Wireshark for network traffic analysis, and a debugger (like x64dbg) for stepping through code execution.
- Important Note: Ensure your network interfaces within the VM are configured carefully. For network analysis, you might want to capture traffic on a host-only network or use a dedicated packet capture device if strictly necessary, though often observing outbound connections from the VM is sufficient for initial analysis.
The execution steps:
- Snapshot the VM: Before any execution, take a clean snapshot. This allows you to revert the VM to its original state after the analysis.
- Launch Monitoring Tools: Start Procmon, Process Explorer, and Wireshark. Configure Procmon to log filesystem, registry, and process/thread activity. Filter out noise where possible (e.g., exclude known AV processes if you have one running for analysis purposes, though ideally, the analysis VM should be free of all security software).
- Execute
kaspersky.exe: Run the suspect executable. - Observe Behavior:
- File System Activity: Does it create, delete, or modify files? Look for suspicious directories (e.g., Temp folders, user profile directories) where it might be dropping additional payloads or configuration files.
- Registry Modifications: Does it add entries to the registry? Persistence mechanisms (e.g., Run keys, Services) are often implemented here.
- Process Creation: Does it spawn new processes? This could indicate the execution of a secondary payload or a legitimate process being injected with malicious code.
- Network Connections: Where does it try to connect? Suspicious IP addresses, domain names, or unusual protocols are strong indicators of command-and-control (C2) communication or data exfiltration. Wireshark will be invaluable here.
- Take Another Snapshot: After the execution and observation period, take another snapshot to compare the changes.
- Analyze Logs: Review the captured data from Procmon and Wireshark meticulously. Correlate events. For example, a file creation event in a specific directory might be followed by a network connection that attempts to upload that file.
During dynamic analysis of our fake Kaspersky, we might observe it attempting to:
- Drop a second-stage payload (e.g., a downloader or a backdoor) into a hidden directory.
- Modify the hosts file or inject malicious DNS entries to redirect traffic.
- Attempt to connect to a hardcoded IP address or a dynamically resolved domain name for C2 instructions.
- Disable or tamper with existing security software.
Digging Deeper: Code Analysis and Vulnerability Exploitation
Once we have an idea of the malware's behavior, we can use a debugger for more in-depth code analysis. This is where we move from observing to understanding the 'how' and 'why'.
Using a debugger like x64dbg, we can:
- Set breakpoints at key locations identified during static analysis or dynamic observation (e.g., API calls related to network communication or file writing).
- Step through the code execution instruction by instruction.
- Examine memory and registers to understand the state of the program.
- Unpack packed code on-the-fly.
For our kaspersky.exe sample, a critical area of investigation would be the code responsible for its deceptive claims. How does it fool the user? Does it display a fake scan progress? Does it attempt to manipulate the user into granting it higher privileges? Understanding these mechanisms is key to developing effective countermeasures and educating users.
Furthermore, we must always consider if the malware itself has exploitable vulnerabilities. While attackers aim to exploit systems, sometimes their own tools contain flaws. Could a buffer overflow in the malware's network handling routine allow us to inject commands? Could improper input validation lead to privilege escalation within the malware's own execution context?
"The most effective way to gain an advantage is to understand the opponent's strategy better than they do." - Unknown. In the realm of malware, this means reverse engineering their tools.
The process involves identifying suspicious code constructs, such as:
- Unchecked buffer operations (e.g., `strcpy`, `sprintf`).
- Vulnerable deserialization routines.
- Improper handling of external input.
If such a vulnerability is found, we can craft an exploit. This typically involves:
- Fuzzing: Automatically feeding a wide range of malformed inputs to the executable to trigger crashes or unexpected behavior.
- Crash Analysis: Analyzing the crash dump to identify the exact input that caused the fault and pinpoint the vulnerable function.
- Exploit Development: Crafting a specific input that reliably triggers the vulnerability and allows for arbitrary code execution or other desired outcomes. This often involves understanding memory layout, stack manipulation, and shellcode.
Arsenal of the Analyst: Tools of the Trade
To effectively analyze malware like this deceptive kaspersky.exe, a robust set of tools is essential. While the specific choices can vary, a core set consistently proves invaluable:
- Virtualization Software: VMware Workstation/Fusion, VirtualBox. Essential for creating isolated analysis environments.
- Disassemblers/Decompilers: IDA Pro (industry standard, expensive), Ghidra (free, powerful), Binary Ninja (modern, scriptable).
- Debuggers: x64dbg (Windows, free, actively developed), OllyDbg (older Windows debugger), GDB (Linux).
- System Monitoring: Sysinternals Suite (Procmon, Process Explorer, Autoruns), API Monitor.
- Network Analysis: Wireshark, NetworkMiner.
- Memory Forensics: Volatility Framework. Useful for analyzing memory dumps to uncover running processes, network connections, and injected code that might not be visible at the filesystem level.
- Online Analysis Services: VirusTotal™, Any.Run, Hybrid Analysis. These services provide automated analysis and community-shared intelligence, offering a quick overview and often revealing initial indicators of compromise (IoCs).
While free tools are powerful, investing in professional-grade solutions like IDA Pro or advanced sandboxing platforms can significantly accelerate the analysis process and uncover more sophisticated threats. For instance, an interactive disassembler like IDA Pro, coupled with its debugging capabilities, is unparalleled for deep reverse engineering tasks. If you're serious about professional malware analysis, exploring the pricing and features of these commercial tools is a necessary step. Look for educational discounts or trials if budget is a concern. The time saved and the insights gained often justify the investment.
Veredicto del Ingeniero: ¿Vale la Pena Analizar Falsos Antivirus?
Absolutely. Analyzing a deceptive executable like this fake kaspersky.exe is not just an academic exercise; it’s a crucial part of building a robust defense. These decoys serve multiple purposes for attackers:
- Bait for Credential Theft: They might trick users into entering login details for fake antivirus portals.
- Delivery Mechanism: They often act as downloaders for more sophisticated malware, such as ransomware or banking trojans.
- Evasion Tactic: By mimicking legitimate software, they can slip past less sophisticated detection methods and lower user suspicion.
- Information Gathering: Some might simply collect system information for later targeting.
Understanding how these decoys are constructed, how they behave, and what their ultimate payload is, provides invaluable intelligence. This knowledge allows security professionals to:
- Develop better detection rules (signatures, behavioral heuristics).
- Educate users on recognizing social engineering tactics.
- Strengthen endpoint security measures against common dropper techniques.
The effort invested in dissecting such samples directly translates into a more resilient security posture. It’s a proactive measure that pays dividends by anticipating and neutralizing threats before they can inflict significant damage.
Preguntas Frecuentes
What is a decoy executable in malware analysis?
A decoy executable is a malicious file designed to impersonate legitimate software, such as antivirus programs, system tools, or popular applications. Its primary goal is to trick users into executing it, thereby bypassing initial security measures and user suspicion.
Is it safe to run a suspicious file in a virtual machine?
Running a suspicious file in a properly configured, isolated virtual machine is a standard and relatively safe practice for malware analysis. However, it is critical to ensure the VM is air-gapped, lacks shared folders with the host, and that snapshots are taken before execution for easy rollback.
How can I identify if an executable is a fake antivirus?
Initial identification can involve checking file hashes against online databases like VirusTotal™, examining file properties for inconsistencies, observing its behavior in a sandbox, and looking for tell-tale signs of packing or obfuscation. However, advanced decoys are designed to be difficult to detect statically.
What are the risks associated with executing unknown files?
Executing unknown files poses significant risks, including system compromise, data theft, ransomware encryption, unauthorized access to sensitive information, and the potential for the malware to spread to other systems on the network.
El Contrato: Autopsia Digital de tu Propio Sistema
You've seen the dissection, the methodical peeling back of layers to expose the truth hidden within a deceptive file. Now, it's your turn to apply these principles. Your contract is to perform a mini-autopsy on a piece of software you suspect might be less than benign on your own system, or perhaps a legitimate piece of software whose behavior you want to understand better. Choose a program you rarely use, or perhaps a free utility downloaded from an unofficial source. Set up your sandboxed environment, take that crucial snapshot, and begin your observations. What does it write to disk? What registry keys does it touch? Does it attempt to communicate externally? Document every step, every observation. This is how you build the critical thinking skills to navigate the digital shadows. The objective is not to find malware, but to practice the methodology until it's second nature.
