The digital realm is a battlefield. Every network, every server, is a potential breach waiting to happen, a whisper of vulnerability in the constant hum of data. In this concrete jungle of ones and zeros, understanding the enemy's arsenal is paramount. Today, we're not just looking at Metasploit; we're dissecting it. This isn't a playbook for chaos, it's a deep dive into the anatomy of an exploit, seen through the eyes of a defender. Forget the beginner's allure of "taking control." We're here to understand the how, so we can build better defenses against the what if.
Is your network a fortress or a flimsy door? Can you spot the backdoor before the intruder does? This analysis will arm you with the knowledge to answer those chilling questions. We'll strip down the exploitation process, not to replicate it, but to understand its footprint, its tells, its weaknesses. Because in the end, the sharpest defense is built on a thorough understanding of the offense.
Table of Contents
- Understanding Metasploit: More Than Just an Exploit Kit
- The Offensive Pipeline: A Defensive View
- Anatomy of an Exploit Scenario
- Hunting for the Digital Ghost: Detection Strategies
- Hardening the Perimeter: Mitigation Tactics
- Verdict of the Engineer: Metasploit in the Defender's Toolkit
- Arsenal of the Analyst
- Frequently Asked Questions
- The Contract: Securing Your Network Against Exploitation
Understanding Metasploit: More Than Just an Exploit Kit
Metasploit Framework is not merely a tool; it's a sophisticated platform designed for developing, testing, and executing exploits. From a defender's perspective, it represents the codified tactics of attackers, a library of methods used to breach systems. While commonly associated with penetration testing and, unfortunately, malicious activities, its true value for cybersecurity professionals lies in its ability to simulate real-world attack vectors. Understanding its modules, payloads, and auxiliary functions is akin to studying the enemy's blueprints.
Published on April 7, 2021, this analysis delves into the core functionalities of Metasploit, framing them within the context of defensive strategy. Think of it as learning judo not to defeat someone, but to understand how to fall safely and redirect an opponent's force. We'll explore its capabilities in reconnaissance (scanning), vulnerability identification, and the art of delivering payloads – all with the ultimate goal of building more robust defenses.
The Offensive Pipeline: A Defensive View
An attacker's journey typically follows a predictable path, a pipeline of actions aimed at gaining unauthorized access. Metasploit excels at automating and streamlining several stages of this pipeline. For us, the defenders, understanding this flow is critical for implementing layered security and detection mechanisms at each step.
- Reconnaissance: This is the phase where an attacker gathers information about the target. Metasploit offers various scanning modules (e.g., port scanners, service version detection) to identify potential entry points and vulnerabilities. A defender's reaction? Proactive network enumeration, robust firewalling, and continuous vulnerability scanning of your own infrastructure.
- Exploitation: Once a vulnerability is identified, the exploitation phase begins. Metasploit houses a vast database of exploits that can be leveraged against specific software flaws. For defenders, this means timely patching, secure configuration management, and intrusion detection systems (IDS) that can spot exploit attempts based on known signatures or anomalous behavior.
- Post-Exploitation: After gaining initial access, attackers aim to maintain persistence, escalate privileges, and move laterally within the network. Metasploit's payloads and Meterpreter provide capabilities for these actions. Defense here involves principle of least privilege, network segmentation, strict access controls, and vigilant monitoring of system processes and network traffic for suspicious activities.
Ignoring these stages is like leaving the front door wide open and then being surprised when someone walks in. Each phase presents opportunities for detection and prevention.
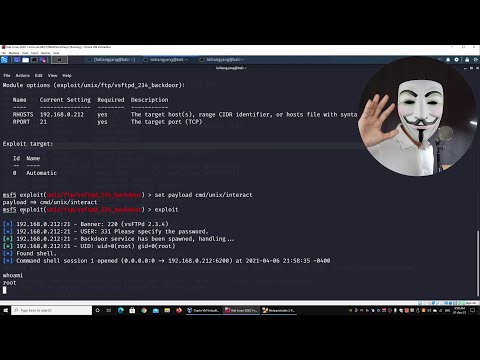
Anatomy of an Exploit Scenario
Let's dissect a hypothetical scenario. Imagine an outdated web server running a vulnerable version of a specific application. An attacker, armed with Metasploit, would first use a reconnaissance module to identify the web server and its services.
# Example command for scanning with Nmap (often integrated or used alongside Metasploit)
nmap -sV -p 80,443 target_ip_addressThis command would reveal the services running on ports 80 (HTTP) and 443 (HTTPS) and attempt to determine their versions. If, for instance, it flags a known vulnerable version of Apache Struts, the attacker would then select an appropriate exploit module from Metasploit.
msf6 > use exploit/multi/http/struts2_parsed_complex_rce
The attacker would then configure the target's IP address and port, and potentially set a payload (the code that runs on the target after successful exploitation). A common payload might be a reverse shell, allowing the attacker to interact with the compromised system.
msf6 exploit(multi/http/struts2_parsed_complex_rce) > set RHOSTS target_ip_address
msf6 exploit(multi/http/struts2_parsed_complex_rce) > set PAYLOAD windows/meterpreter/reverse_tcp
msf6 exploit(multi/http/struts2_parsed_complex_rce) > exploit
The successful execution would grant the attacker a Meterpreter session, a powerful command-and-control interface. This is where the true danger begins – privilege escalation, data exfiltration, or further lateral movement.
Hunting for the Digital Ghost: Detection Strategies
How do we spot this digital apparition before it materializes fully? Detection is not about predicting the future; it's about recognizing the patterns of compromise.
- Network Traffic Analysis: Look for unusual outbound connections from servers that shouldn't be initiating them, especially to unknown or suspicious IP addresses. Meterpreter's reverse TCP payload often establishes a connection back to the attacker's machine. Monitoring NetFlow data and SIEM alerts for anomalous traffic patterns is key.
- Log Analysis: Web server logs can reveal brute-force attempts, unusual request patterns, or queries that indicate vulnerability scanning. System logs on the target machine might show unexpected process creation, privilege escalations, or modification of critical system files. Tools like ELK Stack or Splunk are invaluable here.
- Endpoint Detection and Response (EDR): EDR solutions can monitor endpoint behavior for malicious activities, such as unauthorized process execution, suspicious file writes, or API calls associated with exploit frameworks.
- Vulnerability Management: Regularly scan your network for known vulnerabilities. While this is a preventative measure, identifying a hole that could be exploited by Metasploit serves as a critical alert.
Threat hunting is an active pursuit. You're not waiting for alerts; you're proactively searching for the subtle signs of compromise, the digital footprints left behind by tools like Metasploit.
Hardening the Perimeter: Mitigation Tactics
Prevention is always better than cure. Reducing the attack surface is the primary goal. If there's no vulnerability, there's no exploit.
- Patch Management: This cannot be stressed enough. Keep all operating systems, applications, and libraries updated to the latest stable versions. Zero-day exploits are rare; most attacks leverage known, unpatched vulnerabilities. Automate patching where feasible.
- Secure Configuration: Harden your systems. Disable unnecessary services and ports. Implement strong password policies and multi-factor authentication (MFA). For web servers, implement Web Application Firewalls (WAFs) tuned to detect and block exploit attempts.
- Network Segmentation: Divide your network into smaller, isolated segments. If one segment is compromised, the attacker's ability to move laterally to critical systems is severely restricted.
- Principle of Least Privilege: Ensure that users and services only have the minimum permissions necessary to perform their functions. This limits the damage an attacker can do if they compromise an account or process.
- Regular Audits and Penetration Testing: Conduct regular security audits and penetration tests (preferably by third parties) to identify weaknesses before attackers do. Use the findings to continuously improve your defenses.
Think of your network as a castle. Patches are reinforcing weak walls, strong passwords are guards at the gate, segmentation creates inner keeps, and least privilege ensures no single guard has access to the entire treasury.
Verdict of the Engineer: Metasploit in the Defender's Toolkit
Metasploit Framework is a double-edged sword. Its power makes it an indispensable tool for offensive security professionals conducting penetration tests and red teaming exercises. For defenders, its value lies in understanding the adversary. It allows Blue Teams to simulate attacks, test their detection capabilities, and validate their defensive strategies in a controlled environment. Using Metasploit for defensive purposes (e.g., within a dedicated lab environment for training and testing IDS/IPS rules) is highly recommended. However, deploying or experimenting with it on unauthorized systems is not only unethical but illegal. Its offensive capabilities are best understood through the lens of defense, enabling us to anticipate and counter threat actor methodologies.
Arsenal of the Analyst
To effectively analyze and defend against threats leveraging tools like Metasploit, a robust arsenal is required:
- Metasploit Framework: For understanding attack vectors and testing defenses (in a controlled lab).
- Nmap: Essential for network discovery and vulnerability scanning.
- Wireshark/tcpdump: For deep packet inspection and network traffic analysis.
- SIEM (e.g., Splunk, ELK Stack, QRadar): For centralized log management and correlation, enabling proactive threat hunting.
- EDR Solutions (e.g., CrowdStrike, Microsoft Defender for Endpoint): For real-time endpoint threat detection and response.
- Vulnerability Scanners (e.g., Nessus, Qualys): For continuous identification of system weaknesses.
- Kali Linux / Parrot Security OS: Distributions pre-loaded with a wide array of security tools, including Metasploit.
- Books: "The Hacker Playbook 3: Practical Guide To Penetration Testing" by Peter Kim, "The Web Application Hacker's Handbook" by Dafydd Stuttard and Marcus Pinto, "Red Team Field Manual (RTFM)" by Ben Clark.
- Certifications: OSCP (Offensive Security Certified Professional), CEH (Certified Ethical Hacker), CompTIA Security+. While CEH is often criticized, it provides a foundational understanding of offensive techniques. OSCP is highly regarded for its practical, hands-on approach.
Frequently Asked Questions
What is Metasploit Framework used for?
Metasploit Framework is a cybersecurity tool used for developing, testing, and executing exploit code against remote target machines. It's widely used by penetration testers to identify and exploit vulnerabilities, thus helping organizations to strengthen their security posture.
Is Metasploit legal to use?
Using Metasploit is legal only when conducted on systems and networks for which you have explicit, written permission. Unauthorized use for attacking or gaining access to systems without consent is illegal and carries severe penalties.
How can I defend against Metasploit attacks?
Defense involves a multi-layered approach: keeping systems patched and updated, secure configuration of services and networks, implementing robust intrusion detection and prevention systems, using strong access controls, and regularly conducting vulnerability assessments and penetration tests.
What is a payload in Metasploit?
A payload is the code that runs on the target system after an exploit has been successfully executed. It defines what the attacker can do on the compromised system, such as opening a command shell, uploading files, or maintaining persistent access.
The Contract: Securing Your Network Against Exploitation
The digital shadows are long, and tools like Metasploit are the lanterns illuminating potential paths for intrusion. You've seen the mechanics, the steps an attacker might take. Now, the real work begins. Your contract is to transform this knowledge into action. Map your network. Identify your crown jewels. Then, implement the defenses we've discussed. Patch relentlessly. Monitor everything. Segment aggressively. Don't wait for an alert; hunt for the anomaly. Are your current defenses enough to withstand a targeted assault using known exploits? Prove it. Document your findings, your remediation efforts, and share the lessons learned – responsibly. The war for the perimeter is constant; complacency is the ultimate vulnerability.
