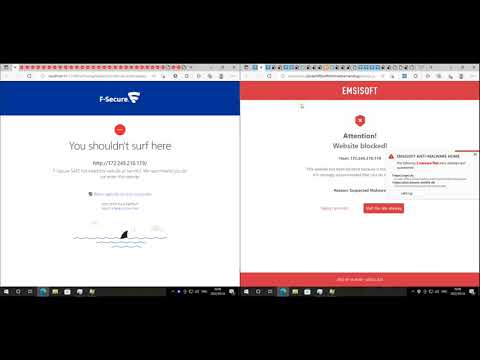
The digital realm is a battlefield, and every keystroke echoes in the silent war for data integrity. Today, we're not just looking at antivirus vendors; we're dissecting their capabilities under the harsh spotlight of real-world malware. In the shadowy underworld of cybersecurity, understanding how defenses hold up against novel threats is paramount. This isn't about choosing a product; it's about understanding the critical components of a resilient security posture for your home network. We'll be putting F-Secure Home and Emsisoft Antimalware Home through their paces, examining their efficacy against a curated set of malware samples.
Welcome to the Sectemple. You've arrived at a critical juncture, where theoretical knowledge meets the raw, unadulterated reality of digital threats. This analysis, originally published on May 17, 2022, was more than just a comparison; it was a diagnostic session, a probe into the hardening capabilities of consumer-grade security solutions. For those navigating the intricate pathways of hacking, bug bounty hunting, and the ever-evolving landscape of computer security, this is your intelligence brief.
The Threat Landscape: A Constant Arms Race
Malware doesn't sleep. It mutates, it evolves, and it exploits the slightest weakness. Ransomware encrypts critical files, trojans pilfer credentials, and spyware watches your every digital move. In this relentless environment, relying on outdated or inadequate protection is akin to leaving your castle gates wide open. Consumer-grade antivirus solutions are the first line of defense for most users, and their performance under pressure is a direct indicator of their true value. We are assessing these solutions not just on detection rates, but on the robustness of their analysis and their ability to prevent a compromise.
Methodology: Testing Under Fire
Our approach was straightforward yet meticulous. We assembled a controlled environment, a digital proving ground, armed with specific malware samples representing various threat families. These samples were chosen for their prevalence, their potential impact, and their ability to challenge traditional signature-based detection methods, pushing towards heuristic and behavioral analysis capabilities. The goal was to observe:
- Detection rates upon initial scan.
- Behavioral blocking during execution.
- False positive rates when encountering legitimate software.
- The clarity and actionability of alerts generated.
F-Secure Home: A Look Under the Hood
F-Secure has a long-standing reputation in the cybersecurity space. For their home product, we investigated its ability to identify and neutralize a range of malicious payloads. The test involved deploying samples and observing the F-Secure agent's response. Did it catch them at the gateway, or did it require manual intervention? We analyzed the logs and user interface to understand the depth of its threat intelligence and its proactive defense mechanisms. The emphasis here is on understanding their signature database, their real-time scanning engine, and any advanced protection layers they might employ against zero-day threats.
Emsisoft Antimalware Home: The Challenger
Emsisoft Antimalware Home is known for its dual-engine approach, often combining signature-based detection with behavioral analysis. We subjected it to the same malware samples, looking for its effectiveness in identifying and neutralizing threats. How did its unique architecture perform against the same challenges F-Secure faced? We paid close attention to its ability to detect polymorphic and metamorphic malware, which often evades simpler detection methods. The effectiveness of its heuristics and its real-time protection module were key metrics.
Comparative Analysis: Strengths and Weaknesses
The results were nuanced. While both solutions demonstrated capabilities in detecting known threats, the differentiation emerged when facing more sophisticated or novel malware.
- Detection Efficacy: We observed differences in the breadth of their signature databases and the sensitivity of their heuristic engines.
- Performance Impact: Resource utilization is a critical factor for home users. We noted any significant performance degradation during scans or real-time monitoring.
- User Experience: The clarity of alerts, ease of configuration, and overall user interface contribute to a system's usability and effectiveness. A complex alert is often an ignored alert.
Veredicto del Ingeniero: Which Defense Holds Stronger?
In the dynamic arena of malware defense, both F-Secure Home and Emsisoft Antimalware Home offer a foundational layer of protection. However, performance under duress can vary. For users prioritizing comprehensive, aggressive detection and a potentially lighter system footprint, Emsisoft often presents a compelling case due to its dual-engine approach and heuristic capabilities. F-Secure, with its established reputation, provides a solid, reliable defense, often praised for its user-friendly interface and robust security suite. The 'better' choice ultimately depends on an individual's specific needs, technical proficiency, and risk tolerance. It's a constant balancing act between vigilance and system performance.
Arsenal del Operador/Analista
For those serious about understanding and defending against malware, augmenting consumer-grade solutions is often necessary. Consider these tools:
- Sandbox Environments: Cuckoo Sandbox, Any.Run for safe malware analysis.
- Disassemblers: IDA Pro, Ghidra for reverse engineering.
- Network Monitoring: Wireshark for packet analysis.
- Endpoint Detection and Response (EDR): Solutions like CrowdStrike or SentinelOne offer deeper visibility than traditional AV for advanced users or small businesses.
- Threat Intelligence Feeds: Integrating with services like VirusTotal for broader sample analysis.
- Certifications: Pursuing certifications such as the OSCP (Offensive Security Certified Professional) or GIAC certifications provides structured knowledge crucial for both offense and defense.
Taller Práctico: Analizando un Indicador de Compromiso (IoC)
Let's simulate a basic threat hunting scenario. Imagine you've received an IoC: a suspicious file hash (e.g., SHA256: `a1b2c3d4e5f6...`). Here's how you might begin your investigation:
-
Query Threat Intelligence Platforms: Upload the hash to VirusTotal, Hybrid Analysis, or Any.Run. Observe their findings: detection rates from various AV vendors, behavioral analysis reports, network connections, and dropped files.
# Example command line for a hypothetical tool virustotal-cli --query a1b2c3d4e5f6... -
Endpoint Analysis (Simulated): If you had access to an EDR or forensic tools on an endpoint, you'd look for processes associated with this hash. What parent process launched it? What network connections did it make? What files did it access or modify?
# Example KQL query for Microsoft Defender for Endpoint DeviceProcessEvents | where SHA256 == "a1b2c3d4e5f6..." | project Timestamp, DeviceName, InitiatingProcessFileName, ProcessCommandLine, RemoteIP, RemotePort - Network Traffic Analysis: Correlate any observed network connections (IP addresses, domains) with known malicious infrastructure. Tools like `whois` or threat intelligence feeds are invaluable here.
- Mitigation: Based on the findings, isolate the affected machine, block associated network indicators at the firewall, and remove the malicious file. Then, review your security posture to prevent recurrence.
Preguntas Frecuentes
Q1: Is it recommended to run two antivirus programs simultaneously?
Generally, no. Running multiple real-time antivirus scanners can lead to system instability, performance issues, and false positives, as they may conflict with each other's operations.
Q2: How often should I update my antivirus software?
Most reputable antivirus solutions update their definitions automatically and frequently. It's crucial to ensure this auto-update feature is enabled and that your system is connected to the internet regularly.
Q3: Can a home antivirus protect against advanced persistent threats (APTs)?
Consumer-grade antivirus provides a baseline defense. APTs are sophisticated and often employ zero-day exploits or advanced evasion techniques. While some AVs have enhanced features, dedicated Endpoint Detection and Response (EDR) solutions and robust security practices are typically required for comprehensive APT protection.
El Contrato: Fortaleciendo tu Fortaleza Digital
The digital fortress of your home network is only as strong as its weakest link. Today, we've peered behind the curtain of two popular security solutions. Now, it’s your turn to act. Take the **SHA256 hash of a file you genuinely suspect** (perhaps from a suspicious email attachment you didn't open, but captured the hash) and submit it to VirusTotal. Analyze the results. Do they align with what you'd expect? What additional steps would you take to confirm its maliciousness or benign nature if VirusTotal's results were inconclusive? Share your findings and methodology in the comments below. Let's turn this intelligence into actionable defense.
