The hum of the servers was a low thrum beneath the stark fluorescent lights. A new client. Their infrastructure, a sprawling mess of virtualized components and, of course, containers. "Docker," they’d said, with a mix of pride and blind faith. My job? To strip away the illusions and reveal the cracks. Today, we dissect Docker security, not with a scalpel, but with the blunt force of an auditor. We're here to establish a baseline, to see how their precious containers stack up against a determined adversary. Forget the glossy marketing; we're looking for the ghosts in the machine.
Table of Contents
- Introduction
- What We Will Be Covering
- Understanding the Docker Platform
- Containers vs. Hypervisors
- Docker Architecture Deep Dive
- What Needs to Be Secured?
- Essential Auditing Tools
- Practical Demonstration: Putting Tools to Work
- Additional Resources & Next Steps
- Frequently Asked Questions
- The Contract: Your Docker Hardening Blueprint
Introduction
In the high-stakes game of modern infrastructure, containerization has become a double-edged sword. Docker, a leading platform, offers unparalleled agility and efficiency, but this very power can become a critical vulnerability if not managed meticulously. This post isn't about theoretical security; it's a gritty, hands-on guide to auditing your Docker environment. We’ll equip you with the knowledge and tools to move beyond assumptions and establish a concrete security posture.
What We Will Be Covering
Our objective is clear: to audit the security of the Docker platform. This involves moving beyond basic setup and diving into the intricacies of its architecture, understanding where potential attack vectors lie, and deploying tools to establish a robust security benchmark. We'll demystify concepts, explore critical components, and, most importantly, show you how to practically assess and improve your container security.
Understanding the Docker Platform
Before you can secure it, you must understand it. Docker abstracts away the complexities of the underlying operating system, allowing applications and their dependencies to be packaged and run in isolated environments called containers. This abstraction is powerful, but it also means that misconfigurations at the Docker daemon level, within the container runtime, or in the images themselves, can have far-reaching consequences. Understanding the lifecycle of a container—from image creation to runtime execution and eventual termination—is paramount for effective auditing.
Containers Vs. Hypervisors
It’s a common misconception to equate containers with virtual machines. They are fundamentally different. Hypervisors create hardware-level virtualization, running a full guest operating system on top of a host OS. Containers, on the other hand, share the host OS kernel. This makes them lighter and faster, but also means they have a smaller isolation boundary. A kernel exploit on the host can compromise all containers running on it, a risk not present with traditional VMs. Understanding this difference is crucial when assessing the threat model and security requirements for your deployment. For true isolation, especially in multi-tenant or high-security environments, a hypervisor-based approach might still be necessary, or a carefully configured container runtime must be employed. Investing in advanced container orchestration platforms that offer enhanced isolation features, like Kubernetes with security contexts and network policies, becomes a strategic decision here. Even then, a robust auditing process remains non-negotiable.
Docker Architecture Deep Dive
The Docker architecture involves several key components that are ripe for security scrutiny: the Docker Daemon (dockerd), the Docker CLI, Docker Images, and Docker Containers. The Daemon, running as a background process, is the heart of Docker, managing images, containers, networks, and volumes. Its configuration is critical; overly permissive settings can allow unauthorized access or privilege escalation. Docker images are built from Dockerfiles, and any vulnerability within the base image or added packages becomes a persistent threat. Containers are ephemeral instances of these images. Understanding how these components interact, how data flows, and what privileges are granted at each level is the bedrock of a successful security audit.
"Security is not a product, but a process." - Bruce Schneier
What Needs to Be Secured?
The attack surface in a Docker environment is multi-faceted:
- Docker Daemon: Configuration files, network exposure, access controls.
- Docker Host: The underlying operating system must be hardened.
- Docker Images: Vulnerabilities in base images, application dependencies.
- Container Runtime: Execution privileges, resource limits, security profiles (AppArmor, SELinux).
- Network Configuration: Container-to-container communication, external exposure.
- Secrets Management: How sensitive data is handled and injected into containers.
- User Access & Permissions: Who can interact with Docker and what they can do.
Essential Auditing Tools
Fortunately, the security community has developed powerful tools to help us navigate this complexity. For serious auditing, relying solely on manual checks is a recipe for disaster. Investing in professional tools like Burp Suite Pro for web application scanning within containers, or comprehensive vulnerability scanners, can save you from missing critical flaws. For Docker itself, several open-source tools are indispensable:
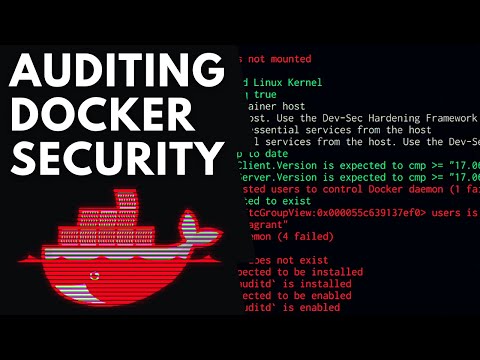
- Docker Bench for Security: This script checks for adherence to the CIS Docker Benchmark, providing automated compliance checks. It's the first step in understanding your compliance status.
- InSpec: Developed by Chef, InSpec is a powerful, open-source framework for **test automation, compliance, and security** validation. It allows you to define security and compliance rules in code.
- Clair: An open-source static analysis tool for the vulnerability, with the goal of helping you manage the security risks of your containers.
- Dive: A tool for exploring a Docker image, layer by layer, to help you understand how it's built and identify potential optimizations or security risks.
For teams serious about DevSecOps and continuous security monitoring, consider integrating these into your CI/CD pipeline. Platforms like Tenable.io or Aqua Security offer commercial-grade solutions that provide deeper insights and automation. Understanding and implementing these tools isn't optional for a professional; it's part of the essential toolkit, akin to having a reliable SIEM system in a traditional SOC.
Practical Demonstration: Putting Tools to Work
Let's get our hands dirty.
- Install Docker: Ensure you have Docker installed and running on your test system. For serious security work, consider a dedicated testing environment or Virtual Machines.
- Clone Docker Bench for Security:
git clone https://github.com/docker/docker-bench-security.git cd docker-bench-security - Run Docker Bench: Execute the script to perform an initial audit.
This command runs the benchmark against the CIS Docker Benchmark standard. Pay close attention to the "FAIL" and "WARN" findings. These are your immediate red flags.sudo sh docker-bench-security.sh -c cisdogtaskfile - Explore with Dive: Let's say you have an image named `my-app:latest`. Use dive to inspect it:
This will open an interactive interface where you can browse layers, see modified files, and analyze image efficiency. Look for obscure files, unnecessary binaries, or sensitive information left within layers.dive my-app:latest - InSpec for Compliance: For more complex compliance checks or custom rules, InSpec is your weapon. You'd typically write InSpec profiles defining your desired security state. For Docker, there are community profiles available. For instance, to run a profile against your Docker daemon:
This requires the InSpec CLI to be installed and configured. The output will detail compliance against predefined controls.inspec exec docker --chef-license accept
Additional Resources & Next Steps
Navigating the labyrinth of container security is an ongoing process. The resources below are crucial for expanding your knowledge and hardening your infrastructure:
- Docker Security Essentials eBook: While not a substitute for hands-on experience, this eBook provides a foundational understanding. [Link: https://bit.ly/3j9qRs8]
- Docker Bench for Security: The official GitHub repository. [Link: https://ift.tt/1eDUM8N]
- InSpec: Explore the power of InSpec for compliance as code. [Link: https://ift.tt/31liBjf]
- Docker CIS Benchmark: The industry standard for Docker security configuration. [Link: https://ift.tt/3okm9f3]
- Part 2 of the Docker Security Series: For a deeper dive into specific advanced topics, registering for the next installment is recommended. [Link: https://bit.ly/3eziZi6]
- Linode Credit: For setting up secure cloud environments, explore Linode. [Link: https://bit.ly/2VMM0Ab]
For those aiming for professional recognition, certifications like the Certified Kubernetes Administrator (CKA) or specialized cloud security certifications often have modules dedicated to container security best practices. Consider investing in quality training from platforms that offer hands-on labs.
Frequently Asked Questions
Q1: How often should I audit my Docker environment?
A: For production systems, a comprehensive audit should be performed at least quarterly, or more frequently after significant changes, new deployments, or in response to emerging threats. Continuous monitoring tools can supplement periodic deep dives.
Q2: Can I run Docker Bench on a production Docker host?
A: Yes, Docker Bench for Security is designed to be run on a live Docker host. However, it's always recommended to test in a staging environment first and be aware of any potential impact, though it's generally non-intrusive.
Q3: What's the difference between auditing images and auditing the Docker daemon?
A: Auditing images focuses on the security of the container's filesystem, dependencies, and build processes. Auditing the daemon focuses on the security of the Docker engine itself—its configuration, network settings, and access controls. Both are critical.
Q4: Are there any paid tools that significantly improve Docker security auditing?
A: Yes. Commercial solutions from vendors like Twistlock (Palo Alto Networks), Aqua Security, or Sysdig provide advanced runtime security, vulnerability management, and compliance monitoring specifically for containerized environments, often integrating with orchestration platforms.
The Contract: Your Docker Hardening Blueprint
The audit is complete. The findings are stark. Now, the real work begins. Your contract is to translate these findings into actionable hardening steps. This isn't optional; it's the price of doing business in the digital frontier. For every 'FAIL' or 'WARN' identified by Docker Bench or InSpec, you must implement a remediation. This might involve updating base images, restricting daemon privileges, implementing network segmentation with Docker networks or Kubernetes Network Policies, or configuring mandatory access control systems like SELinux or AppArmor more strictly. Document every change. Automate where possible. Make security not an afterthought, but a core component of your development and deployment lifecycle. Your challenge: Create a prioritized roadmap of at least five hardening steps based on the common findings of security audits like the CIS Docker Benchmark. Your life, and the integrity of your data, may depend on it.
We hope you found value in this deep dive. Your feedback fuels our analysis. If you have questions or want to challenge our findings, the comments section is open. Let's engage; the digital shadows are vast, and only by sharing knowledge can we navigate them effectively.
