The flickering neon sign of a server rack cast long shadows across the cramped room, each blink a silent testament to the relentless digital tide. In this temple of code and consequence, we don't just patch systems; we dissect them. We hunt the digital phantoms, the anomalies whispered in logs that signal not a malfunction, but an infiltration. Today, we’re not talking about exploits, about the keys to the kingdom. We're talking about the silent war waged in the shadows, the hunt for threats that have already breached the outer walls. This is the cold, hard reality of threat hunting, where intuition meets data, and knowledge is your only weapon.
This article is not a mere tutorial; it's a strategic briefing, lifted directly from the advanced modules of the Sectemple Threat Hunter Certification. We’ll dissect the methodologies that separate the vigilant from the vulnerable, transforming raw data into actionable intelligence. Forget the noise of the news cycles; here, we focus on the fundamental principles that make a professional Threat Hunter indispensable. Gain the insight, and perhaps, the certificate, that will elevate your standing in this high-stakes game.
Table of Contents
- The Hunt Begins: Setting the Stage
- Hypothesis-Driven Hunting: The Strategist's Gambit
- Indicator of Compromise (IoC) Hunting: Chasing Digital Footprints
- Anomaly Detection Hunting: The Art of Spotting the Outlier
- Threat Intelligence-Driven Hunting: Riding the Wave of Known Threats
- Threat Hunting Methodology in Action: A Case Study
- Engineer's Verdict: Is Threat Hunting Worth the Investment?
- The Operator's Arsenal: Essential Tools for the Hunt
- Defensive Workshop: Crafting Detection Rules
- Frequently Asked Questions
- The Contract: Your First Threat Hunt Simulation
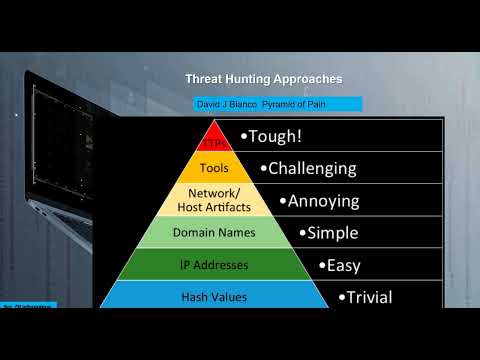
The Hunt Begins: Setting the Stage
In the labyrinthine architecture of modern networks, threats don't always announce their arrival with sirens. They creep, they hide, they adapt. Threat hunting is the proactive, human-driven process of searching for and identifying malicious activity that has bypassed automated security defenses. It's not about waiting for alerts; it's about actively seeking out the unseen. It's the detective work of cybersecurity, where every log entry, every network packet, every process execution is a potential clue in a larger, more sinister narrative.
Hypothesis-Driven Hunting: The Strategist's Gambit
The most effective threat hunts are not random wanderings; they are carefully constructed investigations. Hypothesis-driven hunting begins with a specific, testable assumption about potential malicious activity. This isn't just a guess; it's an educated hypothesis, informed by threat intelligence, knowledge of attacker tactics, techniques, and procedures (TTPs), or an understanding of your own network's baseline behavior.
Example Hypotheses:
- "An external attacker is attempting to exfiltrate sensitive data via an encrypted channel using a novel command-and-control (C2) C2 protocol."
- "A compromised internal host is performing lateral movement using stolen credentials via RDP or SMB."
- "Malware is leveraging DNS tunneling to communicate with its operators, bypassing traditional firewall rules."
The process then involves gathering data relevant to validate or invalidate the hypothesis, looking for specific indicators or deviations from the norm. This structured approach ensures that the hunt is focused, efficient, and yields meaningful results.
"The first step in solving any problem is recognizing there is one. In cybersecurity, many are blind to the shadows until it's too late." - cha0smagick
Indicator of Compromise (IoC) Hunting: Chasing Digital Footprints
IoCs are the digital breadcrumbs left behind by attackers. These can include suspicious IP addresses, domain names, file hashes, registry keys, or specific network traffic patterns. IoC hunting involves systematically searching your environment for these known indicators.
Methodology:
- Acquire IoCs: Obtain lists of known malicious IoCs from trusted threat intelligence feeds, security advisories, or incident response reports.
- Data Collection: Query your security telemetry (logs, network traffic, endpoint data) for the presence of these IoCs.
- Analysis: Investigate any matches. A single IoC match doesn't always mean compromise, but it warrants immediate deeper investigation. Correlation with other events is key.
- Action: If a compromise is confirmed, initiate incident response procedures.
While effective against known threats, IoC hunting can be less effective against novel or sophisticated attacks that avoid leaving easily recognizable traces. This is where other hunting techniques become critical.
Anomaly Detection Hunting: The Art of Spotting the Outlier
This approach focuses on identifying deviations from established baseline behavior within your network. It requires a deep understanding of what "normal" looks like for your systems and users. Anomalies can manifest in various forms:
- Unusual login times or locations.
- Abnormal network traffic volumes or destinations.
- Unexpected process executions or system configurations.
- Unusual data access patterns.
Tools like Security Information and Event Management (SIEM) systems, User and Entity Behavior Analytics (UEBA), and statistical analysis algorithms are often employed here. The challenge lies in distinguishing true malicious anomalies from benign outliers caused by legitimate system changes or user activities. Mature security environments with robust logging and baselining capabilities are best positioned for this type of hunting.
Threat Intelligence-Driven Hunting: Riding the Wave of Known Threats
Leveraging threat intelligence feeds is a cornerstone of modern threat hunting. This intelligence often details new TTPs, malware families, and active threat actor campaigns. Threat hunters use this information to:
- Develop Targeted Queries: Create specific searches based on intelligence about how certain threat actors operate. For example, if intelligence suggests a new ransomware family uses a specific file encryption routine, hunters can search for processes exhibiting that behavior.
- Identify Emerging Threats: Proactively search for signs of new, sophisticated threats before they are widely reported.
- Understand Attacker Motivations: Align hunting efforts with potential attacker goals, focusing on high-value assets or sensitive data.
This method allows hunters to be ahead of the curve, anticipating potential attacks rather than just reacting to them.
Threat Hunting Methodology in Action: A Case Study
Consider a scenario where threat intelligence indicates a specific APT group is using PowerShell for initial reconnaissance and lateral movement. A threat hunter might formulate the hypothesis: "The APT group [X] is exploring our network using PowerShell. We need to find evidence of suspicious PowerShell activity."
Steps:
-
Data Source: Endpoint Detection and Response (EDR) logs capturing PowerShell script block logging, command-line arguments, and process creation events.
# Example KQL query for suspicious PowerShell execution PowerShellExecution | where ScriptBlockLog !contains "Get-NetUser" and ScriptBlockLog !contains "Get-NetComputer" and ScriptBlockLog !contains "Invoke-Command" | where CommandLine contains "-EncodedCommand" or CommandLine contains "-enc" | project TimeGenerated, ComputerName, AccountName, ProcessName, CommandLine, ScriptBlockLog | sort by TimeGenerated desc - Analysis: Look for patterns indicative of reconnaissance: common PowerShell cmdlets used for enumerating users, groups, network shares, or domain information. Look for encoded commands, which are often used to obfuscate malicious scripts. Analyze the parent process of PowerShell; a connection to an unusual application could signal a compromised entry point.
- Validation: If suspicious activity is found, correlate it with other data sources like network logs to identify C2 communication or further endpoint events. For example, if PowerShell launched a process to download a file from an untrusted external IP, that's a strong indicator.
- Mitigation: If compromise is confirmed, isolate the affected systems, analyze the full extent of the breach, and implement stronger detection rules based on the observed TTPs. This might include creating specific Yara rules for identified scripts or updating EDR policies to flag specific PowerShell command patterns.
This methodical approach, combining intelligence, hypothesis, specific data, and careful analysis, is the essence of effective threat hunting.
Engineer's Verdict: Is Threat Hunting Worth the Investment?
Threat hunting is not a luxury; it's a necessity in today's threat landscape. While it requires skilled personnel and robust tooling, the cost of a successful breach — financial, reputational, and operational — far outweighs the investment. It transforms security posture from *reactive* to *proactive*, significantly reducing dwell time and the potential impact of intrusions. For organizations serious about resilience, threat hunting is non-negotiable.
The Operator's Arsenal: Essential Tools for the Hunt
A hunter is only as good as their tools. While creativity and expertise are paramount, the right technology amplifies a threat hunter's capabilities. Consider these essentials:
- Endpoint Detection and Response (EDR) Platforms: CrowdStrike Falcon, SentinelOne, Microsoft Defender for Endpoint.
- SIEM Systems: Splunk Enterprise Security, IBM QRadar, ELK Stack (Elasticsearch, Logstash, Kibana).
- Network Traffic Analysis (NTA) Tools: Zeek (formerly Bro), Suricata, Wireshark.
- Threat Intelligence Platforms (TIPs): Anomali ThreatStream, Recorded Future.
- Forensic Tools: Volatility Framework, Autopsy.
- Scripting Languages: Python (for automating tasks and analysis), KQL (for Azure Sentinel), Splunk SPL.
- Books: "The Practice of Network Security Monitoring" by Richard Bejtlich, "Threat Hunting: A Practical Guide" by Kyle Rainville.
- Certifications: GIAC Certified Incident Handler (GCIH), Certified Threat Intelligence Analyst (CTIA), Offensive Security Certified Professional (OSCP) - while offensive, the methodology is key.
Defensive Workshop: Crafting Detection Rules
The output of a threat hunt is not just identifying an intrusion but also hardening the defenses against future attacks. A crucial outcome is the creation or refinement of detection rules. Here’s a basic example of crafting a rule to detect suspicious PowerShell usage, often abused for lateral movement:
- Identify Suspicious Indicators: Based on observed activity, we might look for PowerShell executions with encoded commands (`-EncodedCommand` or `-enc`) launched by unusual parent processes (e.g., not `explorer.exe` or `powershell.exe` itself).
- Formulate Rule Logic: In a SIEM like Splunk or Azure Sentinel, this translates to a query. For example, in Splunk SPL:
index=wineventlog EventCode=4688 ParentProcessName!=*\\explorer.exe ParentProcessName!=*\\powershell.exe CommandLine="*-EncodedCommand*" OR CommandLine="*-enc*" | stats count by ComputerName, User, CommandLine, ParentProcessName, _time | where count > 0 - Test and Tune: Deploy the rule in a monitoring or detection-only mode first to assess its false positive rate. Tune it to reduce noise while retaining efficacy.
- Deploy and Alert: Once tuned, enable active alerting for security operations center (SOC) analysts.
This proactive loop of hunting, discovering, and defending is what makes a security program resilient.
Frequently Asked Questions
What is the difference between threat hunting and incident response?
Incident response is about reacting to and managing a confirmed breach. Threat hunting is proactive, seeking out breaches that have *not yet* been detected by automated systems.
How much time should be dedicated to threat hunting?
Ideally, threat hunting should be a continuous activity. In practice, organizations dedicate specific teams or allocate a percentage of security analysts' time (e.g., 10-20%) to proactive hunting.
What are the key skills for a threat hunter?
Strong analytical and critical thinking skills, deep understanding of operating systems, networks, and attacker TTPs, proficiency in scripting languages and data analysis tools, and excellent communication skills.
Can threat hunting be fully automated?
No. While automation is crucial for data collection and analysis, the human element of hypothesis generation, contextual understanding, and creative investigation is irreplaceable in effective threat hunting.
The Contract: Your First Threat Hunt Simulation
Your mission, should you choose to accept it, is to analyze publicly available network traffic data (e.g., from a CTF challenge like UNKNOWN-ATTACKER or a Wireshark sample from malware analysis. If unavailable, simulate your own baseline traffic and introduce a simulated anomaly). Formulate a hypothesis about potential malicious activity. Use Wireshark or a similar tool to search for one specific indicator of compromise (e.g., a known malicious IP address, a suspicious DNS query pattern, or unusual port usage). Document your hypothesis, the IoC you searched for, the steps you took, and your findings. The goal is not necessarily to find a real threat, but to practice the structured approach.
Now, over to you. What are your go-to hypotheses when starting a hunt? Share your strategies and any tools you find indispensable in the comments below. Let's build a better defense, together.

No comments:
Post a Comment