The flickering monitor cast long shadows across the dimly lit room. Outside, the city slept, oblivious to the digital skirmishes unfolding in the underbelly of the network. Tonight, the target wasn't a corporate fortress or a government server. Tonight, we were going inside the lion's den – a scammer's call center. Not just disrupting their operation, but witnessing it firsthand. The webcam, a seemingly innocent portal, becomes the window into their world. This is not just about a prank; it's a tactical maneuver to reveal the infrastructure and the individuals behind widespread digital deceit.
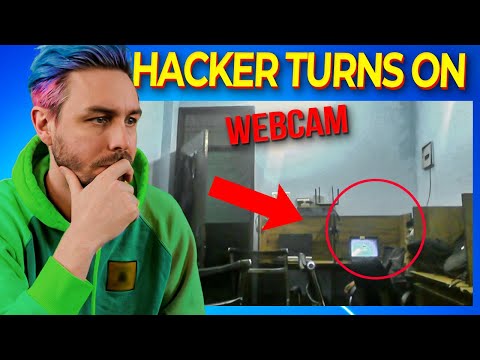
The digital landscape is a battlefield, and misinformation is a weapon. Scam operations thrive in the shadows, preying on the unsuspecting. But even the most elaborate schemes leave digital footprints. Our objective tonight is not merely to disrupt, but to understand the operational methodology of these fraudulent entities. By gaining access to their core operational hub – a call center – we can peel back the layers of deception and expose the mechanics of their trade.
The Digital Infiltration: Gaining the Foothold
The initial phase of engagement involves identifying vulnerabilities within the target's digital infrastructure. In the context of a scammer call center, this often means exploiting the very tools they use to conduct their operations. This could range from unpatched operating systems and weak network configurations to phishing attacks targeting their lower-tier operatives. The goal is to establish a persistent presence, a digital ghost in their machine, before moving to more impactful actions.
Consider the common tools these operations might employ: VoIP systems, CRM software, possibly even remote access tools hastily deployed for managing their workforce. Each of these is a potential entry point. A well-crafted phishing email, masquerading as an internal memo or a system update, can be the key to unlocking their network. Once inside, the objective is reconnaissance – mapping the network, identifying key assets, and locating the sensitive data or access points that will allow for webcam activation.
Operational Reconnaissance: Mapping the Enemy's Territory
With an established foothold, the next critical step is reconnaissance. This is where the attacker truly begins to think like a defender, anticipating the enemy's moves and understanding their environment. For a scam operation, this means identifying:
- Network Topology: How are their systems interconnected? Are they using a centralized server or a distributed network?
- Key Personnel: Who are the individuals managing the operation? Are there technical staff, supervisors, or just operatives?
- Communication Channels: How do they communicate internally and with their targets?
- Hardware and Software: What specific types of computers, cameras, and software are in use?
This phase is crucial. The more information gathered, the more precise and devastating the subsequent actions can be. It's about understanding not just the technical vulnerabilities, but the human element as well. Knowing their routines, their communication patterns, and even the names they use can be invaluable.
Command and Control: Activating the Eyes
The ultimate objective in this scenario is to gain visual access to the scammers' environment. This is achieved through the activation of their webcams. Once a system with webcam access is compromised, and depending on the operating system and installed software, various methods can be employed. This often involves leveraging built-in operating system functionalities or using specialized tools that can interface with the camera hardware.
The technical execution can involve:
- Remote Command Execution: Using tools like PowerShell on Windows or Bash scripting on Linux to trigger camera access.
- Leveraging Existing Software: If the scammers are using remote monitoring or collaboration software, exploiting its features to activate cameras.
- Driver Manipulation: In more sophisticated attacks, directly interacting with the camera's drivers to force activation.
Seeing the faces behind the scams adds a powerful human element to the exposure. It shifts the narrative from abstract digital fraud to tangible individuals perpetrating these crimes. It's a form of digital justice, bringing the perpetrators into the light.
The Fallout: Exposing the Operation
Once visual confirmation is established, the process shifts to documentation and exposure. This footage serves as irrefutable evidence of their operations. The goal is to compile a comprehensive report, often in video format, that details every aspect of the scammer's setup:
- The Environment: The physical space, the number of workstations, the general atmosphere of the call center.
- The Operatives: Their interactions, their scripts, their reactions when confronted.
- The Technology: The specific software and hardware they are using, including potentially sensitive configuration details.
This exposure serves multiple purposes. Firstly, it acts as a deterrent, showing potential scammers that their operations are not as secure as they believe. Secondly, it educates the public about the realities of these scams, helping them to better identify and avoid falling victim. Finally, it can aid law enforcement agencies by providing direct intelligence on criminal organizations operating globally.
Case Study: Beyond the Webcam
The act of turning on a scammer's webcam is more than just a technical feat; it's a part of a larger strategy of disrupting and dismantling criminal enterprises. This approach often involves collaboration with other security researchers and content creators, pooling resources and expertise to achieve a greater impact. Expeditions into the heart of scam operations have revealed a wide spectrum of fraudulent activities, from fake tech support scams targeting the elderly to impersonation schemes designed to steal financial information.
We've seen operations pretending to be major tech companies like Amazon, Apple, Microsoft, and Norton. We've witnessed the deletion of critical files, the use of syskey tools to lock down systems, and the implementation of sophisticated social engineering tactics tailored to specific demographics and languages, including Hindi, Urdu, and others originating from the Indian subcontinent. These operations are not amateur hour; they are organized criminal enterprises requiring a coordinated, multi-faceted response.
Arsenal of the Operator/Analyst
To conduct operations of this nature, a specific set of tools and knowledge is indispensable. While the techniques can vary, a foundational understanding of network penetration, social engineering, and digital forensics is paramount. For those looking to delve deeper into understanding and mitigating such threats, the following resources are invaluable:
- Penetration Testing Tools: Kali Linux distribution, Metasploit Framework, Burp Suite Professional (essential for web application analysis), Nmap for network scanning.
- Programming Languages: Python for scripting and automation (e.g., interacting with APIs, data analysis), Bash for system administration and shell scripting.
- Collaboration Platforms: Discord servers and private forums where security researchers share intelligence and coordinate efforts.
- Content Platforms: YouTube channels like those of Jim Browning and Mark Rober, and platforms like Twitch for live analysis and community engagement.
- Learning Resources: Certifications such as the OSCP (Offensive Security Certified Professional) for practical penetration testing skills, and books like "The Web Application Hacker's Handbook" for in-depth knowledge.
Understanding the tools of engagement is as critical as understanding the mindset of the adversary. This knowledge empowers both offensive and defensive strategies.
FAQ
What legal considerations are there when accessing a scammer's system?
While the primary intent is to disrupt criminal activity, unauthorized access to any system, even a scammer's, can have legal repercussions. Operations like these are typically conducted with a strong focus on evidence gathering for potential law enforcement referral, and often involve collaboration with individuals who understand the legal boundaries. Extreme care is taken to ensure actions are justifiable and ethically sound.
How do these operations typically identify their targets?
Scammers often acquire victim data through various means, including data breaches, phishing campaigns, and the purchase of compromised personal information on the dark web. Our targets, in this case, are the scammers themselves. Identifying their operational infrastructure can involve tracing their communication channels, analyzing their online presence, and sometimes, through direct engagement and social engineering.
What is the primary goal of exposing these scammer call centers?
The primary goals are multi-fold: to disrupt ongoing criminal operations, to gather evidence for potential prosecution, to educate the public about the methods scammers use, and to deter future criminal activity by demonstrating that these operations are not untraceable.
Are these operations always successful in activating webcams?
Success depends heavily on the technical sophistication of the scam operation and the vulnerability of their systems. Some operations employ robust security measures, while others are surprisingly lax. The success rate varies, but the continuous effort is to refine techniques and adapt to evolving defensive measures.
Can this method be applied to other types of cybercrime?
The principles of identifying vulnerabilities, gaining access, and conducting reconnaissance are fundamental to all forms of offensive security and threat intelligence gathering. While webcam activation is specific to certain scenarios, the underlying methodology can be adapted to investigate a wide range of cybercrimes, from botnet operations to financial fraud schemes.
The Contract: Bringing the Shadows to Light
The digital realm is fraught with hidden threats. By turning the tables on those who seek to exploit others, we not only disrupt immediate harm but also illuminate the dark corners of cybercrime for all to see. The activation of a scammer's webcam is a symbolic act, bringing the hidden faces of deception into the unforgiving glare of public scrutiny. It’s a reminder that every digital action has a consequence, and sometimes, those consequences are brought directly to their doorstep.
Now, it's your turn. What are the most effective, ethical, and technically sound methods you've encountered or devised for disrupting illicit online operations? Share your insights, tools, and methodologies below. Let this serve as a testament to the power of collective knowledge in combating digital malfeasance.
<h1>Exposing Scam Operations: A Hacker's Inside Look at Call Center Compromise</h1>
<p><em>The flickering monitor cast long shadows across the dimly lit room. Outside, the city slept, oblivious to the digital skirmishes unfolding in the underbelly of the network. Tonight, the target wasn't a corporate fortress or a government server. Tonight, we were going inside the lion's den – a scammer's call center. Not just disrupting their operation, but witnessing it firsthand. The webcam, a seemingly innocent portal, becomes the window into their world. This is not just about a prank; it's a tactical maneuver to reveal the infrastructure and the individuals behind widespread digital deceit.</em></p>
<!-- MEDIA_PLACEHOLDER_1 -->
<p>The digital landscape is a battlefield, and misinformation is a weapon. Scam operations thrive in the shadows, preying on the unsuspecting. But even the most elaborate schemes leave digital footprints. Our objective tonight is not merely to disrupt, but to understand the operational methodology of these fraudulent entities. By gaining access to their core operational hub – a call center – we can peel back the layers of deception and expose the mechanics of their trade.</p>
<h2>The Digital Infiltration: Gaining the Foothold</h2>
<p>The initial phase of engagement involves identifying vulnerabilities within the target's digital infrastructure. In the context of a scammer call center, this often means exploiting the very tools they use to conduct their operations. This could range from unpatched operating systems and weak network configurations to phishing attacks targeting their lower-tier operatives. The goal is to establish a persistent presence, a digital ghost in their machine, before moving to more impactful actions.</p>
<p>Consider the common tools these operations might employ: VoIP systems, CRM software, possibly even remote access tools hastily deployed for managing their workforce. Each of these is a potential entry point. A well-crafted phishing email, masquerading as an internal memo or a system update, can be the key to unlocking their network. Once inside, the objective is reconnaissance – mapping the network, identifying key assets, and locating the sensitive data or access points that will allow for webcam activation.</p>
<h2>Operational Reconnaissance: Mapping the Enemy's Territory</h2>
<p>With an established foothold, the next critical step is reconnaissance. This is where the attacker truly begins to think like a defender, anticipating the enemy's moves and understanding their environment. For a scam operation, this means identifying:</p>
<ul>
<li><strong>Network Topology:</strong> How are their systems interconnected? Are they using a centralized server or a distributed network?</li>
<li><strong>Key Personnel:</strong> Who are the individuals managing the operation? Are there technical staff, supervisors, or just operatives?</li>
<li><strong>Communication Channels:</strong> How do they communicate internally and with their targets?</li>
<li><strong>Hardware and Software:</strong> What specific types of computers, cameras, and software are in use?</li>
</ul>
<p>This phase is crucial. The more information gathered, the more precise and devastating the subsequent actions can be. It's about understanding not just the technical vulnerabilities, but the human element as well. Knowing their routines, their communication patterns, and even the names they use can be invaluable.</p>
<!-- MEDIA_PLACEHOLDER_2 -->
<h2>Command and Control: Activating the Eyes</h2>
<p>The ultimate objective in this scenario is to gain visual access to the scammers' environment. This is achieved through the activation of their webcams. Once a system with webcam access is compromised, and depending on the operating system and installed software, various methods can be employed. This often involves leveraging built-in operating system functionalities or using specialized tools that can interface with the camera hardware.</p>
<p>The technical execution can involve:</p>
<ul>
<li><strong>Remote Command Execution:</strong> Using tools like PowerShell on Windows or Bash scripting on Linux to trigger camera access.</li>
<li><strong>Leveraging Existing Software:</strong> If the scammers are using remote monitoring or collaboration software, exploiting its features to activate cameras.</li>
<li><strong>Driver Manipulation:</strong> In more sophisticated attacks, directly interacting with the camera's drivers to force activation.</li>
</ul>
<p>Seeing the faces behind the scams adds a powerful human element to the exposure. It shifts the narrative from abstract digital fraud to tangible individuals perpetrating these crimes. It's a form of digital justice, bringing the perpetrators into the light.</p>
<h2>The Fallout: Exposing the Operation</h2>
<p>Once visual confirmation is established, the process shifts to documentation and exposure. This footage serves as irrefutable evidence of their operations. The goal is to compile a comprehensive report, often in video format, that details every aspect of the scammer's setup:</p>
<ul>
<li><strong>The Environment:</strong> The physical space, the number of workstations, the general atmosphere of the call center.</li>
<li><strong>The Operatives:</strong> Their interactions, their scripts, their reactions when confronted.</li>
<li><strong>The Technology:</strong> The specific software and hardware they are using, including potentially sensitive configuration details.</li>
</ul>
<p>This exposure serves multiple purposes. Firstly, it acts as a deterrent, showing potential scammers that their operations are not as secure as they believe. Secondly, it educates the public about the realities of these scams, helping them to better identify and avoid falling victim. Finally, it can aid law enforcement agencies by providing direct intelligence on criminal organizations operating globally.</p>
<h2>Case Study: Beyond the Webcam</h2>
<p>The act of turning on a scammer's webcam is more than just a technical feat; it's a part of a larger strategy of disrupting and dismantling criminal enterprises. This approach often involves collaboration with other security researchers and content creators, pooling resources and expertise to achieve a greater impact. Expeditions into the heart of scam operations have revealed a wide spectrum of fraudulent activities, from fake tech support scams targeting the elderly to impersonation schemes designed to steal financial information.</p>
<p>We've seen operations pretending to be major tech companies like Amazon, Apple, Microsoft, and Norton. We've witnessed the deletion of critical files, the use of syskey tools to lock down systems, and the implementation of sophisticated social engineering tactics tailored to specific demographics and languages, including Hindi, Urdu, and others originating from the Indian subcontinent. These operations are not amateur hour; they are organized criminal enterprises requiring a coordinated, multi-faceted response.</p>
<!-- AD_UNIT_PLACEHOLDER_IN_ARTICLE -->
<h2>Arsenal of the Operator/Analyst</h2>
<p>To conduct operations of this nature, a specific set of tools and knowledge is indispensable. While the techniques can vary, a foundational understanding of network penetration, social engineering, and digital forensics is paramount. For those looking to delve deeper into understanding and mitigating such threats, the following resources are invaluable:</p>
<ul>
<li><strong>Penetration Testing Tools:</strong> Kali Linux distribution, Metasploit Framework, Burp Suite Professional (essential for web application analysis), Nmap for network scanning.</li>
<li><strong>Programming Languages:</strong> Python for scripting and automation (e.g., interacting with APIs, data analysis), Bash for system administration and shell scripting.</li>
<li><strong>Collaboration Platforms:</strong> Discord servers and private forums where security researchers share intelligence and coordinate efforts.</li>
<li><strong>Content Platforms:</strong> YouTube channels like those of Jim Browning and Mark Rober, and platforms like Twitch for live analysis and community engagement.</li>
<li><strong>Learning Resources:</strong> Certifications such as the OSCP (Offensive Security Certified Professional) for practical penetration testing skills, and books like "The Web Application Hacker's Handbook" for in-depth knowledge.</li>
</ul>
<p>Understanding the tools of engagement is as critical as understanding the mindset of the adversary. This knowledge empowers both offensive and defensive strategies.</p>
<h2>FAQ</h2>
<h3>What legal considerations are there when accessing a scammer's system?</h3>
<p>While the primary intent is to disrupt criminal activity, unauthorized access to any system, even a scammer's, can have legal repercussions. Operations like these are typically conducted with a strong focus on evidence gathering for potential law enforcement referral, and often involve collaboration with individuals who understand the legal boundaries. Extreme care is taken to ensure actions are justifiable and ethically sound.</p>
<h3>How do these operations typically identify their targets?</h3>
<p>Scammers often acquire victim data through various means, including data breaches, phishing campaigns, and the purchase of compromised personal information on the dark web. Our targets, in this case, are the scammers themselves. Identifying their operational infrastructure can involve tracing their communication channels, analyzing their online presence, and sometimes, through direct engagement and social engineering.</p>
<h3>What is the primary goal of exposing these scammer call centers?</h3>
<p>The primary goals are multi-fold: to disrupt ongoing criminal operations, to gather evidence for potential prosecution, to educate the public about the methods scammers use, and to deter future criminal activity by demonstrating that these operations are not untraceable.</p>
<h3>Are these operations always successful in activating webcams?</h3>
<p>Success depends heavily on the technical sophistication of the scam operation and the vulnerability of their systems. Some operations employ robust security measures, while others are surprisingly lax. The success rate varies, but the continuous effort is to refine techniques and adapt to evolving defensive measures.</p>
<h3>Can this method be applied to other types of cybercrime?</h3>
<p>The principles of identifying vulnerabilities, gaining access, and conducting reconnaissance are fundamental to all forms of offensive security and threat intelligence gathering. While webcam activation is specific to certain scenarios, the underlying methodology can be adapted to investigate a wide range of cybercrimes, from botnet operations to financial fraud schemes.</p>
<!-- AD_UNIT_PLACEHOLDER_IN_ARTICLE -->
<h2>The Contract: Bringing the Shadows to Light</h2>
<p>The digital realm is fraught with hidden threats. By turning the tables on those who seek to exploit others, we not only disrupt immediate harm but also illuminate the dark corners of cybercrime for all to see. The activation of a scammer's webcam is a symbolic act, bringing the hidden faces of deception into the unforgiving glare of public scrutiny. It’s a reminder that every digital action has a consequence, and sometimes, those consequences are brought directly to their doorstep.</p>
<p>Now, it's your turn. What are the most effective, ethical, and technically sound methods you've encountered or devised for disrupting illicit online operations? Share your insights, tools, and methodologies below. Let this serve as a testament to the power of collective knowledge in combating digital malfeasance.</p>
No comments:
Post a Comment