The digital world is a shadowy alleyway, and data is the currency. But sometimes, that currency gets snatched, locked away behind an encryption wall. Today, we're not building that wall. We're dissecting it. We're pulling apart the mechanics of ransomware, not to replicate it, but to understand its insidious elegance and, more importantly, to build stronger defenses against it. This isn't about unleashing chaos; it's about mastering the art of digital forensics and proactive security by understanding the enemy's toolkit.
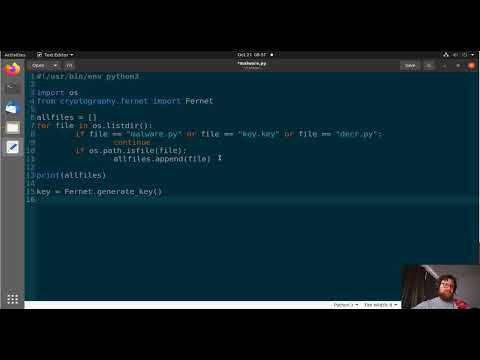
The core of many modern ransomware attacks lies in robust encryption. Python, with its accessible libraries, provides a surprisingly potent environment for crafting these malicious tools, though this analysis focuses purely on the educational aspect for defensive purposes. The cryptography library, specifically the Fernet module, is a prime candidate for this dissection. Fernet ensures that a message being sent can only be expect. Anyone who is trying to tamper with the message will be able to detect it. It also offers authenticated encryption. What this means is that it identifies if any cryptographic messages are being tampered with. This level of security is often found in secure communication protocols, but in the wrong hands, it becomes the lock on your digital vault.
Understanding Fernet Encryption
Fernet is an opinionated implementation of authenticated symmetric encryption. This means a single key is used for both encrypting and decrypting data. The process is straightforward:
- Key Generation: A secure, random key is generated. This key is the linchpin of the entire operation. Without it, decryption is practically impossible.
- Encryption: Using the generated key, the target data (files, in the case of ransomware) is transformed into an unreadable ciphertext. Fernet appends a timestamp to the token, which means that it will be decrypted only if it is not expired.
- Decryption: The same key is used to reverse the process, returning the ciphertext to its original, readable form.
For a ransomware operator, the challenge isn't just encrypting files; it's securely managing and exfiltrating the encryption key. If the key is lost or inaccessible, the ransomware fails its primary objective: extorting payment for decryption. This reliance on a singular key is both its strength and its Achilles' heel from a defensive perspective.
The Anatomy of a Simulated Ransomware Attack (Defensive Perspective)
Let's break down how a ransomware script might operate, always with the blue team's viewpoint in mind. Our goal is detection and mitigation, not execution.
Phase 1: Reconnaissance and Target Identification
The first move is to map the territory. A ransomware script needs to identify the files it will encrypt. This typically involves:
- Directory Traversal: Recursively scanning through directories, starting from a designated point (e.g., user's Documents, Desktop, or even network shares).
- File Filtering: Identifying specific file types based on extensions (e.g.,
.docx,.xlsx,.jpg,.pdf). Critical system files are often skipped to prevent system instability, which would make decryption impossible and alert defenders prematurely.
Defensive Insight: Monitoring unusual file access patterns, especially extensive read/write operations on a large number of user-data files across multiple directories, can be a critical early indicator. File integrity monitoring (FIM) solutions are invaluable here.
Phase 2: Encryption Execution
Once targets are identified, the encryption process begins:
- Key Management: The script either generates a new key for each infection or, more sophisticatedly, uses a pre-generated master key and encrypts each user's key with a public key, exfiltrating the encrypted private key.
- File Encryption: Each target file is read, encrypted using the Fernet algorithm, and then overwritten with the ciphertext. The original file is lost.
- Ransom Note: A note is dropped into affected directories, typically a text file (e.g.,
README.txt,DECRYPT_ME.txt), detailing the attack and instructions for payment.
Defensive Insight: High I/O activity, rapid file modification, and the sudden appearance of ransom notes are strong indicators. Anomaly detection systems looking for these behaviors can trigger alerts. The use of encryption libraries can also be flagged by endpoint detection and response (EDR) solutions.
Phase 3: Persistence and Exfiltration (Optional but common)
More advanced ransomware might:
- Establish Persistence: Modify the registry or schedule tasks to ensure the ransomware runs again after a reboot.
- Exfiltrate Keys: Transmit the encryption key (or keys) to the attacker's command-and-control (C2) server.
Defensive Insight: Monitoring for unusual outbound network connections from endpoints, especially to known C2 infrastructure or unexpected IP addresses, is crucial. Changes to startup configurations and scheduled tasks also warrant investigation.
The Ethical Hacker's Toolkit: Defensive Strategies
Understanding how ransomware works is the first step in defending against it. Here's how ethical hackers and security professionals leverage this knowledge:
Threat Hunting for Ransomware Indicators
Threat hunters actively search for signs of compromise. For ransomware, this involves looking for:
- Suspicious Process Execution: Processes invoking encryption libraries or performing mass file operations.
- Network Anomalies: Communication with known malicious IPs or unusual data transfer patterns.
- File System Events: Rapid creation, modification, or deletion of files, especially followed by the appearance of ransom notes.
- Registry/Scheduled Task Modifications: Persistence mechanisms being established.
Forensic Analysis of Encrypted Files
If an attack occurs, digital forensics is key. This involves:
- Memory Forensics: Extracting encryption keys or other volatile data from system memory before they are overwritten.
- Disk Forensics: Analyzing file system artifacts to understand the scope of the attack, identify the ransomware variant, and potentially recover fragments of original data.
- Log Analysis: Correlating events across system logs, application logs, and network logs to reconstruct the attack timeline.
Arsenal of the Operator/Analist
- For Analysis & Defense:
- SIEM Solutions (e.g., Splunk, ELK Stack): For log aggregation and correlation.
- EDR Solutions (e.g., CrowdStrike, SentinelOne): For endpoint visibility and threat detection.
- Network Intrusion Detection Systems (NIDS): To monitor network traffic for malicious patterns.
- Forensic Tools (e.g., Autopsy, Volatility): For in-depth analysis of compromised systems.
- Scripting Languages (Python, PowerShell): For developing custom detection scripts and analysis tools.
- For Understanding Attack Vectors (Ethical Use Only):
- Python with
cryptographylibrary: To study encryption mechanisms. (Disclaimer: This should only be done in isolated, controlled lab environments. Never execute on production systems or systems you do not own and have explicit permission to test.)
- Python with
- Key Reading Material:
- "The Web Application Hacker's Handbook" by Dafydd Stuttard and Marcus Pinto (For understanding diverse attack vectors)
- "Practical Malware Analysis" by Michael Sikorski and Andrew Honig (For dissecting malicious software)
- Certifications:
- GIAC Certified Incident Handler (GCIH): Focuses on incident handling.
- Certified Ethical Hacker (CEH): Provides a broad overview of ethical hacking tools and techniques.
- Offensive Security Certified Professional (OSCP): A highly regarded hands-on certification focused on penetration testing. (Understanding offensive tactics is crucial for building effective defenses).
Taller Defensivo: Fortaleciendo tu Entorno contra Ransomware
Guía de Detección: Patrones de Cifrado Masivo
- Monitorizar la Actividad de Archivos: Implementa o configura herramientas de Monitoreo de Integridad de Archivos (FIM) para alertar sobre modificaciones masivas o encriptaciones de archivos, especialmente en directorios críticos de usuarios y servidores de archivos.
- Analizar el Uso de APIs de Cifrado: Utiliza soluciones EDR/XDR para detectar el uso de bibliotecas de cifrado (como
cryptographyen Python o APIs de Windows similares) por procesos no autorizados o inesperados. Busca llamadas a funciones comoencrypt()ogenerate_key()realizadas por scripts o ejecutables sospechosos. - Detectar la Creación de Archivos de Ransom: Configura alertas para la aparición súbita de archivos de texto con nombres comunes de notas de rescate (
README.txt,DECRYPT_INSTRUCTIONS.txt) en múltiples directorios. - Rastrear Tráfico de Red Anómalo: Vigila las conexiones salientes a IP o dominios desconocidos o sospechosos, especialmente si coinciden con ventanas de actividad de archivos masiva. Esto podría indicar la exfiltración de claves o la comunicación con servidores de Comando y Control (C2).
- Revisar Cambios en el Registro y Tareas Programadas: Auditorías regulares o alertas automatizadas sobre cambios en claves de registro relacionadas con el inicio automático de programas o la creación de nuevas tareas programadas pueden revelar intentos de persistencia por parte del ransomware.
Preguntas Frecuentes
¿Es posible recuperar archivos cifrados por ransomware sin pagar?
En algunos casos, sí. Si el ransomware es débil, utiliza claves débiles, o si existen vulnerabilidades conocidas en el algoritmo de cifrado o en la implementación, herramientas de descifrado públicas pueden estar disponibles. La cooperación con investigadores de seguridad y equipos de respuesta a incidentes es fundamental. Sin embargo, depender de esto no es una estrategia viable.
¿Cuál es la defensa más efectiva contra el ransomware?
La defensa más efectiva es una estrategia multicapa. Esto incluye copias de seguridad robustas y probadas (offline y fuera de línea), parches de software actualizados, segmentación de red, fuertes políticas de control de acceso, concienciación del usuario sobre phishing, y soluciones de seguridad endpoint avanzadas con capacidades de detección y respuesta.
¿Por qué los atacantes usan Python para crear ransomware?
Python es elegido por su simplicidad, legibilidad y la disponibilidad de bibliotecas potentes como cryptography. Permite a los atacantes desarrollar prototipos rápidamente y desplegar código que puede ser efectivo sin una curva de aprendizaje empinada.
Veredicto del Ingeniero: ¿Vale la pena la paranoia del Ransomware?
Absolutamente. Ignorar el riesgo del ransomware en 2024 es como dejar la puerta de tu bóveda abierta con un cartel de "Bienvenido". Las herramientas para atacar son cada vez más sofisticadas y accesibles. Sin embargo, la tecnología para defenderse también ha avanzado significativamente. La clave está en la proactividad. Las copias de seguridad son tu seguro, la educación es tu primera línea de defensa, y las herramientas de seguridad de vanguardia son tu armadura. No se trata de vivir con miedo, sino de operar con inteligencia y preparación. Entender la amenaza es el primer paso para neutralizarla. El código que hoy analizamos como una lección de defensa, mañana podría ser el rastro que nos permita atrapar a un atacante.
The black hats are always innovating. So must the white hats. This deep dive into ransomware encryption is not an invitation to create, but a blueprint for fortification. It’s about seeing the lock mechanism so you can build an impenetrable vault.
The Contract: Fortify Your Perimeter
Your mission, should you choose to accept it, is threefold:
- Implement Offline Backups: Verify that your critical data has at least one backup that is not continuously connected to your network. Test its restore functionality now.
- Review Endpoint Security Logs: Spend 30 minutes today reviewing security logs on your endpoints, specifically looking for unusual file activity or process executions that might indicate potential ransomware behavior.
- Educate Your Team: Share what you've learned about ransomware tactics with your immediate colleagues or team members. Awareness is a powerful weapon.
Report back with your findings and any critical vulnerabilities you uncovered. The digital frontier demands constant vigilance.

No comments:
Post a Comment