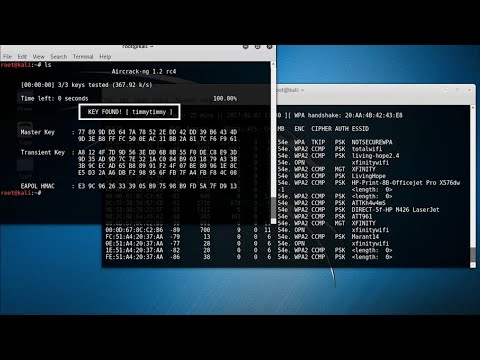
"The belief that anonymity is absolute is a dangerous delusion. Every click, every connection, leaves a trace. The challenge is finding it before the damage is irreversible." - cha0smagick## The Unseen Costs: Risks and the Inescapable Consequences The allure of the deep web is a siren song for the reckless. We issue this stern warning: engaging in these activities is a one-way ticket to severe legal repercussions and a wrecked life. The penalties are harsh, and the damage to one's future is often irreparable. Cybersecurity and digital ethics aren't abstract concepts; they are fundamental responsibilities. Your online actions have real-world consequences, and the digital shadows offer no real sanctuary. ## The Unending War: Forums, Markets, and the Fight Against Cybercrime The persistence of these illicit forums and markets is a testament to the ongoing, evolving nature of cybercrime. It underscores the critical importance of continuous, global efforts to combat these threats. This isn't a battle won with a single offensive or a patch. It requires unwavering collaboration, relentless education, and pervasive awareness. These are our most potent weapons in this digital arms race. In summation, our expedition into the deep web has yielded a chilling yet invaluable insight into the world of initial access brokers and wholesale markets. By leveraging tools like Flair, we’ve illuminated this covert ecosystem, reinforcing the urgent necessity to fortify our cyber defenses and champion ethical online conduct. Vigilance is key. Commitment is paramount. The fight for a safer digital realm is perpetual. ## The Engineer's Verdict: Flair's Place in the Operator's Toolkit Flair isn't for the faint of heart or the casual observer. It’s built for the trenches, for the analysts and threat hunters who need to map the enemy's movements in the darkest corners of the internet. Its strength lies in its specialized focus on Tor-based illicit activities. While it might not be your primary tool for analyzing malware heuristically, as a dedicated deep web intelligence platform, it’s exceptionally powerful. The intel it provides can be critical for proactive defense, understanding attacker methodologies, and even aiding law enforcement. It’s a specialized instrument, essential for specific, high-stakes operational requirements. ## Operator's Arsenal: Tools for the Deep Dive
- **Flair**: Essential for deep web threat intelligence, tracking illicit activity.
- **Tor Browser**: For cautious, ethically-guided exploration and access to .onion services.
- **Wireshark**: For deep packet inspection and network traffic analysis.
- **OSINT Framework**: A meta-resource for gathering open-source intelligence.
- **Malware Analysis Sandbox (e.g., Any.Run, Hybrid Analysis)**: To dissect malicious payloads safely.
- **Intelligence Platforms (e.g., Recorded Future, CyberIntel)**: For broader threat landscape context.
- **Certifications:** OSCP for offensive techniques, GCFA for forensics, GCTI for threat intelligence.
- **Books:** "The Art of Memory Forensics", "Dark Web" by Joshua Davis.
- Hypothesize Threat Vectors: Based on industry reports, threat intel feeds, and the type of data your organization handles, hypothesize how attackers might gain initial access. Consider common techniques like phishing, exploitation of known vulnerabilities, or compromised credentials.
- Leverage Threat Intelligence: Utilize tools like Flair or commercial TI feeds to monitor discussions or marketplaces related to your industry or technologies. Look for mentions of your organization, its hosted services, or specific vulnerabilities that might be for sale.
- Identify Potential IoCs: When intelligence surfaces (e.g., a specific IP address, domain, or C2 server mentioned in a dark web forum), extract these Indicators of Compromise (IoCs).
- Configure Detection Rules: Translate these IoCs into detection rules for your Security Information and Event Management (SIEM) system, Intrusion Detection/Prevention Systems (IDS/IPS), or endpoint detection and response (EDR) solutions. For example, create firewall rules to block known malicious IPs or alerts for suspicious domain lookups.
- Analyze Network Traffic: Monitor outbound network traffic for connections to known Tor exit nodes or suspicious destinations that align with threat intelligence on illicit markets.
- Hunt for Compromised Credentials: Regularly scan dark web dumps and credential leak sites (ethically and with proper authorization) for any signs of your organization's or employees' credentials being exposed. Implement strong password policies and multi-factor authentication (MFA) to mitigate this risk.
- Assume Breach Mentality: Conduct regular tabletop exercises and simulations based on potential initial access scenarios to test your incident response plans and team readiness.
Q: Is it illegal to access the deep web?
A: Accessing the deep web itself is not illegal. It's a part of the internet not indexed by standard search engines. However, engaging in illegal activities within the deep web, such as purchasing illicit goods or services, is strictly prohibited and carries severe legal consequences.
Q: How can I protect myself from initial access brokers?
A: Robust cybersecurity practices are key. This includes strong, unique passwords, multi-factor authentication (MFA), keeping all software updated, being wary of phishing attempts, and maintaining a vigilant network monitoring strategy.
Q: What makes a tool like Flair valuable for cybersecurity professionals?
A: Tools like Flair provide specialized intelligence on threats originating from the deep web. This allows security teams to proactively identify potential attack vectors, understand the tactics of cybercriminals, and strengthen defenses against emerging threats that might not be visible on the surface web.
The Contract: Fortify Your Digital Perimeter
You've peered into the abyss. You've seen the marketplaces where access to systems is bartered. Your contract now is to harden your digital perimeter against these unseen threats. Your challenge: Develop a basic threat model for your organization based on this information.- Identify the top 3 types of initial access an attacker might use against your organization, considering the "Diversity of Offerings" section.
- For each identified vector, list one practical defensive measure you can implement immediately.
- Consider how you would monitor for signs that these access vectors are being targeted or have been successful.