
The digital battlefield of cybersecurity is littered with forgotten configurations and overlooked hardware. In the realm of Wi-Fi penetration testing, the tools you choose can often speak louder than your exploits. A weak adapter is like an audible whisper in a silent room – it’s an invitation for detection. Today, we’re not just opening boxes; we're dissecting the very hardware that forms the frontline of wireless reconnaissance.
In this deep dive, we’ll leverage the insights of seasoned operators like Kody Kinzie, a name synonymous with Null Byte and Hak5, to understand what truly separates a viable Wi-Fi hacking tool from expensive e-waste. Forget the marketing jargon; we’re talking real-world performance, compatibility, and the subtle nuances that make an adapter shine under pressure.
The landscape of Wi-Fi adapters for ethical hacking is vast, ranging from colossal, high-gain antennas to discreet, microcontroller-based solutions. You can acquire a beast like the Alfa Tube U, designed for maximum signal capture, or opt for more compact, versatile devices such as the Alfa AWUS036NHA, the intriguing WEMOS D1 Mini, or the cleverly named WiFi Nugget. Each of these options caters to different operational needs and budget constraints. This isn't about finding the cheapest option; it's about selecting the *right* tool for the job, understanding that the initial investment in quality hardware can save countless hours and prevent critical operational failures.
What Kind of Interview is This?
The integrity of an operation hinges on the fidelity of its tools. In the shadow-ops of wireless security, your Network Interface Card (NIC) is your primary sensor. Choosing the wrong one isn't just inefficient; it's a tactical error that can compromise an entire engagement. This isn't a casual chat; it's a strategic briefing on hardware selection for those who understand the stakes.
Introducing Kody Kinzie
Kody Kinzie is more than a content creator; he’s an operator who bridges the gap between theoretical exploits and practical application. His work on platforms like Null Byte and his ventures with Hak5 have consistently provided the security community with actionable intelligence. In this segment, Kinzie offers his hard-won expertise on selecting hardware that stands up to the rigors of Wi-Fi analysis and exploitation.
Null Byte: What Happened?
Null Byte, for those entrenched in the infosec trenches, was a vital resource. It served as a digital armory, providing guides and discussions on everything from ethical hacking to system administration. Its evolution and subsequent changes represent a common narrative in the online security space: the constant flux of platforms and the enduring need for authentic knowledge. Understanding the history of such resources helps us appreciate the foundational knowledge that underpins current best practices.
Hacking With Friends: SecurityFWD
The concept of "SecurityFWD" (Forward Security) embodies a collaborative spirit within the cybersecurity domain. It suggests a proactive approach, encouraging knowledge sharing and mutual advancement. Engaging with peers, as Kody does through his "SecurityFWD" initiatives, is crucial for staying ahead. The security landscape is a moving target, and isolation is a vulnerability in itself.
Kody's Project: The WiFi Nugget
The WiFi Nugget represents an innovative approach to portable Wi-Fi security assessment. It’s not just a piece of hardware; it’s a compact, self-contained unit designed for discrete operations. The Nugget blurs the lines between a simple adapter and a deployable hacking platform, offering flexibility that traditional USB adapters can’t match. Its design addresses the need for stealth and on-the-go functionality, making it a compelling option for field operations.
It Looks Like A Lightsaber: Best Alfa WiFi Adapter?
The Alfa brand has carved a significant niche in the market for wireless adapters favoured by penetration testers. When Kody likens an adapter to a lightsaber, he’s not just commenting on its aesthetic; he’s alluding to its power and precision as a tool. Among their offerings, adapters like the Alfa AWUS036NHA stand out. This adapter is lauded for its chipset compatibility, particularly with Linux-based systems like Kali, and its ability to operate in monitor mode, a prerequisite for many Wi-Fi attacks. When evaluating Alfa adapters, look for chipsets known for robust driver support and promiscuous mode capabilities.
Hacking from the Hollywood Sign
The narrative of performing a Wi-Fi hack from a geographical landmark like the Hollywood Sign serves as a colourful anecdote. However, it subtly highlights key operational considerations: signal propagation, line-of-sight, and the range limitations of your hardware. It’s a reminder that ethical hacking isn't confined to a lab; it’s about understanding how to leverage tools effectively in diverse, real-world scenarios. The power and sensitivity of your Wi-Fi adapter directly influence the feasibility of such operations.
Small WiFi Adapters: The NEH or the NHA?
For operators prioritizing discretion and portability, smaller form factors are essential. The distinction between adapters like the Alfa AWUS036NEH (often praised for its compact size and functionality with specific chipsets) and the AWUS036NHA (known for the Atheros AR9271 chipset) boils down to specific use cases and driver support. The NHA, often favoured for its superior monitor mode and packet injection capabilities on Linux, is a staple for many pentesters. The NEH, while smaller, might have driver limitations depending on the operating system and the specific tasks at hand. Always verify chipset compatibility for your target OS.
Favourite OS: Kali Linux or?
Kali Linux remains the de facto standard for many in the penetration testing community. Its pre-loaded suite of security tools, including those for Wi-Fi analysis like Aircrack-ng, makes it an efficient starting point. However, experts like Kody understand that proficiency extends beyond the OS. Proficiency with tools on other platforms, such as specialized embedded systems or even Windows with the right drivers, showcases a deeper understanding of the underlying technologies. The OS is a vehicle, but the driver’s skill is paramount.
The Difference: Pi vs Microcontrollers
The distinction between a Raspberry Pi and discrete microcontrollers (like the ESP8266 or ESP32 family, which power devices such as the WiFi Nugget or WEMOS D1 Mini) is fundamental to understanding embedded security hardware.
- Raspberry Pi: A full-fledged single-board computer running a Linux OS. Offers significant processing power, extensive I/O, and the ability to run complex applications. Ideal for more demanding tasks like network analysis, vulnerability scanning, or acting as a portable command-and-control server.
- Microcontrollers: Simpler, lower-power devices focused on specific tasks. They lack a full operating system, running firmware directly. Excellent for dedicated functions like Wi-Fi reconnaissance, deauthentication attacks, or acting as a hardware keylogger. They are ideal for stealthy, low-power deployments and often more cost-effective for single-purpose tools.
The WiFi Nugget leverages the strengths of microcontrollers for a compact, specialized Wi-Fi assessment tool.
Wi-Fi Hacking: What is a WiFi Nugget?
The WiFi Nugget is a prime example of a specialized, portable Wi-Fi hacking tool. It typically integrates a microcontroller (like the ESP8266 or ESP32) with a Wi-Fi chip and minimal interface, often designed to fit discreetly into a USB port or resemble a common electronic device. Its purpose is to perform targeted Wi-Fi operations – such as network scanning, deauthentication attacks, or acting as a rogue access point – with ease and minimal setup, often controllable via a web interface or a companion app.
The process of loading specialized firmware onto devices like the WiFi Nugget is known as "flashing." This involves compiling or downloading the desired hacking tools (e.g., firmware for Wi-Fi deauthentication, network sniffing) and transferring them to the microcontroller's memory. This is typically achieved via a USB connection and a specific flashing utility or, in some advanced cases, through a web browser interface. The ability to easily update or swap firmware transforms these small devices into versatile cyber attack platforms.
Why Hardware is Hard
Developing and utilizing specialized hardware for cybersecurity presents unique challenges. Unlike software, hardware requires physical design, component sourcing, manufacturing, and robust driver development. Compatibility issues across different operating systems and chipsets are rampant. Furthermore, the evolving nature of wireless protocols and security measures means hardware solutions can quickly become obsolete or require significant firmware updates. This complexity is often why we see dedicated hardware projects take off – they solve specific, difficult problems.
The Difference: USB vs WiFi Nugget
The contrast between traditional USB Wi-Fi adapters and devices like the WiFi Nugget lies in their architecture and functionality:
- USB Adapters (e.g., Alfa AWUS036NHA): These are external network interfaces that plug into a host computer (laptop, desktop). They rely on the host's CPU and OS for processing and often require specific drivers. They are versatile for direct analysis and attacks initiated by the connected machine.
- WiFi Nugget (Microcontroller-based): These are typically standalone devices. They contain their own processing capabilities (though more limited than a PC) and often run custom firmware. They can operate independently or be managed remotely, offering greater stealth and portability. They excel at specific, automated tasks without needing a full computer.
The choice depends on whether you need a powerful, flexible tool integrated into a larger system, or a dedicated, discreet device for singular missions.
Flashing via Browser?
The idea of flashing firmware directly through a web browser is a significant convenience. It eliminates the need for specialized software or command-line tools on the host machine, simplifying the deployment process. This is often achieved using JavaScript-based interfaces that communicate with the microcontroller's bootloader. While convenient, ensuring the integrity and security of this browser-based flashing process is critical to prevent malicious firmware injection.
Getting Started with Microcontrollers
Embarking on microcontroller projects for cybersecurity can seem daunting, but the barrier to entry is lower than ever. Platforms like the ESP32 or ESP8266 are popular choices due to their integrated Wi-Fi capabilities, ample community support, and affordability. Development environments like the Arduino IDE or PlatformIO provide structured frameworks for writing and compiling code.
CircuitPython instead of Arduino
While the Arduino IDE is a well-established platform, CircuitPython offers a compelling alternative, particularly for rapid prototyping and ease of use. Developed by Adafruit, CircuitPython is a version of MicroPython designed for simplicity. It allows developers to write code in Python and run it directly on supported microcontrollers without a complex compilation step, treating the device like a USB drive where code can be edited and saved dynamically. This can significantly speed up the development cycle for custom security tools.
Which Nugget to Pick?
Selecting the right "Nugget" or microcontroller-based Wi-Fi tool depends on your specific operational requirements. Factors to consider include:
- Chipset Capabilities: For Wi-Fi attacks requiring advanced features like monitor mode and packet injection, ESP32-based devices often offer superior performance and compatibility compared to older ESP8266 models.
- Form Factor & Power: Do you need something ultra-discreet that fits anywhere, or a slightly larger device with more processing power?
- Firmware Support: Is there active community development for the specific firmware you intend to use? Projects like the ESP8266 Deauther have dedicated communities and ongoing updates.
- Ease of Use: Some devices offer pre-compiled firmware or web interfaces, while others require more hands-on flashing and configuration.
For general-purpose Wi-Fi reconnaissance and basic attacks, many gravitate towards ESP32-based solutions.
Where to Buy the Nugget
Specialized hardware like the WiFi Nugget and its components can be sourced from various online retailers. Adafruit, SparkFun, Amazon, and AliExpress are common marketplaces. For Kody's specific projects, it's advisable to check his official storefronts or recommended vendors, as they often provide curated kits or pre-configured devices. Always verify the seller's reputation and product specifications before purchasing.
Recommended Adapters & Products:
Continuous learning is non-negotiable in cybersecurity. Kody Kinzie actively fosters a community for knowledge exchange. Engaging with his content across platforms like YouTube (SecurityFWD) and Twitter (@KodyKinzie) provides direct access to his insights and the broader community. Joining these networks is how you stay informed about emerging threats, new tools, and advanced techniques.
Thank You & Closing Thoughts
The selection of Wi-Fi hardware is a critical first step in any wireless security assessment. It dictates your capabilities, your stealth, and ultimately, the success of your mission. From high-gain USB adapters to compact microcontroller devices like the WiFi Nugget, each tool has its place in the operator's arsenal. Understanding the underlying technology and specific use cases allows for informed decisions.
Being a Beginner
Every expert was once a novice. The key is to embrace the learning curve. Start with fundamental concepts, understand the hardware's limitations, and gradually scale up your complexity. Don't be afraid to experiment with affordable microcontrollers or entry-level USB adapters. The journey is as important as the destination.
Always Learn: If You Think You Know Everything
The cybersecurity world moves at light speed. What is cutting-edge today might be legacy tomorrow. Arrogance is a vulnerability. Maintain a beginner's mindset, constantly seeking new knowledge, validating your understanding, and challenging your assumptions. The moment you believe you know it all is the moment you become a target.
Don't Make It Your Entire Identity
While passion for cybersecurity is commendable, it shouldn't consume your entire identity. Maintain a balanced life. Your skills are valuable, but they are a part of who you are, not the entirety of it. This perspective helps prevent burnout and fosters a healthier relationship with the demanding field of information security.
Rising Above the Haters as a Content Creator
Creating content in the public sphere, especially in infosec, invites scrutiny and criticism. Develop a thick skin. Focus on delivering value, maintaining ethical standards, and engaging constructively. Not everyone will appreciate your work, but consistent, high-quality content will resonate with those who matter.
End: There's Always a Kid Better Than You
This is a humbling, yet motivating, truth. No matter how skilled you become, there will always be someone younger, faster, or more innovative. Use this as fuel for your own growth, not as a demotivator. Learn from them, collaborate, and continue pushing your own boundaries. The security landscape is vast, and there's always room for improvement.
"The only way to do great work is to love what you do." - Steve Jobs. Applies doubly in cybersecurity; passion fuels the relentless learning required.
Veredicto del Ingeniero: ¿Vale la pena la inversión en hardware especializado?
Absolutely. While software tools and knowledge are paramount, the right hardware acts as a force multiplier. For Wi-Fi operations, specialized adapters and microcontroller platforms like the WiFi Nugget offer distinct advantages in performance, portability, and functionality over generic hardware. Investing in quality adapters like those from Alfa, or dedicated devices for specific tasks, is not an extravagance; it's a strategic decision that enhances operational effectiveness and reduces the risk of exposure. For serious practitioners, these are not optional extras, but essential components of a professional toolkit.
Arsenal del Operador/Analista
- Hardware de Red: Alfa AWUS036NHA, Alfa AWUS036ACM, WiFi Nugget (ESP32-based), Raspberry Pi Zero W.
- Software de Pentesting: Kali Linux, Parrot Security OS.
- Firmware Especializado: ESP8266 Deauther, Mana Toolkit.
- Entornos de Desarrollo: Arduino IDE, PlatformIO, CircuitPython.
- Comunidad y Aprendizaje: Null Byte (archivo), Hak5, SecurityFWD, Kody Kinzie's YouTube channel, Discord servers dedicated to embedded hacking.
- Cursos Relevantes: Kody's Udemy courses on Wi-Fi hacking and microcontrollers, certifications such as OSCP (Offensive Security Certified Professional) which often involve network exploitation.
Taller Defensivo: Fortaleciendo tu Red Wi-Fi Contra Ataques Comunes
- Auditar tus Puntos de Acceso: Verifique que sus routers y puntos de acceso estén actualizados con el último firmware. Los fabricantes lanzan parches para vulnerabilidades conocidas, incluidos fallos en la gestión Wi-Fi.
- Implementar WPA3: Si tu hardware lo soporta, migra a WPA3. Ofrece mejoras criptográficas significativas sobre WPA2, haciendo ataques de fuerza bruta y diccionario mucho más difíciles y lentos.
- Desactivar WPS (Wi-Fi Protected Setup): WPS es notoriamente vulnerable a ataques de fuerza bruta. Si no lo usas explícitamente, desactívalo en la configuración de tu router.
- Segmentar tu Red: Crea una red de invitados separada para visitantes. Esto aísla a los dispositivos no confiables de tu red principal, impidiendo que un ataque a un dispositivo de invitado comprometa tu red interna.
- Monitorizar el Tráfico Desconocido: Utiliza herramientas de monitoreo de red para detectar dispositivos o patrones de tráfico anómalos. La detección temprana de actividad sospechosa es clave para mitigar ataques.
Preguntas Frecuentes
¿Es legal usar adaptadores Wi-Fi para auditorías de seguridad?
El uso de adaptadores Wi-Fi para auditorías de seguridad es legal siempre y cuando poseas la autorización explícita del propietario de la red. Realizar estas actividades en redes sin permiso es ilegal y puede tener severas consecuencias legales. Este contenido es solo para fines educativos y de investigación ética.
¿Qué adaptador Wi-Fi es mejor para principiantes?
Para principiantes, la Alfa AWUS036NHA es una opción sólida. Es compatible con la mayoría de las distribuciones de Linux (incluyendo Kali) y es fácil de usar con herramientas como Aircrack-ng. Su fiabilidad y buen rendimiento en modo monitor la convierten en un excelente punto de partida.
¿Puedo usar mi teléfono Android para auditorías Wi-Fi?
Sí, con las herramientas y accesorios adecuados. Algunos teléfonos Android admiten modo monitor y inyección de paquetes a través de aplicaciones específicas (como NetHunter o WPS Connect) y, a menudo, requieren un adaptador Wi-Fi USB compatible con OTG. Sin embargo, la compatibilidad puede ser limitada y variable.
El Contrato: Asegura tu Perímetro Inalámbrico
La teoría es solo el primer paso. Ahora, aplica este conocimiento. Tu nuevo contrato: identificar al menos dos debilidades de seguridad inalámbrica en tu red doméstica o de trabajo (si tienes permiso) utilizando las técnicas discutidas. Documenta tus hallazgos y, lo que es más importante, implementa las contramedidas defensivas detalladas en el "Taller Defensivo" para fortalecer tu perímetro. Demuestra que no solo lees, sino que actúas para mejorar la seguridad. Comparte tus estrategias de fortalecimiento en los comentarios.


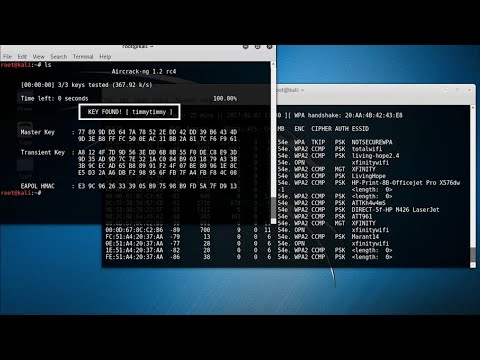

 The digital battlefield of cybersecurity is littered with forgotten configurations and overlooked hardware. In the realm of Wi-Fi penetration testing, the tools you choose can often speak louder than your exploits. A weak adapter is like an audible whisper in a silent room – it’s an invitation for detection. Today, we’re not just opening boxes; we're dissecting the very hardware that forms the frontline of wireless reconnaissance.
The digital battlefield of cybersecurity is littered with forgotten configurations and overlooked hardware. In the realm of Wi-Fi penetration testing, the tools you choose can often speak louder than your exploits. A weak adapter is like an audible whisper in a silent room – it’s an invitation for detection. Today, we’re not just opening boxes; we're dissecting the very hardware that forms the frontline of wireless reconnaissance.

