La luz parpadeante del monitor era la única compañía, mientras los logs del servidor escupían una anomalía. Una que no debería estar ahí. El webinar gratuito de "Security Temple" no fue solo una charla; fue una disección forense de las redes WiFi, un vistazo crudo a cómo los fantasmas digitales se infiltran en nuestros perímetros. Hoy, desmantelaremos ese conocimiento, no para empuñar el bisturí del atacante, sino para fortalecer el escudo del defensor. Hablaremos de adaptadores que susurran secretos, herramientas que revelan vulnerabilidades y la cruda realidad de la seguridad inalámbrica.
En el ajedrez de la ciberseguridad, las redes WiFi son peones expuestos en un tablero demasiado grande. Comprender su mecánica, sus debilidades intrínsecas y las tácticas que los atacantes emplean ya no es una opción, es una necesidad para cualquier operativo que se precie. Este análisis se sumerge en los puntos clave del webinar, desentrañando la esencia de la seguridad inalámbrica para que puedas construir defensas sólidas.
Tabla de Contenidos
- Introducción al Hacking WiFi: El Arte de la Vigilancia
- Adaptadores de Red: La Clave para el Análisis Profundo
- Herramienta Gratuita 'Insider': Escaneando el Terreno
- Clase en Vivo: Fortaleciendo el Arsenal Defensivo
- Seguridad WiFi: Personalización de Diccionarios y Contramedidas
- Veredicto del Ingeniero: ¿Defensa o Ilusión?
- Arsenal del Operador/Analista WiFi
- Taller Defensivo: Fortaleciendo Tu Red WiFi
- Preguntas Frecuentes
- Conclusiones y El Contrato: Tu Próximo Movimiento Defensivo
Introducción al Hacking WiFi: El Arte de la Vigilancia
La red WiFi, esa conveniencia omnipresente, es también una autopista de información vulnerable si no se vigila. El webinar de "Security Temple" pintó un cuadro crudo: la ciberseguridad no es un lujo, es el aire que respiran tus datos. Entender cómo bailan los paquetes de datos a través del éter, cómo se negocian las claves de cifrado y dónde se esconden las fallas, es el primer paso para construir una fortificación digital inexpugnable. Ignorar estas bases es invitar a la catástrofe. Cada dispositivo conectado es un potencial punto de entrada para el adversario; la seguridad WiFi no es solo para corporaciones, es el cerrojo de tu hogar digital.

Adaptadores de Red: La Clave para el Análisis Profundo
No todos los adaptadores de red son iguales en el campo de batalla digital. Para un análisis de seguridad serio, o lo que algunos llaman "hacking ético de WiFi", se requiere hardware específico. El webinar iluminó la importancia crítica de los adaptadores que soportan el modo monitor y la inyección de paquetes. Sin estas capacidades, estás intentando desarmar una bomba con guantes de boxeo. Poder capturar todo el tráfico de un punto de acceso, no solo el dirigido a tu máquina, es fundamental para identificar patrones, contraseñas débiles y posibles explotaciones. Elegir el adaptador correcto no es un detalle menor; es la piedra angular de cualquier operación de reconocimiento de redes inalámbricas.
"La primera regla de la guerra es conocer a tu enemigo y conocerte a ti mismo. En ciberseguridad, esto significa entender las herramientas que el atacante usa y poseer las nuestras."
Invertir en un adaptador compatible es, sin duda, un movimiento inteligente si buscas profundizar en la seguridad WiFi. Claro, puedes realizar escaneos básicos con drivers estándar, pero para análisis forenses de red o pruebas de penetración exhaustivas, necesitas esa capacidad de observación pasiva y activa que solo un adaptador con modo monitor puede ofrecer. La diferencia es entre observar una pelea desde la tribuna y estar en la arena, analizando cada golpe.
Herramienta Gratuita 'Insider': Escaneando el Terreno
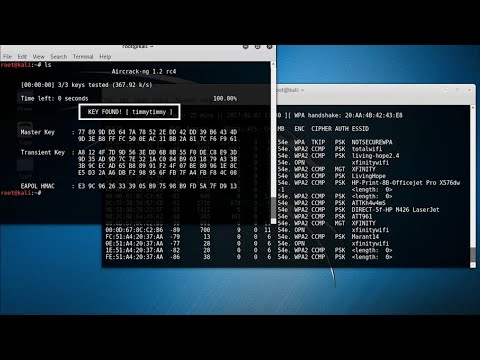
En la caja de herramientas del analista de seguridad, la eficiencia es reina. Durante el evento, se presentó Insider, una herramienta conceptual (o una que podría existir y que utilizaremos como ejemplo) diseñada para escanear redes WiFi y extraer inteligencia valiosa. Imagina tener una brújula y un mapa detallado de las redes circundantes: identifica redes abiertas, encriptadas, la intensidad de la señal, e incluso intenta perfilar los dispositivos conectados. El objetivo no es el ataque, sino la inteligencia de amenazas. Conocer tu entorno digital te permite identificar puntos ciegos en tu propia defensa o, desde una perspectiva ofensiva, los flancos expuestos de un objetivo.
El uso de herramientas como esta, ya sean las mencionadas o alternativas de código abierto como Kismet o Airodump-ng (parte de la suite Aircrack-ng), es crucial para la fase de reconocimiento. Permite desarrollar hipótesis sobre la seguridad de una red basándose en datos reales, no en suposiciones. Para cualquier profesional de la ciberseguridad o entusiasta del hacking ético, dominar estas herramientas de escaneo es un paso indispensable.
Clase en Vivo: Fortaleciendo el Arsenal Defensivo
El webinar fue solo la chispa. Para quienes sintieron la llamada a dominar las profundidades del hacking WiFi, "Security Temple" anunció una clase en vivo de cuatro días. Este no es un curso superficial; es una inmersión completa. Imagina cuatro días intensos desglosando técnicas avanzadas de ataque de diccionario, análisis de tráfico en tiempo real, y, lo más importante, el desarrollo e implementación de estrategias de defensa robustas. Una clase así te equipa con el conocimiento y la experiencia práctica para no solo entender cómo se ataca una red, sino cómo se defiende proactivamente.
Este tipo de formación avanzada es vital. Si buscas una certificación en ciberseguridad o simplemente quieres ser un profesional más competente, invertir en formación de calidad como la oferta de OSCP o cursos especializados en redes es el camino. El mercado laboral actual exige habilidades probadas, y una clase intensiva te acerca mucho más a ese nivel de maestría defensiva.
Seguridad WiFi: Personalización de Diccionarios y Contramedidas
Los atacantes de WiFi no suelen operar a ciegas. Un método común, el ataque de diccionario, depende de listas de contraseñas predefinidas. Sin embargo, los atacantes más astutos personalizan estos diccionarios. Investigan al objetivo, buscan información pública, nombres de mascotas, fechas importantes, y crean listas a medida. Esto aumenta drásticamente la probabilidad de éxito. La defensa contra esto es clara: contraseñas largas, complejas y únicas, preferiblemente gestionadas por un gestor de contraseñas. Además, protocolos de seguridad modernos como WPA3 ofrecen protecciones adicionales contra este tipo de ataques.
Nunca subestimes el poder de una contraseña bien elegida. Es la primera línea de defensa en gran parte del panorama de seguridad. Asegurarse de que tu red WiFi utilice los estándares de encriptación más recientes (WPA3, o WPA2 con AES como mínimo) y una contraseña que sea difícil de adivinar, incluso con diccionarios personalizados, es fundamental. La seguridad WiFi es un ciclo continuo de mejora: detectar, analizar, mitigar, repetir.
Veredicto del Ingeniero: ¿Defensa o Ilusión?
El conocimiento sobre hacking WiFi, adquirido a través de webinars o clases avanzadas, es una espada de doble filo. Puede ser la herramienta que permite a un profesional de la seguridad identificar y parchear vulnerabilidades antes de que sean explotadas, o puede ser el arma de un ciberdelincuente. La clave reside en la ética. Las herramientas y técnicas discutidas son poderosas. Utilizadas con autorización y con fines defensivos o de investigación ética, son invaluables. Utilizadas para invadir la privacidad o robar datos, son ilegales y moralmente reprobables.
Mi veredicto es claro: el conocimiento es poder. ¿Y qué haces con ese poder? La mentalidad de "blue team" (defensor) es, en última instancia, la más valiosa. Entender las tácticas ofensivas te convierte en un mejor defensor. Si te inclinas por el lado del atacante sin el debido respeto por la ética y la ley, te conviertes en parte del problema, no de la solución. El consejo es: aprende, pero aprende para proteger.
Arsenal del Operador/Analista WiFi
- Hardware Esencial:
- Adaptadores WiFi USB compatibles con modo monitor y inyección de paquetes (Ej: Alfa AWUS036NH, TP-Link TL-WN722N v1).
- Raspberry Pi (para despliegues portátiles o continuos).
- Software Clave:
- Suite Aircrack-ng: Indispensable para auditorías de redes WiFi (
airmon-ng,airodump-ng,aireplay-ng,aircrack-ng). - Kismet: Detector de redes inalámbricas, sniffer y sistema de detección de intrusos.
- Wireshark: Analizador de protocolos de red para tráfico capturado.
- Hashcat / John the Ripper: Para el cracking de contraseñas capturadas (archivos .cap/.hccapx).
- Metasploit Framework: Contiene módulos para la explotación de ciertas vulnerabilidades de red.
- Formación y Certificaciones:
- OSCP (Offensive Security Certified Professional): Demuestra habilidades prácticas en pentesting.
- cursos online especializados en redes y WiFi hacking ético en plataformas como Udemy, Coursera, o formaciones específicas de proveedores como Offensive Security.
- Libros como "The Wi-Fi Hacker's Handbook" o la documentación oficial de Aircrack-ng.
Taller Defensivo: Fortaleciendo Tu Red WiFi
- Audita Tu Red:
- Utiliza herramientas como Aircrack-ng (
airodump-ng) o Kismet en modo monitor con un adaptador compatible. - Identifica todas las redes WiFi visibles, incluyendo las no deseadas (rogue APs).
- Verifica el tipo de cifrado utilizado (WPA2/WPA3 es mandatorio).
- Fortalece Las Credenciales:
- Establece una contraseña de red WiFi robusta y única. Combina mayúsculas, minúsculas, números y símbolos. Evita información personal obvia.
- Si tu router lo soporta, habilita WPA3 o al menos WPA2 con cifrado AES. Evita WEP y WPA (TKIP).
- Cambia la contraseña por defecto del router (la de acceso a la administración).
- Configuración del Router:
- Deshabilita WPS (Wi-Fi Protected Setup) si no es estrictamente necesario, ya que es un vector de ataque conocido.
- Considera cambiar el SSID (nombre de la red) a algo genérico, pero no confíes en la ocultación del SSID como medida de seguridad principal; es fácilmente evitable.
- Mantén el firmware del router actualizado. Los fabricantes lanzan parches para vulnerabilidades descubiertas.
- Segmentación de Red:
- Si es posible, configura una red de invitados separada de tu red principal para dispositivos menos confiables (IoT, visitantes).
Preguntas Frecuentes
¿Es legal el hacking de WiFi?
Realizar pruebas de penetración en redes WiFi es legal únicamente si tienes permiso explícito del propietario de la red. Utilizar estas técnicas en redes ajenas sin autorización es ilegal y puede acarrear consecuencias legales graves.
¿Qué adaptador de red recomiendan para empezar?
Para iniciarse, adaptadores como el Alfa AWUS036NH o TP-Link TL-WN722N (v1) son opciones populares y bien soportadas por distribuciones Linux orientadas a la seguridad. Asegúrate de verificar la compatibilidad con tu sistema operativo.
¿Es suficiente con tener una contraseña fuerte para mi WiFi?
Una contraseña fuerte es crucial, pero no es la única capa de defensa. Implementar WPA3, mantener el firmware actualizado y considerar la segmentación de red (redes de invitados) son complementos esenciales para una seguridad WiFi robusta.
¿Qué es más seguro, 2.4 GHz o 5 GHz?
Ambas bandas tienen sus pros y contras. 5 GHz ofrece mayor velocidad y menos interferencia, pero menor alcance. 2.4 GHz tiene mejor alcance y penetración en obstáculos, pero es más susceptible a interferencias y es la banda más utilizada para ataques más antiguos. La seguridad (WPA2/WPA3) es más importante que la banda de frecuencia en sí.
¿Cómo protejo mis dispositivos IoT de ser un punto débil en mi red WiFi?
La mejor práctica es colocar los dispositivos IoT en una red de invitados separada. Esto los aísla de tus dispositivos principales (ordenadores, teléfonos). Además, cambia las contraseñas por defecto y actualiza su firmware regularmente si la opción está disponible.
Conclusiones y El Contrato: Tu Próximo Movimiento Defensivo
El webinar de "Security Temple" demostró que el mundo del hacking WiFi es complejo, fascinante y, sobre todo, un campo de batalla constante. Desde los adaptadores que vemos como meros accesorios hasta las herramientas que desvelan secretos, cada componente juega un rol. La ciberseguridad no es un estado, es un proceso continuo de aprendizaje y adaptación. Comprender las tácticas ofensivas es la base de cualquier defensa eficaz. No se trata de glorificar el ataque, sino de entenderlo para construir muros más altos y seguros.
El Contrato: Asegura Tu Perímetro Inalámbrico
Ahora es tu turno. Empieza por auditar tu propia red WiFi basándote en los pasos del taller defensivo. Identifica tu adaptador de red actual: ¿soporta modo monitor? Si no, considera actualizarlo. Investiga el firmware de tu router: ¿está al día? Y lo más importante, revisa tu contraseña de WiFi y la de administración. ¿Son lo suficientemente fuertes? Documenta tus hallazgos y las acciones que tomaste. Comparte tus experiencias y los desafíos que encontraste en los comentarios. ¿Qué herramientas utilizas para defender tu red? ¿Qué medidas adicionales implementas que no se mencionaron aquí? Demuestra tu compromiso con la defensa.
Este artículo, como todo en "Security Temple", tiene como objetivo equiparte con el conocimiento para prosperar en el panorama digital. La ciberseguridad, el hacking ético y la seguridad en redes son campos que requieren dedicación y aprendizaje constante. Si buscas profundizar, nuestros recursos están diseñados para guiarte.
Para contenido adicional y más inmersiones en el mundo de la ciberseguridad y el hacking WiFi, considera visitar nuestro canal de YouTube: Security Temple en YouTube. La formación continua es tu mejor arma defensiva.