The flickering cursor on the terminal was a lone sentinel in the pre-dawn gloom, each blinking pulse a question mark in the vast, silent network. Logs, usually a mundane chore, were tonight a tapestry of anomalies, whispers of a threat that shouldn't exist. This isn't about breaking in; it's about understanding how the enemy operates so the walls we build are impenetrable. Today, we dissect the Mariposa botnet, not to replicate its sins, but to learn from its ghosts and fortify our digital bastions.

The tale of Chris Davis and the Mariposa botnet, as chronicled in certain podcasts, offers a narrative arc familiar to anyone who's spent nights tracing malicious traffic: the unconventional path to expertise, the relentless hunt for a phantom, and the global impact of a single, pervasive threat. This isn't just a story; it's a case study in threat intelligence, incident response, and the critical nature of collaborative defense. We’ll peel back the layers, not to admire the attacker's technique, but to arm ourselves with the knowledge to detect, disrupt, and defend.
The Unconventional Path to Cybersecurity Expertise
Chris Davis's entry into cybersecurity wasn't through a traditional ivory tower. Leaving high school early, his journey was one of autodidacticism, driven by an insatiable curiosity for the inner workings of technology. This raw, unvarnished hunger for knowledge is often the bedrock of true security expertise. It emphasizes that talent isn't confined to academic pedigrees; it thrives in those who are intrinsically motivated to understand and dissect complex systems. His eventual role within the Canadian government, performing penetration tests and simulated attacks, is the practical application of this drive. These exercises are not merely tests of network resilience; they are opportunities to walk in the attacker's shoes, to understand their methodologies, and to proactively identify vulnerabilities before they are exploited.
Operation Curador: The Hunt for a Digital Ghost
In the digital underworld, adversaries often boast of their exploits, a critical mistake that fuels reconnaissance efforts. "Curador," as the narrative goes, was one such hacker who couldn't resist flaunting his malicious activities. This bravado, from a defensive standpoint, is a goldmine. It provides an entry point, a digital breadcrumb trail. Davis's pursuit of Curador wasn't a lone wolf operation; it was a testament to the power of coordinated efforts. Collaborating with international security agencies turned a single investigator's resolve into a formidable, multi-jurisdictional task force. The eventual arrest of Curador wasn't just a victory for law enforcement; it was a strong signal to the cybercriminal ecosystem: anonymity is fleeting, and accountability is inevitable. For defenders, this highlights the importance of threat intelligence sharing and maintaining open lines of communication with global partners. Unmasking an actor like Curador requires correlation of disparate data points, often spanning multiple networks and jurisdictions.
Mariposa Botnet: A Million-Strong Digital Contagion
The Mariposa botnet represented a threat of a different magnitude. Infecting over a million computers worldwide, it transcended individual hacker exploits to become a significant global infrastructure for cybercrime. A botnet of this scale is a complex organism, requiring sophisticated Command and Control (C2) infrastructure, extensive distribution networks, and a constant stream of malicious payloads. Davis's role in its neutralization underscores the intricate, often arduous, process of dismantling such operations. This involved not just identifying the threat, but tracing its command structure back to its operators, a feat that often requires advanced network forensics, malware analysis, and international legal cooperation. The operation’s success, leading to arrests in Spain, demonstrates the critical importance of deep technical analysis and persistent investigation to disrupt large-scale cyber operations. The sheer number of infected machines meant that understanding the propagation vectors, persistence mechanisms, and C2 communication was paramount to effective takedown.
Key Defensive Takeaways from the Mariposa Saga
1. Collaboration is Non-Negotiable
The Mariposa takedown, like many significant cyber victories, wasn't won by a single entity. It was a symphony of international law enforcement agencies, private cybersecurity firms, and dedicated researchers. In today's interconnected threat landscape, silos are deadly. Defenders must actively cultivate relationships and mechanisms for sharing threat intelligence, IoCs (Indicators of Compromise), and best practices. This collaborative framework allows for earlier detection, more effective response, and a unified front against adversaries who operate globally and without borders.
2. Persistence in Pursuit of Justice
The digital realm is vast, and cybercriminals often believe they can operate with impunity. The capture of individuals like Curador, and the operators behind Mariposa, serves as a powerful deterrent. It underscores that while anonymity might be sought, persistent investigation and coordinated action can unravel even the most carefully constructed digital disguises. For cybersecurity professionals, this translates to a mindset of relentless pursuit, always pushing to uncover the root cause and identify the actors behind malicious campaigns.
3. The Pervasive Reach of Modern Threats
A botnet like Mariposa, infecting millions, illustrates the systemic risk to our digital infrastructure. It’s not just about protecting one system; it’s about securing the entire ecosystem. This necessitates robust endpoint detection and response (EDR), network segmentation, strict access controls, and continuous monitoring. The impact of such widespread infections can cripple economies, disrupt critical services, and compromise sensitive data on a massive scale. Understanding the potential blast radius of such threats informs the prioritization of defensive measures.
Fortifying Our Digital Perimeter: Lessons for the Future
The narrative of Chris Davis and the Mariposa botnet is a stark reminder that the cybersecurity landscape is in constant flux. New threats emerge, and existing ones evolve with alarming speed. The core principles, however, remain evergreen: vigilance, expertise, and collaboration. To stay ahead, organizations must move beyond reactive defense and invest in proactive strategies. This includes:
- Advanced Threat Hunting: Proactively searching networks for signs of compromise that traditional security tools might miss.
- Robust Incident Response Planning: Having well-defined, practiced plans to contain and remediate breaches quickly.
- Continuous Learning: Staying abreast of the latest attack vectors, malware families, and defensive technologies.
- Cross-Border Cooperation: Building bridges with international law enforcement and security communities.
- Talent Development: Nurturing and retaining skilled cybersecurity professionals by providing them with the tools, resources, and challenging environment they need to succeed.
The digital battleground requires constant adaptation. The ghosts of botnets past serve as specters, reminding us of the stakes. By learning from these engagements, we can better prepare for the skirmishes of tomorrow and ensure our digital defenses are not just reactive, but resilient.
Veredicto del Ingeniero: ¿Vale la pena el análisis de casos?
Analizar casos como el de Mariposa es fundamental para cualquier profesional de la ciberseguridad. No se trata de romancear el lado oscuro, sino de extraer lecciones tácticas y estratégicas de las operaciones exitosas de desmantelamiento. Comprender cómo los defensores identificaron la infraestructura C2, analizaron el malware y coordinaron acciones transnacionales proporciona un conocimiento invaluable. Ignorar estas narrativas es como un médico que se niega a estudiar patologías; se condena a la ignorancia y a la ineficacia. La inversión de tiempo en diseccionar estas operaciones de alto nivel es un multiplicador de fuerza para cualquier equipo de defensa.
Arsenal del Operador/Analista
- Anatomía de un Ataque: Libros como "The Web Application Hacker's Handbook" o "Practical Malware Analysis" son esenciales para entender las tácticas ofensivas desde una perspectiva defensiva.
- Herramientas de Análisis Forense: Volatility Framework para análisis de memoria, Wireshark para análisis de tráfico de red, y herramientas de análisis de malware como Ghidra o IDA Pro.
- Plataformas de Threat Intelligence: Servicios como MISP (Malware Information Sharing Platform) o plataformas comerciales de inteligencia de amenazas para correlacionar IoCs.
- Herramientas de Pentesting Ético: Metasploit Framework, Burp Suite (Suite Pro para análisis avanzado), Nmap para reconocimiento. Comprender cómo operan estas herramientas desde el lado del atacante es clave para la defensa.
- Certificaciones: OSCP (Offensive Security Certified Professional) para entender las metodologías de ataque de forma práctica, y CISSP (Certified Information Systems Security Professional) para una visión holística de la seguridad.
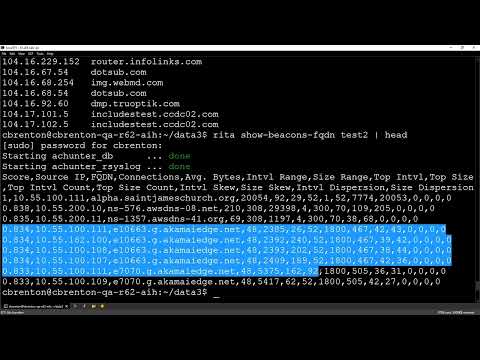
Taller Defensivo: Identificando el Tráfico de C2 de Botnets
La detección temprana de la comunicación C2 es vital para desmantelar botnets. Aquí se presentan pasos generales para identificar patrones anómalos:
- Análisis de Tráfico de Red:
- Monitorea conexiones salientes a IPs o dominios sospechosos. Herramientas como
Zeek (Bro)oSuricatapueden generar logs detallados de flujos de red. - Busca patrones de comunicación inusuales: tráfico a puertos no estándar, comunicaciones frecuentes a intervalos regulares (heartbeats), o volúmenes de datos anómalos.
- Ejemplo de consulta KQL (Azure Sentinel) para detectar conexiones a C2 conocidos:
SecurityEvent | where EventID == 4624 // Successful Logon | join kind=leftouter ( ThreatIntelligenceIndicator | where ThreatType =~ 'BotNet' or ThreatType =~ 'CommandAndControl' | project IOC = LowerCaseToken, TLPLevel ) on $left.AccountName == $right.IOC | where isnotempty(IOC) | project TimeGenerated, Computer, AccountName, IOC, TLPLevel
- Monitorea conexiones salientes a IPs o dominios sospechosos. Herramientas como
- Análisis de Malware:
- Si se identifica un posible huésped de botnet, realiza un análisis estático y dinámico para extraer la lista de dominios/IPs de C2 que el malware intenta contactar.
- Identifica los protocolos de comunicación: HTTP/HTTPS (a menudo disfrazados como tráfico web normal), DNS, o protocolos personalizados.
- Indicadores de Compromiso (IoCs):
- Crea reglas de detección basadas en IPs, dominios, hashes de archivos o claves de registro asociados a botnets conocidas.
- Utiliza feeds de IoCs actualizados y correlaciónalos con tus propios logs de seguridad.
- Monitoreo de DNS Amplification/Reflection:
- Las botnets a menudo abusan de los servicios DNS para realizar ataques DDoS. Monitorea picos anómalos en las consultas DNS salientes, especialmente aquellas dirigidas a servidores DNS abiertos.
Preguntas Frecuentes
¿Cómo puedo diferenciar el tráfico normal de un botnet? Busca anomalías: intervalos regulares de comunicación (heartbeats), conexiones a IPs o dominios no estándar, volúmenes de datos inusuales, o uso de protocolos poco comunes para el contexto del host.
¿Qué papel juega el análisis de memoria en la detección de botnets? El análisis de memoria puede revelar procesos maliciosos residentes en RAM, rastrear las conexiones de red del malware y extraer configuraciones o IoCs que no están presentes en el disco.
¿Es posible eliminar completamente una botnet? Eliminar completamente una botnet es extremadamente difícil, ya que los operadores pueden reconfigurarla o crear nuevas instancias. El objetivo principal es desmantelar su infraestructura de C2 y neutralizar su capacidad operativa.
El Contrato: Asegura tu Perímetro Digital
Hemos desmantelado la narrativa de Mariposa, exponiendo no solo las tácticas del adversario, sino también las estrategias defensivas que llevaron a su caída. Ahora, el contrato es contigo: ¿tu red exhibe alguna de las debilidades que permitieron a Mariposa prosperar? Implementa al menos una de las técnicas de detección de tráfico C2 discutidas o revisa tus políticas de intercambio de inteligencia con socios. Documenta tu hallazgo o tu plan de mejora. El silencio en la red es a menudo una ilusión, y solo la vigilancia activa puede desvelar las amenazas ocultas. Demuestra tu compromiso defensivo.
```json
{
"@context": "https://schema.org",
"@type": "BlogPosting",
"headline": "Anatomy of the Mariposa Botnet Takedown: A Defensive Deep Dive",
"image": {
"@type": "ImageObject",
"url": "URL_DEL_POST_IMAGEN",
"description": "Ilustración abstracta de la estructura de una botnet global con nodos interconectados y un escudo protector."
},
"author": {
"@type": "Person",
"name": "cha0smagick"
},
"publisher": {
"@type": "Organization",
"name": "Sectemple",
"logo": {
"@type": "ImageObject",
"url": "URL_DEL_LOGO_SECTEMPLE"
}
},
"datePublished": "2023-10-27",
"dateModified": "2023-10-27",
"mainEntityOfPage": {
"@type": "WebPage",
"@id": "URL_DEL_POST_ACTUAL"
},
"description": "Un análisis defensivo profundo de la Mariposa Botnet, explorando las lecciones de ciberseguridad, colaboración y desmantelamiento de amenazas.",
"keywords": "botnet, cybersecurity, threat hunting, incident response, Mariposa botnet, defense, C2 communication, Chris Davis, hacking, digital forensics"
}