The digital realm is a shadow-drenched alleyway, and tonight, we're not just walking through it; we're mapping its every dark corner. The hum of servers, the flicker of compromised indicators – this is the symphony of an ongoing digital conflict. Today, we peel back the layers of sophisticated network techniques, focusing on the elusive "FQDN Beacons," a method that can leave even seasoned defenders fumbling in the dark. This isn't about cracking systems; it's about dissecting the enemy's playbook to build an impenetrable fortress. We're diving deep into the mechanics of threat hunting, turning the attacker's art into our shield.
This analysis is brought to you by cha0smagick, your guide through the labyrinthine world of cybersecurity, operating from the shadows of Sectemple. Expect no easy answers, only the grim, methodical truth behind the threats that loom in the digital ether. We'll dissect the anatomy of FQDN beacons, understand their purpose, and most importantly, forge strategies to detect and neutralize them before they become catastrophic breaches. This is a critical deep-dive, essential for any blue team operative looking to elevate their game.
The Shadow Play: Understanding FQDN Beacons
In the intricate dance of network reconnaissance and command and control (C2), attackers constantly seek methods to blend in, to become ghosts in the machine. One potent technique involves Weaponizing the Domain Name System (DNS) itself. FQDN (Fully Qualified Domain Name) beacons, at their core, are a form of DNS tunneling or covert communication. Attackers leverage DNS queries to exfiltrate small amounts of data or to send commands to compromised hosts, masquerading these malicious transmissions as legitimate network traffic.
Imagine a silent signal, a whisper carried on the wind of global network requests. An attacker crafts a series of DNS queries, each containing a piece of data encoded within a subdomain or the domain name itself. The victim machine, infected with malware, makes these requests to a domain controlled by the attacker. The attacker's infrastructure then processes these queries, extracting the encoded information. Conversely, the attacker can embed commands within DNS responses, effectively controlling the compromised host without direct, detectable C2 channels.
Anatomy of a Beacon: How They Work
The elegance of FQDN beacons lies in their deceptive simplicity and their grounding in legitimate network protocols. Here's a breakdown of the mechanics:
- Encoding Data: Attackers encode data (commands, exfiltrated files, system information) into strings that are valid as DNS subdomains or entire domain names. This can involve simple character substitution, Base64 encoding, or more complex transformations. For example, a query for
SGVsbG8gV29ybGQ=.attacker-domain.commight be a Base64 encoded message. - DNS Queries: The malware on the compromised host initiates these specially crafted DNS queries. These queries are directed towards authoritative DNS servers controlled by the attacker, often through a series of recursive lookups that eventually reach the attacker's infrastructure.
- Data Exfiltration/Command Insertion:
- Exfiltration: As the DNS query traverses the network, the payload is embedded within the query itself. The attacker's DNS server receives these queries and extracts the encoded data.
- Command Insertion: In the reverse process, the attacker embeds commands into the DNS response. This could be within the DNS TXT record, CNAME, or even subtly within the IP address or other record types, depending on the attacker's sophistication and chosen tunneling method.
- Low Bandwidth, High Stealth: These methods are typically low-bandwidth, meaning they are not suitable for large file transfers. However, this limitation is a feature for stealth. Small, intermittent data transfers blend easily into the background noise of normal network activity, making detection a formidable challenge.
The Attacker's Edge: Why FQDN Beacons are Dangerous
From a defender's perspective, FQDN beacons present a multifaceted threat:
- Stealth and Evasion: They leverage a fundamental, high-volume protocol (DNS) that is often permitted through firewalls with minimal inspection. This makes them incredibly difficult to distinguish from legitimate traffic.
- Resilience: DNS infrastructure is inherently distributed and resilient. Attackers can set up multiple fallback domains and servers, making it harder to shut down their C2 operations completely.
- Bypassing Traditional Security: Standard network intrusion detection systems (IDS) and firewalls may not inspect the payload of DNS queries deeply enough to identify encoded data or malicious intent.
- Persistent Access: Once established, FQDN beacons can provide a stable, albeit slow, channel for attackers to maintain access, issue commands, and exfiltrate sensitive data over extended periods.
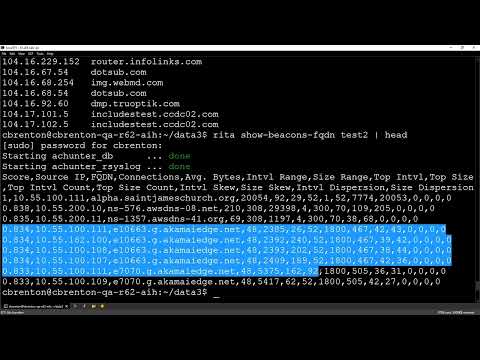
Threat Hunting: Strategies for Detection and Mitigation
Hunting for FQDN beacons requires a shift in focus from traditional network traffic analysis to the granular inspection of DNS logs and the behavior of endpoints. It's about looking for anomalies, deviations from the norm, and patterns that scream "malice" in a sea of legitimate requests.
Hypothesis: Malicious DNS Behavior is Present
Our initial hypothesis is that compromised hosts are utilizing FQDN beacons for covert communication, aiming to exfiltrate data or receive commands, by sending unusually structured or voluminous DNS queries to specific domains or IPs.
Phase 1: Log Collection and Baseline Establishment
The foundation of effective threat hunting lies in comprehensive data. You cannot hunt what you cannot see.
- DNS Server Logs: These are your primary source. Collect logs from internal DNS servers, forwarders, and any security appliances that inspect DNS traffic. Key fields to look for include:
- Timestamp
- Source IP address (of the querying client)
- Destination IP address (of the DNS server being queried)
- Query Type (A, AAAA, TXT, CNAME, MX, etc.)
- Query Name (the FQDN being requested)
- Response Code (NXDOMAIN, NOERROR, etc.)
- Response Data (if available and logged)
- Endpoint Logs: Process execution logs, network connection logs (e.g., Sysmon Event ID 3, 11), and application logs can provide context about which processes are initiating DNS queries.
- Firewall/Proxy Logs: While often limited in DNS payload inspection, these can show connections to suspicious DNS servers or unusual traffic patterns associated with DNS requests.
Establishing a Baseline: Before hunting, you must understand what "normal" looks like. Analyze typical DNS query volumes, query types, and the FQDNs that internal hosts commonly resolve. This baseline is critical for identifying outliers.
Phase 2: IoCs and Detection Techniques
Now, we translate our hypothesis into actionable detection methods. We're looking for the fingerprints of the adversary.
- Unusual Subdomain Depth and Length: Attackers often encode data by creating long, multi-level subdomains. Look for queries with an excessive number of dots or exceptionally long FQDNs.
let avgSubdomainDepth = avg(strlen(query_name) - strlen(tld)); // Example KQL for Azure Sentinel to find deeply nested subdomains DnsEvents | extend DomainParts = split(Name, '.') | extend SubdomainDepth = array_length(DomainParts) - 2 // -2 for TLD and root domain | summarize Count = count() by DnsServerIp, RemoteIP, SubdomainDepth | where SubdomainDepth > 5 // Adjust threshold based on baseline | project DnsServerIp, RemoteIP, SubdomainDepth, Count - High Volume of NXDOMAIN Responses: While legitimate DNS can result in NXDOMAIN (non-existent domain), a disproportionately high rate from a specific client or to a peculiar domain can indicate brute-force attempts at guessing or probing for a C2 channel.
- Anomalous Query Types: While A and AAAA records are standard, attackers might leverage less common types like TXT, NULL, or custom DNS records for data exfiltration if their infrastructure supports it. A sudden surge in these types from a particular host is suspicious.
- Entropy Analysis of FQDNs: Attackers often use pseudo-random or encoded strings. High entropy within subdomain names suggests randomness rather than human-readable hostnames. Tools can be used to calculate entropy scores for FQDNs.
- Beaconing Patterns: Analyze the timing of DNS requests. Are they occurring at regular intervals (e.g., every 60 seconds), or in bursts that don't align with normal user activity? This periodicity can be a strong indicator of automated C2 communication.
- Geographic Anomalies: If your organization's typical DNS traffic is directed towards specific regional servers, sudden spikes in queries to domains hosted in unusual geographic locations can warrant investigation.
- Domain Blacklisting and Reputation: While basic, checking queried domains against threat intelligence feeds and blacklists is a fundamental step. However, advanced attackers use newly registered domains (NRDs) or compromised legitimate domains, making this less effective in isolation.
Phase 3: Mitigation and Containment
Detection is only half the battle. Once an FQDN beacon is identified, swift action is paramount.
- Network Segmentation: Isolate the suspected compromised host(s) from the rest of the network to prevent lateral movement and further data exfiltration.
- DNS Sinkholing: Redirect malicious FQDNs to a controlled sinkhole server. This can prevent the malware from communicating with the attacker's C2 infrastructure and provide valuable intelligence on the scope of the infection.
- Endpoint Remediation: Remove the identified malware from the compromised host. This often involves in-depth forensic analysis to ensure all malicious components are eradicated.
- DNS Firewalling/Policy Enforcement: Implement stricter DNS policies. Block queries to known malicious domains, enforce query length limits, restrict uncommon record types for untrusted clients, and consider using DNS security solutions that perform deep packet inspection.
- Process Monitoring: Use endpoint detection and response (EDR) solutions to monitor process behavior, especially network connections originating from unusual processes or exhibiting anomalous DNS query patterns.
Veredicto del Ingeniero: ¿Vale la pena adoptar estas técnicas de Hunting?
Absolutely. Ignoring the potential for DNS-based C2 and data exfiltration is akin to leaving your castle gates wide open. FQDN beacons are not theoretical; they are a persistent threat employed by sophisticated adversaries, from APTs to advanced ransomware groups. The investment in DNS logging, log analysis tools (like SIEMs or dedicated threat hunting platforms), and the training of your security personnel to recognize these patterns is not an expense – it's a critical investment in organizational resilience. The trade-off for the effort is a significant reduction in the attack surface and a heightened ability to detect and respond to some of the most insidious threats. The time to hunt is always now.
Arsenal del Operador/Analista
- SIEM Solutions: Splunk Enterprise Security, Azure Sentinel, ELK Stack (Elasticsearch, Logstash, Kibana)
- Endpoint Detection and Response (EDR): CrowdStrike Falcon, Microsoft Defender for Endpoint, SentinelOne
- Network Traffic Analysis (NTA): Zeek (Bro), Suricata, Wireshark
- Threat Intelligence Platforms (TIP): MISP, Anomali ThreatStream
- Specialized DNS Security Tools: Infoblox, Cisco Umbrella, Quad9
- Books: "The Art of Network Security Monitoring" by Richard Bejtlich, "Practical Threat Hunting" by Kyle Rainey
- Certifications: GIAC Certified Incident Handler (GCIH), Certified Threat Intelligence Analyst (CTIA), Offensive Security Certified Professional (OSCP) - Yes, knowing offensive techniques is key to defending.
Taller Práctico: Fortaleciendo tu Defensa DNS
Let's craft a basic detection script. This example uses Python to analyze DNS logs for common indicators of FQDN beaconing. It's a starting point, not a definitive solution, but illustrates the concepts.
- Set up your environment: Ensure you have Python installed and a way to feed your DNS logs (e.g., a CSV file exported from your DNS server).
- Install necessary libraries: You might need
dnspythonfor more advanced DNS parsing and potentially libraries for entropy calculation. For this basic example, we'll focus on string manipulation. - Scripting the analysis:
import re import collections def analyze_dns_logs(log_file_path, min_subdomain_depth=4, max_fqdn_length=100, entropy_threshold=3.0): """ Analyzes DNS logs for potential FQDN beacon indicators. Requires logs formatted such that each line contains at least: 'timestamp, client_ip, query_name, query_type' """ suspicious_queries = collections.defaultdict(list) entropy_calculator = EntropyCalculator() # Assume EntropyCalculator class is defined elsewhere try: with open(log_file_path, 'r') as f: for i, line in enumerate(f): # Basic log parsing: adjust regex as needed for your log format match = re.match(r'(\d{4}-\d{2}-\d{2} \d{2}:\d{2}:\d{2}), ?([\d\.]+), ?([^,]+), ?([^,]+)', line) if not match: print(f"Skipping malformed line {i+1}: {line.strip()}") continue timestamp, client_ip, query_name, query_type = match.groups() # Indicator 1: Excessive Subdomain Depth domain_parts = query_name.split('.') # We subtract 2 for the TLD and the root domain (e.g., example.com) # This logic might need tuning based on your domain structures subdomain_depth = len(domain_parts) - 2 if subdomain_depth > min_subdomain_depth: suspicious_queries[client_ip].append(f"Depth={subdomain_depth} ({query_name})") # Indicator 2: Excessive FQDN Length if len(query_name) > max_fqdn_length: suspicious_queries[client_ip].append(f"Length={len(query_name)} ({query_name})") # Indicator 3: High Entropy (Requires EntropyCalculator implementation) # For simplicity, let's assume we're looking at the subdomain part before the TLD if len(domain_parts) > 2: subdomain_part = ".".join(domain_parts[:-2]) if subdomain_part: # Ensure there's a subdomain part to analyze try: entropy = entropy_calculator.calculate(subdomain_part) if entropy > entropy_threshold: suspicious_queries[client_ip].append(f"HighEntropy={entropy:.2f} ({query_name})") except Exception as e: print(f"Error calculating entropy for {subdomain_part}: {e}") except FileNotFoundError: print(f"Error: Log file not found at {log_file_path}") return except Exception as e: print(f"An unexpected error occurred: {e}") return # Report findings print("\n--- Suspicious DNS Activity Report ---") if not suspicious_queries: print("No immediate suspicious activity detected based on current criteria.") else: for ip, indicators in suspicious_queries.items(): print(f"Client IP: {ip}") for indicator in indicators: print(f" - {indicator}") print("-" * 20) # Placeholder for an Entropy Calculator class class EntropyCalculator: def calculate(self, text): from math import log, fsum if not text: return 0 text = text.lower() # Normalize prob = collections.Counter(text) total = len(text) # Shannon entropy: H(X) = -sum(p(x_i) * log2(p(x_i))) entropy = -fsum(count/total * log(count/total, 2) for count in prob.values()) return entropy # --- Example Usage --- # Create a dummy log file for testing dummy_log_content = """ 2023-10-27 10:00:01, 192.168.1.100, google.com, A 2023-10-27 10:00:02, 192.168.1.101, example.com, A 2023-10-27 10:00:03, 192.168.1.100, very.long.subdomain.encoded.data.example.com, A 2023-10-27 10:00:04, 192.168.1.102, example.com, A 2023-10-27 10:00:05, 192.168.1.101, this.is.another.deeply.nested.subdomain.beacon.example.com, A 2023-10-27 10:00:06, 192.168.1.100, google.com, A 2023-10-27 10:00:07, 192.168.1.103, verylongfqdnstringthatisintentionallymadeextralongtoexceedstandardlimitsandtestlimits.attackerdomain.net, A 2023-10-27 10:00:08, 192.168.1.101, data.f0r.exfil.com, TXT 2023-10-27 10:00:09, 192.168.1.104, normal.domain.net, A 2023-10-27 10:00:10, 192.168.1.103, a1b2c3d4e5f67890......longencodedstring.attacker.io, A """ dummy_log_file = "dns_sample.log" with open(dummy_log_file, "w") as f: f.write(dummy_log_content) # Run the analysis analyze_dns_logs(dummy_log_file, min_subdomain_depth=4, max_fqdn_length=70, entropy_threshold=2.5) - Integrate and Automate: Feed live DNS logs into this script or a more sophisticated version running on your SIEM. Set up alerts for IPs triggering multiple indicators.
Frequently Asked Questions
What is the primary goal of an FQDN beacon?
The primary goal is to establish a covert communication channel for commands or data exfiltration by leveraging DNS queries, aiming for stealth and evasion of traditional security controls.
Are there legitimate uses for DNS tunneling?
Yes, DNS tunneling can be used for legitimate purposes like troubleshooting, network monitoring, or secure access in highly restricted environments. However, its structure and usage patterns often differ significantly from malicious implementations.
How can I differentiate between malicious and legitimate DNS tunneling?
Key indicators include the entropy of queried names/subdomains, unusual query volumes, non-standard query types, periodicity of requests, and the reputation of the queried domain. Establishing a strong baseline of normal traffic is crucial.
Is DNS tunneling slow?
Generally, yes. DNS has inherent limitations in terms of the amount of data that can be transmitted per query/response. It's typically used for command and control or small data chunks, not large file transfers.
What is the role of TXT records in DNS beaconing?
TXT records are commonly used because they are designed to hold arbitrary text strings, making them suitable for embedding larger amounts of data or commands compared to other record types.
El Contrato: Secure Your DNS Perimeter
The digital shadows are deep, and FQDN beacons are just one of the phantoms lurking within. Your enemy isn't static; they adapt. Your defenses must do the same. This isn't about chasing every anomaly; it's about building a robust, layered detection strategy that focuses on the indicators of compromise that truly matter. Fortify your DNS infrastructure. Log everything. Analyze intelligently. Hunt relentlessly. The compromise of your network might be just one DNS query away. Are you ready to prevent it?




