The flickering glow of the terminal screen cast sharp shadows across the silenced room. Logs, usually a monotonous stream of routine operations, were whispering now, hinting at activities that defied the established order. In this digital theater of shadows and whispers, a lone operator hunts. Not for glory, but for the elusive ghost in the machine – the reverse shell. Today, we dissect a formidable tool, not to wield its power carelessly,, but to understand its anatomy and, more importantly, to build the bulwarks that repel its intrusion. This is not a siren song for aspiring attackers; it's a battle plan for the defenders, an exposé of the enemy's playbook.
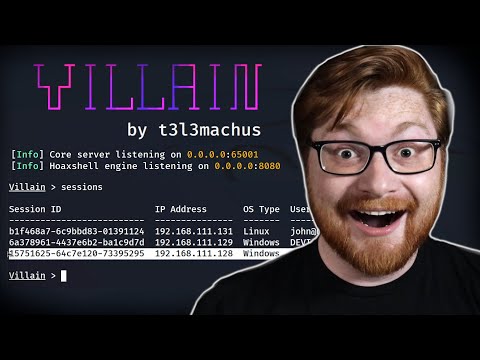
The digital underworld is a complex ecosystem, and understanding its apex predators is paramount to effective defense. Among these, the reverse shell stands out. It’s a fundamental technique, a privileged whisper from a compromised host back to the attacker's command and control (C2) server. While often discussed in the context of offensive operations, its true value to a security professional lies in comprehension – knowing how it works is the first step to detecting and neutralizing it. This deep dive focuses on "Villain," a tool that exemplifies the power and potential of reverse shells, analyzed not for its exploitation prowess, but for the defensive insights it provides.
Understanding the nuances of reverse shells is crucial for anyone involved in cybersecurity, from bug bounty hunters meticulously probing for weaknesses to incident responders sifting through the aftermath of an intrusion. It’s about recognizing the digital fingerprints an attacker leaves behind, the subtle shifts in network traffic, and the unusual process behavior that signals a compromised system.
Dissecting Villain: Anatomy of a Reverse Shell Tool
Villain, developed by t3l3machus, is a powerful, multi-platform reverse shell generator designed for penetration testing and red teaming environments. Its primary function is to create sophisticated and evasive reverse shells that can bypass common security controls. However, for the blue team, Villain serves as a pedagogical tool. By examining its capabilities, we can anticipate attacker methodologies and fortify our defenses accordingly.
Shellcrafting: The Art of Payload Generation
At its core, Villain excels at "shellcrafting" – the process of generating custom payloads. It offers a variety of shell types, including:
bash: For Linux/macOS environments.powershell: For Windows systems.python: Cross-platform scripting.netcat: A classic network utility.socat: A more advanced network relay utility.
The tool allows for customization of host, port, and even the encryption method used for communication. This adaptability is what makes it a threat, and understanding these configurable parameters allows defenders to tailor their detection signatures.
Evasion Techniques: Bypassing the Gatekeepers
Attackers using Villain will often leverage its features to bypass intrusion detection systems (IDS), firewalls, and antivirus software. Key techniques include:
- Encryption: Villain supports various encryption protocols (e.g., AES) to obfuscate the shell traffic, making it appear as benign data to network monitoring tools.
- Staged Payloads: Smaller initial payloads connect back to a listener, which then delivers the larger, more functional shell. This reduces the initial footprint and can evade signature-based detection.
- Multi-protocol Support: The ability to use standard protocols like HTTP/HTTPS for C2 can help blend traffic with legitimate web activity.
Practical Defensive Strategies Against Reverse Shells
The mere existence of tools like Villain underscores the need for robust, multi-layered security. Here’s how to harden your environment:
Network Segmentation and Firewalling
Principle: Limit the blast radius.
Implement strict network segmentation. Isolate critical assets on separate network segments with granular firewall rules. Prevent any outbound connections from internal networks to untrusted external IPs unless explicitly authorized. Regularly audit firewall rules to remove unnecessary open ports or overly permissive outbound policies.
Intrusion Detection and Prevention Systems (IDPS)
Principle: Watch the traffic.
Deploy and meticulously configure IDPS solutions. Develop custom signature rules to detect known Villain payloads or common reverse shell patterns. Monitor for unusual outbound connections on non-standard ports or unexpected protocols. Behavior-based anomaly detection is also critical here, flagging deviations from normal network traffic patterns.
Endpoint Detection and Response (EDR)
Principle: Monitor the endpoint.
EDR solutions provide deep visibility into endpoint activity. Deploy EDR agents capable of monitoring process creation, network connections, and file system modifications. Develop detection logic (e.g., KQL queries for Microsoft Defender for Endpoint) to identify suspicious process execution (like `powershell.exe` or `bash` spawning network connections), unusual command-line arguments, or the download/execution of suspicious scripts.
Least Privilege and Application Whitelisting
Principle: Deny by default.
Enforce the principle of least privilege for users and service accounts. Prevent non-administrative users from executing unauthorized scripts or applications. Implement application whitelisting to ensure only approved executables can run on endpoints. This significantly hinders the execution of downloaded payloads.
Regular Log Analysis and Threat Hunting
Principle: Seek the unseen.
Comprehensive logging is vital. Collect logs from endpoints, firewalls, IDPS, and proxies. Regularly analyze these logs for suspicious indicators. Proactively hunt for threats by searching for anomalies such as:
- Unusual outbound connections from servers.
- Processes making network connections that are not their typical behavior.
- Execution of scripting engines (PowerShell, Python, Bash) with suspicious arguments or network destinations.
- Unexpected file creations or modifications in system directories.
Arsenal of the Defender
To effectively counter threats like those posed by Villain, an operator needs the right tools and knowledge. Investing in these resources is not a luxury; it's a necessity for survival in the modern threat landscape.
- SIEM Solutions: Splunk, ELK Stack, QRadar - for centralized logging and analysis.
- EDR Platforms: CrowdStrike, SentinelOne, Microsoft Defender for Endpoint - for deep endpoint visibility and response.
- Network Traffic Analysis (NTA) Tools: Zeek (Bro), Suricata - for inline traffic inspection and alerting.
- Threat Intelligence Platforms (TIPs): To stay updated on emerging threats and attacker TTPs.
- Training and Certifications: Courses like Hack The Box's CPTS (Certified Penetration Testing Specialist), SANS FOR500 (Windows Forensic and Incident Response), or offensive certifications like OSCP (Offensive Security Certified Professional) to understand attacker methods from the inside out. Acquiring these certifications often involves significant investment, with courses like CPTS representing a key step in understanding offensive TTPs for defense, and specialized training like C# C2 Development from Zero-Point Security highlighting the sophistication of attacker tooling.
- Books: "The Web Application Hacker's Handbook" (though focused on WAH, its principles of understanding attack vectors are universal), and "Practical Threat Hunting: Analysis of Network Traffic".
Veredicto del Ingeniero: Villain and the Evolving Threat Landscape
Villain is a testament to the continuous innovation within the offensive security community. Its ability to generate seemingly innocuous yet highly functional reverse shells presents a significant challenge. However, for the defender, it's a valuable learning opportunity. By dissecting its components, understanding its evasion tactics, and implementing the defensive strategies outlined above, organizations can significantly bolster their resilience against such threats. The key takeaway is that understanding the offense is an indispensable part of building a formidable defense. Tools like this are why continuous threat hunting, robust endpoint security, and strict network controls are non-negotiable.
Taller Práctico: Hunting for Suspicious PowerShell Activity
This workshop focuses on detecting the execution of potentially malicious PowerShell scripts, a common vector for reverse shells.
- Access Logs: Ensure PowerShell script block logging is enabled on your Windows endpoints. This can be configured via Group Policy (Computer Configuration -> Policies -> Administrative Templates -> Windows Components -> Windows PowerShell -> Turn on Module Logging). Ensure these logs are forwarded to your SIEM.
-
Identify Suspicious Commands: Within your SIEM, search for events where `powershell -nop -w hidden -c` or similar obfuscated execution patterns appear. Look for commands that involve network connections (`Invoke-WebRequest`, `TCPClient`, `Sockets`), code execution, or downloading content from external sources.
DeviceProcessEvents | where FileName =~ "powershell.exe" | where ProcessCommandLine has_any ("-nop", "-w", "hidden", "-c", "IEX", "Invoke-Expression", "Invoke-WebRequest", "DownloadString") | project Timestamp, DeviceName, FileName, ProcessCommandLine, InitiatingProcessFileName, InitiatingProcessCommandLine -
Analyze Network Connections: Correlate process execution logs with network connection logs. Look for PowerShell processes initiating outbound connections to unusual or known malicious IP addresses/domains.
DeviceNetworkEvents | where InitiatingProcessFileName =~ "powershell.exe" | where RemoteIP !in ("192.168.0.0/16", "10.0.0.0/8", "172.16.0.0/12") // Exclude private IP ranges | project Timestamp, DeviceName, InitiatingProcessFileName, InitiatingProcessCommandLine, RemoteIP, RemotePort - Investigate Further: If a suspicious event is found, investigate the parent process (`InitiatingProcessFileName`). Was it spawned by a legitimate application, or by another suspicious process? Collect the full script block content if available for deeper analysis.
Preguntas Frecuentes
-
Q: ¿Cómo puede un atacante usar Villain para obtener acceso persistente?
A: Los atacantes pueden combinar Villain con técnicas de persistencia, como el registro de tareas programadas, servicios de Windows o WMI eventos, para re-establecer conexiones de reverse shell si son interrumpidas. -
Q: ¿Qué diferencia a Villain de otras herramientas de reverse shell?
A: Villain se destaca por su interfaz amigable, su capacidad para generar shells multiplataforma y su enfoque en la ofuscación y evasión, lo que lo hace más difícil de detectar que herramientas más rudimentarias. -
Q: ¿Es posible detectar el tráfico cifrado de Villain?
A: Aunque el cifrado dificulta la inspección de contenido, los administradores de red pueden detectar conexiones inusuales (IP de destino, puertos, patrones de tráfico anómalos) e investigar los procesos que las inician en el host.
El Contrato: Fortalece tu Perímetro Contra Shells Inesperados
Tu misión, si decides aceptarla, es realizar un ejercicio de simulación. Utilizando un entorno de laboratorio controlado (como una máquina virtual aislada o un entorno de pentesting certificado), intenta configurar y lanzar una reverse shell básica con una herramienta de tu elección (incluso una simple de Netcat). Luego, enfócate en detectar esa conexión desde el "lado defensor". Configura un firewall básico y monitoriza las conexiones de red de la máquina víctima. ¿Cuánto tiempo te tomó detectarla? ¿Qué indicadores fueron clave? Comparte tus hallazgos y los desafíos que enfrentaste en los comentarios. La defensa eficaz comienza con el conocimiento del adversario.

No comments:
Post a Comment