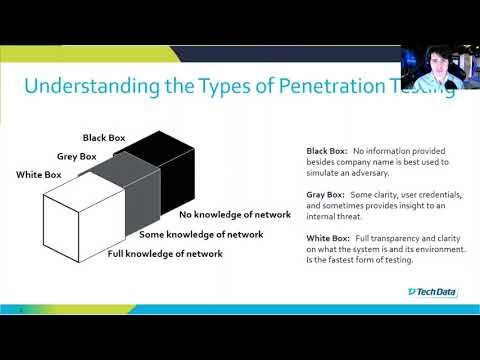
The digital battlefield is a murky place. Systems whisper with exploitable flaws, secrets lie buried in misconfigurations, and the silence of a network can often mask a lurking threat. In this environment, understanding the tools and tactics at your disposal is not just an advantage; it's a prerequisite for survival. Today, we dissect two critical methodologies that form the bedrock of offensive security validation: Vulnerability Assessment (VA) and Penetration Testing (PT).
Many equate these terms, lumping them into a single "security check." This is a rookie mistake, a sure sign of an immature security program. While both aim to identify weaknesses, their scope, depth, and ultimate objectives diverge significantly. Think of it as the difference between a doctor taking your temperature and a surgeon performing a complex operation. Both are medical actions, but their invasiveness, diagnostic power, and desired outcome are worlds apart.
For those on the front lines, whether defending turf or probing enemy lines, grasping these distinctions is paramount. A VA shines a spotlight on potential issues, flagging them for attention. A PT, on the other hand, is an active assault, attempting to leverage those flaws, much like a seasoned attacker would, to gauge the true blast radius of a breach.
Table of Contents
- Understanding Vulnerability Assessment
- Penetration Testing: The Offensive Edge
- Key Differences: A Head-to-Head
- Vulnerability Assessment Methodology
- Penetration Testing Methodology
- Choosing the Right Approach
- Engineer's Verdict: Worth the Investment?
- Operator's Arsenal
- Practical Guide: Simulating an Attack
- Frequently Asked Questions
- The Contract: Securing Your Perimeter
Understanding Vulnerability Assessment
A Vulnerability Assessment is, at its core, an audit. It's a systematic review designed to identify, quantify, and prioritize vulnerabilities within an organization's systems and applications. Think of it as a detailed, automated sweep across your digital estate. Tools like Nessus, OpenVAS, or Qualys are the workhorses here, diligently scanning networks, servers, workstations, and applications for known vulnerabilities, misconfigurations, and policy violations.
The output of a VA is typically a report listing discovered vulnerabilities, often categorized by severity (e.g., Critical, High, Medium, Low). It tells you *what* is wrong. It highlights that port 22 is open with an outdated SSH version, or that a web application is susceptible to SQL injection based on banner information. However, it stops short of verifying if these vulnerabilities are actually exploitable in your specific environment, or if a chain of lesser vulnerabilities could lead to a significant compromise.
"A vulnerability is a weakness. An exploit is the act of leveraging that weakness for unauthorized access or control."
Vulnerability Assessments are essential for maintaining a baseline understanding of your security posture. They are cost-effective for broad coverage and are excellent for compliance requirements where simply knowing about potential issues is sufficient. However, for an attacker, this report is just a shopping list of potential targets. They still need to do the heavy lifting of confirming exploitability.
Penetration Testing: The Offensive Edge
Penetration Testing, often dubbed "pentesting," goes beyond mere identification. It's an authorized, simulated cyberattack on your systems, performed to evaluate their security by actively exploiting vulnerabilities. Professional penetration testers, much like the black hats they mimic, aim to breach defenses, gain access to sensitive data, and demonstrate the real-world impact of security weaknesses. The goal isn't just to find vulnerabilities, but to prove how they can be weaponized.
A PT is a hands-on, often manual, process that simulates the tactics, techniques, and procedures (TTPs) of real-world adversaries. It involves reconnaissance, scanning, gaining initial access, escalating privileges, lateral movement, and potentially exfiltrating data. The report from a PT details not only the vulnerabilities found but also how they were exploited, the pathways to compromise, and the potential business impact. It answers the question: *What could an attacker actually do with these flaws?*
A comprehensive penetration test can uncover vulnerabilities missed by automated scans, like business logic flaws, complex chained exploits, or instances where a combination of low-severity issues creates a critical pathway for attackers. It provides a much deeper, more actionable insight into an organization's true resilience against targeted attacks. This is where the true value for an offensive security professional lies – understanding the exploitability and impact.
Key Differences: A Head-to-Head
Let's break down the core distinctions:
- Objective: VA aims to identify and catalogue vulnerabilities. PT aims to exploit vulnerabilities to assess real-world risk.
- Methodology: VA is largely automated, using scanners. PT is a mix of automated tools and intensive manual effort, mimicking attacker behavior.
- Depth: VA provides breadth (identifying many potential issues). PT provides depth (confirming exploitability and impact of selected issues).
- Scope: VA typically covers a wider range of systems, scanning for known signatures. PT often focuses on specific attack vectors or critical assets, attempting to break through.
- Output: VA reports a list of vulnerabilities with severity ratings. PT reports on successful exploits, compromised systems, and business impact, alongside vulnerabilities.
- Verification: VA relies on vulnerability signatures. PT involves active exploitation and verification of access.
Vulnerability Assessment Methodology
The standard VA process generally follows these stages:
- Planning: Define the scope, objectives, and systems to be assessed.
- Scanning: Utilize automated tools (e.g., Nessus, Qualys, OpenVAS) to scan networks, hosts, and applications for known vulnerabilities, misconfigurations, and policy violations. This can include authenticated (credentialed) scans for deeper insights or unauthenticated scans for an external attacker's perspective.
- Analysis: Review scan results, eliminate false positives, and prioritize identified vulnerabilities based on severity, asset criticality, and threat intelligence.
- Reporting: Generate a detailed report outlining all identified vulnerabilities, their potential impact, and recommended remediation steps. This is often a technical document aimed at IT and security teams.
A crucial aspect of VA is its reliance on databases of known vulnerabilities (like CVEs). It's great at finding the "low-hanging fruit" and widely published exploits, but it struggles with zero-days or unique application logic flaws.
Penetration Testing Methodology
PT is a more rigorous and adversarial process, often following a framework like the Penetration Testing Execution Standard (PTES) or mimicking the Cyber Kill Chain. A typical PT lifecycle includes:
- Reconnaissance: Gathering information about the target, both passively (open-source intelligence, OSINT) and actively (network scanning, port enumeration). This is where the attacker learns the battlefield.
- Vulnerability Analysis: Identifying potential weaknesses, often building upon the reconnaissance phase. This can involve using automated scanners, but it's heavily augmented by manual investigation and understanding of application logic.
- Exploitation: Actively attempting to leverage identified vulnerabilities to gain unauthorized access. This is the core of PT, using tools like Metasploit, custom scripts, and manual techniques.
- Post-Exploitation: Once access is gained, the tester attempts to maintain persistence, escalate privileges, move laterally across the network, and identify sensitive data. This phase demonstrates the true damage potential.
- Reporting: A comprehensive report is generated, detailing the entire attack chain, successful exploits, compromised systems, data discovered, and actionable remediation strategies. This report is critical for executive-level understanding of risk.
The human element in PT is critical. A skilled tester can identify issues that automated tools would miss and creatively chain vulnerabilities in ways that a scanner never could. This is what separates a "list of flaws" from a "risk assessment."
Choosing the Right Approach
The decision between VA and PT depends on your organization's maturity, budget, and specific security goals:
- For Compliance and Broad Coverage: A Vulnerability Assessment is often sufficient. It's cost-effective for identifying a wide range of known issues and meeting baseline security requirements. If your goal is to simply know what's out there, VA is your answer.
- For Deep Risk Assessment and Proactive Defense: A Penetration Test is indispensable. It validates the effectiveness of your security controls and provides a realistic view of your organization's resilience against sophisticated attacks. PT is for organizations that want to understand how their defenses would fare in a real-world scenario.
Ideally, organizations should employ both. A regular VA can provide continuous monitoring, while periodic PTs offer a deeper, more aggressive validation. Think of it as a health check-up followed by a stress test.
Engineer's Verdict: Worth the Investment?
Absolutely. Both Vulnerability Assessments and Penetration Tests are critical components of a robust cybersecurity strategy, not optional luxuries. Neglecting them is akin to leaving the doors of your most valuable assets unlocked and hoping for the best. The cost of a breach—data loss, reputational damage, regulatory fines—far outweighs the investment in these proactive security measures.
Vulnerability Assessments are your proactive sentinel. They offer continuous visibility and are essential for maintaining a healthy attack surface. They're a fundamental layer of defense.
Penetration Tests are your adversarial simulation. They test the effectiveness of your defenses under pressure and reveal exploitable pathways that automated tools miss. They are vital for understanding your true risk posture.
For organizations serious about security, a tiered approach is best: leverage automated VAs for ongoing monitoring and gap analysis, augmented by periodic, in-depth Penetration Tests. This dual strategy provides comprehensive coverage, ensuring you're not just aware of potential weaknesses but also equipped to defend against their exploitation.
Operator's Arsenal
To effectively conduct or evaluate VAs and PTs, an operator needs a specific set of tools and knowledge. Here's a glimpse into the essentials:
- Vulnerability Scanners: Nessus, Qualys, OpenVAS, Nexpose. For web applications, OWASP ZAP and Burp Suite (Community/Professional) are indispensable.
- Exploitation Frameworks: Metasploit Framework is the industry standard. Cobalt Strike is a commercial favorite for its advanced post-exploitation capabilities, though its cost is significant.
- Network Analysis Tools: Wireshark for deep packet inspection, Nmap for network discovery and port scanning.
- OSINT Tools: Maltego, theHarvester, Recon-ng for gathering external intelligence.
- Privilege Escalation & Lateral Movement: Mimikatz, PowerSploit, BloodHound for Active Directory environments.
- Reporting Tools: Templating engines for custom reports, Markdown and LaTeX for technical documentation.
- Knowledge Base: Access to CVE databases (NVD), exploit-db, security blogs, and research papers. Continuous learning is non-negotiable.
For professionals looking to formalize their skills, certifications like the OSCP (Offensive Security Certified Professional) from Offensive Security, or the CEH (Certified Ethical Hacker) from EC-Council, are highly regarded. A strong understanding of networking protocols, operating systems (Windows, Linux), web technologies, and scripting languages (Python, Bash) is foundational. Consider subscribing to security news feeds and threat intelligence platforms to stay abreast of the latest TTPs.
Practical Guide: Simulating an Attack
Let's outline a basic pseudo-walkthrough for a simplified penetration test focusing on web application vulnerabilities, a common scenario.
-
Objective Definition: Assume a target is a fictional e-commerce web application hosted at
http://example-shop.com. The goal is to identify and exploit common web vulnerabilities. -
Reconnaissance (Passive & Active):
- Use OSINT tools (e.g., Google dorking, Shodan) to find subdomains, publicly exposed information, and technologies used.
- Employ Nmap to scan the web server's IP for open ports, focusing on 80 (HTTP) and 443 (HTTPS).
- Use Burp Suite's proxy to intercept and inspect all traffic to
http://example-shop.com.
-
Vulnerability Scanning (Automated & Manual):
- Run an automated web scanner (like OWASP ZAP Scanner or Burp Suite Scanner) against the target URL.
- Manually inspect forms, input fields, URL parameters, and HTTP headers for potential injection points (SQLi, XSS, Command Injection).
- Example: Look for parameters like
product_idin URLs (e.g.,http://example-shop.com/products?id=123). Try injecting characters like `'`, `"`, `;`, `|` to see if the application throws errors or behaves unexpectedly. A common SQLi test is appending' OR '1'='1. - Example XSS: Inject simple payloads like
<script>alert(1)</script>into search bars or user profile fields. If an alert box pops up, you've found a reflected or stored XSS vulnerability.
-
Exploitation:
- If a SQL injection vulnerability is confirmed, attempt to extract data (e.g., usernames, passwords from a login form). Tools like sqlmap can automate this process.
- If an XSS vulnerability is found, consider what sensitive data could be stolen (e.g., session cookies) or if it can be used to redirect users to a phishing site.
- Check for Broken Access Control: Can a low-privileged user access admin panels or other users' data by simply changing an ID in the URL?
- Reporting: Document all steps, confirmed vulnerabilities, screenshots of exploits, and potential impact. For instance, "Confirmed SQL Injection in product search leading to potential database compromise. Extracted user table headers."
Remember, this is a simplified overview. Real-world pentesting involves much more complex techniques for evasion, persistence, and lateral movement.
Frequently Asked Questions
What is the primary difference in outcome between VA and PT?
A VA provides a list of potential vulnerabilities. A PT demonstrates the actual risk by exploiting those vulnerabilities and showing the impact.
Can one replace the other?
No. They serve complementary purposes. VAs offer breadth and continuous monitoring, while PTs offer depth and validation.
How often should an organization perform these tests?
Vulnerability Assessments should be performed frequently (e.g., monthly or quarterly). Penetration Tests are typically done annually or after significant system changes.
Are automated tools sufficient for penetration testing?
Automated tools are essential for VAs and the initial phases of PTs, but they cannot replace the critical thinking, creativity, and manual effort of a skilled human penetration tester.
What's the typical cost difference?
Vulnerability Assessments are generally less expensive due to their automated nature. Penetration Tests are more costly due to the intensive manual labor and expertise required.
The Contract: Securing Your Perimeter
Your organization’s digital perimeter is under constant siege. You can either understand the threats by actively probing your defenses, or you can wait for the inevitability of a breach. The choice between a Vulnerability Assessment and a Penetration Test is not mutually exclusive; it’s about choosing the right tool for the right job at the right time.
A VA tells you what *might* be wrong. A PT tells you what *is* wrong and how bad it can get. Both are essential contracts with your business continuity and your customers' trust.
Now, it's your turn. Have you ever encountered a situation where a VA missed a critical vulnerability that a PT later discovered? Or perhaps you've seen a PT report that was less actionable than expected? Share your experiences below. Let's break down the real-world effectiveness of these methodologies in the comments. What are your go-to tools and techniques for validating security posture?
```Vulnerability Assessment vs. Penetration Testing: A Deep Dive for the Modern Operator

The digital battlefield is a murky place. Systems whisper with exploitable flaws, secrets lie buried in misconfigurations, and the silence of a network can often mask a lurking threat. In this environment, understanding the tools and tactics at your disposal is not just an advantage; it's a prerequisite for survival. Today, we dissect two critical methodologies that form the bedrock of offensive security validation: Vulnerability Assessment (VA) and Penetration Testing (PT).
Many equate these terms, lumping them into a single "security check." This is a rookie mistake, a sure sign of an immature security program. While both aim to identify weaknesses, their scope, depth, and ultimate objectives diverge significantly. Think of it as the difference between a doctor taking your temperature and a surgeon performing a complex operation. Both are medical actions, but their invasiveness, diagnostic power, and desired outcome are worlds apart.
For those on the front lines, whether defending turf or probing enemy lines, grasping these distinctions is paramount. A VA shines a spotlight on potential issues, flagging them for attention. A PT, on the other hand, is an active assault, attempting to leverage those flaws, much like a seasoned attacker would, to gauge the true blast radius of a breach.
Table of Contents
- Understanding Vulnerability Assessment
- Penetration Testing: The Offensive Edge
- Key Differences: A Head-to-Head
- Vulnerability Assessment Methodology
- Penetration Testing Methodology
- Choosing the Right Approach
- Engineer's Verdict: Worth the Investment?
- Operator's Arsenal
- Practical Guide: Simulating an Attack
- Frequently Asked Questions
- The Contract: Securing Your Perimeter
Understanding Vulnerability Assessment
A Vulnerability Assessment is, at its core, an audit. It's a systematic review designed to identify, quantify, and prioritize vulnerabilities within an organization's systems and applications. Think of it as a detailed, automated sweep across your digital estate. Tools like Nessus, OpenVAS, or Qualys are the workhorses here, diligently scanning networks, servers, workstations, and applications for known vulnerabilities, misconfigurations, and policy violations.
The output of a VA is typically a report listing discovered vulnerabilities, often categorized by severity (e.g., Critical, High, Medium, Low). It tells you *what* is wrong. It highlights that port 22 is open with an outdated SSH version, or that a web application is susceptible to SQL injection based on banner information. However, it stops short of verifying if these vulnerabilities are actually exploitable in your specific environment, or if a chain of lesser vulnerabilities could lead to a significant compromise.
"A vulnerability is a weakness. An exploit is the act of leveraging that weakness for unauthorized access or control."
Vulnerability Assessments are essential for maintaining a baseline understanding of your security posture. They are cost-effective for broad coverage and are excellent for compliance requirements where simply knowing about potential issues is sufficient. However, for an attacker, this report is just a shopping list of potential targets. They still need to do the heavy lifting of confirming exploitability.
Penetration Testing: The Offensive Edge
Penetration Testing, often dubbed "pentesting," goes beyond mere identification. It's an authorized, simulated cyberattack on your systems, performed to evaluate their security by actively exploiting vulnerabilities. Professional penetration testers, much like the black hats they mimic, aim to breach defenses, gain access to sensitive data, and demonstrate the real-world impact of security weaknesses. The goal isn't just to find vulnerabilities, but to prove how they can be weaponized.
A PT is a hands-on, often manual, process that simulates the tactics, techniques, and procedures (TTPs) of real-world adversaries. It involves reconnaissance, scanning, gaining initial access, escalating privileges, lateral movement, and potentially exfiltrating data. The report from a PT details not only the vulnerabilities found but also how they were exploited, the pathways to compromise, and the potential business impact. It answers the question: *What could an attacker actually do with these flaws?*
A comprehensive penetration test can uncover vulnerabilities missed by automated scans, like business logic flaws, complex chained exploits, or instances where a combination of low-severity issues creates a critical pathway for attackers. It provides a much deeper, more actionable insight into an organization's true resilience against targeted attacks. This is where the true value for an offensive security professional lies – understanding the exploitability and impact.
Key Differences: A Head-to-Head
Let's break down the core distinctions:
- Objective: VA aims to identify and catalogue vulnerabilities. PT aims to exploit vulnerabilities to assess real-world risk.
- Methodology: VA is largely automated, using scanners. PT is a mix of automated tools and intensive manual effort, mimicking attacker behavior.
- Depth: VA provides breadth (identifying many potential issues). PT provides depth (confirming exploitability and impact of selected issues).
- Scope: VA typically covers a wider range of systems, scanning for known signatures. PT often focuses on specific attack vectors or critical assets, attempting to break through.
- Output: VA reports a list of vulnerabilities with severity ratings. PT reports on successful exploits, compromised systems, and business impact, alongside vulnerabilities.
- Verification: VA relies on vulnerability signatures. PT involves active exploitation and verification of access.
Vulnerability Assessment Methodology
The standard VA process generally follows these stages:
- Planning: Define the scope, objectives, and systems to be assessed.
- Scanning: Utilize automated tools (eg. Nessus, Qualys, OpenVAS) to scan networks, hosts, and applications for known vulnerabilities, misconfigurations, and policy violations. This can include authenticated (credentialed) scans for deeper insights or unauthenticated scans for an external attacker's perspective.
- Analysis: Review scan results, eliminate false positives, and prioritize identified vulnerabilities based on severity, asset criticality, and threat intelligence.
- Reporting: Generate a detailed report outlining all identified vulnerabilities, their potential impact, and recommended remediation steps. This is often a technical document aimed at IT and security teams.
A crucial aspect of VA is its reliance on databases of known vulnerabilities (like CVEs). It's great at finding the "low-hanging fruit" and widely published exploits, but it struggles with zero-days or unique application logic flaws.
Penetration Testing Methodology
PT is a more rigorous and adversarial process, often following a framework like the Penetration Testing Execution Standard (PTES) or mimicking the Cyber Kill Chain. A typical PT lifecycle includes:
- Reconnaissance: Gathering information about the target, both passively (open-source intelligence, OSINT) and actively (network scanning, port enumeration). This is where the attacker learns the battlefield.
- Vulnerability Analysis: Identifying potential weaknesses, often building upon the reconnaissance phase. This can involve using automated scanners, but it's heavily augmented by manual investigation and understanding of application logic.
- Exploitation: Actively attempting to leverage identified vulnerabilities to gain unauthorized access. This is the core of PT, using tools like Metasploit, custom scripts, and manual techniques.
- Post-Exploitation: Once access is gained, the tester attempts to maintain persistence, escalate privileges, move laterally across the network, and identify sensitive data. This phase demonstrates the true damage potential.
- Reporting: A comprehensive report is generated, detailing the entire attack chain, successful exploits, compromised systems, data discovered, and actionable remediation strategies. This report is critical for executive-level understanding of risk.
The human element in PT is critical. A skilled tester can identify issues that automated tools would miss and creatively chain vulnerabilities in ways that a scanner never could. This is what separates a "list of flaws" from a "risk assessment."
Choosing the Right Approach
The decision between VA and PT depends on your organization's maturity, budget, and specific security goals:
- For Compliance and Broad Coverage: A Vulnerability Assessment is often sufficient. It's cost-effective for identifying a wide range of known issues and meeting baseline security requirements. If your goal is to simply know what's out there, VA is your answer.
- For Deep Risk Assessment and Proactive Defense: A Penetration Test is indispensable. It validates the effectiveness of your security controls and provides a realistic view of your organization's resilience against sophisticated attacks. PT is for organizations that want to understand how their defenses would fare in a real-world scenario.
Ideally, organizations should employ both. A regular VA can provide continuous monitoring, while periodic PTs offer a deeper, more aggressive validation. Think of it as a health check-up followed by a stress test.
Engineer's Verdict: Worth the Investment?
Absolutely. Both Vulnerability Assessments and Penetration Tests are critical components of a robust cybersecurity strategy, not optional luxuries. Neglecting them is akin to leaving the doors of your most valuable assets unlocked and hoping for the best. The cost of a breach—data loss, reputational damage, regulatory fines—far outweighs the investment in these proactive security measures.
Vulnerability Assessments are your proactive sentinel. They offer continuous visibility and are essential for maintaining a healthy attack surface. They're a fundamental layer of defense.
Penetration Tests are your adversarial simulation. They test the effectiveness of your defenses under pressure and reveal exploitable pathways that automated tools miss. They are vital for understanding your true risk posture.
For organizations serious about security, a tiered approach is best: leverage automated VAs for ongoing monitoring and gap analysis, augmented by periodic, in-depth Penetration Tests. This dual strategy provides comprehensive coverage, ensuring you're not just aware of potential weaknesses but also equipped to defend against their exploitation.
Operator's Arsenal
To effectively conduct or evaluate VAs and PTs, an operator needs a specific set of tools and knowledge. Here's a glimpse into the essentials:
- Vulnerability Scanners: Nessus, Qualys, OpenVAS, Nexpose. For web applications, OWASP ZAP and Burp Suite (Community/Professional) are indispensable.
- Exploitation Frameworks: Metasploit Framework is the industry standard. Cobalt Strike is a commercial favorite for its advanced post-exploitation capabilities, though its cost is significant.
- Network Analysis Tools: Wireshark for deep packet inspection, Nmap for network discovery and port scanning.
- OSINT Tools: Maltego, theHarvester, Recon-ng for gathering external intelligence.
- Privilege Escalation & Lateral Movement: Mimikatz, PowerSploit, BloodHound for Active Directory environments.
- Reporting Tools: Templating engines for custom reports, Markdown and LaTeX for technical documentation.
- Knowledge Base: Access to CVE databases (NVD), exploit-db, security blogs, and research papers. Continuous learning is non-negotiable.
For professionals looking to formalize their skills, certifications like the OSCP (Offensive Security Certified Professional) from Offensive Security, or the CEH (Certified Ethical Hacker) from EC-Council, are highly regarded. A strong understanding of networking protocols, operating systems (Windows, Linux), web technologies, and scripting languages (Python, Bash) is foundational. Consider subscribing to security news feeds and threat intelligence platforms to stay abreast of the latest TTPs.
Practical Guide: Simulating an Attack
Let's outline a basic pseudo-walkthrough for a simplified penetration test focusing on web application vulnerabilities, a common scenario.
-
Objective Definition: Assume a target is a fictional e-commerce web application hosted at
http://example-shop.com. The goal is to identify and exploit common web vulnerabilities. -
Reconnaissance (Passive & Active):
- Use OSINT tools (eg. Google dorking, Shodan) to find subdomains, publicly exposed information, and technologies used.
- Employ Nmap to scan the web server's IP for open ports, focusing on 80 (HTTP) and 443 (HTTPS).
- Use Burp Suite's proxy to intercept and inspect all traffic to
http://example-shop.com.
-
Vulnerability Scanning (Automated & Manual):
- Run an automated web scanner (like OWASP ZAP Scanner or Burp Suite Scanner) against the target URL.
- Manually inspect forms, input fields, URL parameters, and HTTP headers for potential injection points (SQLi, XSS, Command Injection).
- Example: Look for parameters like
product_idin URLs (eg.http://example-shop.com/products?id=123). Try injecting characters like',",;,|to see if the application throws errors or behaves unexpectedly. A common SQLi test is appending' OR '1'='1. - Example XSS: Inject simple payloads like
<script>alert(1)</script>into search bars or user profile fields. If an alert box pops up, you've found a reflected or stored XSS vulnerability.
-
Exploitation:
- If a SQL injection vulnerability is confirmed, attempt to extract data (eg. usernames, passwords from a login form). Tools like sqlmap can automate this process.
- If an XSS vulnerability is found, consider what sensitive data could be stolen (eg. session cookies) or if it can be used to redirect users to a phishing site.
- Check for Broken Access Control: Can a low-privileged user access admin panels or other users' data by simply changing an ID in the URL?
- Reporting: Document all steps, confirmed vulnerabilities, screenshots of exploits, and potential impact. For instance, "Confirmed SQL Injection in product search leading to potential database compromise. Extracted user table headers."
Remember, this is a simplified overview. Real-world pentesting involves much more complex techniques for evasion, persistence, and lateral movement.
Frequently Asked Questions
What is the primary difference in outcome between VA and PT?
A VA provides a list of potential vulnerabilities. A PT demonstrates the actual risk by exploiting those vulnerabilities and showing the impact.
Can one replace the other?
No. They serve complementary purposes. VAs offer breadth and continuous monitoring, while PTs offer depth and validation.
How often should an organization perform these tests?
Vulnerability Assessments should be performed frequently (eg. monthly or quarterly). Penetration Tests are typically done annually or after significant system changes.
Are automated tools sufficient for penetration testing?
Automated tools are essential for VAs and the initial phases of PTs, but they cannot replace the critical thinking, creativity, and manual effort of a skilled human penetration tester.
What's the typical cost difference?
Vulnerability Assessments are generally less expensive due to their automated nature. Penetration Tests are more costly due to the intensive manual labor and expertise required.
The Contract: Securing Your Perimeter
Your organization’s digital perimeter is under constant siege. You can either understand the threats by actively probing your defenses, or you can wait for the inevitability of a breach. The choice between a Vulnerability Assessment and a Penetration Test is not mutually exclusive; it’s about choosing the right tool for the right job at the right time.
A VA tells you what *might* be wrong. A PT tells you what *is* wrong and how bad it can get. Both are essential contracts with your business continuity and your customers' trust.
Now, it's your turn. Have you ever encountered a situation where a VA missed a critical vulnerability that a PT later discovered? Or perhaps you've seen a PT report that was less actionable than expected? Share your experiences below. Let's break down the real-world effectiveness of these methodologies in the comments. What are your go-to tools and techniques for validating security posture?

No comments:
Post a Comment