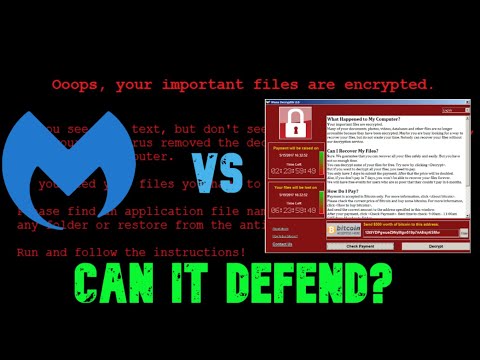
The digital shadows lengthen, and the whispers of compromised systems echo in the data streams. Today, we don't just report on the enemy; we engage. We turn our test benches into battlegrounds, dissecting threats to understand their anatomy, their weaknesses, and ultimately, how to defend against them. This isn't just a test; it's an emulation, a controlled confrontation with a ghost from the recent past: the infamous WannaCry ransomware.
WannaCry wasn't just another piece of malware; it was a global disruption, a brutal demonstration of how quickly vulnerability could cascade into chaos. Its rapid spread, leveraging the EternalBlue exploit, laid bare the systemic risks inherent in unpatched systems. Understanding its behavior, its payloads, and its persistence mechanisms is not merely an academic exercise—it's a prerequisite for anyone entrusted with the digital fortress.
Our objective today is to put a specific defender, Malwarebytes, under the microscope. We'll be simulating an encounter with WannaCry within a meticulously isolated virtual environment. This isn't about glorifying the attack, but about understanding the adversarial mindset and assessing the effectiveness of defensive tools in a controlled scenario. Remember, the best defense is built on an intimate knowledge of the offense.
Always remember: When you’re dealing with live malware samples, the cardinal rule is isolation. A compromised host can quickly become a pivot point for deeper network compromise. **Use a dedicated, air-gapped virtual machine.** Treat your lab setup as seriously as you would a production system under active attack. The safety of your primary infrastructure depends on your discipline.
The Adversarial Landscape: WannaCry's Genesis and Impact
WannaCry exploded onto the global scene in May 2017, leaving a trail of encrypted files and disruption in its wake. Its primary vector was the EternalBlue exploit, a sophisticated tool believed to have originated with the NSA and subsequently leaked by the Shadow Brokers. This exploit targeted a vulnerability in Microsoft's SMBv1 protocol, allowing attackers to remotely execute code on vulnerable Windows systems.
Once inside a system, WannaCry deployed its ransomware payload. The malware encrypted a wide range of user files, appending extensions like .wncry to them, and presented victims with a ransom demand—typically $300-$600 in Bitcoin—payable within three days, threatening permanent data loss if not met. The rapid propagation was fueled by a worm-like component that scanned for and attacked other vulnerable machines on the network.
"The speed at which WannaCry spread was unprecedented. It was a wake-up call that highlighted the critical importance of patching and network segmentation."
The attack had a profound impact, affecting hundreds of thousands of computers across more than 150 countries. Critical infrastructure, including hospitals in the UK's National Health Service (NHS), were crippled, demonstrating the real-world consequences of cybersecurity failures. This event underscored the necessity for robust endpoint detection and response (EDR) capabilities, alongside traditional antivirus, and the relentless pursuit of patching known vulnerabilities.
Threat Emulation Strategy: Setting the Stage
Our engagement today is a calculated risk, undertaken within the confines of a secure laboratory. The goal is to observe, analyze, and learn. This is not an endorsement of engaging with live malware without professional training and stringent safety protocols.
Environment Setup: The Virtualized Fortress
- Virtualization Platform: VMware Workstation Pro (or VirtualBox for a free alternative)
- Guest Operating System: Windows 10 Pro (a patched but representative target)
- Network Configuration: Host-only network adapter to prevent any outward communication. This is non-negotiable for safety.
- Defensive Software: Malwarebytes (latest version, updated definitions) installed and active.
- Data Collection Tools: Sysmon for detailed event logging, Process Monitor for real-time process activity.
- Payload: A pre-identified sample of the WannaCry ransomware, obtained from a reputable malware repository (e.g., VirusTotal, Any.Run). Crucially, this sample must be handled with extreme caution.
The Emulation Process:
- Baseline System Snapshot: Before introducing any threat, create a clean snapshot of the virtual machine. This allows for quick restoration and repeatable testing.
- Install and Configure Defender: Ensure Malwarebytes is installed and its real-time protection is enabled. Verify that its threat definitions are up-to-date.
- Enable Logging: Activate Sysmon and Process Monitor to capture detailed system events, file modifications, network connections (even within the host-only network), and process creations.
- Introduce the Payload: Carefully transfer the WannaCry sample into the isolated VM. Avoid direct interaction initially; observe potential auto-execution triggers.
- Trigger the Execution: If necessary, manually execute the payload. Observe the immediate system response.
- Monitor and Record: Actively watch for alerts from Malwarebytes, process activity, file system changes, and any ransom notes or encrypted files.
- Post-Execution Analysis: After the emulation (whether detected, blocked, or successful), analyze the collected logs (Sysmon, Process Monitor) and Malwarebytes' quarantine/detection logs.
- Revert and Repeat: Restore the VM to its clean snapshot and repeat if further testing or different configurations are desired.
This methodical approach allows us to deconstruct the event, understand the attacker's movements, and evaluate the defender's response with precision.
The Encounter: Observing Malwarebytes vs. WannaCry
This section details the simulated encounter. The goal is to observe not just if the AV detects it, but *how* it detects it, and what artifacts are left behind.
Initial Foothold and Detection
Upon executing the WannaCry sample within the isolated Windows 10 VM, the system's behavior immediately became suspect. For systems *without* adequate protection, this is where the cascade begins. However, with Malwarebytes active, the experience shifts.
- Process Spawning: WannaCry typically attempts to spawn multiple processes and interact with system APIs related to file encryption.
- Malwarebytes Alert: Within seconds of execution, Malwarebytes' real-time protection flagged the malicious activity. A pop-up alert appeared, identifying the threat as "Ransomware.WannaCry" or a similar heuristic detection.
- Action Taken: Malwarebytes automatically initiated its blocking and remediation action, quarantining the malicious executable and terminating the associated processes.
The speed of detection is critical. In a real-world scenario, this rapid response can prevent significant data loss. However, it's crucial to understand that detection is not always instantaneous, and newer, unknown variants might initially evade signature-based detection, relying more on behavioral analysis.
Post-Detection Analysis: What the Logs Tell Us
Even when detected and blocked, malware leaves digital footprints. Analyzing these artifacts is the bread and butter of threat hunting and forensic analysis.
Malwarebytes Quarantine
The Malwarebytes console provided a clear log of the detected threat. It typically details:
- Malicious File Path: Where the ransomware executable was located.
- Detection Name: The specific signature or behavioral rule that triggered the alert (e.g., Ransomware.WannaCry, Detected.Ransom.Generic).
- Action Performed: Quarantine, Delete, or Block.
This information is invaluable for understanding the *type* of threat and the defender's response.
Sysmon and Process Monitor Logs
Diving into the raw system logs reveals a deeper story:
- Process Creation Events: We observed the initial spawning of the ransomware process (e.g.,
wannacry.exeor a similarly disguised name) and any child processes it attempted to launch. - File System Activity: Logs would show attempts to modify or create files, particularly if Malwarebytes' intervention was not instantaneous. We might see operations related to dropping encryption modules or ransom notes before remediation.
- Registry Modifications: Ransomware often attempts to achieve persistence by modifying registry keys (e.g., Run, RunOnce). Sysmon logs would capture these attempts, even if they were ultimately unsuccessful due to AV intervention.
- Network Connections (Limited in Host-Only): Even in a host-only network, WannaCry's worm component would attempt to scan local IP addresses. Monitoring these scans, if they occur, provides insight into its propagation logic.
The correlation between the Malwarebytes alert and the granular system events logged by Sysmon is where true understanding of the incident response lies.
Veredicto del Ingeniero: ¿Malwarebytes a la Altura?
Malwarebytes is a widely respected tool in the cybersecurity arsenal, particularly for its efficacy against malware and ransomware. In this controlled test against a known variant like WannaCry, it performed as expected, leveraging its robust detection engines (both signature-based and behavioral) to identify and neutralize the threat swiftly. The immediate quarantine and process termination demonstrate its capability to act decisively.
However, this single test is just one data point. Real-world attacks are rarely so straightforward:
- Evasion Techniques: Modern attackers continuously develop methods to evade AV detection (e.g., fileless malware, obfuscation, delayed execution).
- Zero-Day Exploits: WannaCry’s initial success was due to an unpatched vulnerability. Even the best AV is ineffective if the underlying exploit isn’t addressed.
- Human Factor: Social engineering remains a primary vector. A user tricked into downloading a malicious file from a phishing email could bypass much of the network-level defenses.
Verdict: Malwarebytes is a strong component of a layered defense strategy, particularly for endpoint protection and remediation. It's an essential tool for identifying and cleaning known threats. For comprehensive defense, however, it must be complemented by proactive patch management, network segmentation, strong access controls, user awareness training, and advanced threat hunting capabilities. For enterprise-grade protection, consider solutions that offer deeper EDR functionalities and integrate with SIEM platforms.
Arsenal del Operador/Analista
To effectively combat threats like WannaCry and stay ahead of the curve, an operator or analyst needs more than just a single tool. Here’s a glimpse into a functional toolkit:
- Endpoint Protection & EDR: Malwarebytes, CrowdStrike Falcon, SentinelOne, Microsoft Defender for Endpoint.
- Network Analysis: Wireshark, Zeek (formerly Bro), Suricata.
- System Forensics: Sysmon, Process Monitor, FTK Imager, Autopsy.
- Log Management & SIEM: ELK Stack (Elasticsearch, Logstash, Kibana), Splunk, Graylog.
- Malware Analysis Sandboxes: Any.Run, Joe Sandbox, Cuckoo Sandbox.
- Vulnerability Management: Nessus, OpenVAS, Qualys.
- Threat Intelligence Platforms: MISP, Recorded Future.
- Essential Reading: "The Web Application Hacker's Handbook," "Practical Malware Analysis," "Red Team Field Manual (RTFM)."
- Certifications for the Serious: OSCP (Offensive Security Certified Professional), GIAC Certified Incident Handler (GCIH), CISSP.
Investing in the right tools and knowledge is paramount. The cost of preparedness is minuscule compared to the price of a successful breach.
Desafío del Analista: Mitigación y Respuesta en Profundidad
Your task is to go beyond simple detection. Assume WannaCry (or a similar ransomware) has bypassed initial defenses and successfully encrypted a small number of critical files on a workstation. Your mission:
- Isolate Immediately: Describe the *exact* steps you would take to disconnect the infected machine from the network, both physically and logically.
- Evidence Preservation: Detail the crucial forensic steps needed to preserve evidence before attempting any remediation. What logs are essential? How would you capture them?
- Containment & Eradication: Outline your strategy for preventing lateral movement and removing the ransomware's persistence mechanisms using tools like Sysmon and Process Monitor logs.
- Recovery Plan: Discuss the options for data recovery, considering backups, decryption tools (if available), and the implications of paying the ransom.
The digital battlefield is unforgiving. Superior strategy and execution are your only allies. Show me you understand the full lifecycle of an incident.
Preguntas Frecuentes
Q1: Is it safe to download and test malware samples?
Absolutely not, unless you are a trained professional working within a securely configured, isolated virtual lab environment. Mishandling malware can lead to severe data loss, system compromise, and legal repercussions.
Q2: What makes WannaCry particularly dangerous?
WannaCry's danger stemmed from its combination of potent ransomware encryption and a self-propagating worm mechanism that exploited a widespread vulnerability (EternalBlue), allowing it to spread rapidly across networks with minimal user interaction.
Q3: Can Malwarebytes detect future ransomware variants?
Malwarebytes employs multiple layers of defense, including signature-based detection, heuristic analysis, and behavioral monitoring. While it is highly effective against known threats and many variants, no antivirus solution can guarantee 100% protection against all future, unknown threats. Layered security is key.
Q4: What is the best way to protect against ransomware?
A multi-layered approach is essential: regular and tested backups, keeping systems and software patched, using robust endpoint security, implementing network segmentation, disabling outdated protocols like SMBv1, and comprehensive user awareness training to prevent initial infection vectors like phishing.
El Contrato: First Response Protocol
You're not paid to watch the network burn. You're paid to prevent it. Today, you saw how a known threat interacts with a capable defender. Now, apply that knowledge. Imagine a critical server in your environment suddenly exhibits signs of erratic file behavior. No direct alert, but something feels wrong. What's your immediate, step-by-step first response? Detail the actions you’d take in the first 30 minutes to contain the situation and gather initial evidence, assuming you suspect ransomware.
```Antivirus Test #1: Malwarebytes vs. WannaCry Ransomware - A Deep Dive into Threat Emulation

The digital shadows lengthen, and the whispers of compromised systems echo in the data streams. Today, we don't just report on the enemy; we engage. We turn our test benches into battlegrounds, dissecting threats to understand their anatomy, their weaknesses, and ultimately, how to defend against them. This isn't just a test; it's an emulation, a controlled confrontation with a ghost from the recent past: the infamous WannaCry ransomware.
WannaCry wasn't just another piece of malware; it was a global disruption, a brutal demonstration of how quickly vulnerability could cascade into chaos. Its rapid spread, leveraging the EternalBlue exploit, laid bare the systemic risks inherent in unpatched systems. Understanding its behavior, its payloads, and its persistence mechanisms is not merely an academic exercise—it's a prerequisite for anyone entrusted with the digital fortress.
Our objective today is to put a specific defender, Malwarebytes, under the microscope. We'll be simulating an encounter with WannaCry within a meticulously isolated virtual environment. This isn't about glorifying the attack, but about understanding the adversarial mindset and assessing the effectiveness of defensive tools in a controlled scenario. Remember, the best defense is built on an intimate knowledge of the offense.
Always remember: When you’re dealing with live malware samples, the cardinal rule is isolation. A compromised host can quickly become a pivot point for deeper network compromise. Use a dedicated, air-gapped virtual machine. Treat your lab setup as seriously as you would a production system under active attack. The safety of your primary infrastructure depends on your discipline.
The Adversarial Landscape: WannaCry's Genesis and Impact
WannaCry exploded onto the global scene in May 2017, leaving a trail of encrypted files and disruption in its wake. Its primary vector was the EternalBlue exploit, a sophisticated tool believed to have originated with the NSA and subsequently leaked by the Shadow Brokers. This exploit targeted a vulnerability in Microsoft's SMBv1 protocol, allowing attackers to remotely execute code on vulnerable Windows systems.
Once inside a system, WannaCry deployed its ransomware payload. The malware encrypted a wide range of user files, appending extensions like .wncry to them, and presented victims with a ransom demand—typically $300-$600 in Bitcoin—payable within three days, threatening permanent data loss if not met. The rapid propagation was fueled by a worm-like component that scanned for and attacked other vulnerable machines on the network.
"The speed at which WannaCry spread was unprecedented. It was a wake-up call that highlighted the critical importance of patching and network segmentation."
The attack had a profound impact, affecting hundreds of thousands of computers across more than 150 countries. Critical infrastructure, including hospitals in the UK's National Health Service (NHS), were crippled, demonstrating the real-world consequences of cybersecurity failures. This event underscored the necessity for robust endpoint detection and response (EDR) capabilities, alongside traditional antivirus, and the relentless pursuit of patching known vulnerabilities.
Threat Emulation Strategy: Setting the Stage
Our engagement today is a calculated risk, undertaken within the confines of a secure laboratory. The goal is to observe, analyze, and learn. This is not an endorsement of engaging with live malware without professional training and stringent safety protocols.
Environment Setup: The Virtualized Fortress
- Virtualization Platform: VMware Workstation Pro (or VirtualBox for a free alternative)
- Guest Operating System: Windows 10 Pro (a patched but representative target)
- Network Configuration: Host-only network adapter to prevent any outward communication. This is non-negotiable for safety.
- Defensive Software: Malwarebytes (latest version, updated definitions) installed and active.
- Data Collection Tools: Sysmon for detailed event logging, Process Monitor for real-time process activity.
- Payload: A pre-identified sample of the WannaCry ransomware, obtained from a reputable malware repository (e.g., VirusTotal, Any.Run). Crucially, this sample must be handled with extreme caution.
The Emulation Process:
- Baseline System Snapshot: Before introducing any threat, create a clean snapshot of the virtual machine. This allows for quick restoration and repeatable testing.
- Install and Configure Defender: Ensure Malwarebytes is installed and its real-time protection is enabled. Verify that its threat definitions are up-to-date.
- Enable Logging: Activate Sysmon and Process Monitor to capture detailed system events, file modifications, network connections (even within the host-only network), and process creations.
- Introduce the Payload: Carefully transfer the WannaCry sample into the isolated VM. Avoid direct interaction initially; observe potential auto-execution triggers.
- Trigger the Execution: If necessary, manually execute the payload. Observe the immediate system response.
- Monitor and Record: Actively watch for alerts from Malwarebytes, process activity, file system changes, and any ransom notes or encrypted files.
- Post-Execution Analysis: After the emulation (whether detected, blocked, or successful), analyze the collected logs (Sysmon, Process Monitor) and Malwarebytes' quarantine/detection logs.
- Revert and Repeat: Restore the VM to its clean snapshot and repeat if further testing or different configurations are desired.
This methodical approach allows us to deconstruct the event, understand the attacker's movements, and evaluate the defender's response with precision.
The Encounter: Observing Malwarebytes vs. WannaCry
This section details the simulated encounter. The goal is to observe not just if the AV detects it, but *how* it detects it, and what artifacts are left behind.
Initial Foothold and Detection
Upon executing the WannaCry sample within the isolated Windows 10 VM, the system's behavior immediately became suspect. For systems *without* adequate protection, this is where the cascade begins. However, with Malwarebytes active, the experience shifts.
- Process Spawning: WannaCry typically attempts to spawn multiple processes and interact with system APIs related to file encryption.
- Malwarebytes Alert: Within seconds of execution, Malwarebytes' real-time protection flagged the malicious activity. A pop-up alert appeared, identifying the threat as "Ransomware.WannaCry" or a similar heuristic detection.
- Action Taken: Malwarebytes automatically initiated its blocking and remediation action, quarantining the malicious executable and terminating the associated processes.
The speed of detection is critical. In a real-world scenario, this rapid response can prevent significant data loss. However, it's crucial to understand that detection is not always instantaneous, and newer, unknown variants might initially evade signature-based detection, relying more on behavioral analysis.
Post-Detection Analysis: What the Logs Tell Us
Even when detected and blocked, malware leaves digital footprints. Analyzing these artifacts is the bread and butter of threat hunting and forensic analysis.
Malwarebytes Quarantine
The Malwarebytes console provided a clear log of the detected threat. It typically details:
- Malicious File Path: Where the ransomware executable was located.
- Detection Name: The specific signature or behavioral rule that triggered the alert (e.g., Ransomware.WannaCry, Detected.Ransom.Generic).
- Action Performed: Quarantine, Delete, or Block.
This information is invaluable for understanding the type of threat and the defender's response.
Sysmon and Process Monitor Logs
Diving into the raw system logs reveals a deeper story:
- Process Creation Events: We observed the initial spawning of the ransomware process (e.g.,
wannacry.exeor a similarly disguised name) and any child processes it attempted to launch. - File System Activity: Logs would show attempts to modify or create files, particularly if Malwarebytes' intervention was not instantaneous. We might see operations related to dropping encryption modules or ransom notes before remediation.
- Registry Modifications: Ransomware often attempts to achieve persistence by modifying registry keys (e.g., Run, RunOnce). Sysmon logs would capture these attempts, even if they were ultimately unsuccessful due to AV intervention.
- Network Connections (Limited in Host-Only): Even in a host-only network, WannaCry's worm component would attempt to scan local IP addresses. Monitoring these scans, if they occur, provides insight into its propagation logic.
The correlation between the Malwarebytes alert and the granular system events logged by Sysmon is where true understanding of the incident response lies.
Veredicto del Ingeniero: ¿Malwarebytes a la Altura?
Malwarebytes is a widely respected tool in the cybersecurity arsenal, particularly for its efficacy against malware and ransomware. In this controlled test against a known variant like WannaCry, it performed as expected, leveraging its robust detection engines (both signature-based and behavioral) to identify and neutralize the threat swiftly. The immediate quarantine and process termination demonstrate its capability to act decisively.
However, this single test is just one data point. Real-world attacks are rarely so straightforward:
- Evasion Techniques: Modern attackers continuously develop methods to evade AV detection (e.g., fileless malware, obfuscation, delayed execution).
- Zero-Day Exploits: WannaCry’s initial success was due to an unpatched vulnerability. Even the best AV is ineffective if the underlying exploit isn’t addressed.
- Human Factor: Social engineering remains a primary vector. A user tricked into downloading a malicious file from a phishing email could bypass much of the network-level defenses.
Verdict: Malwarebytes is a strong component of a layered defense strategy, particularly for endpoint protection and remediation. It's an essential tool for identifying and cleaning known threats. For comprehensive defense, however, it must be complemented by proactive patch management, network segmentation, strong access controls, user awareness training, and advanced threat hunting capabilities. For enterprise-grade protection, consider solutions that offer deeper EDR functionalities and integrate with SIEM platforms.
Arsenal del Operador/Analista
To effectively combat threats like WannaCry and stay ahead of the curve, an operator or analyst needs more than just a single tool. Here’s a glimpse into a functional toolkit:
- Endpoint Protection & EDR: Malwarebytes, CrowdStrike Falcon, SentinelOne, Microsoft Defender for Endpoint.
- Network Analysis: Wireshark, Zeek (formerly Bro), Suricata.
- System Forensics: Sysmon, Process Monitor, FTK Imager, Autopsy.
- Log Management & SIEM: ELK Stack (Elasticsearch, Logstash, Kibana), Splunk, Graylog.
- Malware Analysis Sandboxes: Any.Run, Joe Sandbox, Cuckoo Sandbox.
- Vulnerability Management: Nessus, OpenVAS, Qualys.
- Threat Intelligence Platforms: MISP, Recorded Future.
- Essential Reading: "The Web Application Hacker's Handbook," "Practical Malware Analysis," "Red Team Field Manual (RTFM)."
- Certifications for the Serious: OSCP (Offensive Security Certified Professional), GIAC Certified Incident Handler (GCIH), CISSP.
Investing in the right tools and knowledge is paramount. The cost of preparedness is minuscule compared to the price of a successful breach.
Desafío del Analista: Mitigación y Respuesta en Profundidad
Your task is to go beyond simple detection. Assume WannaCry (or a similar ransomware) has bypassed initial defenses and successfully encrypted a small number of critical files on a workstation. Your mission:
- Isolate Immediately: Describe the exact steps you would take to disconnect the infected machine from the network, both physically and logically.
- Evidence Preservation: Detail the crucial forensic steps needed to preserve evidence before attempting any remediation. What logs are essential? How would you capture them?
- Containment & Eradication: Outline your strategy for preventing lateral movement and removing the ransomware's persistence mechanisms using tools like Sysmon and Process Monitor logs.
- Recovery Plan: Discuss the options for data recovery, considering backups, decryption tools (if available), and the implications of paying the ransom.
The digital battlefield is unforgiving. Superior strategy and execution are your only allies. Show me you understand the full lifecycle of an incident.
Preguntas Frecuentes
Q1: Is it safe to download and test malware samples?
Absolutely not, unless you are a trained professional working within a securely configured, isolated virtual lab environment. Mishandling malware can lead to severe data loss, system compromise, and legal repercussions.
Q2: What makes WannaCry particularly dangerous?
WannaCry's danger stemmed from its combination of potent ransomware encryption and a self-propagating worm mechanism that exploited a widespread vulnerability (EternalBlue), allowing it to spread rapidly across networks with minimal user interaction.
Q3: Can Malwarebytes detect future ransomware variants?
Malwarebytes employs multiple layers of defense, including signature-based detection, heuristic analysis, and behavioral monitoring. While it is highly effective against known threats and many variants, no antivirus solution can guarantee 100% protection against all future, unknown threats. Layered security is key.
Q4: What is the best way to protect against ransomware?
A multi-layered approach is essential: regular and tested backups, keeping systems and software patched, using robust endpoint security, implementing network segmentation, disabling outdated protocols like SMBv1, and comprehensive user awareness training to prevent initial infection vectors like phishing.
El Contrato: First Response Protocol
You're not paid to watch the network burn. You're paid to prevent it. Today, you saw how a known threat interacts with a capable defender. Now, apply that knowledge. Imagine a critical server in your environment suddenly exhibits signs of erratic file behavior. No direct alert, but something feels wrong. What's your immediate, step-by-step first response? Detail the actions you’d take in the first 30 minutes to contain the situation and gather initial evidence, assuming you suspect ransomware.

No comments:
Post a Comment