The digital realm is a shadowy alleyway, teeming with opportunists and predators. Among them, the keys to your most sensitive data – your databases – are often left carelessly guarded. phpMyAdmin, a ubiquitous tool in the MySQL ecosystem, is a prime target. Its web-based GUI, while convenient, can become a gaping vulnerability if left unhardened. Today, we’re not just looking at a tool; we’re dissecting its defenses, revealing its weak points, and reinforcing its architecture. This isn't about pretty interfaces; it's about survival in the dark. Let's talk about securing phpMyAdmin, from the ground up.
phpMyAdmin, for all its utility, is a complex application that touches the core of your data infrastructure. It’s a cross-platform, web-based interface built on PHP, designed for managing MySQL databases. While its accessibility is its strength, it's also its Achilles' heel. Attackers know this. They scan the web for default installations, weak credentials, and unpatched versions. Failing to secure it is akin to leaving your bank vault door ajar. We'll cover the essential steps to transform it from a potential liability into a hardened asset.
Table of Contents
- Default Configuration Pitfalls
- Authentication: The First Line of Defense
- Access Control: Building Walls
- Securing Communication and Transport
- Patching and Updates: The Eternal Vigilance
- Disguising Your Fortifications
- Advanced Hardening Techniques
- Arsenal of the Security Operator
- FAQ: Frequently Asked Questions
- The Contract: Secure Your Interface Now
Default Configuration Pitfalls
The default installation of phpMyAdmin is often a hacker's best friend. It's designed for ease of use out-of-the-box, not for the battlefield of the internet. Leaving it as-is exposes you to a buffet of potential attacks:
- Insecure Authentication: Default credentials, or lack thereof, are common.
- Unrestricted Access: Accessible from anywhere on the internet without IP restrictions.
- Lack of Encryption: Data transmitted in plain text, vulnerable to eavesdropping.
- Outdated Software: Relying on old versions with known exploits.
To mitigate these risks, we need to move beyond the defaults. This requires a methodical approach, treating your phpMyAdmin instance as a critical piece of infrastructure that demands constant attention. For any serious deployment, consider investing in comprehensive training courses that cover web application security and database hardening. Certifications like CompTIA Security+ or even more advanced ones like the OSCP can provide the deep understanding needed.
Authentication: The First Line of Defense
The cornerstone of any secure system is its authentication mechanism. For phpMyAdmin, this means ditching flimsy passwords and implementing robust controls.
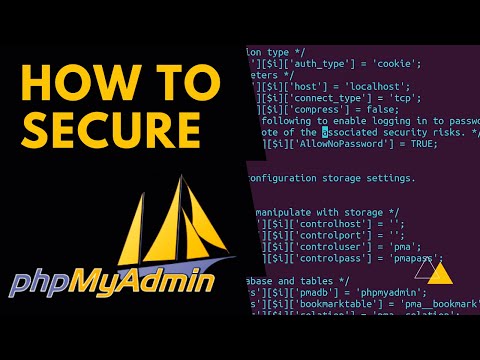
Modifying `config.inc.php`:
The primary configuration file, `config.inc.php`, is where you'll make most of these changes. If it doesn't exist, you can copy `config.sample.inc.php` and rename it.
/* Authentication type */
$cfg['Servers'][$i]['auth_type'] = 'cookie'; // Use cookie authentication
$cfg['Servers'][$i]['user'] = ''; // No default user
$cfg['Servers'][$i]['password'] = ''; // No default password
$cfg['Servers'][$i]['AllowUserSort'] = true;
$cfg['Servers'][$i]['AllowProprietaryDatabases'] = true;
Explanation:
- `auth_type = 'cookie'`: This is the recommended method. It uses cookies to maintain user sessions, which is more secure than embedding credentials directly or relying solely on HTTP basic authentication, especially if your transport layer isn't perfectly secured.
- `user` and `password`: Leaving these empty forces the user to log in with their specific MySQL credentials. Never embed root credentials here. Create dedicated MySQL users with the minimum necessary privileges for the tasks they need to perform.
HTTP Authentication:
Alternatively, you can use HTTP authentication provided by your web server. This adds an extra layer before the phpMyAdmin login screen even appears. You'll typically configure this within your web server's configuration files (e.g., Apache's `.htaccess` or `httpd.conf`).
# Example for Apache .htaccess
AuthType Basic
AuthName "Restricted Access"
AuthUserFile /path/to/.htpasswd
Require valid-user
Securing these credentials is paramount. For a truly hardened setup, consider integrating phpMyAdmin with a centralized authentication system like LDAP, though this is often outside the scope of a standard deployment and is typically found in enterprise-level security solutions or advanced penetration testing scenarios.
Access Control: Building Walls
Who gets to see the keys to the kingdom? You decide. Restricting access is crucial, especially if phpMyAdmin is exposed to the internet. The most effective method is IP-based access control.
Web Server Configuration (Apache Example):
<Directory /var/www/html/phpmyadmin>
Options FollowSymLinks
DirectoryIndex index.php
<IfModule mod_authz_core.c>
Require ip 192.168.1.0/24 # Allow access from your local network
Require ip 10.10.0.0/16 # Allow access from another internal network
# Deny from all implicitly if no 'Require' directive matches
</IfModule>
<IfModule !mod_authz_core.c>
Order deny,allow
Deny from all
Allow from 192.168.1.0/24
Allow from 10.10.0.0/16
</IfModule>
</Directory>
Explanation:
- The `Require ip` (Apache 2.4+) or `Allow from` (Apache 2.2) directives limit access to specific IP addresses or ranges.
- Crucially, if phpMyAdmin is accessible from the public internet, you should only allow access from known, trusted IP addresses (your office, your home IP if static, or a bastion host).
Nginx Example:
location ~ ^/phpmyadmin/(.*) {
allow 192.168.1.0/24;
allow 10.10.0.0/16;
deny all;
# Other phpMyAdmin configurations...
}
This configuration ensures that only authorized IPs can even reach the phpMyAdmin login page, significantly reducing the attack surface. Remember, relying solely on a firewall is often insufficient; server-level access control provides a more granular defense.
Securing Communication and Transport
Even with strong authentication and access control, if your connection to phpMyAdmin is unencrypted, your credentials and data are transmitted in plain text. This is a classic man-in-the-middle (MITM) attack waiting to happen. The solution is straightforward: use HTTPS.
Enforcing HTTPS:
- Obtain an SSL/TLS Certificate: You can get free certificates from Let's Encrypt or purchase one from a Certificate Authority (CA).
- Configure Your Web Server: Set up your web server (Apache, Nginx) to use the SSL/TLS certificate.
- Redirect HTTP to HTTPS: Ensure all HTTP requests to your phpMyAdmin URL are automatically redirected to the HTTPS version.
Apache Example (Virtual Host):
<VirtualHost *:80>
ServerName yourdomain.com
Redirect permanent /phpmyadmin https://yourdomain.com/phpmyadmin
</VirtualHost>
<VirtualHost *:443>
ServerName yourdomain.com
DocumentRoot /var/www/html
SSLEngine on
SSLCertificateFile /path/to/your/ssl.crt
SSLCertificateKeyFile /path/to/your/ssl.key
# ... phpMyAdmin configuration within this SSL virtual host ...
</VirtualHost>
Consider using security headers like Strict-Transport-Security (HSTS) to enforce browser compliance with HTTPS. This isn't merely a suggestion; it's a fundamental requirement for any web application managing sensitive data. Tools like Qualys SSL Labs can help you assess your TLS configuration's strength.
Patching and Updates: The Eternal Vigilance
Software vulnerabilities are a constant threat. phpMyAdmin, like any software project, has had its share of security flaws discovered over the years. The most effective defense against these is to keep your installation updated.
Update Strategy:
- Subscribe to Alerts: Follow phpMyAdmin's official announcements and security advisories.
- Regular Checks: Periodically visit the official phpMyAdmin website to check for new releases.
- Automated Updates (with caution): While tempting, fully automated updates can sometimes break functionality. A better approach is to set up notifications or use a package manager (`apt`, `yum`) that simplifies the update process.
- Test Updates: Before deploying updates to a production environment, test them on a staging or development server.
Example using `apt` (Debian/Ubuntu):
sudo apt update
sudo apt upgrade phpmyadmin
Ignoring updates leaves you exposed to known exploits that automated scanners actively hunt for. For serious security professionals, understanding the vulnerability lifecycle and diligently patching is a non-negotiable aspect of their daily routine. If you're serious about this, consider exploring books like "The Web Application Hacker's Handbook" for deeper insights into exploit methodologies.
Disguising Your Fortifications
While not a primary security measure, obscurity can be a useful layer in a defense-in-depth strategy. Making your phpMyAdmin installation harder to find can deter casual attackers and automated scans.
Changing the Alias:
The default path `/phpmyadmin` is widely known. You can change this by modifying your web server's configuration.
Apache Example:
Instead of linking to `/var/www/html/phpmyadmin`, you might use an alias:
Alias /mysecretadmin /var/www/html/phpmyadmin
<Directory /var/www/html/phpmyadmin>
# ... Access control directives as shown previously ...
</Directory>
Nginx Example:
location /mysecretadmin {
alias /var/www/html/phpmyadmin;
# ... Access control directives ...
}
Disabling Directory Listing:
Ensure that directory listing is disabled for your web server. This prevents attackers from browsing the contents of your directories if they somehow gain access.
Options -Indexes in Apache's `.htaccess` or `
Remember, obscurity alone is not security. It should complement, not replace, strong authentication, access control, and patching. Think of it as making your front door harder to find, but still having a robust lock and a guard.
Advanced Hardening Techniques
For those operating in high-security environments or engaging in rigorous security assessments, further steps can be taken:
- Two-Factor Authentication (2FA): While phpMyAdmin doesn't natively support 2FA, you can implement it at the web server level using modules like `mod_security` with custom rules or by proxying through an authentication gateway that supports 2FA.
- Web Application Firewall (WAF): Deploying a WAF (like ModSecurity, Cloudflare, or AWS WAF) can filter malicious requests before they even reach phpMyAdmin, protecting against SQL injection, XSS, and other common web attacks.
- Containerization: Running phpMyAdmin in a Docker container can provide isolation and simplify deployment and security management. Ensure the container image is kept updated and only exposes necessary ports.
- Dedicated Host/Subdomain: Host phpMyAdmin on its own subdomain or even a dedicated server, separate from your main web applications, to limit the blast radius of a compromise.
Investing in professional penetration testing services can help identify subtle misconfigurations and vulnerabilities you might have missed. These services often uncover issues that even the most diligent internal teams overlook.
Arsenal of the Security Operator
To effectively secure and manage phpMyAdmin, a seasoned operator relies on a curated set of tools and resources:
- Web Server Configuration Files: Apache (`httpd.conf`, `.htaccess`), Nginx (`nginx.conf`, site-specific configs) are your primary tools for access control and SSL enforcement.
- phpMyAdmin `config.inc.php`: The central hub for phpMyAdmin's own configuration.
- SSL/TLS Certificate Providers: Let's Encrypt, commercial CAs.
- Web Application Firewalls (WAFs): ModSecurity, Cloudflare, Sucuri, AWS WAF.
- Network Scanners: Nmap (to check open ports and services), Nikto (web server scanner).
- Packet Analyzers: Wireshark (for deep network traffic inspection).
- Containerization Platforms: Docker, Kubernetes.
- Books: "The Web Application Hacker's Handbook" (Dafydd Stuttard, Marcus Pinto), "SQL Injection Attacks and Defenses" (Justin Clarke).
- Certifications: CompTIA Security+, Certified Ethical Hacker (CEH), Offensive Security Certified Professional (OSCP).
- Online Resources: Official phpMyAdmin documentation, OWASP (Open Web Application Security Project).
"The greatest security risk is the user." - Often attributed to various security experts, emphasizing the importance of user education and credential management.
FAQ: Frequently Asked Questions
Q1: Is it safe to expose phpMyAdmin to the internet?
A: Exposing phpMyAdmin to the public internet without rigorous security measures is highly discouraged. Best practice is to restrict access by IP, use HTTPS, and employ strong authentication.
Q2: Can I use the root MySQL user for phpMyAdmin?
A: Absolutely not. Granting root privileges to phpMyAdmin is a massive security risk. Create specific MySQL users with the minimal privileges required for the tasks they will perform.
Q3: How often should I update phpMyAdmin?
A: You should update phpMyAdmin whenever a new stable version or security patch is released. Regularly checking for updates is part of maintaining a secure environment.
Q4: What is the best authentication method for phpMyAdmin?
A: Cookie authentication (`auth_type = 'cookie'`) is generally recommended for its balance of security and usability. For extremely sensitive environments, combining it with HTTP authentication and IP restrictions provides a strong defense.
Q5: How can I further secure my MySQL server itself?
A: Securing phpMyAdmin is only part of the puzzle. Ensure your MySQL server is also hardened: use strong passwords, restrict network access, disable unnecessary features, encrypt sensitive data, and keep the MySQL server software updated.
The Contract: Secure Your Interface Now
You've seen the blueprints. You understand the vectors. Leaving your phpMyAdmin installation exposed is a debt that will inevitably be collected, likely at the worst possible moment. The contract is simple: implement these security measures or face the consequences. Start with the basics – change the alias, enforce cookie authentication, and lock down access by IP. Then, layer on HTTPS and commit to a regular patching schedule. Don't wait for an alert from your SIEM or, worse, a notification about a data breach. The time to act is now. Your data’s integrity depends on your discipline.
Now, the floor is yours. Are there other hardening techniques you employ? Have you encountered particularly sophisticated attacks against phpMyAdmin? Share your knowledge, your scripts, and your war stories in the comments. Let's build a collective defense.

No comments:
Post a Comment