The digital shadows whisper tales of executables that wreak havoc. Among them, 000.exe stands as a relic, a testament to simpler, yet equally destructive, forms of malware. This isn't a guide to unleash chaos; it's a deep dive into what makes such a file tick, dissecting its anatomy to understand its impact and, more importantly, how to build better defenses against its modern descendants. We're not just looking at a file; we're performing a digital autopsy.
The core of cybersecurity is understanding the adversary. While the landscape of threats constantly evolves, the fundamental techniques often remain the same, just veiled in more sophisticated packaging. 000.exe, though seemingly rudimentary by today's standards, exemplifies a common attack vector that many systems still fall prey to: the execution of malicious code. This post is an exercise in reverse engineering the attacker's mindset to bolster our own fortifications. We'll peer into the mechanisms of disruption, not to replicate them, but to illuminate the vulnerabilities they exploit and the silent alarms we can set to detect them.
In the grand theater of cybersecurity, where every system is a potential stage for a digital performance, understanding the opening act of an attack is paramount. 000.exe, a name that echoes in the annals of malware history, represents a fundamental class of threats: self-propagating executables designed to alter system behavior, often through disruptive means. Its historical impact, particularly on older Windows environments like Windows 7, serves as a crucial case study. By deconstructing its function, we gain invaluable insights into the tactics, techniques, and procedures (TTPs) that form the bedrock of many modern malware operations. This analysis is not about celebrating destruction, but about learning from it, applying that knowledge to fortify our digital perimeters.
The Artifact: Understanding 000.exe
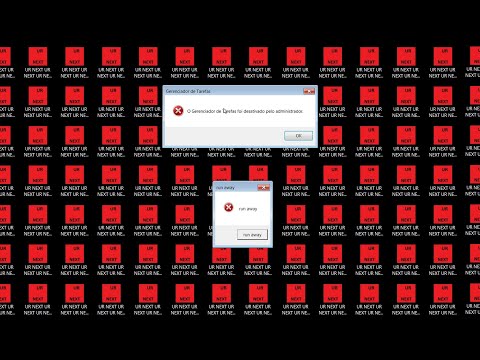
At its heart, 000.exe is a program designed to execute a specific set of commands once launched. Its primary function, observed in historical analyses, often involved creating copies of itself across the system, potentially modifying the Windows Registry to ensure persistence, and even altering desktop configurations to display disruptive messages or icons, as was famously demonstrated on Windows 7 desktops. This self-propagation mechanism is a classic characteristic of worms and certain types of viruses.
Mechanism of Action: What Did It Do?
- Self-Replication: A key feature was its ability to copy itself to various locations on the infected system, often targeting removable drives or system folders. This allowed the infection to spread beyond the initial point of entry.
- Desktop Manipulation: Beyond simple replication, 000.exe was known to alter the user's desktop by replacing icons with its own executable or displaying specific messages. This served as a visual indicator of infection and often a primary method of user notification (albeit a destructive one).
- Registry Modifications: To achieve persistence, malware like 000.exe would often modify critical Windows Registry keys. This ensures that the malware would automatically execute every time the system booted, making it difficult to remove without specific knowledge of these modifications.
- Potential for Further Payload Delivery: While the primary observed behavior was disruptive, executables of this nature often serve as a dropper or initial access vector for more potent, secondary payloads that could lead to data exfiltration, ransomware, or remote access.
Defensive Strategy: Lessons Learned from 000.exe
The "mess" left by 000.exe on a Windows 7 desktop, while visually striking, points to fundamental security weaknesses that we must address. The ease with which such an executable could infect a system highlights the critical importance of a multi-layered defense strategy. The principles learned from analyzing this classic malware are directly applicable to defending against contemporary threats.
Threat Hunting Hypothesis: Look for the Echoes
When hunting for threats, particularly those that mimic older malware behaviors, we can formulate hypotheses based on observed TTPs. For 000.exe, a threat hunting query might look for:
- Unusual file creation events in specific system directories.
- Registry modifications to startup keys (e.g., `Run`, `RunOnce`).
- Processes creating copies of themselves across the filesystem.
- Unexpected changes to desktop shortcuts or system icons.
These are the digital fingerprints we seek. The absence of sophisticated obfuscation in 000.exe makes it an excellent training ground for developing foundational detection skills.
Vulnerability Analysis and Mitigation: Patching the Gaps
The primary vulnerability exploited by 000.exe is the user's trust in executing unknown files, coupled with operating system configurations that allowed such execution with elevated privileges. Mitigation strategies include:
- User Education (The Human Firewall): This is paramount. Users must be trained to recognize the dangers of downloading and executing files from untrusted sources, especially those received via email or suspicious websites. The allure of "free stuff" or "curiosity" is a potent social engineering vector.
- Application Whitelisting: Technologies like AppLocker or Windows Defender Application Control can prevent unauthorized executables from running altogether. This is a strong technical control against files like 000.exe.
- Principle of Least Privilege: Users should operate with the minimum necessary privileges. If a user account doesn't have administrative rights, it significantly limits the damage an executable can inflict, such as widespread registry modifications or system file alterations.
- Endpoint Detection and Response (EDR): Modern security solutions are designed to detect anomalous behavior, even from unknown executables. They can monitor file system activity, process creation, and registry changes, providing alerts and automated response capabilities.
- Regular Patching and Updates: While 000.exe itself might target older systems, the principle holds: keeping operating systems and applications patched closes known security holes that malware can exploit for initial access or privilege escalation.
Taller Práctico: Fortaleciendo la Resiliencia del Sistema
Guía de Detección: Anomalías en la Creación de Archivos y Registros
Here's a conceptual approach to detecting similar behaviors using PowerShell, a staple for Windows administration and threat hunting:
-
Monitor Process Creation and File Writes: Observe processes that unexpectedly create executable files in user directories or temporary folders.
# Conceptual PowerShell Snippet for Monitoring Suspicious File Writes # This requires advanced logging and potentially EDR integration for real-time monitoring. # This is illustrative of the *type* of detection logic. Get-WinEvent -FilterHashtable @{ LogName = 'Microsoft-Windows-Sysmon/Operational' ID = 11 # FileCreate event ID in Sysmon } | Where-Object { $filePath = $_.Properties[6].Value $processName = $_.Properties[2].Value # Define directories to monitor for suspicious file creations $suspiciousPaths = @( "$env:USERPROFILE\Downloads", "$env:TEMP", "$env:APPDATA", "$env:LOCALAPPDATA" ) # Check if the file is being created in a suspicious location and is an executable if ($suspiciousPaths -contains (Split-Path $filePath -Parent) -and ($filePath -like "*.exe" -or $filePath -like "*.dll")) { Write-Host "Suspicious file creation detected: $($filePath) by process $($processName)" } } -
Detect Registry Run Key Modifications: Monitor for changes to registry keys that automatically start programs.
# Conceptual PowerShell Snippet for Detecting Registry Run Key Modifications # This also benefits greatly from Sysmon logging. Get-WinEvent -FilterHashtable @{ LogName = 'Microsoft-Windows-Sysmon/Operational' ID = 12 # RegistryEvent event ID in Sysmon Data = 'Run' # Filter specifically for 'Run' key modifications } | Where-Object { $keyPath = $_.Properties[1].Value $action = $_.Properties[0].Value # Operation type (e.g., SetValue, DeleteKey) # Focus on modifications that add new entries if ($action -eq 'SetValue' -and $keyPath -like "*\\Software\\Microsoft\\Windows\\CurrentVersion\\Run*") { $valueName = $_.Properties[2].Value $newValue = $_.Properties[3].Value Write-Host "Suspicious Registry modification: $($action) on $($keyPath)\$($valueName) with value $($newValue)" } } -
Analyze Running Processes for Replication: Look for processes that are numerous and creating new files or processes in an unusual pattern.
# Conceptual PowerShell Snippet for basic process monitoring # Note: Sophisticated replication detection often requires baseline comparison and behavioral analysis. Get-Process | Where-Object { $_.ProcessName -ne "svchost" -and $_.ProcessName -ne "System" } | Select-Object ProcessName, Id, Path | ForEach-Object { # Basic check: Does the process path seem unusual or is it in a user-writable location? if ($_.Path -like "$env:USERPROFILE\*" -or $_.Path -like "$env:TEMP\*") { Write-Host "Process $(($_.Path) ?? $_.ProcessName) with PID $($_.Id) is running from a suspicious location." } # Further analysis would involve comparing process creation times, parent process, etc. }
Verdicto del Ingeniero: ¿Vale la Pena Adoptar un Enfoque Minimalista?
000.exe represents a bygone era of malware simplicity. Its effectiveness stemmed not from complex evasion techniques, but from exploiting fundamental user trust and system misconfigurations. For defenders, this translates to a clear, actionable takeaway: the most effective defenses often lie in the basics. Robust user education, strict adherence to the principle of least privilege, and diligent patch management form an impenetrable first line of defense. While advanced threat detection tools are crucial, they are most effective when augmenting, not replacing, these foundational security practices. Ignoring the lessons from rudimentary malware is akin to designing a fortress against modern artillery while leaving the gates wide open and undefended.
Arsenal del Operador/Analista
- Sysmon: Essential for detailed system activity logging, enabling granular threat hunting.
- PowerShell: The Swiss Army knife for Windows system administration and incident response scripting.
- Sigcheck (Sysinternals Suite): Useful for verifying file signatures and detecting unsigned executables.
- Volatility Framework: For in-depth memory forensics, should the malware leave traces in RAM.
- Burp Suite / OWASP ZAP: While 000.exe is not a web exploit, understanding web security tools is vital for a comprehensive skillset.
- CompTIA Security+ / OSCP: Certifications that solidify foundational and advanced cybersecurity knowledge, respectively.
- "The Web Application Hacker's Handbook": A classic reference for understanding web vulnerabilities, applicable to a broad range of security analysis.
Preguntas Frecuentes
¿Es 000.exe peligroso hoy en día?
While 000.exe itself is largely an artifact of the past and unlikely to infect modern, patched Windows systems effectively, the *techniques* it employed (self-replication, registry manipulation, unauthorized execution) are still foundational to many contemporary malware threats. Understanding it is a stepping stone.
¿Cómo elimino malware similar a 000.exe si mi sistema está infectado?
For older systems, manual removal might involve deleting the executable files, cleaning up registry entries associated with its persistence, and potentially using specialized removal tools. For modern systems, an EDR solution or a reputable antivirus scanner is the primary defense and removal mechanism.
¿Por qué analizar malware antiguo en lugar de las amenazas actuales?
Analyzing older malware like 000.exe provides a clear understanding of fundamental exploitation techniques. It builds a strong foundation in reverse engineering, malware analysis, and detection logic that is transferable to understanding more complex modern threats.
¿Qué sistemas operativos son más vulnerables a este tipo de malware?
Older versions of Windows, particularly those without up-to-date security patches or advanced security features (like Windows XP, Vista, and early versions of Windows 7), are most vulnerable. Modern operating systems with robust security controls and up-to-date patches offer significantly better protection.
El Contrato: Asegura Tu Perímetro contra Ejecutables Inesperados
Your mission, should you choose to accept it, is to simulate a basic defense for a hypothetical workstation. Imagine this machine is running an older, unpatched Windows version. Without using any advanced tools, outline the manual steps you would take, based on the behaviors of 000.exe, to both identify and attempt to remove such a threat. Consider file locations, registry keys, and potential user impact. Document your findings and the logic behind each step. The goal is to think like a first responder with limited resources.

No comments:
Post a Comment